Linux系统之防火墙(iptables)
注意:firewalld和iptables不能同时打开,一定要关闭firewalld,再打开iptables,不然会对下面的实验有影响
防火墙的工作机制(三表五链)
链: 链就是位置,共有五个 : 数据包进路由之前(PREROUTING)、目的地址为本机,进系统(INPUT) 、转发(FORWARD)、原地址为本机,向外发送,出系统(OUTPUT)、发送到网卡之前,出路由(POSTROUTING); 数据包到了该链处,会去对应表中查询设置的规则,然后决定是否放行、丢弃、转发还是修改等等操作。每个链都是一个规则列表,对对应的包进行匹配。
表:具有相同功能的规则的集合叫做表。filter表:负责过滤功能,经过内核的; nat表:网络地址转换,不经过内核的 ,实现数据包转发,修改源地址 端口 目标地址 端口,实现地址转换;mangle表:拆解报文,作出修改,封装报文;raw表: 关闭nat表上启用的链接追踪机制。
表链关系: 我们所有自定义的规则都是这四种分类中的规则,或者说,所有的规则都存在于这4张表中。
filter表格:放的是经过内核的ip input output forward
nat表格:放的不是经过内核的服务 input output postrouting prerouting
备用表格mangle: input output forward postrouting prerouting
iptables的参数
| 含义 | 参数 |
|---|---|
| 不作解析 | iptables -t |
| 列出指定表中的策略 | iptables -L |
| 增加策略 | iptables -A |
| 网络协议 | iptables -P |
| 端口 | iptables –dport |
| 数据来源 | iptables -s |
| 动作:ACCEPT允许;REJECT拒绝;DROP丢弃 | iptables -j |
| 增加链 | iptables -N |
| 修改链名称 | iptables -E |
| 删除链 | iptables -X |
| 删除指定策略 | iptables -D |
| 插入 | iptables -I |
| 修改策略 | iptables -R |
| 修改默认策略 | iptables -P |
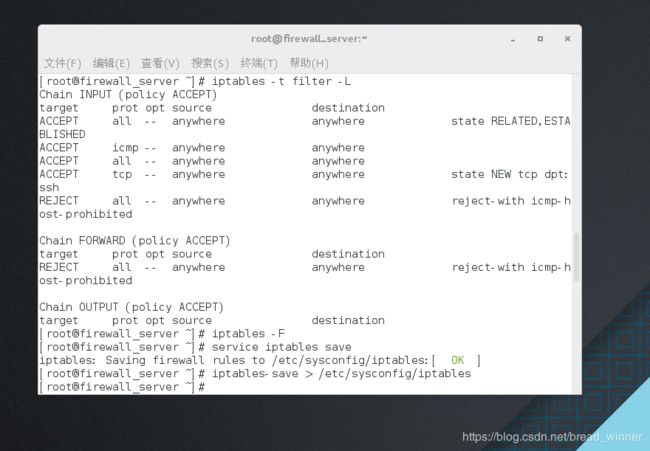
##不作解析 查看filter表格里面的链( 不跟-t,默认为filter表格)——iptables -t filter -nL
[root@firewall_server ~]# systemctl stop firewalld.service
