DNS配置文件及区域文件
修改主配置文件
[root@school named]# vim /etc/named.conf
options {
// listen-on port 53 { 127.0.0.1; };
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
// dump-file "/var/named/data/cache_dump.db";
// statistics-file "/var/named/data/named_stats.txt";
// memstatistics-file "/var/named/data/named_mem_stats.txt";
// allow-query { localhost; };
recursion yes;
// dnssec-enable yes;
// dnssec-validation yes;
// dnssec-lookaside auto;
// /* Path to ISC DLV key */
// bindkeys-file "/etc/named.iscdlv.key";
//
};
include "/etc/named.rfc1912.zones";
//include "/etc/named.root.key";定义区域
[root@school named]# vim /etc/named.rfc1912.zones
zone "sky.com" IN {
type master;
file "sky.com.zone";
allow-transfer { 192.168.0.10; };
};
zone "0.168.192.in-addr.arpa." IN {
type master;
file "192.168.0.zone";
allow-transfer { 192.168.0.10; };
};添加正向区域解析库
[root@school named]# vim /var/named/sky.com.zone
$TTL 86400
@ IN SOA ns.sky.com. admin.sky.com. (
2015072401
2H
10M
3D
1D )
@ IN NS ns
@ IN NS ns1
ns IN A 192.168.0.9
ns1 IN A 192.168.0.10
www IN A 192.168.0.9
ftp IN A 192.168.0.20添加反向区域解析库
[root@school named]# vim /var/named/192.168.0.zone
$TTL 86400
@ IN SOA ns.sky.com. admin.sky.com. (
2015072401
2H
10M
3D
1D )
@ IN NS ns.sky.com.
@ IN NS ns1.sky.com.
9 IN PTR ns.sky.com.
10 IN PTR ns1.sky.com.
9 IN PTR www.sky.com.
20 IN PTR ftp.sky.com.改属主属组
[root@school named]# chgrp named sky.com.zone 192.168.0.zone
[root@school named]# chmod 640 sky.com.zone 192.168.0.zone配置文件语法检查
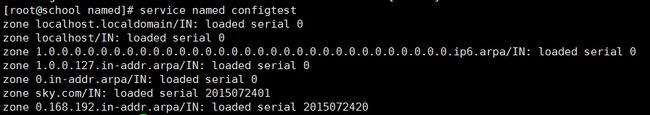
[root@school named]# named-checkconf区域语法检查
[root@school named]# named-checkzone "sky.com" sky.com.zone
[root@school named]# named-checkzone "0.168.192.in-addr.arpa" 192.168.0.zone重启
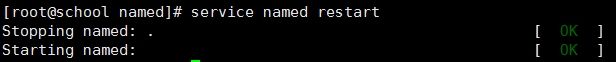
[root@school named]# service named restart
Stopping named: . [ OK ]
Starting named: [ OK ]如无自己主机端口,则是主配置文件没有注释端口
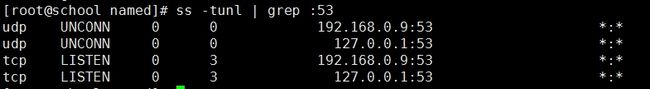
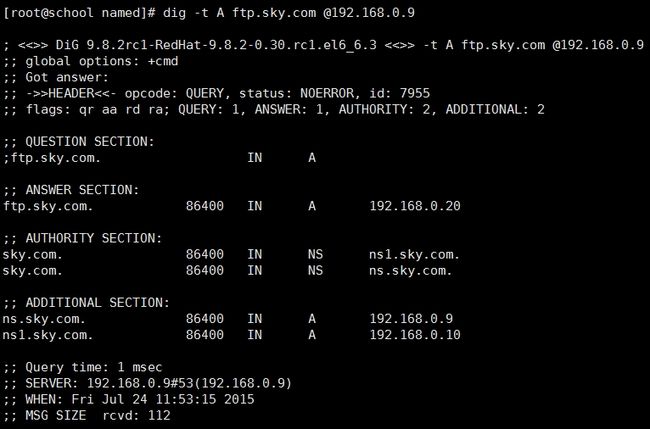
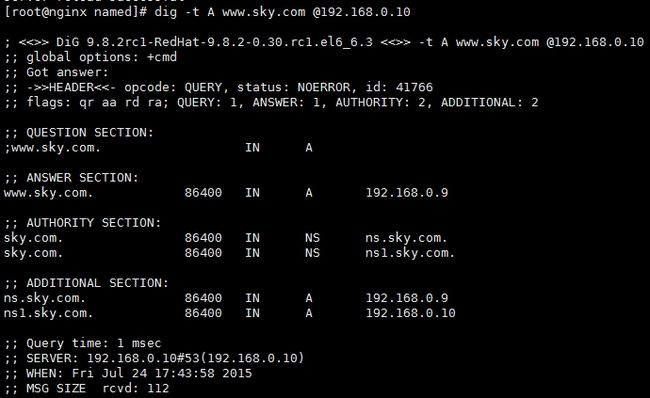
正向测试
反向测试
主从复制
前提:
1、时间同步
2、bind版本差异
二者相同
不同时从服务器应该比主服务器版本高
实验:主DNS为192.168.0.9,从DNS为192.168.0.10,要求:只允许从服务器来传输区域文件。
主服务器配置文件定义区域并限定传送
1、在主服务器配置文件中添加允许从服务器传送,在主服务器正反向解析文件中添加从服务器
[root@school named]# vim /etc/named.rfc1912.zones
zone "sky.com" IN {
type master;
file "sky.com.zone";
allow-transfer { 192.168.0.10; }; #允许从服务同步
};
zone "0.168.192.in-addr.arpa." IN {
type master;
file "192.168.0.zone";
allow-transfer { 192.168.0.10; }; #允许从服务同步
};
[root@school named]# vim /var/named/sky.com.zone
$TTL 86400
@ IN SOA ns.sky.com. admin.sky.com. (
2015072401
2H
10M
3D
1D )
@ IN NS ns
@ IN NS ns1 #添加从服务器
ns IN A 192.168.0.9
ns1 IN A 192.168.0.10 #添加从服务器地址
www IN A 192.168.0.9
ftp IN A 192.168.0.20
[root@school named]# vim /var/named/192.168.0.zone
$TTL 86400
@ IN SOA ns.sky.com. admin.sky.com. (
2015072401
2H
10M
3D
1D )
@ IN NS ns.sky.com.
