vsftp-安全和虚拟账户
Vsftp传输重要数据不安全,要采用ssl保证安全
1.安装ca
[root@www ~]# vim /etc/hosts
127.0.0.1 localhost.localdomain localhost
::1 localhost6.localdomain6 localhost6
222.1.1.132 www.hotel.com
[root@www ~]# hostname
www.hotel.com
[root@www ~]# cat /etc/sysconfig/network
HOSTNAME=www.hotel.com
[root@www ~]# vim /etc/pki/tls/openssl.cnf
45 dir = /etc/pki/CA # Where everything is kept
88 countryName = optional
89 stateOrProvinceName = optional
90 organizationName = optional
[root@www ~]# cd /etc/pki/CA/
[root@www CA]# openssl genrsa 1024 >private/cakey.pem
[root@www CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem
[root@www CA]# chmod 600 private/*
[root@www CA]# mkdir crl certs newcerts
[root@www CA]# touch serial index.txt
[root@www CA]# echo "09">serial
[root@www Server]# rpm -ivh vsftpd--16.el5_4.1.i386.rpm
[root@www Server]# mkdir -pv /etc/ftp/certs
mkdir: created directory `/etc/ftp'
mkdir: created directory `/etc/ftp/certs'
[root@www Server]# cd /etc/ftp/certs
[root@www certs]# openssl genrsa 1024 >vsftpd.key产生密钥
[root@www certs]# openssl req -new -key vsftpd.key -out vsftpd.csr产生请求证书的文件
[root@www certs]# openssl ca -in vsftpd.csr -out vsftpd.crt
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 9 (0x9)
Validity
Not Before: Oct 22 11:34:52 2011 GMT
Not After : Oct 21 11:34:52 2012 GMT
Subject:
countryName = cn
stateOrProvinceName = hn
organizationName = zzu
organizationalUnitName = hotel
commonName = www.hotel.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
74:9A:07:DB:7B:89:75:D0:90:66:71:04:91:72:42:68:F9:9F:0A:0A
X509v3 Authority Key Identifier:
keyid:B6:53:B5:C4:64:8E:7C:E2:DE:2A:8C:F9:8E:0D:1C:5C:7F:52:99:48
Certificate is to be certified until Oct 21 11:34:52 2012 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
使用抓包工具测试ftp的安全性
# yum list all |grep wireshark
wireshark.i386 -1.el5_3.1 rhel-server
wireshark-gnome.i386 -1.el5_3.1 rhel-server
# yum install wireshark* -y --有依赖的包
# useradd user1
# passwd user1
#service vsftpd start
#chkconfig vsftpd on
# cd /var/ftp/pub/
# touch test01
# touch test02
#tshark –ni eth0 –R “tcp.dstport eq 21”
67-1
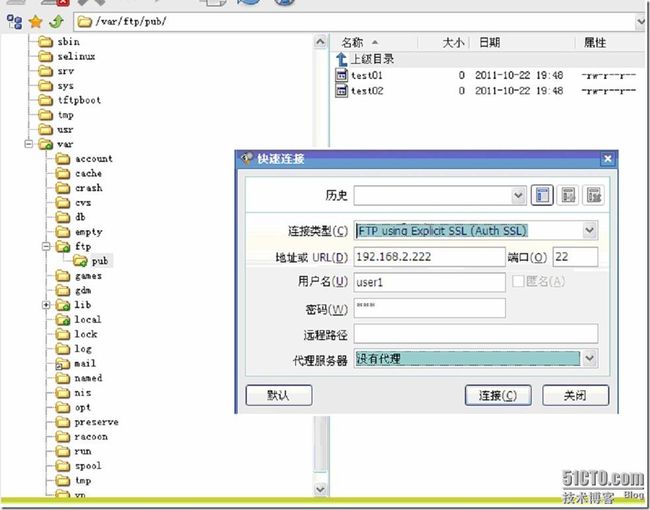
采用ssl安全登陆
[root@www pub]# vim /etc/vsftpd/vsftpd.conf
--vsftp是支持ssl的
--默认是no
force_local_logins_ssl=YES
force_local_data_ssl=YES
ssl_enable=YES
ssl_tlsv1=YES
ssl_sslv2=YES
ssl_sslv3=YES
rsa_cert_file=/etc/ftp/certs/vsftpd.crt
rsa_private_key_file=/etc/ftp/certs/vsftpd.key
pam_service_name=vsftpd
userlist_enable=YES
tcp_wrappers=YES
[root@www pub]# service vsftpd restart
[root@www pub]# chmod 600 /etc/ftp/certs*
#service vsftpd restart
命令行不支持ftps登陆,需要使用ftp客户端工具登陆
Flashfxp
[root@www pub]# tail -f /var/log/secure
Oct 22 20:18:28 www sshd[5584]: pam_unix(sshd:session): session opened for user user1 by (uid=0)
Oct 22 20:18:28 www sshd[5588]: subsystem request for sftp
Oct 22 20:18:55 www sshd[5584]: pam_unix(sshd:session): session closed for user user1
67-2
虚拟账号
在linux系统上不存在的账号,但是是能够访问ftp的账号
当虚拟用户登陆到ftp服务器时会转换成其他linux系统上用户的身份访问ftp
1.创建虚拟账号的文件并转换成数据库文件
[root@www pub]# cd /etc/ftp
[root@www ftp]# cd /etc/vsftpd/
[root@www vsftpd]# vim viruser.txt
zhangsan
123
lisi
123
需要安装光盘的数据库转换文件的工具
[root@www vsftpd]# cd /mnt/cdrom/Server/
rpm –qlp db4-utils-4.3.29-10.el5.i386.rpm
--查看有没有db_load工具
[root@www Server]# rpm -ivh db4-utils--10.el5.i386.rpm
#/lib/security/pam_userdb.so 模块存放的位置
# /lib/security/pam_userdb.so
Segmentation fault
# more /usr/share/doc/pam-0.99.6.2/txts/README.pam_userdb
查看模块的用法
[root@www Server]# cd /etc/vsftpd/
--db_load 没有man手册
[root@www vsftpd]# db_load -T -t hash -f viruser.txt viruser.db
[root@www vsftpd]# vim /etc/vsftpd/vsftpd.conf
force_local_logins_ssl=YES
force_local_data_ssl=YES
ssl_enable=YES
ssl_tlsv1=YES
ssl_sslv2=YES
ssl_sslv3=YES
rsa_cert_file=/etc/ftp/certs/vsftpd.crt
rsa_private_key_file=/etc/ftp/certs/vsftpd.key
pam_service_name=vsftpd.v
需要加入来宾账户
guest_enable=YES 打开guest账号否则虚拟用户登陆到ftp站点,提示连接错误
guest_username=user1 设置虚拟账号的映射必须是本地的用户账号可以没有密码的账号
[root@www pam.d]# cp vsftpd vsftpd.v
[root@www pam.d]# vim vsftpd.v
#%PAM-1.0
--验证的规则的文件和模块
auth required pam_userdb.so db=/etc/vsftpd/viruser
--判断账号密码是否有效
account required pam_userdb.so db=/etc/vsftpd/viruser
[root@www pam.d]# service vsftpd restart
ftp client 测试匿名用户登陆
67-3
--登陆有关的日志
[root@www pam.d]# tail -f /var/log/secure
Oct 22 20:26:08 www sshd[5678]: pam_unix(sshd:session): session opened for user user1 by (uid=0)
Oct 22 20:26:08 www sshd[5680]: subsystem request for sftp
Oct 22 20:38:25 www sshd[5678]: pam_unix(sshd:session): session closed for user user1
Oct 22 20:38:51 www sshd[5756]: Accepted password for user1 from UNKNOWN port 2627 ssh2
Oct 22 20:38:51 www sshd[5756]: pam_unix(sshd:session): session opened for user user1 by (uid=0)
Oct 22 21:11:00 www vsftpd: pam_userdb(vsftpd.v:auth): user 'zhangsan' granted access
Oct 22 21:14:27 www vsftpd: pam_userdb(vsftpd.v:auth): user 'lisi' granted access