[root@firewall_server ~]# systemctl start iptables.service
[root@firewall_server ~]# iptables -t filter -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
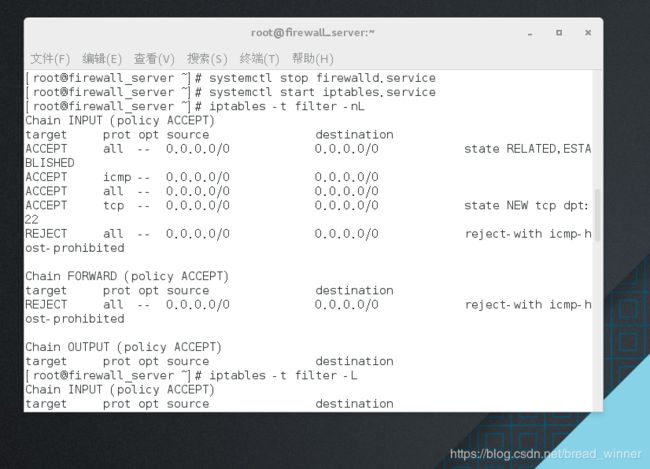
##作解析** 查看filter表格里面的链——iptables -t filter - L
[root@firewall_server ~]# iptables -t filter -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT icmp -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
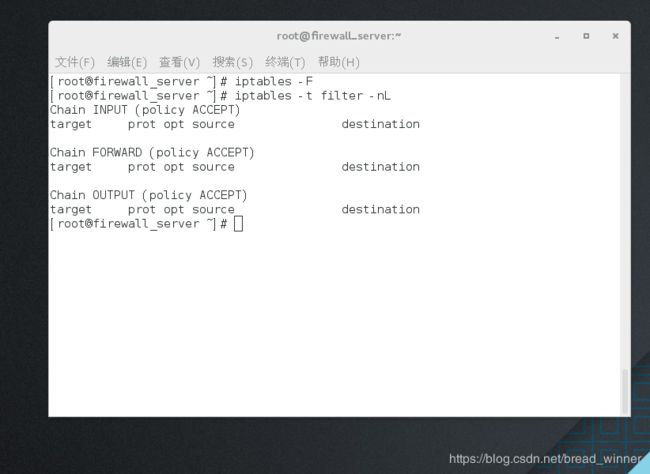
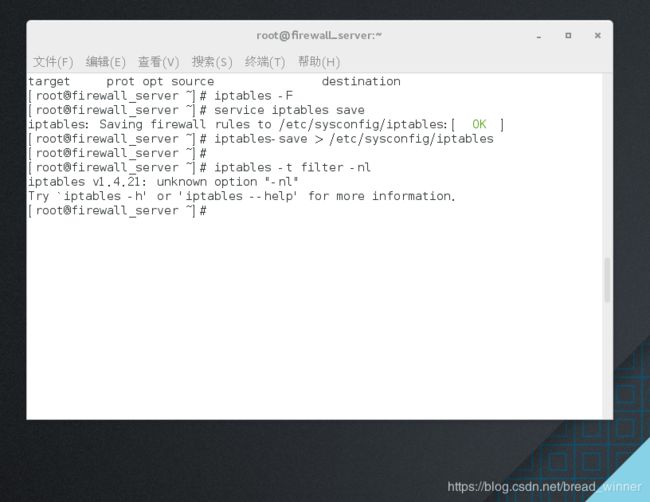
##清除所有策略——iptables -F
[root@firewall_server ~]# iptables -F
[root@firewall_server ~]# iptables -t filter -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
保存策略——service iptables save 和iptables-save > /etc/sysconfig/iptables
[root@firewall_server ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
[root@firewall_server ~]# iptables-save > /etc/sysconfig/iptables
[root@firewall_server ~]#
[root@firewall_server ~]# iptables -t filter -nl
iptables v1.4.21: unknown option “-nl”
Try `iptables -h’ or ‘iptables --help’ for more information.
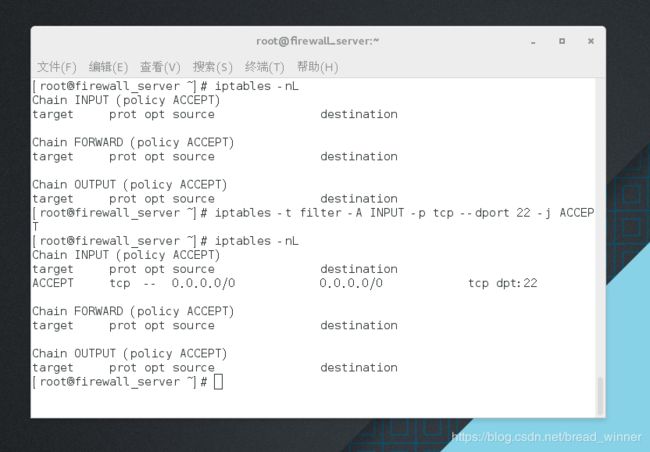
##接受所有访问22端口的—— iptables -t filter -A INPUT -p tcp --dport 22 -j ACCEPT
