ip virtual-reassembly:IP虚拟分片重组
把分片的报文在自身组装起来,这样可以识别一些攻击之类的 FW功能。
IP虚拟分片重组
为了避免每个业务模块(如:IPSec、NAT和防火墙)单独处理后片先到(报文分片后)这种情况而导致复杂度过高,设备需要收到IP报文后就对分片报文进行虚拟分片重组。IP虚拟分片重组功能可以对分片报文进行检验、排序和缓存,保证后续业务模块处理的都是顺序正确的分片报文。
同时,IP虚拟分片重组功能还可以对下面几种分片攻击进行检测。如果检测到分片攻击,则设备会丢弃收到的分片报文,从而提高了设备的安全性。
Tiny Fragment攻击:如果设备收到分片报文的首片长度非常小,并且传输层协议(如:TCP、UDP)头字段放在第二个分片中,则认为是受到了Tiny Fragment攻击;
Overlapping Fragment攻击:如果设备收到了完全相同的分片报文,或者收到的分片报文与其前一分片或后一分片出现重叠时,则认为是受到了Overlapping Fragment攻击;
Fragment-flood攻击:如果设备收到的分片报文超过了指定的最大分片报文数或者设备上创建的分片队列个数超过了指定的最大分片队列个数,则认为是受到了Fragment-flood攻击。
Configuring VFR
Use this task to enable VFR on an interface, specify maximum threshold values to combat buffer overflow and control memory usage, and verify any VFR configurations.
SUMMARY STEPS
1. ![]() enable
enable
2. ![]() configureterminal
configureterminal
3. ![]() interface type type number
interface type type number
4. ![]() ip virtual-reassembly [max-reassemblies number] [max-fragments number] [timeout seconds] [drop-fragments]
ip virtual-reassembly [max-reassemblies number] [max-fragments number] [timeout seconds] [drop-fragments]
5. ![]() exit
exit
6. ![]() exit
exit
7. ![]() show ip virtual-reassembly [interface type]
show ip virtual-reassembly [interface type]
DETAILED STEPS
Step 1
enable
Example:Router> enable
Enables privileged EXEC mode.
•![]() Enter your password if prompted.
Enter your password if prompted.
Step 2
configureterminal
Example:Router# configure terminal
Enters global configuration mode.
Step 3
interfacetype number
Example:Router(config)# interface ethernet1/1
Configures an interface type and enters interface configuration mode.
Step 4
ip virtual-reassembly [max-reassemblies number] [max-fragments number] [timeout seconds] [drop-fragments]
Example:Router(config-if)# ip virtual-reassembly max-reassemblies 64 max-fragments 16 timeout 5
Enables VFR on an interface.
Step 5
exit
Example:Router(config-if)# exit
Exits interface configuration mode.
Step 6
exit
Example:Router(config)# exit
Exits global configuration mode.
Step 7
show ip virtual-reassembly [interface type]
Example:Router# show ip virtual-reassembly ethernet1/1
Displays the configuration and statistical information of the VFR.
If an interface is not specified, VFR information is shown for all configured interfaces.
Troubleshooting Tips
To view debugging messages related to the VFR subsystem, use the debug ip virtual-reassembly command.
Configuration Examples for Fragmentation Reassembly
This section contains the following configuration example:
•![]() Configuring VFR and a Cisco IOS Firewall: Example
Configuring VFR and a Cisco IOS Firewall: Example
Configuring VFR and a Cisco IOS Firewall: Example
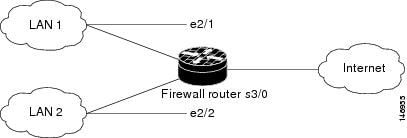
The following example shows a typical scenario where the Virtual Fragment Reassembly module is enabled on interfaces ethernet2/1, ethernet2/2, and serial3/0 to facilitate the firewall that is enabled in the outbound direction on interface serial3/0. In this example, the firewall rules that specify the list of LAN1 and LAN2 originating protocols (FTP, HTTP and SMTP) are to be inspected.
Figure 1 VFR and Cisco IOS Firewall Sample Topology
!
ip inspect name INTERNET-FW ftp
ip inspect name INTERNET-FW http
ip inspect name INTERNET-FW smtp
!
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface Ethernet2/0
ip address 9.4.21.9 255.255.0.0
no ip proxy-arp
no ip mroute-cache
duplex half
no cdp enable
!
interface Ethernet2/1
description LAN1
ip address 14.0.0.2 255.255.255.0
ip virtual-reassembly
duplex half
!
interface Ethernet2/2
description LAN2
ip address 15.0.0.2 255.255.255.0
ip virtual-reassembly
duplex half
!
interface Ethernet2/3
no ip address
no ip mroute-cache
shutdown
duplex half
!
interface Serial3/0
description Internet
ip unnumbered Loopback0
encapsulation ppp
ip access-group 102 in
ip inspect INTERNET-FW out
ip virtual-reassembly
serial restart-delay 0
!
ip classless
ip route 0.0.0.0 0.0.0.0 s3/0
!
!
! Access Control Rule that drops all internet originated traffic.
!
access-list 102 deny ip any any
!
!
!
!
control-plane
!
no call rsvp-sync
!
!
!
dial-peer cor custom
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
stopbits 1
line aux 0
stopbits 1
line vty 0 4
password lab
login
!
!
end