linux高阶-Nginx(七)-高级配置
文章目录
- 一.状态页
- 二.第三方模块
- 三.Nginx变量
- 四.自定义变量
- 五.自定义访问日志
- 5.1 自定义日志
- 5.2 自定义json格式日志
- 5.3 使用 Python 统计 json 格式日志
- 六.http配置
- 6.1 SSL配置项
- 6.2 使用自签名证书
- 6.3 nginx ssl证书示例
- 6.4 实现多域名 HTTPS
- 七.安全配置
- 7.1 隐藏nginx版本号
- 7.2 升级openssl版本
- 八.其他配置
- 8.1 nginx压缩功能
- 8.2 favicon.ico
一.状态页
- Nginx 状态页类似于 apache 和 php 使用的状态页面,基于ngx_http_auth_basic_module实现,在编译安装 nginx 的时候需要添加编译参数–with-http_stub_status_module,否则配置完成之后监测会是提⽰语法错误。
server {
server_name blog.bokebi.cn;
keepalive_requests 5;
keepalive_timeout 65 66;
location /status {
stub_status;
}
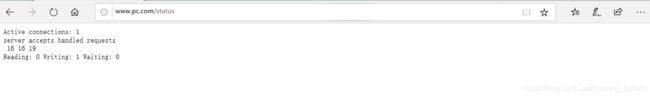
- 浏览器访问http://www.pc.com/status
- status页面说明
# 对齐一下是下面的样子
Active connections: 1
server accepts handled requests
16 16 19
Reading: 0 Writing: 1 Waiting: 0
ctive connections: 当前处于活动状态的客⼾端连接数,包括连接等待空闲连接数。
accepts:统计总值,Nginx⾃启动后已经接受的客⼾端请求的总数。
handled:统计总值,Nginx⾃启动后已经处理完成的客⼾端请求的总数,通常等于accepts,除⾮有因
worker_connections的值限制等被拒绝的连接。
requests:统计总值,Nginx⾃启动后客⼾端发来的总的请求数。
Reading:当前状态,正在读取客⼾端请求报⽂⾸部的连接的连接数。
Writing:当前状态,正在向客⼾端发送响应报⽂过程中的连接数。
Waiting:当前状态,正在等待客⼾端发出请求的空闲连接数,开启 keep-alive的情况下,这个值
Waiting = Active connections – (Reading+Writing). 此处 1=2-1
二.第三方模块
-
Nginx 支持扩展第三方模块,第三⽅模块需要在编译安装 Nginx 的时候使⽤参数–add-module=PATH指定路径添加,PATH是第三方模块的源码路径。有的模块是由公司的开发⼈员针对业务需求定制开发的,有的模块是开源爱好者开发好之后上传到 github 进⾏开源的模块,nginx ⽀持第三⽅模块需要从源码重新编译⽀持,⽐如开源的 echo 模块。
-
github上的echo模块: https://github.com/openresty/echo-nginx-module.
//进入源码包目录
cd /usr/local/src/
//下载echo源码包
git clone https://github.com/openresty/echo-nginx-module.git
//查看安装信息(复制之前安装信息)
/apps/nginx/sbin/nginx -V
//查看帮助,找到添加模块选项
./configure --help
//指定第三方模块的源码路径
./configure --prefix=/apps/nginx --user=nginx --group=nginx --with-httdule --with-http_stub_status_module --with-http_gzip_static_module --wealip_module --add-module=/usr/local/src/echo-nginx-module
//制作生成文件
make && make install
--------------------------
vim /apps/nginx/conf/nginx.conf
server {
server {
listen 80;
server_name localhost;
location / {
root html;
index index.html index.htm;
}
location /status {
stub_status;
}
location /main {
index index.html;
default_type text/html;
echo "Hello Nginx echo...";
echo_reset_timer;
echo_location /echo1;
echo_location /echo2;
echo "It took $echo_timer_elapsed secs to echo these words.";
}
location /echo1 {
echo _sleep 1;
echo This is echo1!!!;
}
location /echo2 {
echo _sleep 1;
echo This is echo2!!!ds;
}
}
---------------------------------------
curl 172.20.26.104/echo1
This is echo1
curl 172.20.26.104/echo2
This is echo2
curl 172.20.26.104/main
Hello Nginx echo...