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@firewall_server ~]# iptables -t filter -A INPUT -p tcp --dport 22 -j ACCEPT
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
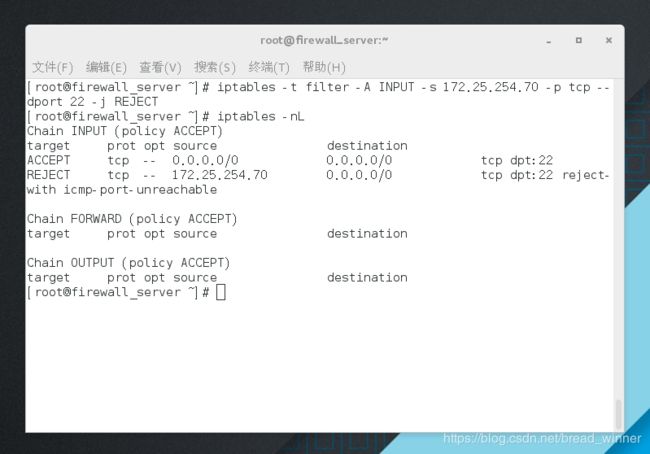
##拒绝172.25.254.70 访问22端口——iptables -t filter -A INPUT -s 172.25.254.70 -p tcp --dport 22 -j REJECT
[root@firewall_server ~]# iptables -t filter -A INPUT -s 172.25.254.70 -p tcp --dport 22 -j REJECT
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
REJECT tcp -- 172.25.254.70 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
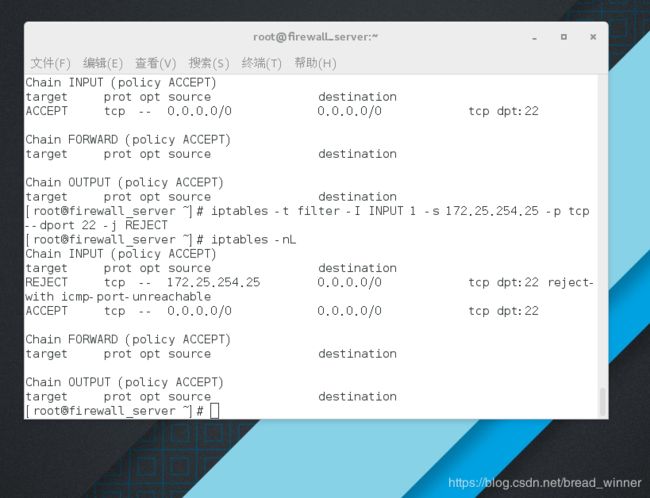
测试:发现策略未成功,因为 防火墙匹配从上往下读取策略,匹配之后就执行,不再读取。
解决办法:插入策略默认插入到第一条——iptables -t filter -I INPUT 1 -s 172.25.254.25 -p tcp --dport 22 -j REJECT
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
REJECT tcp -- 172.25.254.70 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@firewall_server ~]# iptables -D INPUT 2
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@firewall_server ~]# iptables -t filter -I INPUT 1 -s 172.25.254.70 -p tcp --dport 22 -j REJECT
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 172.25.254.70 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@firewall_server ~]# iptables-save > /etc/sysconfig/iptables
