BugKu MISC 部分题目Write_up(三)
第十三题: Linux基础1
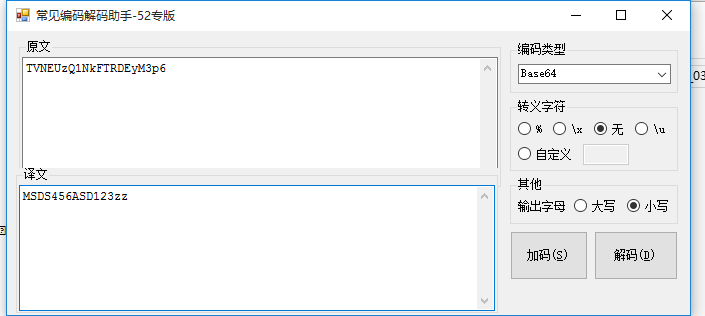
1.通过网址下载题目zip包brave.zip,解压得到brave文件,题目说的是linux基础,应该是想考察linux下的grep命令,但是我直接用notepad++打开,搜索字符串KEY,直接找到了flag:
第十四题: 细心的大象
1.通过网址下载图片,照例我们通过binwalk命令查看图片,发现有隐藏文件:
2.通过foremost命令修复文件得到压缩包:
![]()
3.打开压缩包发现压缩包加密了,右键属性查看图片的详细信息,发现有一段base64的编码字符串,理所应当,肯定就是密码了:
4.解码字符串得到密码,通过密码解开rar压缩包,发现是第二题的图片,所以后面就是第二题的思路,得到flag。
第十五题: MISC 图穷匕见
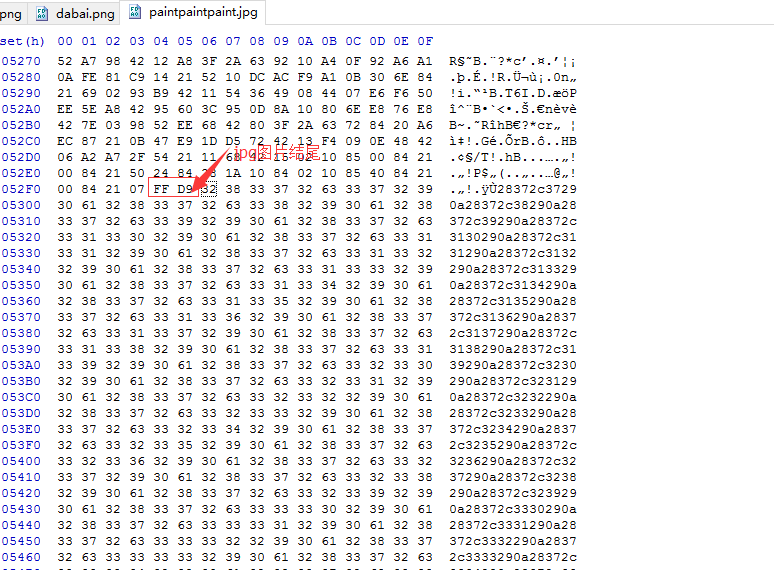
1.通过网址,下载图片,通过HxD查看图片的16进制值:
2.可以看到FF D9是jpg的结尾,后面明显是追加的一些值,将后面的值拷贝出来,在HxD中新建一个文件查看这些16进制值,我们可以看到这些都是一个个坐标值:
3.将坐标值拷贝出来,删掉括号和中间逗号得到所有的坐标,将值存入文件中保存为txt:
4.通过gnuplot画图工具画出图形:
通过手机扫描二维码得到flag。
第十六题: convert
1.通过网址,可以看到一个convert.txt文件,文件内容为二进制01串:
![]()
2.写一个demo,将所有的二进制串转化为十六进制串,转换好的十六进制字符串为:
526172211A0700CF907300000D00000000000000F7C07420902C000D09000059220000023E6370190A59B34A1D330700200000006B65792E6A706700F014A319101D911508917C9015EACB02ECD08228A0B868B4D082A05DB62880816089A944DAA0A0DA68B3426CB02CC44D29A1445404474882209A501D06C5411514313101044D5DC6C050B5440C14B4103B1607446C0E0F71EB11DF1CCEF7C33C4FB91313C999FAA7EE4C473C262BF989D1F54CCD4E88FA3F7EA9F0A88A8A8A889AAAF09889C7F463FEC0D2ADABAD2B8036580DF85E031FD3A5AC567C6F6DCC2B8B80D783281200F0CDE031C943050297464341E070CBB4AD050F80202966E146372501F14FB13A3E058B645BF47C0B162D91A06FC683C257B22568F8162C5B23EBA3E058B64559980E407C03704F4B03C01EC0B806502B0090374599029F99C6854DC72570C946017729FF72D881BC03EFD8CAB0565CCFB702A04F5D0A7E63E0E4AFA170B9045DCC2E794424FE3E30072AB02B2A312EB0278A20D692E0EAD84053D6C52860A4722F0DEE798D696D6052DAF2B7D07A4C1BAE4814D6D8DA3C8F05E453B111FC16F79246A1748B09B66E7979754F162DCDE1287B5BA701B129A9D1C85BE0F751615A05814073E3A8F6A716C2F3FAC90CD45451BDF494A8C29BDAF3032ECD7062E3AAAB63737ACBEBBB630BEEE989A9F5C5A939AD18729690D541F13DF1C9D5C8BD878AFA7C1CD6B32A8A17DAFC9E17BE84E1684A4A0EED6DA9EC1B757FE0A850971FF1F18F796253DA5A53A3B90CE153B24163068B1A352422A92F049CCBF1F124BBD0D085E6822FFE2404AE2BFB01A3E4058B6473FB8D1F202C58B647AFFEC83F1A55B63985A497B0B48AC7B402A804999988333212232C3434126A6E77A437363637D569B4E72767FAB4140CBCF8F852225230A424843CC28FB4D7240CD8ECB2841464E514D1AA09497B21BA16018D3242F6373DD2690F46EB0FB5837267E3D300E84816415A1C32100C0E8307CBB1FC00410BA930C836547DF63D0C601CC4CB3B012686A6C1149ED29761758730310E646462621557E0AB80C4E8CB4DACD8AA19E9D7C78842763B1B0315D31287B6EC77B50C15B7C8897C077822FCD49E1EEAB568BAD4647D76BF65B34CDA26A727AAEDD595D6165696D85898D919777BC666A0B60D20DCDEE0F0F245E9EDF093EC1F1212161A1F8BC68B8CE5C6F323B9BCEE7C97524E53AB2B2D2F31D9ED4ECF4FD050D151D3F7FC1E1A8F178EA6AABBCD5F61E7B1F45959FA49DC5CDD7ABD7777852FF03F7C1F87C708AFCB0F4319CF38386FB8CADE7590E7AB9EB1888CAC6627BD028745C39EB19E99517C40F76D3A1161277B6CF672434434B60BED416ADCF551365E945BFD0C6FFD47F4F1A82C9EBC9CFE319B301B87C90C0EB3A700E06161A3C9401AFFFACD54751096D052D73DA3E0CBB3892562899A55DF576FF9526B3D394B3E1DFA8CB07A5D5E372FC8A74B070B691F71AAC3B099FCED19FAA473A9E43074532A0420C6BBA969AB27717714D58ACECE713EBF7A47A3D7B58711832DF30DD55C9469F63D76B61C28B42854385C4AF0D656CD0CF64ADEAB5F2456B5DA8BF532648CDED71312D18C6471491C949C814B28D6F971BAA1AFC16E9A9A2641B63C359A5CE909A258E0F01B26E0E2B455576A2CE2B799D7A94D29A04D91EE242239BA489B6B358717FFBB541F1BBA277E25384729C6A922755EC140C87BC18A4A2D5CF799A9D182528B5053985192CD147C1694C071A8265DBAD793F187A43B9045DEC6401C61F62F3D33DE514D4E21A536D6A12DA085F8DB7472256E625EA77B1757F6B61206FBC6F3C5237A27EDE29AB48382CA960458CD8AC9CAE4F76E7FB911573FCE45E4A6DAC321ECFCAF921507455CEF6DC44F37F1266935EEDC86EBEE9422647FA7D9106D24C4B49637B3B445593D4E9B17E24F45858A3E1D7984F7B48B7EB0E777ACFBBDC470F61EEF569ED1586C118C39F07B4CD32249BF9D4E42FB87C7C8A592E4D002E0F9976B7D88BCB33BB0A995A48B27BBEEB51AC7F921D3F7FC32313713876DF87751BDB4CE1BD5CC63C12E2D04F01F5A2325F5B3528A9C2875F6CDEFB9456136630F0A1D2540737471E2A7A36AE4C6A95336D34EA432BA6B0620FC6B6C6A320EB5EB854489852657AAF12965158E05139C09136E2DFEAE9D8ED9024385EC292F14BBF54848621F414EAD571B16C1F9029FE3EBA6D4CAEE3A2CF6D2CDAC075BAC65D1085C9D2159FB76725EE23D33B3C9F918E20BDB481C56E30A62B08D6B221729503198C8B2506C4B8161DB52F4B23468C71E256FC12597C2802894D20FB68F6E93E3CFBBCBEEF19471AC01A8C910D77AE8029FF7FD35F66FC81515A568FDEEB51ED1986CB42CA83703843FBA4C6F99BB32972D47AE7C8514730FF1005C972B9D7FA103975DB6D198F311A2AB4FF55E6F780920B3139D5526A283DFFD2552B9712EDF946C4C444D0A3272366E3F9F7E8D139FBD4BAB222FA0FCF38CD77A9E43AE82B60B59C145640B21EC9A7E1EDA5C3D3B2CE58F34AD2D3DB8AB1237895253D0F4D30870FF298345FF2A72949D76FDE471C0EB9DD436351D4FCFD93536CFDED5B6CBF52F06EECA0C9370E433214DFE49DECE8B2B0EE4E75A57A99A8EB291D30EE98B0624E3DEC97DCDE656F3ACCDBAFB9432B0C7D8DA8A2B8166EE367F1ECB6D04FF1ED2A291A949C209FD2D9D48CAB7E1BE38AE2762BD028713D07D1B43C05D953B8029D4B5E64BE045D541DD617896EFD04F3C3D65A9951BD9970BE34E2E046C3A6AFD63AB8DB6C3F5EEA3DA55E70DCD927B0746377A4E14C87066EC39B8F9A49FD19A8BB1D24825447AA0ECCB8C8FE1D5DE3D71E5A479CFB03ED70C37C827439BBA3E0B037E76132A670570C3DDAB3BDBA55F9BF750E76084BCCCD0EE5D2863B7BEBE302F540F0C5629DE8C7C19E012F1517587719FF00DFB59EECDC37C98F7C22A1724EEE7FCE36EEC62D414E0AA861CA760CB76DA65AA49B49CF79467A26AB64C04D66C8E1950E0D4CFD760DB7907266CDB8D871227511096800A99B11E0305D3C71A0D3B779D17A90833005FE57F6F35699EBAD7A7A0FC8188BB5F010F1F507501F3F3D446939ADA2BF6B533EFA7F8028A3D3BF8AD6B0CE3A03E0E3B08F3F48428767B5B4E3AD1D7EDD8BDB0B1B1E6A64E49E730E512CC7E8CC305709CE8903D9CA6C3B75B3D2C4665B79E8F290F2FDF449982D740CAAB1DAF06FE565C6C64C4AA39AF619691338D643DD789C1428CAAE4E2447C986EFEA0497F365767FD7A60A3DB3A152AFC3470DD2627FB569FAF6BC75E8BBA5D9280D55D2C62F87E72FB698C5B00F77AEAFFE74DFE8308C7B2FF28C43D7B004007003.将转换好的十六进制字符串拷贝到HxD中查看,我们可以看到十六进制开头的0x52,0x61,0x72是rar压缩包的开头:
4.将这些十六进制字符串写入到一个rar的压缩包中,解压压缩包我们可以看到一个CTF图片:
![]()
5.右键查看图片详细信息,我们可以看到主题栏中隐藏着base64编码的字符串:
6.解码字符串,得到flag:
注:附上我的bintohex的demo以及存入rar包的代码
import binascii
__author__ = 'feifei'
# !/usr/bin/env python
# -*- coding: utf-8 -*-
base = [str(x) for x in range(10)] + [chr(x) for x in range(ord('A'), ord('A') + 6)]
# bin2dec
def bin2dec(string_num):
return str(int(string_num, 2))
# hex2dec
def hex2dec(string_num):
return str(int(string_num.upper(), 16))
# dec2bin
def dec2bin(string_num):
num = int(string_num)
mid = []
while True:
if num == 0: break
num, rem = divmod(num, 2)
mid.append(base[rem])
return ''.join([str(x) for x in mid[::-1]])
# dec2hex
def dec2hex(string_num):
num = int(string_num)
mid = []
while True:
if num == 0:
break
num, rem = divmod(num, 16)
mid.append(base[rem])
return ''.join([str(x) for x in mid[::-1]])
# hex2tobin
def hex2bin(string_num):
return dec2bin(hex2dec(string_num.upper()))
# bin2hex
def bin2hex(string_num):
return dec2hex(bin2dec(string_num))
if __name__ == '__main__':
file1 = open('convert.txt')
s = file1.read()
hexx = bin2hex(s)
print hexx
file2 = open('4.rar', 'wb')
file2.write(binascii.a2b_hex(hexx))第十七题: 听首音乐
1.通过网址,下载wav的音乐源文件:
2.通过Audacity软件打开音乐源文件,我们可以看到源文件中插入了一串东西:
3.放大观察,我们很容易想到是一串摩斯密码(短横杠代表.,长横杠代表-,中间代表空格):
4.按照规律得到摩斯密码为:
..... -... -.-. ----. ..--- ..... -.... ....- ----. -.-. -... ----- .---- ---.. ---.. ..-. ..... ..--- . -.... .---- --... -.. --... ----- ----. ..--- ----. .---- ----. .---- -.-.5.通过解密网站得到解密后的字符串,传送门,得到flag:
第十八题: 好多压缩包
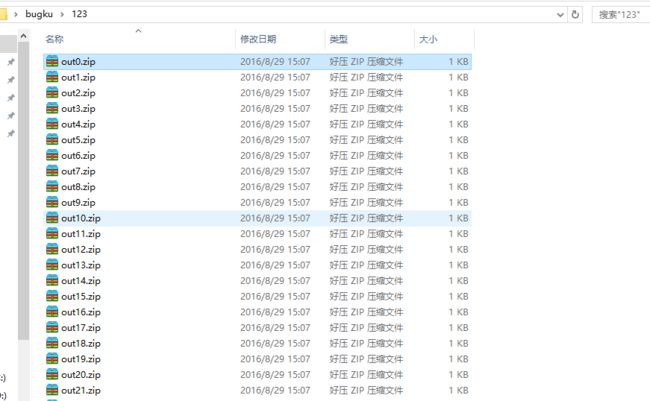
1.通过网址下载压缩包,解压得到68个加密压缩包:
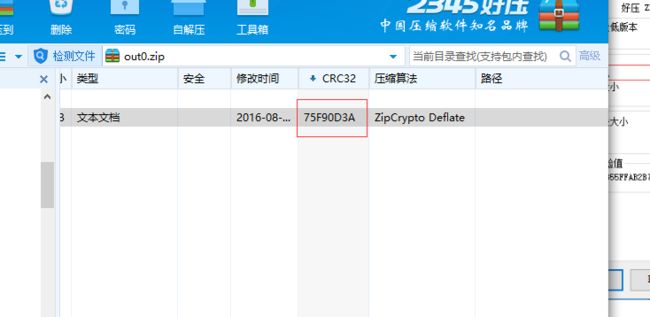
2.打开任意一个压缩包,我们可以看到每个压缩包中含有一个data.txt文件,查看文件详细信息,看到文件总大小为4个字节,和CRC32值。
3.编写脚本,通过CRC32碰撞,暴力破解出值:
# coding:utf-8
import zipfile
import string
import binascii
import base64
def CrackCrc(crc):
for i in dic:
for j in dic:
for p in dic:
for q in dic:
s = i + j + p + q
if crc == (binascii.crc32(s) & 0xffffffff):
# print s
f.write(s)
return
def CrackZip():
for I in range(68):
file = 'out' + str(I) + '.zip'
f = zipfile.ZipFile(file, 'r')
GetCrc = f.getinfo('data.txt')
crc = GetCrc.CRC
CrackCrc(crc)
dic = string.ascii_letters + string.digits + '+/='
f = open('out.txt', 'w')
CrackZip()
f.close()4.得到碰撞出的值,可以看出来为base64编码过:
5.先base64解码,然后转换成十六进制值,拷贝到HxD中,可以看到fix the file and get the flag得知我们需要修复文件就可以得到flag:
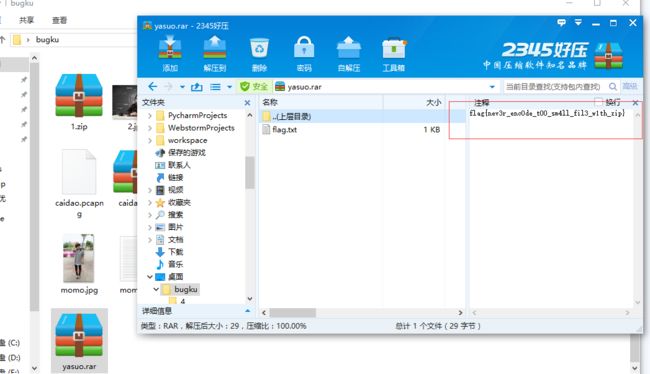
6.我们知道C4 3D 7B 00 40 07 00为rar文件的十六进制结尾,所以我们需要在文件头部添加rar文件的十六进制头52 61 72 21 1A 07 00,然后另存为rar文件。打开rar文件,在注释中得到flag:
第十九题: 妹子的陌陌
1.通过网址下载图片到本地:
2.通过binwork查看图片详细信息,然后通过foremost对图片进行分离,得到一个压缩包:
3.打开压缩包,发现是经过加密的,原本想爆破,尝试好久,无果,最后经过别人提醒知道密码就是图片上的中文喜欢我吗.,真的是脑洞。解密后得到一个momo.txt文件:
4.第一步,解摩斯密码,得到网址:
5.访问网址,是一个解密网站,正好第二步已知我们AESkey我们需要AES解密:
6.拼接解密后的内容,访问网址http://c.bugku.com/momoj2j.png,得到一张二维码图片:
7.直接扫描二维码发现并不能识别,发现背景颜色反转了,通过Stegsolve.jar打开,反转图片:
8.扫描二维码获得flag。