This is echo1
This is echo2
It took 2.002 secs to echo these words.
三.Nginx变量
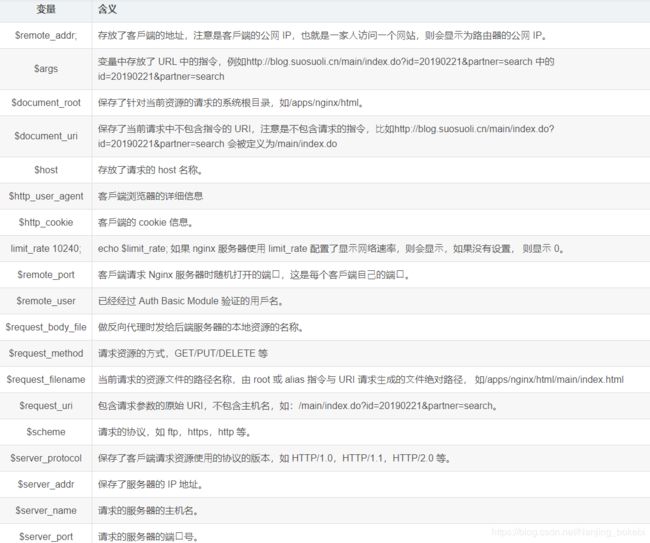
- nginx 的变量可以在配置⽂件中引⽤,作为功能判断或者⽇志等场景使⽤,变量可以分为内置变量和⾃定义变量,内置变量是由 nginx 模块⾃带,通过变量可以获取到众多的与
客⼾端访问相关的值。
vim /apps/nginx/conf/nginx.conf
server {
server {
listen 80;
server_name localhost;
location / {
root html;
index index.html index.htm;
}
location /status {
stub_status;
}
location /variables {
index index.html;
default_type text/html;
echo "remote_addr is : $remote_addr";
echo "args in URL are : $args";
echo "document root is : $document_root";
echo "document uri is : $document_uri";
echo "requested host is: $host";
echo "user agent is : $http_user_agent";
echo "cookies in agent : $http_cookie";
echo "the network speed: limit_rate";
echo "user agent random port: $remote_port";
echo "authed user is : $remote_user";
echo "to backend file : $request_body_file";
echo "request method : $request_method";
echo "requset file path: $request_filename"; # 如/apps/nginx/html/main/index.html
echo "not include host : $request_uri";
echo "protocol used : $scheme";
echo "spec protocol user agent used : $server_protocol";
echo "server address : $server_addr";
echo "server hostname : $server_name";
echo "requested server port : $server_port";
}
location /main {
index index.html;
default_type text/html;
echo "Hello Nginx echo...";
echo_reset_timer;
echo_location /echo1;
echo_location /echo2;
echo "It took $echo_timer_elapsed secs to echo these words.";
}
location /echo1 {
echo _sleep 1;
echo This is echo1!!!;
}
location /echo2 {
echo _sleep 1;
echo This is echo2!!!ds;
}
}
-----------------------------------------------
# 使用curl测试
root@ubuntu-bokebi-node1:/etc/nginx/conf.d# curl 172.20.26.104/variables
remote_addr is : 172.20.2.189
args in URL are :
document root is : /apps/nginx/html
document uri is : /variables
requested host is: 172.20.26.104
user agent is : curl/7.58.0
cookies in agent :
the network speed: limit_rate
user agent random port: 60513
authed user is :
to backend file :
request method : GET
requset file path: /apps/nginx/html/variables
not include host : /variables
protocol used : http
spec protocol user agent used : HTTP/1.1
server address : 172.20.26.104
server hostname : localhost
requested server port : 80
四.自定义变量
- Nginx 的变量支持自定义变量。假如需要⾃定义变量名称和值,使⽤指令
set $variable value;。具体⽅法如下:
Syntax: set $variable value; Default: — Context: server, location, if
set $name magedu;
echo $name;
set $my_port $server_port;
echo $my_port;
echo "$server_name:$server_port";
- 示例:
vim /apps/nginx/conf/nginx.conf
server {
listen 80;
server_name localhost;
location / {
root html;
index index.html index.htm;
}
location /status {
stub_status;
}
location /my_info {
index index.html;
default_type text/html;
set $my_name bokebi;
echo "My name is : $my_name";
set $my_profession DevOps;
echo "My profession is : $my_profession";
set $my_hobbies Linux;
echo "My hobbies are : $my_hobbies";
set $my_host $server_addr;
echo "I'm admin $my_host just for now.";
}
}
-----------------------------------------------------
curl 172.20.26.104/my_info
My name is : bokebi
My profession is : DevOps
My hobbies are : Linux
I'm admin 172.20.26.104 just for now.
