Linux系统之docker(二)——搭建阿里云的镜像加速器和私有仓库(registry)
一.为什么要使用阿里云镜像加速器
在系统拉取镜像时,软件默认去hub.docker.com这个网站中拉取镜像。但该网站在国外,拉取镜像速度十分缓慢
国内很多云服务商都提供了国内加速器服务,例如:
Azure 中国镜像 https://dockerhub.azk8s.cn
阿里云加速器(需登录账号获取)
七牛云加速器 https://reg-mirror.qiniu.com
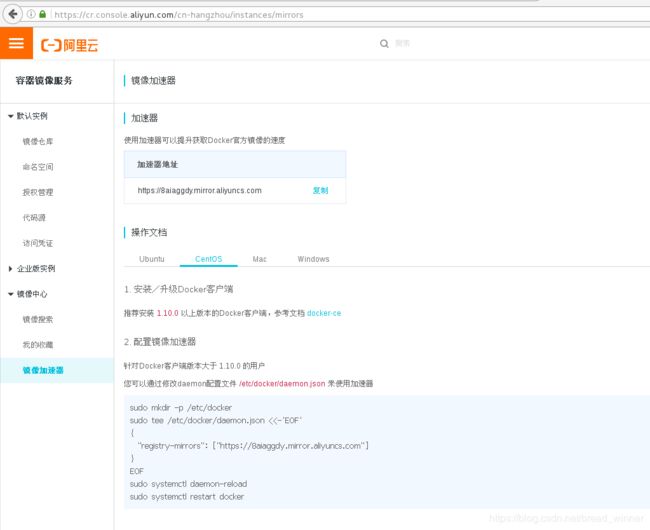
在阿里云上有自己的镜像可以供我们使用,如果没有也可以通设置阿里云镜像加速器来加快景象的拉取速度
二.搭建阿里云的镜像加速器
[root@server1 ~]# cd /etc/docker/
[root@server1 docker]# ls
daemon.json key.json
[root@server1 docker]# cat daemon.json
{
“registry-mirrors”: [“https://8aiaggdy.mirror.aliyuncs.com”]
}
[root@server1 docker]# systemctl daemon-reload
[root@server1 docker]# systemctl restart docker
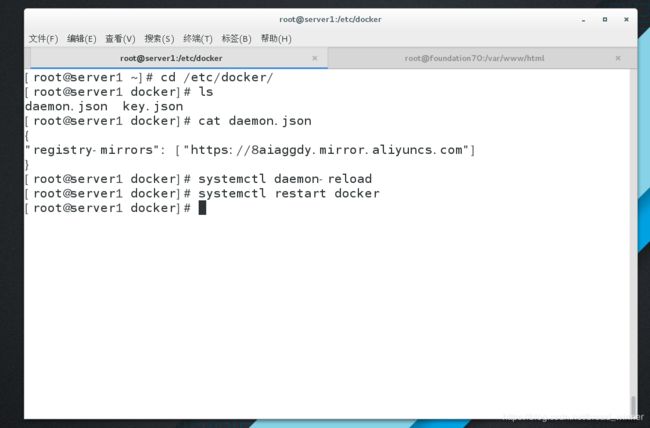
这样,阿里云的镜像加速器就成功搭建好了
三.docker仓库
我们知道docker仓库分为共有仓库和私有仓库。
最大的公开仓库是 Docker Hub,存放了数量庞大的镜像供用户下载
国内的公开仓库包括 Docker Pool等,可以提供大陆用户更稳定快速的访问
当然,用户也可以在本地网络内创建一个私有仓库
当用户创建了自己的镜像之后就可以使用 push 命令将它上传到公有或者私有仓库
这样下次在另外一台机器上使用这个镜像时候,只需要从仓库上 pull 下来就可以了
使用私有仓库的优点有:
1)节省网络带宽,针对于每个镜像不用每个人都去中央仓库上面去下载,只需要从私有仓库中下载即可;
2)提供镜像资源利用,针对于公司内部使用的镜像,推送到本地的私有仓库中,以供公司内部相关人员使用。
四.搭建私有仓库并添加安全证书
当我们新加一台主机server2时,如果没有添加安全证书,这样server2上也同样可以访问我们在server1上搭建好的私有仓库里面的镜像,此时会出现不安全的现象。所以,我们应当为其添加安全证书,保证其安全。
Docker 官方已经把仓库封装为镜像,直接通过启动容器就可以完成部署仓库,导入registry镜像
-
第一步:搭建私有仓库
##导入镜像
[root@server1 mnt]# docker load -i registry.tar
917c0fc99b35: Loading layer 130.9MB/130.9MB
5f70bf18a086: Loading layer 1.024kB/1.024kB
e6107e74315e: Loading layer 20.71MB/20.71MB
5deabacb4c9b: Loading layer 20.66MB/20.66MB
32d89efca72a: Loading layer 3.584kB/3.584kB
Loaded image: registry:2.3.1
##查看镜像
[root@server1 mnt]# docker images registry
REPOSITORY TAG IMAGE ID CREATED SIZE
registry 2.3.1 83139345d017 3 years ago 166MB
[root@server1 mnt]# cd /opt/
[root@server1 opt]# ls
containerd
##建立私有仓库目录
[root@server1 opt]# mkdir -p registry/docker/
[root@server1 opt]# cd registry/
##运行私有仓库
[root@server1 registry]# docker run -d --name registry -p 5000:5000 -v /opt/registry/:/var/lib/registry registry:2.3.1
8bc46f9592ef1080e3ebfc246dad5c927bf9761f94b92a3184db6f9f63dfad42
##查看运行中的镜像
[root@server1 registry]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
8bc46f9592ef registry:2.3.1 “/bin/registry /etc/…” 9 seconds ago Up 8 seconds 0.0.0.0:5000->5000/tcp registry
##查看镜像
