Linux基础-----系统安全及应用
目录
一.锁定账户文件、密码文件
二.密码安全控制
三.历史命令的限制
四.终端自动注销
五.使用su命令切换用户
六.sudo命令提升执行权限
七.PAM安全认证
八.开关机安全控制
九.终端以及登录控制
十.系统弱口令检测
一.锁定账户文件、密码文件
- Linux系统中的所有账户文件在/etc/passwd,密码文件在/etc/shadow
- 此时配置文件,内容无法更改,无法添加,删除用户
- 使用chattr + i 锁定配置文件,chattr - i 解锁配置文件
- 使用lsattr 命令查看文件锁定情况
- 实例如下:
[root@localhost ~]# chattr +i /etc/passwd /etc/shadow //锁定文件
[root@localhost ~]# id wangwu
id: wangwu: no such user
[root@localhost ~]# useradd wangwu
useradd:无法打开 /etc/passwd
[root@localhost ~]# lsattr /etc/passwd /etc/shadow //查看文件,处于锁定状态
----i----------- /etc/passwd
----i----------- /etc/shadow
[root@localhost ~]# chattr -i /etc/passwd /etc/shadow //解锁文件
[root@localhost ~]# useradd wangwu
[root@localhost ~]# id wangwu
uid=1002(wangwu) gid=1002(wangwu) 组=1002(wangwu)
[root@localhost ~]# lsattr /etc/passwd /etc/shadow
---------------- /etc/passwd
---------------- /etc/shadow
[root@localhost ~]#
二.密码安全控制
- 管理员可以在服务器端限制用户密码使用期限
- 对于已经创建的用户,使用chage -M 使用期限 账户名,设置密码使用期限
- 实例如下
[root@localhost ~]# tail -5 /etc/shadow
apache:!!:18211::::::
named:!!:18211::::::
zhangsan:$6$p.VzHcHU8yZntT2f$f.TaW8ASwqa.k1fOJm5xdTExlc1xLWhew4VvUTzS8i9QMwwz1tB7QWnvxpZMoJ3wAn/tDQeyHqC0hT1cFR9Eq/:18209:0:99999:7:::
lisi:$6$VzaO83/n$5ryFrD3iEK2oo85sD3B2PKuV8.cMFUe7v/7ZSrgvw9L4530I8Phz.LHltyIFN3qfzj0oSnE9z74oDdvHFAATD/:18214:0:99999:7:::
wangwu:!!:18214:0:30:7:::
[root@localhost ~]# chage -M 99999 wangwu
[root@localhost ~]# tail -5 /etc/shadow
apache:!!:18211::::::
named:!!:18211::::::
zhangsan:$6$p.VzHcHU8yZntT2f$f.TaW8ASwqa.k1fOJm5xdTExlc1xLWhew4VvUTzS8i9QMwwz1tB7QWnvxpZMoJ3wAn/tDQeyHqC0hT1cFR9Eq/:18209:0:99999:7:::
lisi:$6$VzaO83/n$5ryFrD3iEK2oo85sD3B2PKuV8.cMFUe7v/7ZSrgvw9L4530I8Phz.LHltyIFN3qfzj0oSnE9z74oDdvHFAATD/:18214:0:99999:7:::
wangwu:!!:18214:0:99999:7:::
[root@localhost ~]#
- 对于还未创建的用户,可以进入密码使用期限的配置文件/etc/login.defs,编辑配置文件后,不会影响已有的账户
- 实例如下
[root@localhost ~]# vim /etc/login.defs
......
PASS_MAX_DAYS 30
PASS_MIN_DAYS 0
PASS_MIN_LEN 5
PASS_WARN_AGE 7
......
[root@localhost ~]# useradd zhaoliu
[root@localhost ~]# passwd zhaoliu
更改用户 zhaoliu 的密码 。
新的 密码:
无效的密码: 密码少于 8 个字符
重新输入新的 密码:
passwd:所有的身份验证令牌已经成功更新。
[root@localhost ~]# tail -2 /etc/shadow
wangwu:!!:18214:0:99999:7:::
zhaoliu:$6$AITY5Yfv$QRyWL95zE0aLA1ctBBTfVsB2Td3mdM9fWyjs3Z3Vc8hW.VS/cSN1JfLC4kiEPiF6884U1gs8DDJ6mHyQONdJC1:18214:0:30:7:::
[root@localhost ~]#
- 下次登录时及时修改密码:chage -d 0 账户
三.历史命令的限制
- 历史命令记录文件目录在 /etc/profile
- 历史命令的记录条数由变量HISTSIZE控制,默认HISTSIZE=1000
- 可以通过修改/etc/profile文件中的HISSIZE值,控制历史命令条数
- 实例如下
360 userdel -r wangwu
361 tail -5 /etc/passwd
362 id lisi
363 id zhangsan
364 id root
365 history
[root@localhost ~]# vim /etc/profile
......