五.自定义访问日志
5.1 自定义日志
-
access_log访问⽇志用来记录客⼾端的具体请求内容信息;error_log错误日志用在全局配置(http{…})块中指定服务器运行时的日志和记录的错误级别。
-
Nginx 的错误⽇志⼀般只有⼀个,但是访问⽇志可以在不同 server 中定义多个,定义⼀个⽇志需要使⽤ access_log 指定⽇志的保存路径,使⽤ log_format 指定⽇志的格式,格式中定义要保存的具体⽇志内容。
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
log_format customize_log '$remote_addr - $remote_user [$time_local] "$request" ';
access_log logs/access.log customize_log;
sendfile on;
tcp_nopush on;
keepalive_timeout 65 66;
server {
listen 80;
server_name localhost;
location / {
root html;
index index.html index.htm;
}
}
}
---------------------------------------
//访问验证
tail /apps/nginx/logs/access.log
172.20.26.4 - - [05/Jan/2020:20:14:44 +0800] "GET /my_info HTTP/1.1"
172.20.26.4 - - [05/Jan/2020:20:14:45 +0800] "GET /my_info HTTP/1.1"
172.20.26.14 - - [05/Jan/2020:20:14:55 +0800] "GET / HTTP/1.1"
172.20.26.14 - - [05/Jan/2020:20:15:00 +0800] "GET / HTTP/1.1"
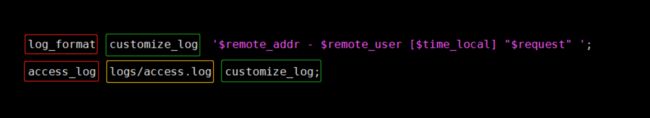
- 自定义日志如下图: 使用红色的指令指明定义日志格式和存放路径,使用绿色的框
写明自定义日志名称,黄色代表日志文件存储路径。
5.2 自定义json格式日志
- Nginx 的默认访问⽇志记录内容相对⽐较单⼀,默认的格式也不⽅便后期做⽇志统计分析,⽣产环境中通常将 nginx ⽇志转换为 json ⽇志,然后配合使⽤ ELK 等工具做⽇志收集-统计-分析。典型的配置如下:
log_format access_json '{"@timestamp":"$time_iso8601",'
'"host":"$server_addr",'
'"clientip":"$remote_addr",'
'"size":$body_bytes_sent,'
'"responsetime":$request_time,'
'"upstreamtime":"$upstream_response_time",'
'"upstreamhost":"$upstream_addr",'
'"http_host":"$host",'
'"uri":"$uri",'
'"domain":"$host",'
'"xff":"$http_x_forwarded_for",'
'"referer":"$http_referer",'
'"tcp_xff":"$proxy_protocol_addr",'
'"http_user_agent":"$http_user_agent",'
'"status":"$status"}';
access_log /apps/nginx/logs/access_json.log access_json;
vim /apps/nginx/conf/nginx.conf
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
#log_format customize_log '$remote_addr - $remote_user [$time_local] "$request" ';
#access_log logs/access.log customize_log;
log_format log_json '{"@timestamp":"$time_iso8601",'
'"host":"$server_addr",'
'"clientip":"$remote_addr",'
'"size":$body_bytes_sent,'
'"responsetime":$request_time,'
'"upstreamtime":"$upstream_response_time",'
'"upstreamhost":"$upstream_addr",'
'"http_host":"$host",'
'"uri":"$uri",'
'"domain":"$host",'
'"xff":"$http_x_forwarded_for",'
'"referer":"$http_referer",'
'"tcp_xff":"$proxy_protocol_addr",'
'"http_user_agent":"$http_user_agent",'
'"status":"$status"}';
access_log /apps/nginx/logs/access_json_log log_json;
sendfile on;
tcp_nopush on;
keepalive_timeout 65 66;
server {
listen 80;
server_name localhost;
location / {
root html;
index index.html index.htm;
}
}
}
# 访问测试
[root@node1 html]# tail /apps/nginx/logs/access_json_log -f
{"@timestamp":"2020-01-05T20:25:45+08:00","host":"172.20.26.104","clientip":"172.20.1.1","size":136,"responsetime":0.000,"upstreamtime":"-","upstreamhost":"-","http_host":"172.20.26.104","uri":"/my_info","domain":"172.20.26.104","xff":"-","referer":"-","tcp_xff":"","http_user_agent":"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.87 Safari/537.36","status":"200"}