[root@server1 registry]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest e548f1a579cf 20 months ago 109MB
registry 2.3.1 83139345d017 3 years ago 166MB
##将nginx打包成一个新的v1版本
[root@server1 registry]# docker tag nginx:latest localhost:5000/nginx:v1
##上传打包好的镜像
[root@server1 registry]# docker push localhost:5000/nginx:v1
The push refers to repository [localhost:5000/nginx]
e89b70d28795: Pushed
832a3ae4ac84: Pushed
014cf8bfcb2d: Pushed
v1: digest: sha256:600bff7fb36d7992512f8c07abd50aac08db8f17c94e3c83e47d53435a1a6f7c size: 948
[root@server1 registry]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
localhost:5000/nginx v1 e548f1a579cf 20 months ago 109MB
nginx latest e548f1a579cf 20 months ago 109MB
registry 2.3.1 83139345d017 3 years ago 166MB
##删除在本的nginx:v1版本的镜像
[root@server1 registry]# docker rmi localhost:5000/nginx:v1
Untagged: localhost:5000/nginx:v1
Untagged: localhost:5000/nginx@sha256:600bff7fb36d7992512f8c07abd50aac08db8f17c94e3c83e47d53435a1a6f7c
[root@server1 registry]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest e548f1a579cf 20 months ago 109MB
registry 2.3.1 83139345d017 3 years ago 166MB
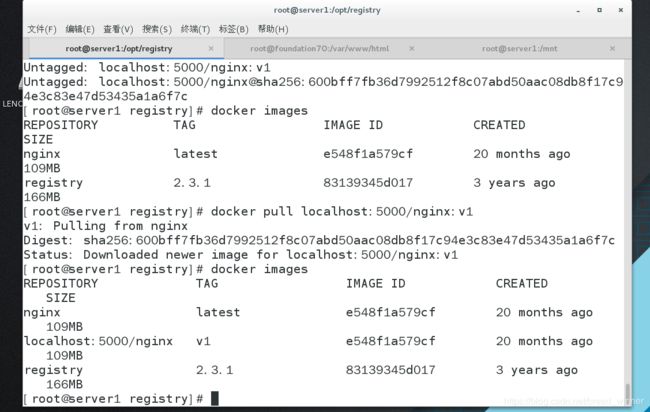
##从私有仓库中拉取nginx:v1版本的镜像
[root@server1 registry]# docker pull localhost:5000/nginx:v1
v1: Pulling from nginx
Digest: sha256:600bff7fb36d7992512f8c07abd50aac08db8f17c94e3c83e47d53435a1a6f7c
Status: Downloaded newer image for localhost:5000/nginx:v1
[root@server1 registry]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest e548f1a579cf 20 months ago 109MB
localhost:5000/nginx v1 e548f1a579cf 20 months ago 109MB
registry 2.3.1 83139345d017 3 years ago 166MB
-
第二步:为私有仓库添加证书
##建立生成加密密匙的文件夹
[root@server1 ~]# mkdir /etc/docker/certs
[root@server1 ~]# cd /etc/docker/
##生成证书和key
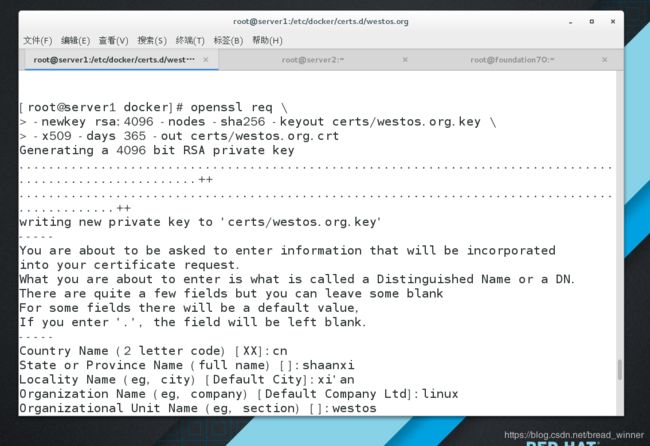
[root@server1 docker]# openssl req \
> -newkey rsa:4096 -nodes -sha256 -keyout certs/westos.org.key \
> -x509 -days 365 -out certs/westos.org.crt
Generating a 4096 bit RSA private key
........................................................................................................++
.............................................................................................++
writing new private key to 'certs/westos.org.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:shaanxi