HOSTNAME=`/usr/bin/hostname 2>/dev/null`
HISTSIZE=5
if [ "$HISTCONTROL" = "ignorespace" ] ; then
export HISTCONTROL=ignoreboth
else
export HISTCONTROL=ignoredups
fi
export PATH USER LOGNAME MAIL HOSTNAME HISTSIZE HISTCONTROL
......
[root@localhost ~]#source /etc/profile //执行文件,否则要重启
[root@localhost ~]# history
2 history
3 vim /etc/profile
4 history
5 reboot
6 history
[root@localhost ~]#
-
宿主家目录中的.bash_logout文件,再用户退出bash坏境之后被执行,可以修改该文件,添加清空历史命令的操作语句
-
当用户退出时,所记录的历史命令会被清空
-
实例如下
[root@localhost ~]# ls -a
. .bash_history .bashrc .cshrc .ICEauthority .local .Xauthority 视频 下载
.. .bash_logout .cache .dbus initial-setup-ks.cfg .tcshrc 公共 图片 音乐
anaconda-ks.cfg .bash_profile .config .esd_auth john-1.8.0.tar.gz .viminfo 模板 文档 桌面
[root@localhost ~]# vim ./.bash_logout
# ~/.bash_logout
history -c
clear
~
[root@localhost ~]#source ./bash_logout //使这个文件生效
[root@localhost ~]# history
1 history
[root@localhost ~]#
四.终端自动注销
- /etc/profile中的变量TMOUT控制闲置超时时间,当超过时间时自动注销终端,默认以秒为单位
- 实例如下
[root@localhost ~]# vim /etc/profile
......
unset i
unset -f pathmunge
export TMOUT=30 // 设置超过30s注销
[root@localhost ~]# source /etc/profile // 执行文件
[root@localhost ~]#
五.使用su命令切换用户
- 格式:su - 目标用户 ,切换到目标用户的家目录
- su 目标用户,切换到当前目录
- 使用whoami命令查看当前用户
- 默认情况下,任何用户都允许使用su命令,可以借助pam_wheel认证模块,只允许个别用户使用su命令切换
- 实例如下
[root@localhost ~]# tail -2 /etc/passwd
zhangsan:x:1000:1000:zhangsan:/home/zhangsan:/bin/bash
lisi:x:1001:1001::/home/lisi:/bin/bash
[root@localhost ~]# id zhangsan
uid=1000(zhangsan) gid=1000(zhangsan) 组=1000(zhangsan),10(wheel)
[root@localhost ~]# id lisi
uid=1001(lisi) gid=1001(lisi) 组=1001(lisi)
[root@localhost ~]# vim /etc/pam.d/su
#%PAM-1.0
auth sufficient pam_rootok.so
# Uncomment the following line to implicitly trust users in the "wheel" group.
#auth sufficient pam_wheel.so trust use_uid
# Uncomment the following line to require a user to be in the "wheel" group.
auth required pam_wheel.so use_uid //开启PAM认证
auth substack system-auth
auth include postlogin
account sufficient pam_succeed_if.so uid = 0 use_uid quiet
account include system-auth
password include system-auth
session include system-auth
session include postlogin
session optional pam_xauth.so
~
[root@localhost ~]# su - lisi
上一次登录:四 11月 14 18:42:09 CST 2019pts/0 上
[lisi@localhost ~]$ su - root
密码:
su: 拒绝权限
[lisi@localhost ~]$ 注:只有在wheel组里才有权限切换到任意用户
六.sudo命令提升执行权限
- sudo命令的用途:以其他用户(如root)执行授权的命令
- 命令格式:sudo 授权命令
- 配置sudo授权的配置文件/etc/sudoers,利用visudo或者vim /etc/sudoers进行编辑
- /etc/sudoers中的记录格式:用户 主机名列表 = 命令程序列表 ,且命令程序要写绝对路径
- 在wheel组的账号,才能使用sudo提权
- 给wheel组的账号进行提权操作,如下:
[root@localhost ~]# id zhangsan
uid=1000(zhangsan) gid=1000(zhangsan) 组=1000(zhangsan),10(wheel)
[root@localhost ~]# su - zhangsan
上一次登录:六 11月 9 16:41:02 CST 2019:0 上
[zhangsan@localhost ~]$ ifconfig
ens33: flags=4163 mtu 1500
inet 192.168.43.133 netmask 255.255.255.0 broadcast 192.168.43.255
inet6 fe80::fe27:a784:dd8d:8487 prefixlen 64 scopeid 0x20
ether 00:0c:29:de:a0:aa txqueuelen 1000 (Ethernet)
RX packets 1115 bytes 77414 (75.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 284 bytes 28574 (27.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
......