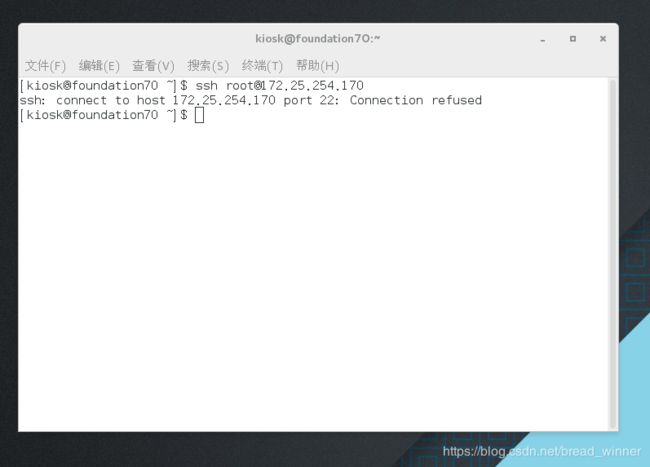
测试:发现此时有错误提示
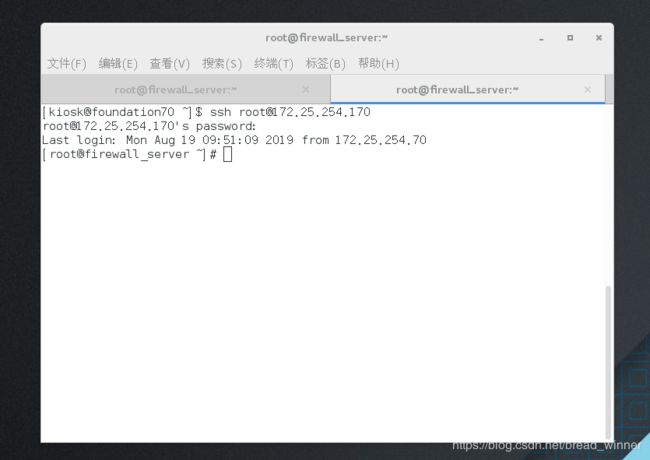
[kiosk@foundation70 ~]$ ssh [email protected]
ssh: connect to host 172.25.254.170 port 22: Connection refused
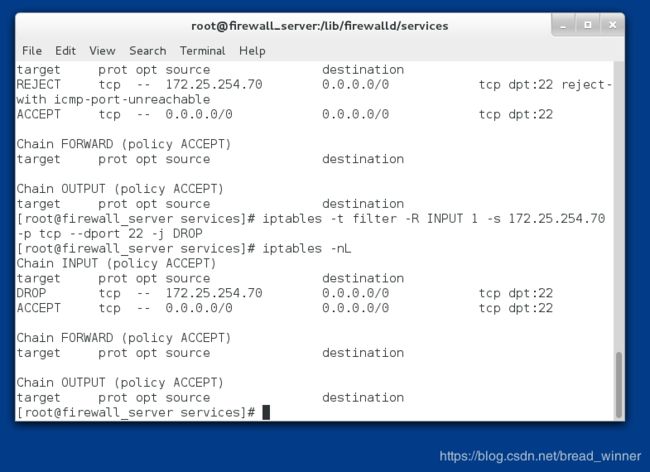
##修改策略的动作 REJECT–> DROP 从有拒绝提示到没有提示——iptables -t filter -R INPUT 1 -s 172.25.254.25 -p tcp --dport 22 -j DROP
[root@firewall_server services]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 172.25.254.70 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@firewall_server services]# iptables -t filter -R INPUT 1 -s 172.25.254.70 -p tcp --dport 22 -j DROP
[root@firewall_server services]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 172.25.254.70 0.0.0.0/0 tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
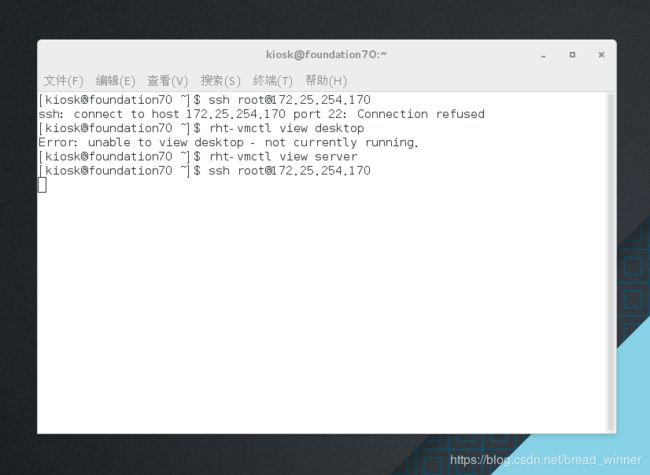
测试:拒绝后没有回显
[kiosk@foundation70 ~]$ ssh [email protected]
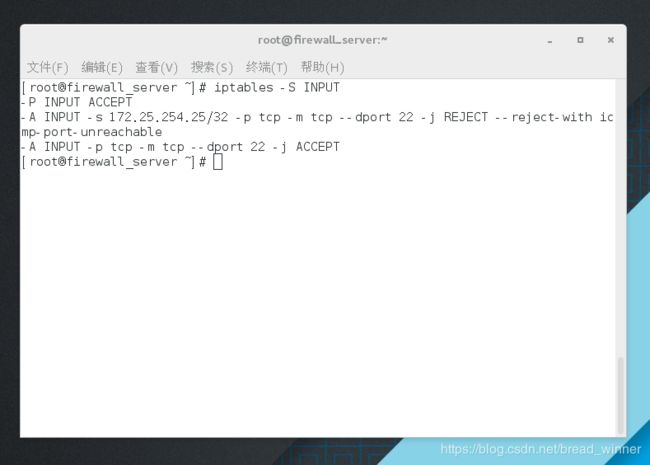
##显示所有已添加策略——iptables -S INPU
[root@firewall_server ~]# iptables -S INPUT
-P INPUT ACCEPT
-A INPUT -s 172.25.254.25/32 -p tcp -m tcp --dport 22 -j REJECT --reject-with icmp-port-unreachable
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
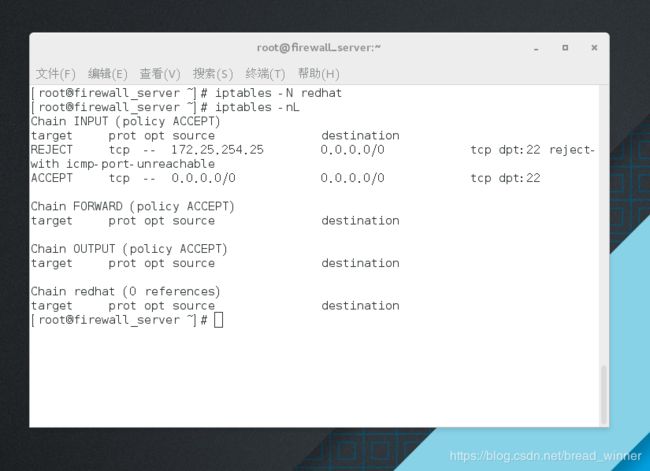
