AWS学习笔记——Chapter3 Virtual Private Cloud
前注:
学习书籍
Index
- Virtual Private Cloud
- 1. Amazon VPC Components and Terminology
- (1) Amazon VPC
- (2) Subnet
- (3) Route Table
- (4) Internet Gateway
- (5) Network Address Translation (NAT)
- (6) Egress-only Internet Gateway
- (7) Elastic Network Interface (ENI)
- (8) Elastic IP Address
- (9) Security Group
- (10)Network Access Control List (NACL)
- (11)Amazon VPC Peering
- (12)Amazon VPC Endpoint
- (13)DNS and VPC
- (14)DHCP Option Sets
- (15)Connecting to a VPC
- (16)VPC Flow Logs
- 2. Default VPC
Virtual Private Cloud
You can do the following things by having a virtual private network:
· Have some of the applications running in the cloud within VPC and some of the applications running on-premise.
· Create multiple subnets within VPC.
eg. Create a public subnet by providing it with Internet access and can keep the resource isolated from the Internet by creating a private subnet.
· Have dedicated connectivity between your corporate data center and VPN by using Direct Connect.
· If you need more than one VPC, you can create multiple VPCs and can connect each one of them by VPC peering. This way you can share the resources across multiple VPCs and accounts.
· Connect to resources such as S3 using a VPC endpoint.
1. Amazon VPC Components and Terminology
(1) Amazon VPC
The first step of creating a VPC is deciding the IP range by providing a Classless Inter-Domain Routing (CIDR) block.
VPC supports both IPv4 and IPv6. Having a CIDR block for IPv6 is optional, but you need an IPv4 CIDR block.
Once you create a VPC, you can’t alter the size of it.
A VPC is limited to a region which means you can’t have a VPC spanning regions. Within a VPC, you have all the AZs that are part of the region where the VPC belongs.
(2) Subnet
Subnet is short for subnetwork, which is logical subdivision of an IP network.
The most common ones are public subnets, private subnets and VPN-only subnets.
Public subnet: create for resources that need to be connected to the Internet.
Private subnet: create for resources that do not need to be connected to the Internet.
VPC-only subnet: create when you want to connect your virtual private cloud with your corporate data center.
Subnets are AZ specific. For multiple AZs, create multiple subnets. VPC are region specific. For multiple regions, create different VPCs.
If you create more than one subnet in a VPC, the CIDR blocks of the subnets cannot overlap.
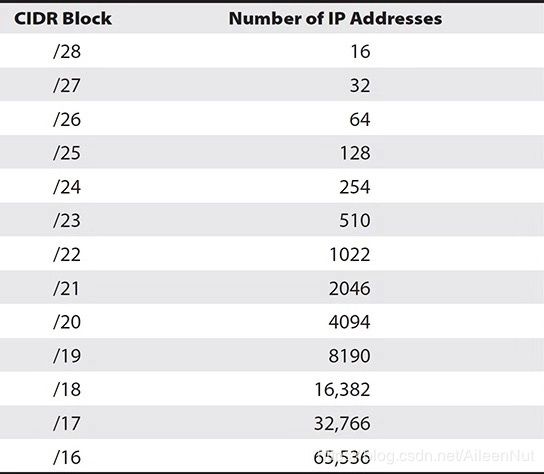 Table CIDR Block and Available IP Addresses
Table CIDR Block and Available IP Addresses
For any subnet AWS reserves, the first four IP addressed and the last IP address are for internal networking purposes, and they are not available for your usage.
(3) Route Table
A route table is a table consisting of certain rules known as routes that determine where the traffic is directed.
Each subnet must have a route table at any time, but you can associate multiple subnets with the same route table.
When you create a subnet and do not associate it with any other route table, it is automatically associated with the main route table of the VPC.
The VPC’s default route table (known as the main route table) is created automatically, and you can’t modify it.
For the case you don’t want to use the main route table of VPC, a best practice would be to keep the main route table of the VPC in an original state with only the local route and assign a custom route table for each subnet you have created.
A target if “local” means only local traffic can flow within the virtual private cloud and no other traffic is allowed.
(4) Internet Gateway
An Internet Gateway (IG) is a component of VPC that allows your VPC to communicate with the Internet.
An IG supports both IPv4 and IPv6 traffic.
Attach an IG: add the entry for the IG in the routing table and you are all set.
If you add an IG in your VPC, then you can make any of the subnets inside that VPC accessible to the Internet just by adding the IG in the subnet’s route table.
If Amazon VPC does not have an IG in the route table, then you won’t be able to make any of the subnets accessible to the Internet.
(5) Network Address Translation (NAT)
Using a NAT device, you can enable any instance in a private subnet to connect to the Internet, but this does not mean the Internet can initiate a connection to the instance. (私有子网中的实例可以连接网络,但网络不能发起对实例的连接)
A NAT device forwards traffic from the instances in the private subnet to the Internet and then sends the response to the instances. (NAT设备将流量从专有子网中的实例转发到Internet,然后将响应发送到实例)
When traffic goes to the Internet, the source IPv4 address is replaced with the NAT device’s address; similarly, when the response traffic goes to those instances, the NAT device translates the address back to those instances’ private IPv4 addresses. (当流量进入Internet时,源IPv4地址将替换为NAT设备的地址;同样,当响应流量进入这些实例时,NAT设备会将地址转换回这些实例的专用IPv4地址)
NAT devices can be used only for IPv4 traffic.
Two types of NAT devices:
NAT instances
By using a NAT instance in a public subnet, you can have the instance running in the private subnet initiate outbound traffic to the Internet or to some other AWS service.
The NAT instance is a single point of failure, if it goes down, the DB server in the private subnet won’t be able to connect to the Internet.
NAT gateways
Perform the same function as that of a NAT instance, but it does not have the same limitations as a NAT instance.
When creating a NAT gateway, you must specify an elastic IP address and associate with it.
When a NAT gateway is created, it is created in a specific AZ in a redundant fashion.
A NAT gateway is preferred over a NAT instance since it provides better availability and bandwidth.
(6) Egress-only Internet Gateway
Similar to NAT gateways, an egress-only IG is a component of your VPC, which allows VPC to communicate with the Internet for IPv6 traffic.
Egress only, outbound only, which means it prevents the Internet from initiating an IPv6 connection with your instances.
NAT gateway handles IPv4 traffic, Egress-only gateway handles IPv6 traffic. (the only difference between them)
(7) Elastic Network Interface (ENI)
ENI gives you the ability to create one or more network and attach them to your instance.
Can attach or detach ENI from an instance anytime, can also reattach it to a different instance.
Whenever you move ENI from one instance to another, all the traffic is redirected to the new instance, also the attributes of the ENI follow along with it.
An ENI can have following attributes: A MAC address; One public IPv4 address; One or more IPv6 address; A primary private IPv4 address; One or more secondary private IPv4 address; One elastic IP address (IPv4) per private IPv4 address; One or more security groups; A source/destination check flag and description.
You cannot change the default network interface of any instance, which is also known as a primary network interface (etho).
The number of ENIs you can attach to a particular instance varies from instance to instance type.
ENI doesn’t impact the network bandwidth to the instance, so cannot be used as a method to increase or double the network bandwidth.
(8) Elastic IP Address
An elastic IP (EIP) address is designed for applications running on the cloud.
Instead of changing the IP address for all applications every time, you can obtain an EIP and associate that with the EC2 instance and map the EIP with the application.
An EIP is a static IP address.
An EIP supports only IPv4 and does not support IPv6.
An EIP is a public IPv4 address, which means it is reachable from the Internet.
Three steps to use an EIP:
· Allocate one EIP to your account from the console.
· Associate the EIP either with your instance or with a network interface.
· Start using it.
(9) Security Group
A security group defines what traffic can flow inside and outside a particular instance. (instance level, not subnet level)
Can attach up to five different security groups to each instance. But the limit is not hard limits and can be raised by a support request.
A security group is stateful and consists of IP addressed, ports and protocols.
Can only specify allow rules, the way of deny is to not allow.
Whenever you make any changes to a security group, the changes are reflected in the instance immediately and automatically.
Security groups are stateful. If you send a request from your instance, and vice versa, traffic is allowed.
When you create a security group, by default no incoming traffic is allowed and all the outbound traffic is allowed.
Amazon VPC always comes with a default security group. You cannot delete it, However, you can change the rules for it.
(10)Network Access Control List (NACL)
An NACL is a layer of security that acts as a firewall at the subnet level (Optional).
An NACL is stateless and a combination of IP address, port, protocol and allow/deny for a subnet.
VPC comes with a default NACL that can be modified which allows all inbound and outbound IPv4 and IPv6 traffic (if applicable).
A custom NACL denies all inbound and outbound traffic until you add rules by default.
AnNACL can associate with multiple subnets, but a subnet can be associated with only one NACL at time.
NACLs contain a numbered list of rules. Rules are evaluated starting with the lowest numbered rule and will apply regardless of any higher-numbered rule that may contradict it.
An NACL has separate inbound and outbound rules, and each rule can either allow or deny traffic.
NACL supports protocols. You can specify any protocol that has a standard protocol number, and choose to allow or deny specific traffic.
Differences between NACLs and security groups:
· A security group can be applied only at the instance level, whereas an NACL can be applied at the subnet level. So, if you have ten instances within a subnet, NACL rules are going to be applied for all ten instances.
· A security group is stateful (return traffic is allowed by default), whereas an NACL is stateless (return traffic is not allowed by default).
· A security group supports allow rules only; you can’t specify a deny rule explicitly. An NACL allows both allow and deny rules.
· In a security group, all the rules are evaluated before deciding whether to allow the traffic, whereas in NACLs the rule number gets precedence.
