ssh(远程访问及连接)和tcp wrappers策略应用
远程访问及连接ssh和tcp wrappers策略应用
文章目录
- 远程访问及连接ssh和tcp wrappers策略应用
- 一、ssh远程连接
- 【1】配置文件
- 【2】ssh基本配置及应用
- 【3】ssh密钥对解释及应用
- (1)加密方式
- (2)应用步骤
- 1、创建生成密钥对
- 2、上传公钥文件给客户端
- 3、查看客户端公钥信息是否正确
- 4、使用密钥对验证
- 5、赋予免密登录权限
- 【4】ssh客户端的上传和下载
- (1)普通的上传和下载
- (2)在线快速上传和下载
- 二、TCPWrappers策略的应用
- 【1】保护原理
- 【2】访问策略的配置文件(先白后黑)
- (1)白名单允许
- (2)黑名单拒绝
一、ssh远程连接
【1】配置文件
(1)服务端配置文件:/etc/ssh/sshd_config
(2)客户端配置文件:/etc/ssh/ssh_config
【2】ssh基本配置及应用
(1)远程登录的命令格式:ssh username@hostIP
[root@kgc ~]# hostname test02
[root@kgc ~]# bash(临时修改主机名方便下面的实验)
[root@test02 ~]# vim /etc/ssh/sshd_config
Port 22(进入配置文件打开22端口)
使用远程登录的方式登录客户端root用户
[root@test02 ~]# ssh [email protected]
[email protected]'s password:
Last login: Sun Jul 12 11:12:02 2020
[root@test01 ~]# exit
登出
Connection to 192.168.60.60 closed.
[root@test02 ~]#
参数解释:
exit ###退出当前bash环境
Permission denied ###权限拒绝(密码输错)
(2)禁止使用root用户远程登录
[root@test01 ~]# vim /etc/ssh/sshd_config
PermitRootLogin no(禁用以root身份远程登录)
[root@test01 ~]# systemctl restart sshd(每次修改配置文件均要重启服务)
[root@test02 ~]# ssh [email protected]
[email protected]'s password:
Permission denied, please try again.
(3)限制切换root用户
[root@test02 ~]# ssh [email protected]
[email protected]'s password:
Last login: Sun Jul 12 11:56:27 2020 from 192.168.60.10
[lisi@test01 ~]$ su - root
密码:
上一次登录:日 7月 12 20:25:23 CST 2020从 192.168.60.10pts/2 上
[root@test01 ~]# exit
虽然仅用了以root身份登录,但可以登录客户端其他用户,在切换成root身份,所以要限制切换root用户。
[root@test01 ~]# vim /etc/pam.d/su
auth required pam_wheel.so use_uid
[root@test01 ~]# usermod -g wheel zhangsan(把用户zhangsan加入到wheel组中)
[root@test01 ~]# id zhangsan
uid=1001(zhangsan) gid=10(wheel) 组=10(wheel)
这样就只有在wheel组中的用户可以切换root其余的不可以。
[root@test01 ~]# ssh [email protected]
The authenticity of host '192.168.60.60 (192.168.60.60)' can't be established.
ECDSA key fingerprint is SHA256:I1y8AwPDuMn4brw9K9N/buO2y4hgZ6+Ft6PJcuVoC58.
ECDSA key fingerprint is MD5:42:47:cb:ec:24:fe:9e:14:6b:77:6d:98:72:73:c4:8b.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.60.60' (ECDSA) to the list of known hosts.
[email protected]'s password:
Last login: Sun Jul 12 11:27:52 2020 from 192.168.60.10
[wangwu@test01 ~]$ su - root
密码:
su: 拒绝权限
(4)使用白名单或黑名单
命令格式:
AllowUsers username(用户可以使用任意终端远程登录)
DenyUsers username@host IP(用户不能能使用这一终端进行远程登录)
一般使用白名单,在配置文件中写入允许什么用户使用什么终端登录
[root@test01 ~]# vim /etc/ssh/sshd_config
AllowUsers wangwu [email protected]
####允许wangwu以任何终端登录,lisi以192.168.60.10终端登录
(5)限制密码验证次数
[root@test01 ~]# vim /etc/ssh/sshd_config
#LoginGraceTime 2m(会话超时时间)
#StrictModes yes(在接收登录请求之前是否检查用户家目录和rhosts文件的权限和所有权)
MaxAuthTries 6(最大密码尝试次数)
#MaxSessions 10(允许创建会话的个数)
#PermitEmptyPasswords no(不允许空密码登录)
PasswordAuthentication yes(使用密码验证登录)
[root@test01 ~]#ssh -o NumberOfPasswdPrompts=8 [email protected]
####设置最大登录次数为8次,默认是3次######
【3】ssh密钥对解释及应用
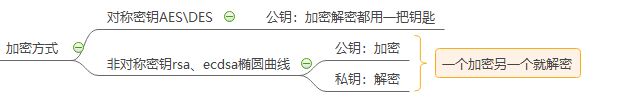
(1)加密方式
[root@test01 ~]# vim /etc/ssh/sshd_config
PubkeyAuthentication yes (启用密钥认证)
AuthorizedKeysFile .ssh/authorized_keys(密钥文件默认路径)
(2)应用步骤
1、创建生成密钥对
[caiwu@tes02 ~]$ ssh-keygen -t ecdsa
Generating public/private ecdsa key pair.
Enter file in which to save the key (/home/caiwu/.ssh/id_ecdsa): (选择默认路径)
Created directory '/home/caiwu/.ssh'.