[zhangsan@localhost ~]$ sudo ifconfig ens33 10.10.10.10
我们信任您已经从系统管理员那里了解了日常注意事项。
总结起来无外乎这三点:
#1) 尊重别人的隐私。
#2) 输入前要先考虑(后果和风险)。
#3) 权力越大,责任越大。
[sudo] zhangsan 的密码:
[zhangsan@localhost ~]$ ifconfig
ens33: flags=4163 mtu 1500
inet 10.10.10.10 netmask 255.0.0.0 broadcast 10.255.255.255
inet6 fe80::fe27:a784:dd8d:8487 prefixlen 64 scopeid 0x20
ether 00:0c:29:de:a0:aa txqueuelen 1000 (Ethernet)
RX packets 1116 bytes 77657 (75.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 295 bytes 31297 (30.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
......
[zhangsan@localhost ~]$
- 给非wheel组的账户,在/etc/sudoers配置文件中进行,添加编辑该账号权限
- 实例如下
[root@localhost ~]# id lisi
uid=1001(lisi) gid=1001(lisi) 组=1001(lisi)
[root@localhost ~]# su - lisi
[lisi@localhost ~]$ sudo ifconfig ens33 8.8.8.8
我们信任您已经从系统管理员那里了解了日常注意事项。
总结起来无外乎这三点:
#1) 尊重别人的隐私。
#2) 输入前要先考虑(后果和风险)。
#3) 权力越大,责任越大。
[sudo] lisi 的密码:
lisi 不在 sudoers 文件中。此事将被报告。
[lisi@localhost ~]$ ifconfig
ens33: flags=4163 mtu 1500
inet 10.10.10.10 netmask 255.0.0.0 broadcast 10.255.255.255
inet6 fe80::fe27:a784:dd8d:8487 prefixlen 64 scopeid 0x20
ether 00:0c:29:de:a0:aa txqueuelen 1000 (Ethernet)
RX packets 1205 bytes 82997 (81.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 295 bytes 31297 (30.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
......
[root@localhost ~]# vim /etc/sudoers
lisi localhost=/sbin/ifconfig
:wq!
[lisi@localhost ~]$ sudo ifconfig ens33 10.10.10.10
[lisi@localhost ~]$ ifconfig
ens33: flags=4163 mtu 1500
inet 10.10.10.10 netmask 255.0.0.0 broadcast 10.255.255.255
inet6 fe80::fe27:a784:dd8d:8487 prefixlen 64 scopeid 0x20
ether 00:0c:29:de:a0:aa txqueuelen 1000 (Ethernet)
RX packets 1352 bytes 92726 (90.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 346 bytes 36834 (35.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
......