[root@firewall_server ~]# iptables -N redhat
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 172.25.254.25 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain redhat (0 references)
target prot opt source destination
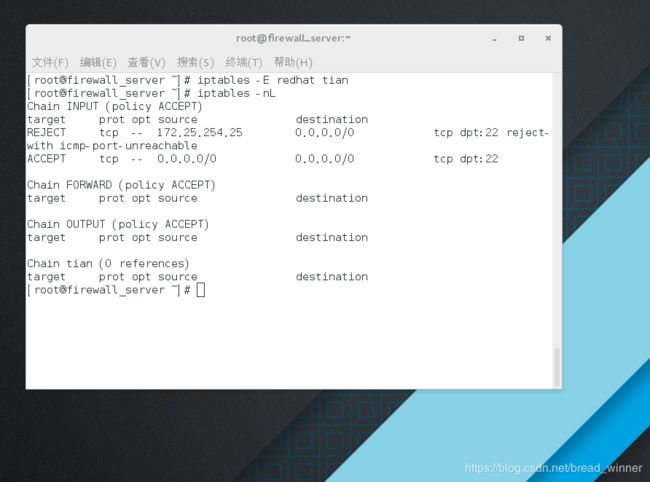
##修改链的名称———— iptables -E redhat RANRAN
[root@firewall_server ~]# iptables -E redhat tian
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 172.25.254.25 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain tian (0 references)
target prot opt source destination
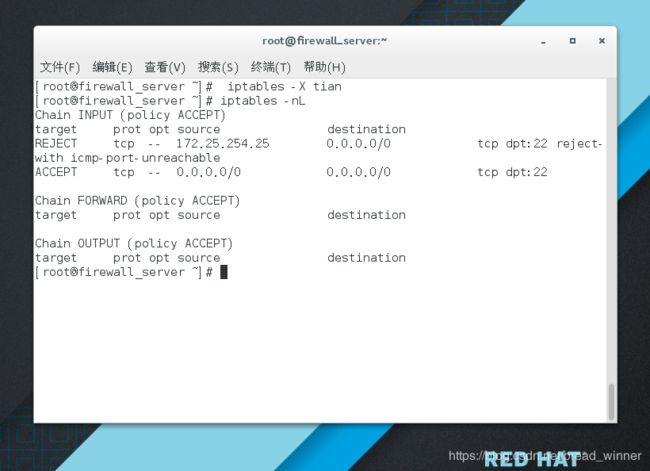
##删除链—— iptables -X RANRAN
[root@firewall_server ~]# iptables -X tian
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 172.25.254.25 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
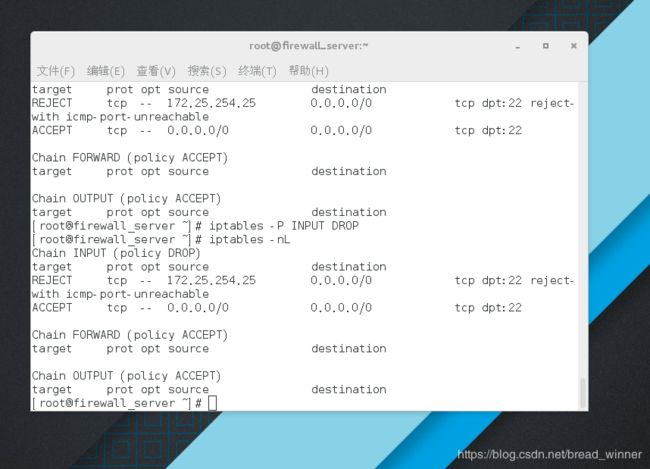
##修改链的默认策略——iptables -P INPUT DROP
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 172.25.254.25 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@firewall_server ~]# iptables -P INPUT DROP
[root@firewall_server ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
REJECT tcp -- 172.25.254.25 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
默认策略只可以修改为DROP和ACCET
iptables的地址伪装
实验环境:
server虚拟机双网卡:172.25.254.170和192.168.0.170
desktop虚拟机单网卡:196.168.0.70
物理机:172.25.254.70
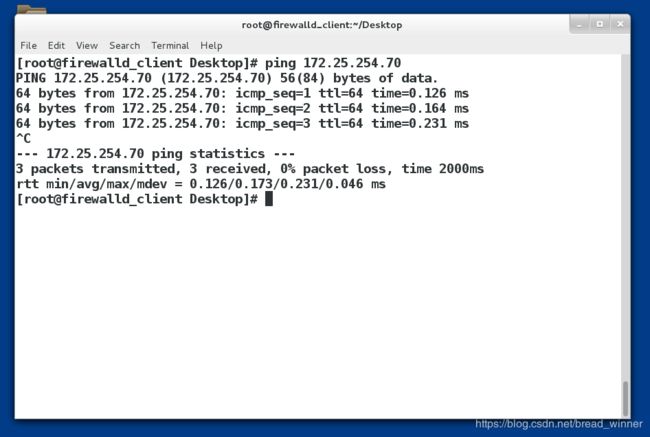
实验目的:通过iptables的地址伪装使desktop的196.168.0.70ping通172.25.254.170和172.25.254.70
开启地址伪装功能——iptables -t nat -A POSTROUTING -o(output) eth0 -j SNAT --to-source ip
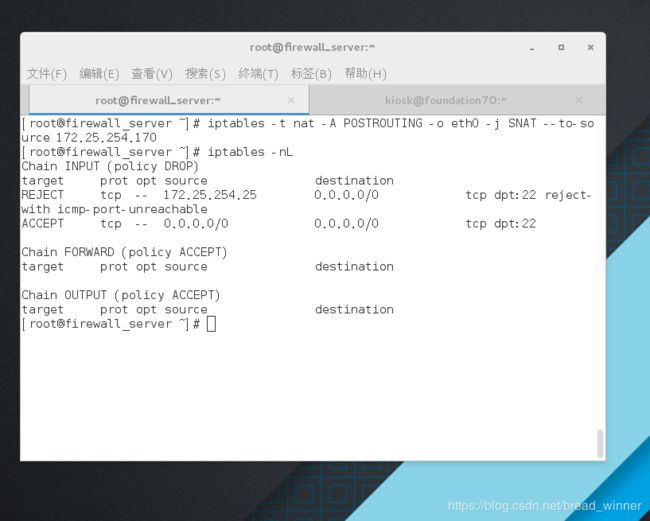
测试:
在desktop196.168.0.70上面(需要设置网关192.168.0.170)
端口转发(DNAT)
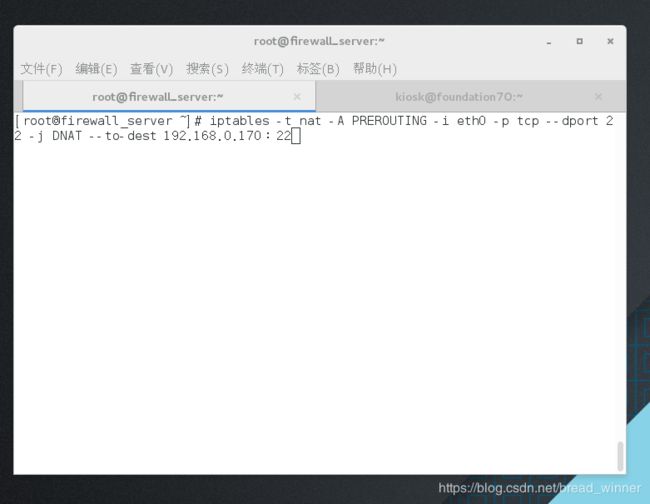
实验目的:真机172.25.254.70 ssh [email protected]直接连上192.168.0.170server
##添加地址转发功能,从172.25.254.170的22端口进入的都转到192.168.0.170的22端口上去——iptables -t nat -A PREROUTING -i(input) eth0 -p tcp --dport 22 -j DNAT --to-dest 192.168.0.170:22
[root@firewall_server ~]# iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 22 -j DNAT --to-dest 192.168.0.170:22
测试:在真机上面 ,连接172.25.254.170desktop ssh [email protected]
ifconfig 发现是server192.168.0.170 , 实现了地址转发的功能
[kiosk@foundation70 ~]$ ssh [email protected]
[email protected]'s password:
Last login: Mon Aug 19 10:32:05 2019 from 172.25.254.70
[root@server ~]# ifconfig eth0
eth0: flags=4163 mtu 1500
inet 192.168.0.170 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::5054:ff:fe18:f07 prefixlen 64 scopeid 0x20
ether 52:54:00:18:0f:07 txqueuelen 1000 (Ethernet)
