Linux之firewalld防火墙策略优化
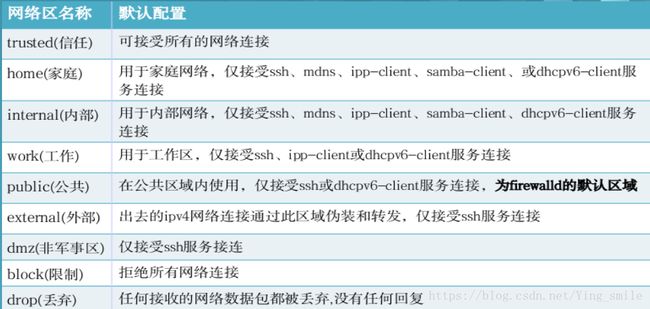
firewalld 域
开启 firewalld
systemctl stop iptables.service
systemctl disable iptables.service
systemctl start firewalld
systemctl enable firewalld
实验:
下载安装防火墙:

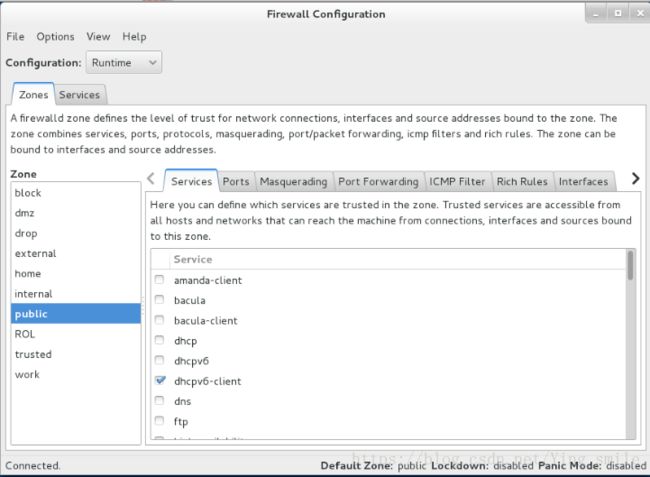
[root@client ~]# firewall-config
界面如下图所示:
下载iptables

关闭iptables,打开防火墙

firewalld 的管理
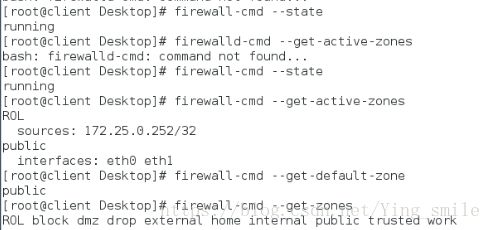
firewall-cmd --state
查看火墙当前生效的域
firewall-cmd --get-active-zones
查看默认的域
firewall-cmd --get-default-zone
查看所有的域
firewall-cmd --get-zones
查看public域里面的信息
firewall-cmd --zone=public --list-all
查看block域里面的信息
firewall-cmd --zone=block --list-all
查看所有域的状态
firewall-cmd --list-all-zones
列出所有域的规则
firewall-cmd --list-all
列出系统当中用名称代表的服务
firewall-cmd --get-services
打开防火墙界面
firewall-config
修改 firewalld 域
修改默认的域为trusted域
firewall-cmd --set-default-zone=trusted
代表可以接收所有网络访问
实验:
[root@client Desktop]# yum install httpd -y #安装apache
[root@client Desktop]# systemctl start httpd
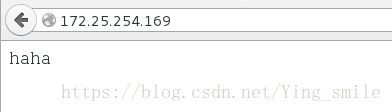
[root@client Desktop]# echo haha >/var/www/html/index.html #给默认发布文件写入内容haha
浏览器测试,因为firewalld的域为public所以查看不到内容:
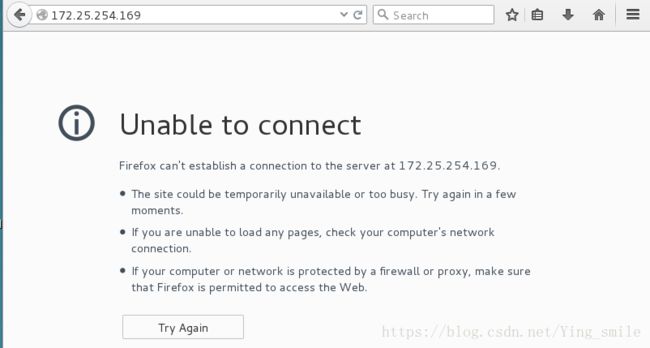
[root@client Desktop]# firewall-cmd --set-default-zone=trusted #修改域为trusted
success
[root@client Desktop]# firewall-cmd --get-default-zone
trusted
使用命令行配置防火墙
添加网卡:

给网卡添加ip后查看ip:
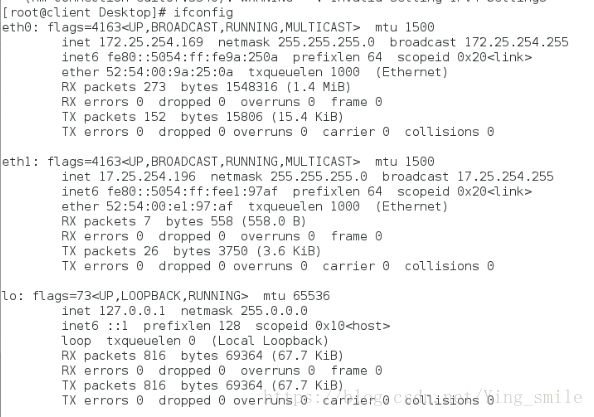
更改域为public:

添加主机ip为信任:
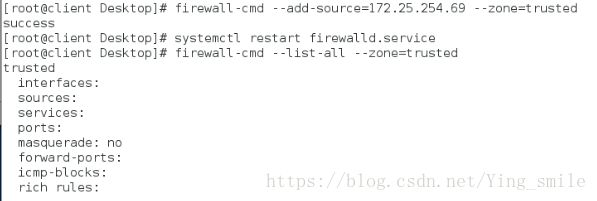
修改设备状态:
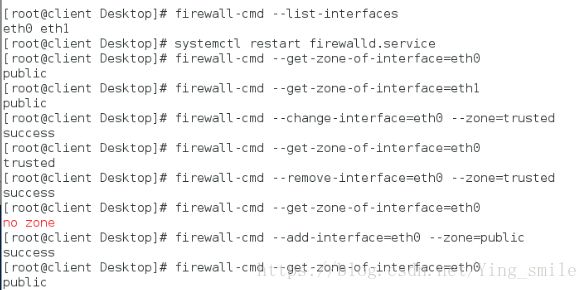
临时添加主机域,重启之后会失效:
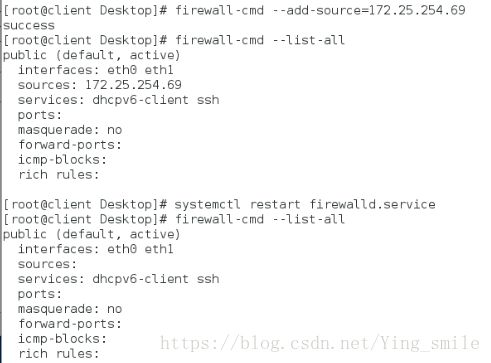
永久添加主机域,重启之后不会失效:

[root@client Desktop]# cd /etc/firewalld/
[root@client firewalld]# ls
firewalld.conf icmptypes services
firewalld.conf.old lockdown-whitelist.xml zones
[root@client firewalld]# cd zones/
[root@client zones]# ls
public.xml public.xml.old ROL.xml
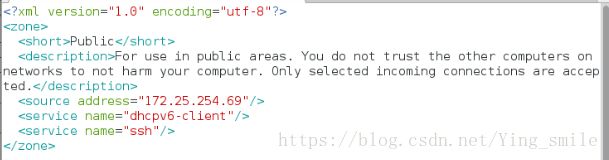
[root@client zones]# vim public.xml #查看firewalld规则文件
内容如下:
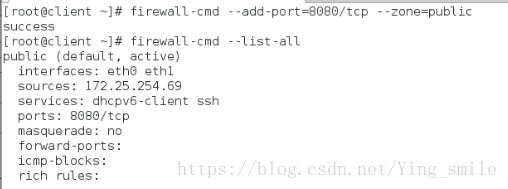
修改端口:
临时移除防火墙允许服务:

永久移除防火墙允许服务:

移除允许服务后在真机测试,不能使用ssh服务连接到主机:
![]()
当永久删除firewlld允许的ssh服务时 firewall-cmd --reload 与firewall-cmd --complete-reload 重新加载的区别:
在真机连接到服务主机之后
使用 firewall-cmd --reload 重新加载时,不会断开连接,可以进行操作
使用 firewall-cmd --complete-reload 重新加载时,会中断连接,不能进行操作
Direct Rules
三表:
filter:访问本机数据,过滤,防火墙(包含input、output、forword)
nat:从本机经过的数据,网络地址转换(包含output、prerouting、postrouting)
mangle:(包含input、output、postrouting、prerouting、forward)
五链:
input:目的地址为本机
output:原地址为本机,向外发送
forward:实现转发
postrouting:数据包进入路由之后
prerouting;数据包进入路由之前
当http加入firewalld允许访问的列表里面,所有主机都可以访问,这是不安全的,应该对个别主机设定访问权限,以保证安全
1、当添加http到firewalld允许访问列表实验
[root@client Desktop]# yum install httpd #下载http
[root@client Desktop]# systemctl start httpd #开启http服务
[root@client Desktop]# firewall-cmd --permanent --add-service=http
success #将http永久加入防火墙
[root@client Desktop]# firewall-cmd --reload #重新加载
success
[root@client Desktop]# firewall-cmd --list-all #查看已经加入
public (default, active)
interfaces: eth0 eth1
sources:
services: dhcpv6-client http ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
测试:两个主机的浏览器都可以看到http的页面

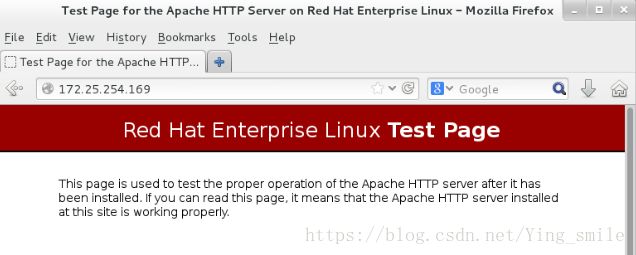
2、对个别主机设定访问权限
[root@client Desktop]# firewall-cmd --permanent --remove-service=http #永久移除http
success
[root@client Desktop]# firewall-cmd --reload #重新加载
success
[root@client Desktop]# firewall-cmd --list-all
public (default, active)
interfaces: eth0 eth1
sources:
services: dhcpv6-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
[root@client Desktop]# firewall-cmd --direct --add-rule ipv4 filter INPUT 1 -p tcp --dport 80 -s 172.25.254.196 -j ACCEPT
#--direct 添加规则,ipv4 协议方式,filter 表,INPUT 链,-p 协议,--dport 目的地,-s 数据来源,-j 动作(reject是有回应的拒绝,drop丢弃没有回应的访问,accept接受)
success
[root@client Desktop]# systemctl restart httpd #重启服务
测试:
IP为172.25.254.196主机:

其他主机:
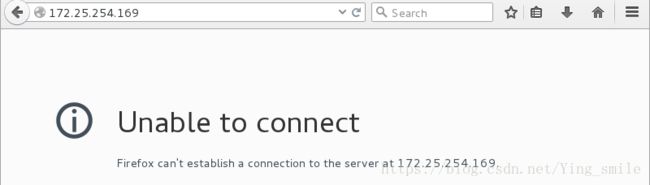
端口转发
[root@client Desktop]# firewall-cmd --permanent --add-forward-port=port=22:proto=tcp:toport=22:toaddr=172.25.254.196 #伪装端口,连接本机时看到的是伪装的ip
success
[root@client Desktop]# firewall-cmd --permanent --add-masquerade #永久打开masquerade服务
success
[root@client Desktop]# firewall-cmd --reload #重新加载
success
[root@client Desktop]# firewall-cmd --list-all #查看
public (default, active)
interfaces: eth0 eth1
sources:
services: dhcpv6-client ssh
ports:
masquerade: yes
forward-ports: port=22:proto=tcp:toport=22:toaddr=172.25.254.196
icmp-blocks:
rich rules:
真机测试:
[kiosk@foundation69 Desktop]$ ssh [email protected] #连接设置了伪装端口的主机
[email protected]'s password:
Last login: Tue Jun 12 08:14:36 2018
[root@server ~]# ifconfig eth0 #查看连接到的ip是伪装的ip
eth0: flags=4163 mtu 1500
inet 172.25.254.196 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::5054:ff:fe00:450b prefixlen 64 scopeid 0x20
ether 52:54:00:00:45:0b txqueuelen 1000 (Ethernet)
RX packets 2015 bytes 176248 (172.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 3581 bytes 198961 (194.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
地址伪装
在添加地址伪装的主机添加两块网卡并设置不同网段的ip
[root@client Desktop]# ifconfig eth0
eth0: flags=4163 mtu 1500
inet 172.25.254.169 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::5054:ff:fe9a:250a prefixlen 64 scopeid 0x20
ether 52:54:00:9a:25:0a txqueuelen 1000 (Ethernet)
RX packets 3985 bytes 211650 (206.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 341 bytes 62706 (61.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@client Desktop]# ifconfig eth1
eth1: flags=4163 mtu 1500
inet 172.25.0.169 netmask 255.255.255.0 broadcast 172.25.0.255
inet6 fe80::5054:ff:fee1:97af prefixlen 64 scopeid 0x20
ether 52:54:00:e1:97:af txqueuelen 1000 (Ethernet)
RX packets 4778 bytes 254297 (248.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1019 bytes 100569 (98.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@client Desktop]# firewall-cmd --list-all
public (default, active)
interfaces: eth0 eth1
sources:
services: dhcpv6-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
[root@client Desktop]# firewall-cmd --permanent --remove-forward-port=port=22:proto=tcp:toport=22:toaddr=172.25.254.196 #永久移除伪装的ip端口
success
[root@client Desktop]# sysctl -a | grep ip_forward #net.ipv4.ip_forward为0时,编辑文件/etc/sysctl.conf然后执行sysctl -p 加载文件参数即可
net.ipv4.ip_forward = 0
[root@client Desktop]# vim /etc/sysctl.conf
文件内容如下:
![]()
[root@client Desktop]# sysctl -p
net.ipv4.ip_forward = 1
测试主机:
[root@server Desktop]# ifconfig eth0 #查看ip
eth0: flags=4163 mtu 1500
inet 172.25.0.196 netmask 255.255.255.0 broadcast 172.25.0.255
inet6 fe80::5054:ff:fe00:450b prefixlen 64 scopeid 0x20
ether 52:54:00:00:45:0b txqueuelen 1000 (Ethernet)
RX packets 2034 bytes 177714 (173.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4005 bytes 223681 (218.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@server Desktop]# route -n #查看网关,这里网关是不同网段地址伪装主机的ip
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 172.25.0.169 0.0.0.0 UG 1024 0 0 eth0
172.25.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
[root@server Desktop]# ping 172.25.254.69 #可以通过地址伪装主机做路由从而可以ping通不同网段的ip
PING 172.25.254.69 (172.25.254.69) 56(84) bytes of data.
64 bytes from 172.25.254.69: icmp_seq=1 ttl=63 time=0.545 ms
64 bytes from 172.25.254.69: icmp_seq=2 ttl=63 time=0.371 ms
^C
--- 172.25.254.69 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 0.371/0.458/0.545/0.087 ms