@ IN NS ns1.sky.com. #添加从服务器
9 IN PTR ns.sky.com.
10 IN PTR ns1.sky.com. #添加从服务器地址
9 IN PTR www.sky.com.
20 IN PTR ftp.sky.com.语法检查、重启
定义从服务器的区域文件
[root@nginx ~]# vim /etc/named.rfc1912.zones
zone "sky.com" IN {
type slave;
masters { 192.168.0.9; };
file "slaves/sky.com.zone";
};
zone "0.168.192.in-addr.arpa" IN {
type slave;
masters { 192.168.0.9; };
file "slaves/192.168.0.zone";
};语法检查
重启
查看端口
查看文件
在从服务器上测试
正向
反向
子域授权和转发
正向子域授权:只需要在父域的区域解析库中添加“胶水记录”即可
例如:
子域名称 IN NS 子域的名称服务器
ops IN NS ns.ops
dev IN NS ns.dev
ns.ops IN A 192.168.0.5
ns.dev IN A 192.168.0.6flags:aa权威答案
配置转发器:转发所有的非本机负责的区域的请求至某指定的DNS服务器
options{
…
forward only|first;
forwarders { ip; };
}
only:只使用forwarders DNS服务器做域名解析,如果查询不到则返回查询失败。
first:优先使用forwarders DNS服务器做域名解析,如果查询不到再使用本地DNS服务器做域名解析访问控制
allow-transfer{};#传输白名单
allow-query{}; #查询白名单
allow-update{}; #更新白名单,一般为none
allow-recursion{};#递归白名单
recursionyes;#一般不用这个配置转发区域:转发本区域解析不到的请求至某指定的DNS服务器,而非根
zone "" IN {
type forward;
forward only|first;
forwarders { ip;ip; };
};bind acl:内置的acl:none,any,local,localnet(本机所在网络)
自定义acl,在options上面写
acl acl_name {
ip;
ip;
ip;
network;
};
例如:
acl localnetwork {
网络;
网络;
};实验:父域服务器:192.168.0.9,子域服务器:192.168.0.10,子域:ops.sky.com。要求子域授权,子域可以使用,子域查询不到向父域请求,父域解析不了,返回失败。
在父域正向解析文件添加胶水记录
[root@school named]# vim sky.com.zone
ops IN NS ns.ops
ns.ops IN A 192.168.0.10#子域可在不同网父域检查语法
子服务器添加子域和转发域
转发器
在/etc/named.conf的options里添加转发器
forward only;
forwarders { 192.168.0.9; };转发域
[root@nginx ~]# vim /etc/named.rfc1912.zones
zone "ops.sky.com" {
type master;
file "ops.sky.com.zone";
};
zone "sky.com" {
type forward;
forward only;
forwarders { 192.168.0.9; };
};[root@nginx named]# vim ops.sky.com.zone
$TTL 3600
$ORIGIN ops.sky.com.