{"@timestamp":"2020-01-05T20:25:49+08:00","host":"172.20.26.104","clientip":"172.20.1.1","size":136,"responsetime":0.000,"upstreamtime":"-","upstreamhost":"-","http_host":"172.20.26.104","uri":"/my_info","domain":"172.20.26.104","xff":"-","referer":"-","tcp_xff":"","http_user_agent":"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.87 Safari/537.36","status":"200"}
{"@timestamp":"2020-01-05T20:26:01+08:00","host":"172.20.26.104","clientip":"172.20.1.1","size":136,"responsetime":0.000,"upstreamtime":"-","upstreamhost":"-","http_host":"172.20.26.104","uri":"/my_info","domain":"172.20.26.104","xff":"-","referer":"-","tcp_xff":"","http_user_agent":"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.87 Safari/537.36","status":"200"}
{"@timestamp":"2020-01-05T20:26:07+08:00","host":"172.20.26.104","clientip":"172.20.2.189","size":612,"responsetime":0.000,"upstreamtime":"-","upstreamhost":"-","http_host":"172.20.26.104","uri":"/index.html","domain":"172.20.26.104","xff":"-","referer":"-","tcp_xff":"","http_user_agent":"curl/7.58.0","status":"200"}
{"@timestamp":"2020-01-05T20:26:13+08:00","host":"172.20.26.104","clientip":"172.20.2.189","size":612,"responsetime":0.000,"upstreamtime":"-","upstreamhost":"-","http_host":"172.20.26.104","uri":"/index.html","domain":"172.20.26.104","xff":"-","referer":"-","tcp_xff":"","http_user_agent":"curl/7.58.0","status":"200"}
{"@timestamp":"2020-01-05T20:26:13+08:00","host":"172.20.26.104","clientip":"172.20.2.189","size":612,"responsetime":0.000,"upstreamtime":"-","upstreamhost":"-","http_host":"172.20.26.104","uri":"/index.html","domain":"172.20.26.104","xff":"-","referer":"-","tcp_xff":"","http_user_agent":"curl/7.58.0","status":"200"}
{"@timestamp":"2020-01-05T20:26:38+08:00","host":"172.20.26.104","clientip":"172.20.1.1","size":555,"responsetime":0.000,"upstreamtime":"-","upstreamhost":"-","http_host":"172.20.26.104","uri":"/sdf","domain":"172.20.26.104","xff":"-","referer":"-","tcp_xff":"","http_user_agent":"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.87 Safari/537.36","status":"404"}
{"@timestamp":"2020-01-05T20:26:47+08:00","host":"172.20.26.104","clientip":"172.20.1.1","size":555,"responsetime":0.000,"upstreamtime":"-","upstreamhost":"-","http_host":"172.20.26.104","uri":"/devops.png","domain":"172.20.26.104","xff":"-","referer":"-","tcp_xff":"","http_user_agent":"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.87 Safari/537.36","status":"404"}
5.3 使用 Python 统计 json 格式日志
- 简单的处理程序
#! /usr/bin/env python
#coding:utf-8
status_200 = []
status_404 = []
with open("access_json_log") as log_data:
for line in log_data.readlines():
line = eval(line)
if line.get("status") == "200":
status_200.append(line.get)
elif line.get("status") == "404":
status_404.append(line.get)
else:
print("status ERROR")
log_data.close()
print(f'There are {len(status_200)} requests succeeded.')
print(f'There are {len(status_404)} requests for something not find.')
- 将日志文件和python处理程序放在/data目录下测试
ll /data
-rw-r--r-- 1 root root 2968 Jan 5 20:36 access_json_log
-rw-r--r-- 1 root root 624 Jan 5 20:37 log_analyses.py
python3 log_analyses.py
There are 6 requests succeeded.
There are 2 requests for something not find.
六.http配置
-
Web ⽹站的登录⻚⾯都是使⽤ https 加密传输的,加密数据以保障数据的安全,HTTPS 能够加密信息,以免敏感信息被第三⽅获取,所以很多银⾏⽹站或电⼦邮箱等等安全级别较⾼的服务都会采⽤ HTTPS 协议,HTTPS 其实是有两部分组成:HTTP + SSL / TLS,也就是在 HTTP 上⼜加了⼀层处理加密信息的模块。服务端和客⼾端的信息传输都会通过 TLS 进⾏加密,所以传输的数据都是加密后的数据。
-
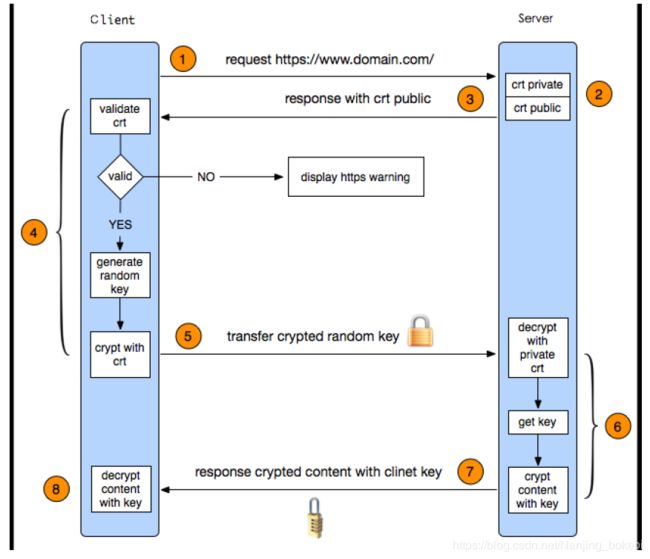
HTTPS协议加密原理如下图:
1.客⼾端发起HTTPS请求:
客⼾端访问某个web端的地址,⼀般都是URL+443端⼝。例如:https://www.bokebi.cn:443
由于https默认端口是443,所以直接访问:https://wwww.bokebi.cn就可以。
2.服务端的配置:
采⽤https协议的服务器必须要有⼀套证书,可以通过⼀些组织申请,也可以⾃⼰制作,
向证书颁发机构申请的证书需要交费用,这种证书是受信任的证书,可以用来实现
https。自己给自己颁发的证书不受信任,但是可以在局域网或者公司内部使用,只要
公司内部的电脑都被配置为信任该证书。
3.传送证书:
服务端给客⼾端传递证书,其实就是公钥,⾥⾯包含了很多信息,例如证书的颁发机构、
证书的过期时间等等。
4.客⼾端解析证书:
这部分⼯作是有客⼾端完成的,⾸先会验证公钥的有效性,⽐如颁发机构、过期时间等,
如果发现异常则会弹出⼀个警告框提⽰证书可能存在问题,如果服务器返回的公钥没有
问题就⽣成⼀个随机值,然后⽤公钥对该随机值进⾏加密,由于服务器的公钥加密的内
容只能使用服务器的私钥解密,所以在此时传输过程中就算有中间人截获该信息,其
也无能为力。
5.传送4步骤的加密数据:
就是将⽤证书加密后的随机值传递给服务器,⽬的就是为了让服务器得到这个随机值,以
后客⼾端和服务端的通信就可以通过这个随机值进⾏加密解密了。
6.服务端解密信息:
服务端⽤私钥解密5步骤加密后的随机值之后,得到了客⼾端传过来的随机值(私钥),然后
把内容通过该值进⾏对称加密,对称加密就是将信息和私钥通过算法混合在⼀起,这样除⾮
你知道私钥,不然是⽆法获取其内部的内容,⽽正好客⼾端和服务端都知道这个私钥,所以
只要机密算法够复杂就可以保证数据的安全性。
7.传输加密后的信息:
服务端将⽤私钥加密后的数据传递给客⼾端,在客⼾端可以被还原出原数据内容。
8.客⼾端解密信息:
客⼾端⽤之前⽣成的私钥获解密服务端传递过来的数据,由于数据⼀直是加密的,因此即使
第三⽅获取到数据也⽆法知道其详细内容。
6.1 SSL配置项
-
nginx 的 https 功能基于模块 ngx_http_ssl_module 实现,因此如果是编译安装的nginx 要使⽤参数 --with-http_ssl_module 开启 ssl 功能,但是作为 nginx 的核⼼功能,yum 安装的 nginx 默认就是开启的。
-
ngx_http_ssl_modeule 官⽅⽂档: https://nginx.org/en/docs/http/ngx_http_ssl_module.html