(11)Amazon VPC Peering
VPC peering helps to connect one VPC to another and route the traffic across the VPCs using a private IPv4 or IPv6 address.
VPC peering can be done only for VPCs within a region.
You can peer multiple VPCs running in your account, and also peer them across different accounts.
VPC Peering is not any kind of gateway or a VPN connection, it relies on special hardware.
No single point of failure or throttling of bandwidth due to its internal infrastructure.
A VPC peering connection is a one-to-one relationship between two VPCs.
eg. VPC A peers VPC B, VPC A peers VPC C, but can’t peer B and C through A.
Three steps to peer VPC A and B:
· The owner of VPC A sends a request to VPC B to create the VPC. Once the owner of VPC B gets the request, the owner needs to accept the VPC peering connection to activate the VPC peering connection.
Notes:
The CIDR block cannot overlap.
VPC A and B can be part of the same account or a different account.
· The owner of each VPC needs to add a route to one or more of their VPC’s route tables that point to the IP address range of the other VPC.
· (Optional) You might be required to update the security group rules associated with your instance to make sure the traffic from the peered VPC can reach your instance. Similarly, you may have to modify your VPC connection to enable DNS hostname resolution.
(12)Amazon VPC Endpoint
VPC endpoint gives you the ability to connect to VPC and the AWS services running outside VPC directly using a private connection. Therefore, the traffic never leaves the Amazon network.
If don’t use the VPC endpoint, you need to connect VPC to these services either via the Internet or via your corporate data center.
The VPC endpoint is actually a virtual device. To use it, you don’t need a public IPv4 address or Internet gateway, NAT device/gateway, or virtual private gateway in your VPC.
Currently, the VPC endpoint is available only for S3 and DynamoDB. Soon there will be more services.
By using VPC endpoints, you save a lot of money. Since EC2 and S3 are connected via endpoints, there are no data transfer charges.
Two steps to configure a VPC endpoint:
· Specify the VPC and the service. Attach a policy to the endpoint and specify the route tables that will be used by the endpoint.
· Specify one or more route tables to control the routing of traffic your VPC and the other service.
(13)DNS and VPC
DNS servers maintain a directory of domain names and translate them to IP addresses.
A DNS hostname is a name that uniquely names a computer. It’s composed of a hostname and a domain name.
Amazon provides DNS servers that are used to resolve the address of any instance running inside VPC.
There are two main DNS attributes that define whether an instance can have a public DNS hostname. If both the attributes are true, then it gets a public DNS hostname. If one of them is not true, it doesn’t get a public DNS hostname.

You can also use your own DNS server and create a new set of DHCP options for your VPC.
(14)DHCP Option Sets
Dynamic Host Configuration Protocol (DHCP) option sets are used to specify host configurations for instances in your VPC, including the default domain name and DNS server for your instances. (动态主机配置协议(DHCP)选项集用于指定VPC中实例的主机配置,包括实例的默认域名和DNS服务器)
AWS recommends that you create a DHCP options set for your AWS Directory Service directory and assign the DHCP options set to the VPC that your directory is in. This allows any instances in that VPC to point to the specified domain and DNS servers to resolve their domain names.
For your VPC, Amazon automatically creates and associates a DHCP option set. It also sets two options in it that are domain name servers defaulted to AmazonProvidedDNS (which is an Amazon DNS server) and the domain name for your region.
Every VPC must have only one DHCP option set assigned to it.
Once you create a DHCP option set, you can’t modify it.
If you need to specify different DHCP options, you’ll need to create a new DHCP option set.
Once you’ve associated a new DHCP option set, new instances launched in VPC will automatically start using the settings in the newer DHCP option set. Instances that are already running in VPC will pick up the new options when their DHCP lease is renewed.
The option field of DHCP contains the configuration parameters, you can provide the following values: domain-name-servers; domain-name; ntp-servers; netbios-name-servers; netbios-node-type.
(15)Connecting to a VPC
Two terms:
Virtual private gateway:
A virtual private gateway is the VPN concentrator on the Amazon side of the VPN connection.
Customer gateway:
A customer gateway is a physical device, or it could be a software application on your corporate data center or your side of the VPN connection.
Four main private connectivity options:
AWS hardware VPN
AWS Direct Connect
VPN CloudHub
Software VPN
(16)VPC Flow Logs
Amazon VPC flow logs enable you to capture information about the IP traffic going to and from network interfaces in your VPC.
Flow log data is stored using Amazon CloudWatch logs.
2. Default VPC
Default VPC: In every account, a VPC is created in each region by default.
In a default VPC, instances in default subnets have security group-controlled public and private IPs.
The default VPC comes precreated with the following features:
Dynamic private IP;
Dynamic public IP;
AWS-provided DNS names;
Private DNS name;
Public DNS name.
You can also do the following in the default VPC:
Create additional subnets and change routing rules;
Create additional network controls (security groups, NACLs, routing);
Set hardware VPN options between corporate networks.