RX packets 2788 bytes 290238 (283.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4181 bytes 355695 (347.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
设置只允许httpd、sshd、squid服务通过的防火墙策略
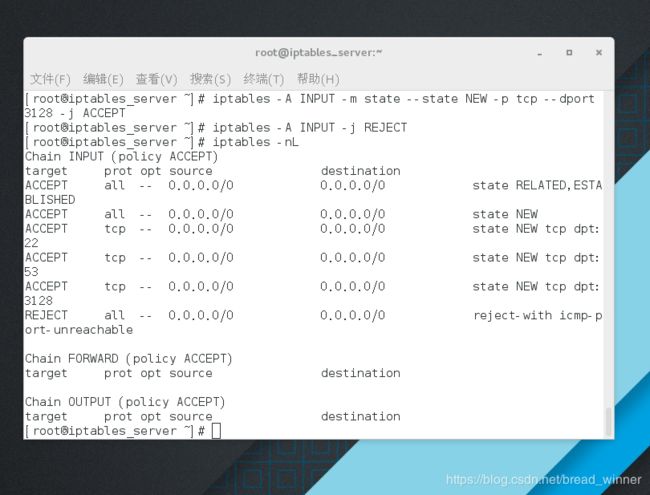
[root@iptables_server ~]# iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
[root@iptables_server ~]# iptables -A INPUT -m state --state NEW -I lo -j ACCEPT
iptables v1.4.21: Cannot use -I with -A
Try `iptables -h' or 'iptables --help' for more information.
[root@iptables_server ~]# iptables -A INPUT -m state --state NEW -i lo -j ACCEPT
[root@iptables_server ~]# iptables -A INPUT -m state --state NEW -p tcp --dport 22 -j ACCEPT
[root@iptables_server ~]# iptables -A INPUT -m state --state NEW -p tcp --dport 53 -j ACCEPT
[root@iptables_server ~]# iptables -A INPUT -m state --state NEW -p tcp --dport 3128 -j ACCEPT
[root@iptables_server ~]# iptables -A INPUT -j REJECT
[root@iptables_server ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state NEW
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:53
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:3128
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination