Linux网络----配置DNS服务(正向解析)并使用HTTP访问
文章目录
- 实验环境
- DNS正向解析实验
- 配置主配置文件
- 配置区域文件
- 配置区域数据文件
- 打开一台windows 10进行验证
实验环境
两台cenTOs 7.6
一台windows 10
DNS正向解析实验
[root@localhost ~]# yum -y install bind 安装bing服务软件包
已加载插件:fastestmirror, langpacks
Loading mirror speeds from cached hostfile
* base: mirrors.aliyun.com
* extras: mirrors.bfsu.edu.cn
* updates: mirrors.bfsu.edu.cn
正在解决依赖关系
--> 正在检查事务
---> 软件包 bind.x86_64.32.9.11.4-16.P2.el7_8.6 将被 安装
--> 正在处理依赖关系 bind-libs-lite(x86-64) = 32:9.11.4-16.P2.el7_8.6,它被软件包 32:bind-9.11.4-16.P2.el7_8.6.x86_64 需要
--> 正在处理依赖关系 bind-libs(x86-64) = 32:9.11.4-16.P2.el7_8.6,它被软件包 32:bind-9.11.4-16.P2.el7_8.6.x86_64 需要
--> 正在处理依赖关系 liblwres.so.160()(64bit),它被软件包 32:bind-9.11.4-16.P2.el7_8.6.x86_64 需要
--> 正在处理依赖关系 libisccfg.so.160()(64bit),它被软件包 32:bind-9.11.4-16.P2.el7_8.6
.....省略
[root@localhost ~]# rpm -qc bind ##查看bing配置文件
/etc/logrotate.d/named
/etc/named.conf ##主配置文件
/etc/named.iscdlv.key
/etc/named.rfc1912.zones ##区配置文件
/etc/named.root.key
/etc/rndc.conf
/etc/rndc.key
/etc/sysconfig/named
/var/named/named.ca
/var/named/named.empty
/var/named/named.localhost ##区域数据配置文件
/var/named/named.loopback
配置主配置文件
[root@localhost ~]# vim /etc/named.conf
11
12 options {
13 listen-on port 53 { any; }; ##进来后把监听地址改为any
14 listen-on-v6 port 53 { ::1; };
15 directory "/var/named"; ##目录
16 dump-file "/var/named/data/cache_dump.db";
17 statistics-file "/var/named/data/named_stats.txt";
18 memstatistics-file "/var/named/data/named_mem_stats.txt";
19 recursing-file "/var/named/data/named.recursing";
20 secroots-file "/var/named/data/named.secroots";
21 allow-query { any; }; ##把localhost改为any 任何都可以访问地址
22
23 /*
24 - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
25 - If you are building a RECURSIVE (caching) DNS server, you need to enable
26 recursion.
27 - If your recursive DNS server has a public IP address, you MUST enable access
28 control to limit queries to your legitimate users. Failing to do so will
29 cause your server to become part of large scale DNS amplification
30 attacks. Implementing BCP38 within your network would greatly
31 reduce such attack surface
32 */
33 recursion yes;
34
35 dnssec-enable yes;
36 dnssec-validation yes;
:wq 保存退出
配置区域文件
[root@localhost named]# vim /etc/named.rfc1912.zones
.......省略内容
4 };
25 26 zone "shuaige.com" IN { 27 type master; ##解析域名
28 file "shuaige.com.zone"; #关联区域数据文件
29 allow-update { none; };
30 };
:wq 保存退出
配置区域数据文件
[root@localhost ~]# cd /var/named ##切到named目录
[root@localhost named]# ls
data named.ca named.localhost slaves
dynamic named.empty named.loopback
[root@localhost named]# ll ##这边注意文件的属主属组的权限
总用量 16
drwxrwx---. 2 named named 6 6月 1 23:26 data
drwxrwx---. 2 named named 6 6月 1 23:26 dynamic
-rw-r-----. 1 root named 2253 4月 5 2018 named.ca
-rw-r-----. 1 root named 152 12月 15 2009 named.empty
-rw-r-----. 1 root named 152 6月 21 2007 named.localhost
-rw-r-----. 1 root named 168 12月 15 2009 named.loopback
drwxrwx---. 2 named named 6 6月 1 23:26 slaves
[root@localhost named]# cp -p named.localhost shuaige.com.zone
##-p 保持文件属性不变
[root@localhost named]# ll
总用量 20
drwxrwx---. 2 named named 6 6月 1 23:26 data
drwxrwx---. 2 named named 6 6月 1 23:26 dynamic
-rw-r-----. 1 root named 2253 4月 5 2018 named.ca
-rw-r-----. 1 root named 152 12月 15 2009 named.empty
-rw-r-----. 1 root named 152 6月 21 2007 named.localhost
-rw-r-----. 1 root named 168 12月 15 2009 named.loopback
drwxrwx---. 2 named named 6 6月 1 23:26 slaves
-rw-r-----. 1 root named 152 6月 21 2007 xiaokeai.com.zone
[root@localhost named]# vim xiaokeai.com.zone ##编辑区域数据文件
$TTL 1D
@ IN SOA aokeai.com. admin.xiaokeai.com. ( ##域名设置xiaokeai.com
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS xiaokeai.com. ##域名设置为xiaokeai.com
A 127.0.0.1
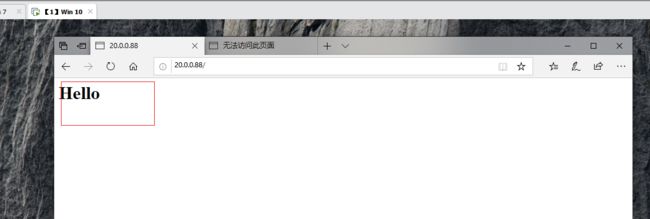
www IN A 20.0.0.88 ##配置解析记录IP地址
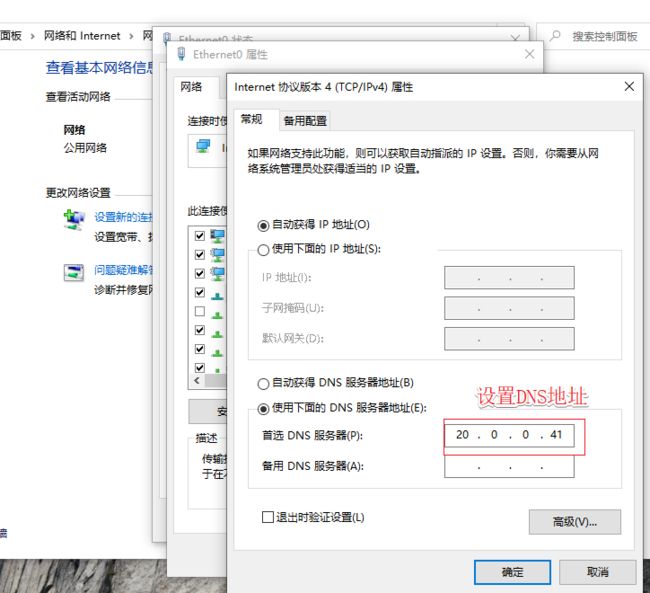
[root@localhost named]# echo "nameserver 20.0.0.41" > /etc/resolv.conf ##设置域名服务器
[root@localhost named]# systemctl restart named ##重启服务
[root@localhost named]# netstat -nuap 查看tcp连接
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
udp 0 0 0.0.0.0:5353 0.0.0.0:* 8638/avahi-daemon:
udp 0 0 20.0.0.41:51154 84.16.67.12:123 ESTABLISHED 8640/chronyd
udp 0 0 192.168.122.1:53 0.0.0.0:* 87628/named
udp 0 0 20.0.0.41:53 0.0.0.0:* 87628/named
udp 0 0 127.0.0.1:53 0.0.0.0:* 87628/named
udp 0 0 192.168.122.1:53 0.0.0.0:* 11234/dnsmasq
udp 0 0 0.0.0.0:67 0.0.0.0:* 11234/dnsmasq