@ IN SOA ns.ops.sky.com. admin.ops.sky.com. (
2015072401
1H
10M
1D
1D )
IN NS ns
ns IN A 192.168.0.10
www IN A 192.168.0.90
ftp IN A 192.168.0.95
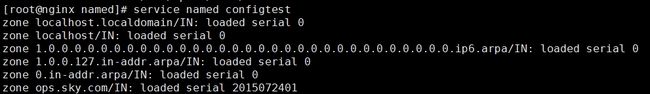
pop IN A 192.168.0.100检查配置文件语法
![]()
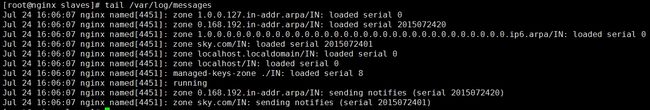
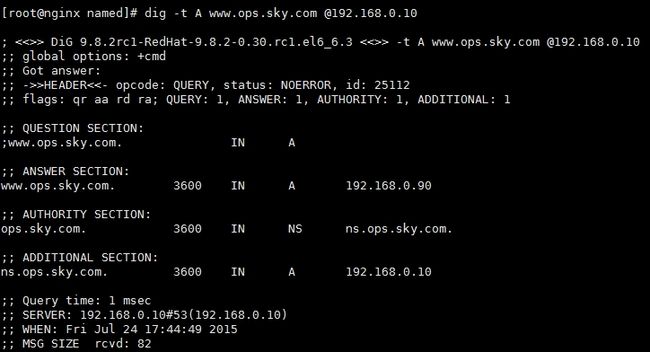
测试子域自己解析
测试转发
视图
功能:根据客户端来源的不同,将同一个名称解析至不同的值
viewview_name {
match-clients {};
zone{
};
};各zone都必须放在view,view可以定义多个
格式:
acl telecom {
};
acl unicom {
};
view telecom {
match-clients { telecom; };
zone "sky.com" IN {
type master;
file "sky.com.zone.tel";
};
};
view unicom {
match-clients { unicom; };
zone "sky.com" IN {
type master;
file "sky.com.zone.uni";
};
};view注意事项:
1、通常只为内网客户端提供递归功能,提供根区域
2、通常只为外网客户端提供本机所负责的区域的解析
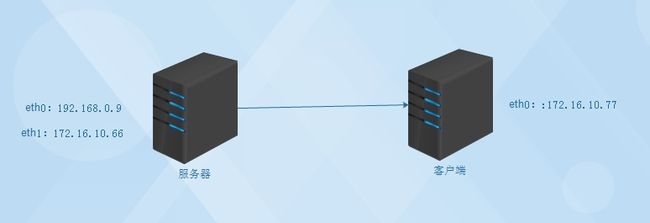
服务器端:192.168.0.9和172.16.10.66
客户端:172.16.10.77
拓扑图如下
 客户端需打开网卡转发功能:vim /etc/sysctl.conf,设置net.ipv4.ip_forward = 1
客户端需打开网卡转发功能:vim /etc/sysctl.conf,设置net.ipv4.ip_forward = 1
服务器eth1不设置网关,客户端网关指向172.16.10.66即可
服务器端设置:
view internal {
recursion yes;
match-clients { 192.168.0.0/24; };
zone "." IN {
type hint;
file "named.ca";
};
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
zone "sky.com" IN {
type master;
file "sky.com.int";
allow-transfer { 192.168.0.10; };
};
zone "0.168.192.in-addr.arpa" IN {
type master;
file "192.168.0.zone";
allow-transfer { 192.168.0.10; };
};
};
view external {
recursion no;
match-clients { 172.16.0.0/16; };
zone "sky.com" IN {
type master;
file "sky.com.ext";
};
};创建内部正向解析文件
[root@school named]# vim sky.com.int
$TTL 86400
$ORIGIN sky.com.
@ IN SOA ns.sky.com. admin.sky.com. (
2015072460
2H
10M
3D
1D )
@ IN NS ns
ns IN A 192.168.0.9
www IN A 192.168.0.20
ftp IN A 192.168.0.2创建外部反向解析文件
[root@school named]# vim sky.com.ext
$TTL 86400
$ORIGIN sky.com.
@ IN SOA ns.sky.com. admin.sky.com. (
2015072460
2H
10M
3D
1D )
@ IN NS ns
ns IN A 192.168.0.9
www IN A 172.16.10.20
ftp IN A 172.16.10.2更改属主属组和权限
[root@school named]# chgrp named sky.com.int sky.com.ext
[root@school named]# chmod 640 sky.com.int sky.com.ext语法检查
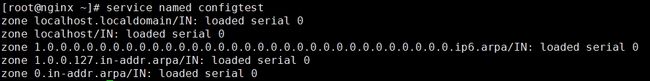
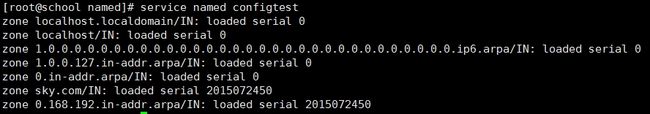
[root@school named]# service named configtest
zone localhost.localdomain/IN: loaded serial 0
zone localhost/IN: loaded serial 0
zone 1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa/IN: loaded serial 0
zone 1.0.0.127.in-addr.arpa/IN: loaded serial 0
zone 0.in-addr.arpa/IN: loaded serial 0
zone sky.com/IN: loaded serial 2015072450
zone 0.168.192.in-addr.arpa/IN: loaded serial 2015072450
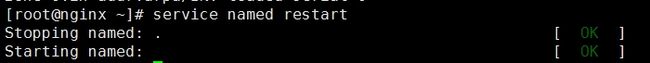
zone sky.com/IN: loaded serial 2015072450重启
[root@school named]# rndc reload
server reload successful测试