-
配置参数如下
ssl on | off;
# 为指定的虚拟主机配置是否启⽤ssl功能,此功能在1.15.0废弃,使⽤listen [ssl]替代。
ssl_certificate /path/to/file;
# 当前虚拟主机使⽤使⽤的公钥⽂件,⼀般是crt⽂件
ssl_certificate_key /path/to/file;
# 当前虚拟主机使⽤的私钥⽂件,⼀般是key⽂件
ssl_protocols [SSLv2] [SSLv3] [TLSv1] [TLSv1.1] [TLSv1.2];
# ⽀持ssl协议版本,早期为ssl,现在是TSL,默认为后三个
ssl_session_cache off | none | [builtin[:size]] [shared:name:size];
# 配置ssl缓存
off: 关闭缓存
none: 通知客⼾端⽀持ssl session cache,但实际不⽀持
builtin[:size]: 使⽤OpenSSL内建缓存,为每worker进程私有
[shared:name:size]: # 在各worker之间使⽤⼀个共享的缓存,需要定义⼀个缓存名称和缓存空间⼤⼩,
# 1MB 可以存储4000个会话信息,多个虚拟主机可以使⽤相同的缓存名称。
ssl_session_timeout time; # 客⼾端连接可以复⽤ssl session cache中缓存的有效时⻓,默认5m
6.2 使用自签名证书
//创建一个目录用于保存证书
mkdir /apps/nginx/certs
//进入目录
cd /apps/nginx/certs
//生成自签名CA证书
openssl req -newkey rsa:4096 -nodes -sha256 -keyout ca.key -x509 -days 3650 -out ca.crt
//生成私钥和证书申请请求文件
openssl req -newkey rsa:4096 -nodes -sha256 -keyout www.bokebi.cn.key -out www.bokebi.cn.csr
//ll
ca.crt
ca.key
www.bokebi.cn.csr
www.bokebi.cn.key
//给自己签发证书
openssl x509 -req -days 3650 -in www.bokebi.cn.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out www.bokebi.cn.crt
//查看签发的证书内容
openssl x509 -in www.bokebi.cn.crt -noout -text
# 通过查看该证书内容,可以看到Issuer(颁发者)和Subject(申请者)的信息几乎一样,
# 这就说明可该证书是自签名证书
6.3 nginx ssl证书示例
[root@node1 conf]# vim nginx.conf
http {
......
server {
server_name pc.bokebi.cn;
listen 80;
listen 443 ssl;
ssl_certificate /apps/nginx/certs/www.bokebi.cn.crt;
ssl_certificate_key /apps/nginx/certs/www.bokebi.cn.key;
ssl_session_cache shared:sslcache:20m;
ssl_session_timeout 10m;
location / {
root /apps/nginx/html/bokebi;
index index.html;
}
}
......
}
-
在 hosts 文件添加172.20.2.37 pc.bokebi.cn
-
访问https://pc.bokebi.cn,浏览器提示不安全,点击高级,继续访问该网站。
-
这是我的证书是不受浏览器信任的,是因为它找不到我的证书的颁发者。而实际上这个证书是我自己颁发的,浏览器当然找不到。所以是不受信任的。事实上受信任的证书都来自收信人的颁发机构,而几乎所有的操作系统都会提前把所有受信任的颁发机构预置到系统中,下图就是 windows 预置的受信任的证书颁发机构,包括顶级 CA、中级 CA 和一些第三方 CA。
-
按住windows+r键,在窗口输入certmgr.msc可调出下列窗口
6.4 实现多域名 HTTPS
- Nginx ⽀持基于单个 IP 实现多域名的功能,并且还⽀持单 IP 多域名的基础之上实现HTTPS,其实是基于 Nginx 的 SNI(Server Name Indication)功能实现,SNI 是为了解决⼀个 Nginx 服务器内使⽤⼀个 IP 绑定多个域名和证书的功能,其具体功能是客⼾端在连接到服务器建⽴ SSL 链接之前先发送要访问站点的域名(Hostname),这样服务器再根据这个域名返回给客⼾端⼀个合适的证书。
// 生成私钥和证书申请文件
openssl req -newkey rsa:4096 -nodes -sha256 -keyout www.bokebi.cn.key -out www.bokebi.cn.csr
//ll
ca.crt
ca.key
ca.srl
wap.bokebi.cn.key
wap.bokebi.cn.csr
www.bokebi.cn.crt
www.bokebi.cn.key
//签名证书
openssl x509 -req -days 3650 -in wap.bokebi.cn.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out wap.bokebi.cn.crt
//查看证书
openssl x509 -in wap.bokebi.cn.crt -noout -text
- 配置nginx
//创建存放页面文件目录
mkdir /apps/nginx/html/bokebi-wap
//创建实验页面
echo "This is a very nice mobile website." > bokebi-wap/index.html
//编辑相关配置文件
vim /apps/nginx/conf/nginx.conf
http {
include mime.types;
default_type application/octet-stream;
......
# pc virtual host #
server {
server_name pc.bokebi.cn;
listen 80;
listen 443 ssl;
ssl_certificate /apps/nginx/certs/www.bokebi.cn.crt;
ssl_certificate_key /apps/nginx/certs/www.bokebi.cn.key;
ssl_session_cache shared:sslcache:20m;
ssl_session_timeout 10m;
location / {
root /apps/nginx/html/bokebi;
index index.html;
}
}
# mobile virtual host #
server {
server_name wap.bokebi.cn;
listen 80;
listen 443 ssl;
ssl_certificate /apps/nginx/certs/wap.bokebi.cn.crt;
ssl_certificate_key /apps/nginx/certs/wap.bokebi.cn.key;
ssl_session_cache shared:sslcache:20m;
ssl_session_timeout 10m;
location / {
root /apps/nginx/html/bokebi-wap;
index index.html;
}
}
......
}
七.安全配置
7.1 隐藏nginx版本号
- 通过修改源码的某些变量值,可以自定义一些信息,其中 Nginx 版本就可以通过修改源码来变更,让外界无法知晓网站用的是什么服务。
vim nginx-1.16.1/src/http/ngx_http_header_filter_module.c
......
47
48
49 static u_char ngx_http_server_string[] = "Server: nginx" CRLF;
50 static u_char ngx_http_server_full_string[] = "Server: " NGINX_VER CRLF;
51 static u_char ngx_http_server_build_string[] = "Server: " NGINX_VER_BUILD CRLF;
52
......