udp 0 0 0.0.0.0:51288 0.0.0.0:* 8638/avahi-daemon:
udp 0 0 0.0.0.0:111 0.0.0.0:* 1/systemd
udp 0 0 127.0.0.1:323 0.0.0.0:* 8640/chronyd
udp 0 0 0.0.0.0:744 0.0.0.0:* 8626/rpcbind
udp6 0 0 ::1:53 :::* 87628/named
udp6 0 0 :::111 :::* 1/systemd
udp6 0 0 ::1:323 :::* 8640/chronyd
udp6 0 0 :::744 :::* 8626/rpcbind
[root@localhost named]# netstat -ntap
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 1/systemd
tcp 0 0 0.0.0.0:6000 0.0.0.0:* LISTEN 18020/X
tcp 0 0 20.0.0.41:53 0.0.0.0:* LISTEN 87628/named
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 87628/named
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 11234/dnsmasq
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 9164/sshd
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 9165/cupsd
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 87628/named
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 9648/master
tcp 0 0 127.0.0.1:6010 0.0.0.0:* LISTEN 82677/sshd: root@pt
tcp 0 0 127.0.0.1:6011 0.0.0.0:* LISTEN 83250/sshd: root@pt
tcp 0 0 127.0.0.1:6012 0.0.0.0:* LISTEN 86566/sshd: root@pt
tcp 0 36 20.0.0.41:22 20.0.0.3:52347 ESTABLISHED 86566/sshd: root@pt
tcp 0 0 20.0.0.41:22 20.0.0.1:56666 ESTABLISHED 83250/sshd: root@pt
tcp 0 0 20.0.0.41:22 20.0.0.1:56567 ESTABLISHED 82677/sshd: root@pt
tcp6 0 0 :::111 :::* LISTEN 1/systemd
tcp6 0 0 :::6000 :::* LISTEN 18020/X
tcp6 0 0 ::1:53 :::* LISTEN 87628/named
tcp6 0 0 :::22 :::* LISTEN 9164/sshd
tcp6 0 0 ::1:631 :::* LISTEN 9165/cupsd
tcp6 0 0 ::1:953 :::* LISTEN 87628/named
tcp6 0 0 ::1:25 :::* LISTEN 9648/master
tcp6 0 0 ::1:6010 :::* LISTEN 82677/sshd: root@pt
tcp6 0 0 ::1:6011 :::* LISTEN 83250/sshd: root@pt
tcp6 0 0 ::1:6012 :::* LISTEN 86566/sshd: root@pt
[root@localhost named]# host www.shuaige.com
www.shuaige.com has address 20.0.0.88 ##域名解析IP成功
打开一台windows 10进行验证
##配置网卡信息
[root@localhost ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens33
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=staic ##配置静态IP
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=e5c91dc3-cda7-452d-80ae-7ce1a28cfc65
DEVICE=ens33
ONBOOT=yes
IPADDR=20.0.0.88 ##配置ip
PREFIX=24 ##配置子网掩码
GATEWAY=20.0.0.2 ##网关
DNS1=20.0.0.2
~
[root@localhost ~]# yum -y install httpd
[root@localhost ~]# setenforce 0
[root@localhost ~]# iptables -F
[root@localhost ~]# systemctl restart httpd
[root@localhost ~]# cd /var
[root@localhost var]# ls
account crash games lib log opt spool www
adm db gopher local mail preserve target yp
cache empty kerberos lock nis run tmp
[root@localhost var]# cd www
[root@localhost www]# ls
cgi-bin html
[root@localhost www]# cd html
[root@localhost html]# vi index.html