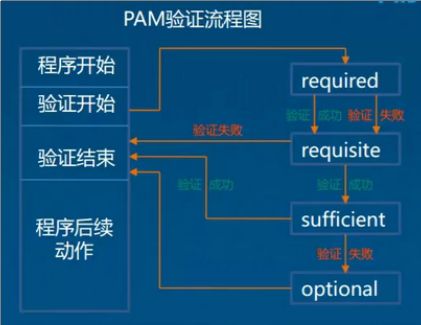
七.PAM安全认证
- PAM可插拔式认证模块,它是一种高效而且灵活便利的用户级别的认证方式,他也是当前Linux服务器普遍使用的认证方式
- PAM认证一般的顺序:service(服务)>PAM(配置文件)>pam_*.so
- PAM认证首先要确定哪一项服务,然后加载相应的PAM配置文件(/etc/pam.d),最后调用认证文件(/etc/security)进行安全认证
- 用户访问服务器的时候,服务器的某一个服务程序把用户的请求送到PAM模块进行认证
- 不同的应用程序所对应的PAM模块也是不同的
- PAM安全认证流程
- PAM的认证类型:认证管理,账户管理,密码管理,会话管理
- PAM认证的构成:其中每一行都是一个独立的认证过程,每一行可以区分为三个字段(认证类型,控制类型,PAM模块及其参数)
八.开关机安全控制
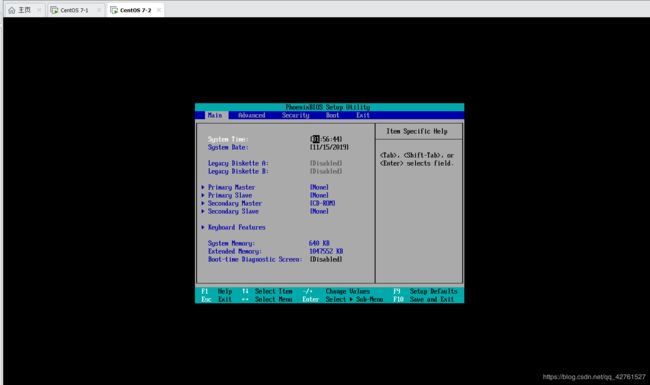
- 调整BIOS引导设置
- 将第一引导设备设为当前系统所在硬盘
- 禁止从其他设备(光盘,U盘,网络)引导系统(在Linux基础-----引导过程管理与服务控制文章中提过用光盘修改root用户密码)
- 将安全级别设为setup,并设置管理员密码,以防止未授权的修改
- 实例如下(当系统开始读条时,f2可进入BIOS界面)
- GRUB限制
- 使用grub2-mkpasswd-pbkdf2生成密钥
- 修改/etc/grub.d/00_header文件中,添加密码记录
- 生成新的grub.cfg配置文件
- 实例步骤:
拷贝GRUB的配置文件/boot/grub2/grub.cfg和/etc/grub.d/00_header.bak
[root@localhost ~]# cp /boot/grub2/grub.cfg /boot/grub2/grub.cfg.bak
[root@localhost ~]# cp /etc/grub.d/00_header /etc/grub.d/00_header.bak
[root@localhost ~]# ls /boot/grub2
device.map fonts grub.cfg grub.cfg.bak grubenv i386-pc locale
[root@localhost ~]# ls /etc/grub.d
00_header 01_users 20_ppc_terminfo 41_custom
00_header.bak 10_linux 30_os-prober README
00_tuned 20_linux_xen 40_custom
[root@localhost ~]#
生成密钥
[root@localhost ~]# grub2-mkpasswd-pbkdf2
输入口令:
Reenter password:
PBKDF2 hash of your password is grub.pbkdf2.sha512.10000.216CF19C390AA52C29DD8E0E499EE272863A984A88A532C91594A467A2D3F42FA018E96811D3392EF73869361BAAFCB353F7A0552C73016E0C67C59F20AB85A0.1BCBF077B8F4BA7605869EC17356BC7DB54F59132955ED3DAE7BC0C209ABD7531A54BBA948058F8A785AE13194A952207D51D836E7BE84BF8B47A65BEADE22CA
[root@localhost ~]#
修改头文件
[root@localhost ~]# vim /etc/grub.d/00_header
if [ "x$GRUB_BUTTON_CMOS_ADDRESS" != "x" ]; then
cat <生成新的GRUB配置文件
[root@localhost ~]# grub2-mkconfig -o /boot/grub2/grub.cfg
Generating grub configuration file ...