Locality Name (eg, city) [Default City]:xi'an
Organization Name (eg, company) [Default Company Ltd]:linux
Organizational Unit Name (eg, section) []:westos
Common Name (eg, your name or your server's hostname) []:westos.org
Email Address []:[email protected]
[root@server1 docker]# cd certs/
[root@server1 certs]# ls
westos.org.crt westos.org.key
##添加本地解析
[root@server1 certs]# vim /etc/hosts
[root@server1 certs]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
8bc46f9592ef registry:2.3.1 "/bin/registry /etc/…" 30 minutes ago Up 30 minutes 0.0.0.0:5000->5000/tcp registry
##删除原来没有加密的私有仓库
[root@server1 certs]# docker rm -f 8bc46f9592ef
8bc46f9592ef
[root@server1 certs]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
[root@server1 certs]# netstat -antlp | grep :443
[root@server1 certs]# cd /etc/docker/
##构建容器(私有仓库)
[root@server1 docker]# docker run -d \
> --restart=always \
> --name registry \
> -v "$(pwd)"/certs:/certs \
> -e REGISTRY_HTTP_ADDR=0.0.0.0:443 \
> -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/westos.org.crt \
> -e REGISTRY_HTTP_TLS_KEY=/certs/westos.org.key \
> -p 443:443 \
> -v /opt/registry:/var/lib/registry registry:2.3.1
c46c271604d177900c42ae85c176ca14f3486d6e3d20faf8fd5eff534e788a6d
[root@server1 docker]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
c46c271604d1 registry:2.3.1 "/bin/registry /etc/…" 9 seconds ago Up 8 seconds 0.0.0.0:443->443/tcp, 5000/tcp registry
[root@server1 docker]# mkdir -p certs.d/westos.org
[root@server1 docker]# cd certs.d/westos.org/
[root@server1 westos.org]# cp /etc/docker/certs/westos.org. ca.crt
##创建证书存放目录,并复制证书
[root@server1 westos.org]# cp /etc/docker/certs/westos.org.crt ca.crt
[root@server1 westos.org]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
localhost:5000/nginx v1 e548f1a579cf 20 months ago 109MB
nginx latest e548f1a579cf 20 months ago 109MB
registry 2.3.1 83139345d017 3 years ago 166MB
##重新打包一个新的镜像
[root@server1 westos.org]# docker tag nginx:latest westos.org/nginx:v1
##查看该镜像
[root@server1 westos.org]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest e548f1a579cf 20 months ago 109MB
localhost:5000/nginx v1 e548f1a579cf 20 months ago 109MB
westos.org/nginx v1 e548f1a579cf 20 months ago 109MB
registry 2.3.1 83139345d017 3 years ago 166MB
##上传镜像到私有仓库
[root@server1 westos.org]# docker push westos.org/nginx:v1
The push refers to repository [westos.org/nginx]
e89b70d28795: Layer already exists
832a3ae4ac84: Layer already exists
014cf8bfcb2d: Layer already exists
v1: digest: sha256:600bff7fb36d7992512f8c07abd50aac08db8f17c94e3c83e47d53435a1a6f7c size: 948
此时,在server2上无法使用,如果想要在server2上使用该私有仓库,可以进行下面的内容
首先在server上安装dockr服务,然后建立和server1上相同的证书目录,并将服务端证书传到此位置
[root@server2 ~]# mkdir /etc/docker/certs.d
[root@server2 ~]# cd /etc/docker/certs.d
[root@server2 certs.d]#
[root@server2 certs.d]# mkdi
mkdict mkdir
[root@server2 certs.d]# mkdir westos.org
[root@server2 certs.d]# cd westos.org/
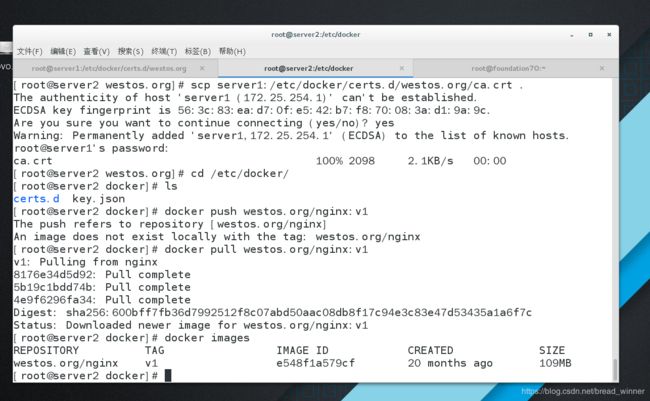
[root@server2 westos.org]# scp server1:/etc/docker/certs.d/westos.org/ca.crt .
然后进行拉取在server1端上传的westos。org/nginx:v1镜像
[root@server2 westos.org]# cd /etc/docker/
[root@server2 docker]# ls
certs.d key.json
[root@server2 docker]# docker push westos.org/nginx:v1
The push refers to repository [westos.org/nginx]
An image does not exist locally with the tag: westos.org/nginx
[root@server2 docker]# docker pull westos.org/nginx:v1
v1: Pulling from nginx
8176e34d5d92: Pull complete
5b19c1bdd74b: Pull complete
4e9f6296fa34: Pull complete
Digest: sha256:600bff7fb36d7992512f8c07abd50aac08db8f17c94e3c83e47d53435a1a6f7c
Status: Downloaded newer image for westos.org/nginx:v1
[root@server2 docker]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
westos.org/nginx v1 e548f1a579cf 20 months ago 109MB
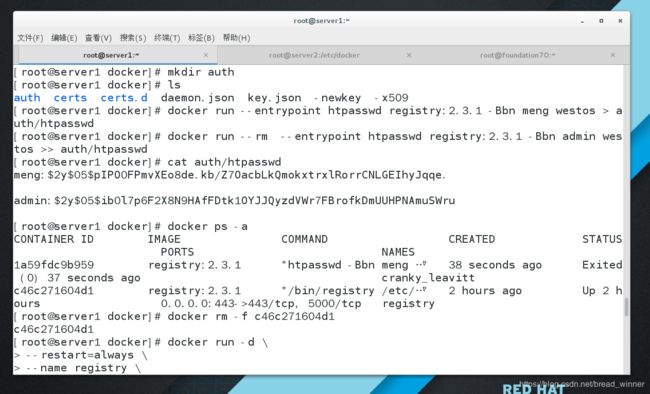
五.配置用户权限 ,给证书加密
如果想要控制registry的使用权限,使其只有在登录用户名和密码之后才能使用的话
还需要做额外的设置,registry的用户名密码文件可以通过htpasswd来生成
第一步:服务端设置用户密码并查看
##在服务端设置用户密码并查看
[root@server1 westos.org]# cd /etc/docker/
[root@server1 docker]# mkdir auth
[root@server1 docker]# ls
auth certs certs.d daemon.json key.json -newkey -x509
[root@server1 docker]# docker run --entrypoint htpasswd registry:2.3.1 -Bbn meng westos > auth/htpasswd
[root@server1 docker]# docker run --rm --entrypoint htpasswd registry:2.3.1 -Bbn admin westos >> auth/htpasswd
[root@server1 docker]# cat auth/htpasswd
meng:$2y$05$pIPO0FPmvXEo8de.kb/Z7OacbLkQmokxtrxlRorrCNLGEIhyJqqe.
admin:$2y$05$ib0l7p6F2X8N9HAfFDtk1OYJJQyzdVWr7FBrofkDmUUHPNAmuSWru
##删除之前的私有仓库
[root@server1 docker]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
1a59fdc9b959 registry:2.3.1 "htpasswd -Bbn meng …" 38 seconds ago Exited (0) 37 seconds ago cranky_leavitt
c46c271604d1 registry:2.3.1 "/bin/registry /etc/…" 2 hours ago Up 2 hours 0.0.0.0:443->443/tcp, 5000/tcp registry
[root@server1 docker]# docker rm -f c46c271604d1
c46c271604d1
##建立新的私有仓库
[root@server1 docker]# docker run -d \
> --restart=always \
> --name registry \
> -v "$(pwd)"/certs:/certs \
> -e REGISTRY_HTTP_ADDR=0.0.0.0:443 \
> -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/westos.org.crt \
> -e REGISTRY_HTTP_TLS_KEY=/certs/westos.org.key \
> -p 443:443 \
> -v /opt/registry:/var/lib/registry \
> -v "$(pwd)"/auth:/auth \
> -e "REGISTRY_AUTH=htpasswd" \
> -e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" \
> -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd registry:2.3.1
ce6d400dae5d0b97250f40d3a04e5c2b2238ea288c0624fe52bd177f41450bb8
[root@server1 docker]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
ce6d400dae5d registry:2.3.1 "/bin/registry /etc/…" 23 seconds ago Up 23 seconds 0.0.0.0:443->443/tcp, 5000/tcp registry
1a59fdc9b959 registry:2.3.1 "htpasswd -Bbn meng …" 4 minutes ago Exited (0) 4 minutes ago cranky_leavitt
##查看本地所包含的镜像并创建一个新的镜像
[root@server1 docker]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest e548f1a579cf 20 months ago 109MB
localhost:5000/nginx v1 e548f1a579cf 20 months ago 109MB
westos.org/nginx v1 e548f1a579cf 20 months ago 109MB
registry 2.3.1 83139345d017 3 years ago 166MB
[root@server1 docker]# docker tag nginx:latest westos.org/nginx:v2
[root@server1 docker]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
westos.org/nginx v1 e548f1a579cf 20 months ago 109MB
westos.org/nginx v2 e548f1a579cf 20 months ago 109MB
nginx latest e548f1a579cf 20 months ago 109MB
localhost:5000/nginx v1 e548f1a579cf 20 months ago 109MB
registry 2.3.1 83139345d017 3 years ago 166MB
##上传新建立的镜像,结果失败,因为这次的私有镜像开启了登陆验证的功能
[root@server1 docker]# docker push westos.org/nginx:v2
The push refers to repository [westos.org/nginx]
e89b70d28795: Preparing
832a3ae4ac84: Preparing
014cf8bfcb2d: Preparing
no basic auth credentials
##登录加密仓库,并输入用户名和密码进行认证
[root@server1 docker]# docker login westos.org