# 将无符号字符串static u_char ngx_http_server_string[] 改为自己想改的字符串,比如
49 static u_char ngx_http_server_string[] = "Server: bokebi-engine/1.0" CRLF;
# 再编译安装,就可以在浏览器的调试面板看到响应信息。如:
Server: bokebi-engine/1.0
7.2 升级openssl版本
- ⼼脏出⾎(英语:Heartbleed),也简称为⼼⾎漏洞,是⼀个出现在加密程序库OpenSSL 的安全漏洞,该程序库⼴泛⽤于实现互联⽹的传输层安全(TLS)协议。它于 2012 年被引⼊了软件中,2014 年 4 ⽉⾸次向公众披露。只要使⽤的是存在缺陷的 OpenSSL 实例,⽆论是服务器还是客⼾端,都可能因此⽽受到攻击。此问题的原因是在实现 TLS 的⼼跳扩展时没有对输⼊进⾏适当验证(缺少边界检查),因此漏洞的名称来源于“⼼跳”(heartbeat)。该程序错误属于缓冲区过读,即可以读取的数据⽐应该允许读取的还多。
准备OpenSSL源码包:
# pwd
/usr/local/src
# tar xvf openssl-1.1.1d
编译安装Nginx并制定新版本OpenSSL路径:
# cd /usr/local/src/nginx-1.16.1/
#./configure \
--prefix=/apps/nginx --user=nginx --group=nginx --with-http_ssl_module \
--with-http_v2_module --with-http_realip_module --with-http_stub_status_module \ --with-http_gzip_static_module --with-pcre --with-stream \
--with-stream_ssl_module --with-stream_realip_module \
--with-select_module --with-file-aio \
--add-module=/usr/local/src/echo-nginx-module \
--with-openssl=/usr/local/src/openssl-1.1.1d
# make && make install
验证并启动Nginx:
# /apps/nginx/sbin/nginx -t
nginx: the configuration file /apps/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /apps/nginx/conf/nginx.conf test is successful
# /apps/nginx/sbin/nginx
八.其他配置
8.1 nginx压缩功能
-
Nginx ⽀持对指定类型的⽂件进⾏压缩然后再传输给客⼾端,⽽且压缩还可以设置压缩⽐例,压缩后的⽂件⼤⼩将⽐源⽂件显著变⼩,这样有助于降低出⼝带宽的利⽤率,降低企业的 IT ⽀出,不过会占⽤相应的 CPU 资源。Nginx 对⽂件的压缩功能是依赖于模块ngx_http_gzip_module
-
官⽅⽂档: https://nginx.org/en/docs/http/ngx_http_gzip_module.html
-
配置指令如下:
#启⽤或禁⽤gzip压缩,默认关闭
gzip on | off;
#压缩⽐由低到⾼从1到9,默认为1
gzip_comp_level level;
#禁⽤IE6 gzip功能
gzip_disable "MSIE [1-6]\.";
#gzip压缩的最⼩⽂件,⼩于设置值的⽂件将不会压缩
gzip_min_length 1k;
#启⽤压缩功能时,协议的最⼩版本,默认HTTP/1.1
gzip_http_version 1.0 | 1.1;
#指定Nginx服务需要向服务器申请的缓存空间的个数*⼤⼩,默认32 4k|16 8k;
gzip_buffers number size;
#指明仅对哪些类型的资源执⾏压缩操作;默认为gzip_types text/html,不⽤显⽰指定,否则出错
gzip_types mime-type ...;
#如果启⽤压缩,是否在响应报⽂⾸部插⼊“Vary: Accept-Encoding”
gzip_vary on | off;
8.2 favicon.ico
-
favicon.ico ⽂件是浏览器收藏⽹址时显⽰的图标,也就是在每个浏览器的调板上显示的图标。当客⼾端使⽤浏览器问⻚⾯时,浏览器会⾃⼰主动发起请求获取⻚⾯的 favicon.ico ⽂件,但是当浏览器请求的 favicon.ico ⽂件不存在时,服务器会记录 404 ⽇志,⽽且浏览器也会显⽰ 404 报错。
-
一般可以准备一个图标文件,并进行如下配置
#⼀:服务器不记录访问⽇志:
#location = /favicon.ico {
#log_not_found off;
#access_log off;
#}
#⼆:将图标保存到指定⽬录访问:
#location ~ ^/favicon\.ico$ {
location = /favicon.ico {
root /data/nginx/html/bokebi/images;
expires 90d; #设置⽂件过期时间
}