Found linux image: /boot/vmlinuz-3.10.0-693.el7.x86_64
Found initrd image: /boot/initramfs-3.10.0-693.el7.x86_64.img
Found linux image: /boot/vmlinuz-0-rescue-dec81954d1114e09bb2764d831144880
Found initrd image: /boot/initramfs-0-rescue-dec81954d1114e09bb2764d831144880.img
done
[root@localhost ~]#
九.终端以及登录控制
- Linux系统中login程序读取安全终端配置文件/etc/securetty
- vim /etc/securetty编辑增删终端,限制root的登录
- 如下
[root@localhost ~]# cat /etc/securetty
console
vc/1
vc/2
vc/3
vc/4
vc/5
vc/6
vc/7
vc/8
vc/9
vc/10
vc/11
tty1
tty2
tty3
tty4
tty5
tty6
tty7
tty8
tty9
tty10
tty11
ttyS0
ttysclp0
sclp_line0
3270/tty1
hvc0
hvc1
hvc2
hvc3
hvc4
hvc5
hvc6
hvc7
hvsi0
hvsi1
hvsi2
xvc0
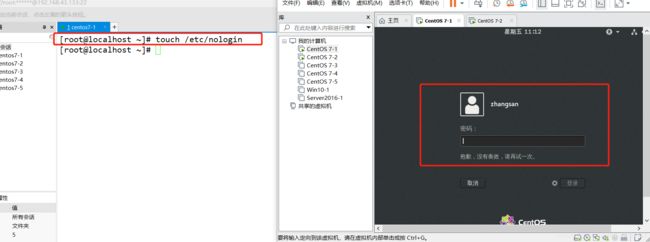
[root@localhost ~]#- 禁止普通用户登录,通过在/etc下面建立 /nologin文件(touch /etc/nologin)
- 删除nologin文件或者重启后恢复正常(rm -rf /etc/nologin)
- 实例如下
十.系统弱口令检测
- 手工编译安装Joth the Ripper工具,简称为JR
- JR工具支持字典式的的暴力破解,通过对shadow的口令分析,可以检测密码强度
- 实例如下
手工编译安装工具,把解压到/mnt目录下
[root@localhost mnt]# rz
[root@localhost mnt]# ls
john-1.8.0.tar.gz
[root@localhost mnt]# tar xvfz john-1.8.0.tar.gz
[root@localhost mnt]# ls
john-1.8.0 john-1.8.0.tar.gz
[root@localhost mnt]#
安装编译环境
[root@localhost mnt]# cd john-1.8.0/
[root@localhost john-1.8.0]# cd src/
[root@localhost src]# yum install gcc gcc-c++ -y
安装
[root@localhost src]# make linux-x86-64
测试
[root@localhost mnt]# ls
john-1.8.0 john-1.8.0.tar.gz
[root@localhost mnt]# cd ./john-1.8.0/
[root@localhost john-1.8.0]# ls
doc README run src
[root@localhost john-1.8.0]# cd ./run
[root@localhost run]# ls
ascii.chr john.conf makechr unafs
digits.chr lm_ascii.chr password.lst unique
john mailer relbench unshadow
[root@localhost run]# ./john /etc/passwd /etc/shadow
Loaded 2 password hashes with 2 different salts (crypt, generic crypt(3) [?/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
123123 (root)
123123 (zhangsan)
2g 0:00:00:23 100% 2/3 0.08389g/s 266.1p/s 286.2c/s 286.2C/s leslie..boston
Use the "--show" option to display all of the cracked passwords reliably
Session completed
[root@localhost run]#
- nmap网络扫描工具,nmap可以找出网路中不可控的服务,从而及时关闭不安全的服务,减少安全风险
- nmap的使用格式:nmap [扫描类型] [选项] <扫描目标 ...>
- nmap -sU 目标ip,扫描目标主机UDP服务
- nmap -sS 目标ip,tcp syn半开扫描
- nmap -sT 目标ip,完整的TCP扫描
- nmap -sF 目标ip,tcp fin扫描
- nmap -sP 目标ip,ping 扫描,探测主机是否开启
- nmap -P0 目标ip , 跳过ping检测,此方式认为所有目标主机是存活的
- 实例如下
[root@localhost ~]# nmap -sT 192.168.43.133
Starting Nmap 6.40 ( http://nmap.org ) at 2019-11-15 12:07 CST
Nmap scan report for 192.168.43.133
Host is up (0.00045s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
111/tcp open rpcbind
Nmap done: 1 IP address (1 host up) scanned in 0.06 seconds
[root@localhost ~]# nmap -sS 192.168.43.133
Starting Nmap 6.40 ( http://nmap.org ) at 2019-11-15 12:07 CST
Nmap scan report for 192.168.43.133
Host is up (0.0000020s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
111/tcp open rpcbind
Nmap done: 1 IP address (1 host up) scanned in 0.05 seconds
[root@localhost ~]# nmap -sU 192.168.43.133
Starting Nmap 6.40 ( http://nmap.org ) at 2019-11-15 12:08 CST
Stats: 0:00:02 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
Nmap scan report for 192.168.43.133
Host is up (0.000080s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
68/udp open|filtered dhcpc
111/udp open rpcbind
5353/udp open|filtered zeroconf
Nmap done: 1 IP address (1 host up) scanned in 48.01 seconds