Enter passphrase (empty for no passphrase): (输入密钥对密码)
Enter same passphrase again: (再确认密码)
Your identification has been saved in /home/caiwu/.ssh/id_ecdsa.
Your public key has been saved in /home/caiwu/.ssh/id_ecdsa.pub.
The key fingerprint is:
SHA256:4XCsX9haLvwHYPwh4OKhfDkITiVyLPFzJaAwEhQo7xw caiwu@tes02
The key's randomart image is:
+---[ECDSA 256]---+
|O*o.. . |
|B=o. o.. |
|++= ...o+ |
|..Eoo .==+. |
|o= = +..S++. |
| .* = o =o |
| . . = .. |
| o . |
| .. |
+----[SHA256]-----+
[caiwu@tes02 ~]$ ls -a /home/caiwu/.ssh
. .. id_ecdsa id_ecdsa.pub
[caiwu@tes02 ~]$
2、上传公钥文件给客户端
[caiwu@tes02 ~]$ ssh-copy-id -i .ssh/id_ecdsa.pub [email protected]
/bin/ssh-copy-id: INFO: Source of key(s) to be installed: ".ssh/id_ecdsa.pub"
The authenticity of host '192.168.60.60 (192.168.60.60)' can't be established.
ECDSA key fingerprint is SHA256:I1y8AwPDuMn4brw9K9N/buO2y4hgZ6+Ft6PJcuVoC58.
ECDSA key fingerprint is MD5:42:47:cb:ec:24:fe:9e:14:6b:77:6d:98:72:73:c4:8b.
Are you sure you want to continue connecting (yes/no)? yes
/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
[email protected]'s password: (输入zhangsan用户的密码)
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '[email protected]'"
and check to make sure that only the key(s) you wanted were added.
3、查看客户端公钥信息是否正确
[zhangsan@test01 ~]$ cat .ssh/authorized_keys
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBN7Q6CI+ERkPcsG9vfCNFWt+VcWWQNptxbdxJJ3/sdARpKhnBrW1poJEucVO2C8Sb7XZjd8DpU7kIy5FpaORMUs= caiwu@tes02
[zhangsan@test01 ~]$
4、使用密钥对验证
[caiwu@tes02 ~]$ ssh [email protected]
Enter passphrase for key '/home/caiwu/.ssh/id_ecdsa': (输入密钥对的密码)
Last login: Sun Jul 12 21:09:27 2020
[zhangsan@test01 ~]$
5、赋予免密登录权限
因为每次登录要输入密钥对密码,为了方便起见,直接免密登录
[caiwu@tes02 ~]$ ssh-agent bash
[caiwu@tes02 ~]$ ssh-add
Enter passphrase for /home/caiwu/.ssh/id_ecdsa: (密钥对密码)
Identity added: /home/caiwu/.ssh/id_ecdsa (/home/caiwu/.ssh/id_ecdsa)
[caiwu@tes02 ~]$ ssh [email protected]
Last login: Sun Jul 12 21:11:53 2020 from 192.168.60.10
[zhangsan@test01 ~]$
【4】ssh客户端的上传和下载
(1)普通的上传和下载
[root@tes02 opt]# ls
ssh_server.txt test02
上传:
[root@tes02 opt]# scp -r test02 [email protected]:/opt
[email protected]'s password: (root用户登录密码)
[root@test01 ~]# cd /opt
[root@test01 opt]# ls
test02 test03
下载:
[root@tes02 opt]# scp -r [email protected]:/opt/test03/ /opt
[email protected]'s password:
txt.txt 100% 0 0.0KB/s 00:00
[root@tes02 opt]# ls
ssh_server.txt test02 test03
(2)在线快速上传和下载
[root@tes02 opt]# sftp [email protected]
[email protected]'s password:
Connected to 192.168.60.60.
sftp> cd /opt(可以在对方的任何目录做任何操作)
sftp> ls(如果写错可以ctrl+backspace删除)
test02 test03
sftp> put ssh_server.txt (上传)
Uploading ssh_server.txt to /opt/ssh_server.txt
ssh_server.txt 100% 17 26.6KB/s 00:00
sftp> ls
ssh_server.txt test02 test03
sftp> get -r test04 (下载)
Fetching /opt/test04/ to test04
Retrieving /opt/test04
[root@tes02 opt]# ls
ssh_server.txt test02 test03 test04
二、TCPWrappers策略的应用
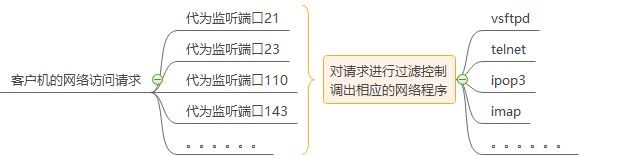
【1】保护原理
TCPWrappers相当于一个简略的防火墙,客户机的访问请求经过TCP wrappers时监听端口号,对请求的端口号进行控制调出相应的网络程序。
【2】访问策略的配置文件(先白后黑)
(1)白名单允许
配置文件:/etc/hosts.allow
[root@tes02 ~]# vim /etc/hosts.allow
sshd:192.168.60.*,20.0.0.20 ####允许192.168.60网段所有以及20.0.0.20主机远程登录
(2)黑名单拒绝
配置文件:/etc/hosts.deny
[root@tes02 ~]# vim /etc/hosts.deny
sshd:ALL(禁止所有进行远程登录)