openssl:Generate self signed CA and issue cert
GenerateCA and sign out certificate:
Precondition
1. Centos install(memory2048, GUI mode)
https://blog.csdn.net/hui_2016/article/details/68927487
2. Make sure openssl.cnf under /etc/pki/tls, we use default configuration
3. Following steps, you can refer to below:
https://blog.csdn.net/chenyefei/article/details/48522767
Steps:
1. Create private key
opensslgenrsa -des3 -out ca.key 4096
Note: the password is important (ca.key password:1234)
2. Generate root certificate whichis signed by itself
openssl req -new -x509 -days 365 -key ca.key -out ca.crt
openssl will ask you the pswd of private key, and then a serials of questions,
# Common Name(CN) is important
2.1 Formatconvert: crt to pem:
openssl x509 -in ca.crt -out ca.pem
3. Generate server side private key
openssl genrsa -des3 -out server.key 4096 (4090 is key size, also can select 1024,2048……)
Server.keypassword 4321
Challengepassword:1111
4. Generate signature request forthe object which need to be signed (server side):
openssl req -new -key server.key -out server.csr
Note: CommonName must diff than root CA
5. Sign the step4’s signaturerequest by using root CA generated in step 2, and use private key instep1
openssl x509-req -days 365 -in server.csr-CA ca.pem -CAkey ca.key -set_serial 01-out dispenser.pem
Sign a one day expired certificate:
openssl x509-req -days 1 -in server.csr -CA ca.pem -CAkey ca.key -set_serial 04 -outdispenser3.pem
Revoke& CRL
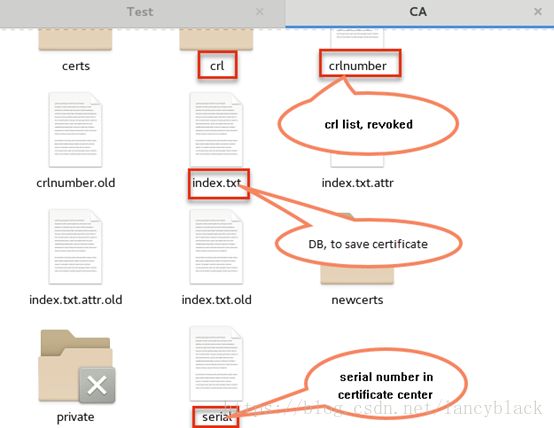
Precondition
make sure /etc/pki/CA has following file:
[root@lancy catesting]#touch crlnumber new crlnumber file
[root@lancy catesting]#echo “00”>crlnumber initial data 00
[root@lancy catesting]#touch index.txt create DB file,initial,nodata
[root@lancy catesting]#touch serial new serial file
[root@lancy catesting]#echo “00”>serial initial data 00
Revoke certificate
openssl ca-revoke dispenser1.pem -cert ca.pem -keyfile ca.key
Generate CRL
openssl ca -gencrl -out client.crl -cert ca.pem -keyfile ca.key -config /etc/pki/tls/openssl.cnf
Note:-config /etc/pki/tls/openssl.cnf canignore, use default config
Mock up a CRL to root CA
cat ca.pemclient.crl > crl_chain_Test.pem
others
print certificate serial number:
opensslx509 -in dispenser12.pem -noout –serial
check certificate dates:
opensslx509 -in dispenser3.pem -noout –dates
Verify certificate:
opensslverify -CAfile ca.pem dispenser4.pem
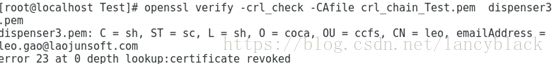
Verifycertificate revoke:
openssl verify-crl_check -CAfile crl_chain_Test.pem dispenser4.pem
用SHA256算法计算文件ca.pem的哈西值,输出到文件digest.txt
openssl sha256-out digest.txt ca.pem
//解析证书完整信息
$openssl x509 -in user.cer -inform PEM -text-noout
//查看证书指定信息
$openssl x509 -in user.cer -inform PEM -noout-pubkey-modulus-serial-subject-issuer-email-startdate-enddate-dates-fingerprint -subject_hash-issuer_hash-subject_hash_old-issuer_hash_old
//查看证书用途
openssl x509 -purpose-noout-in user.cer
· -x509—— 此选项输出自签名证书。这通常用于生成测试证书或自签名根证书。添加到证书的扩展项(如果有)在配置文件中指定。除非使用set_serial选项,否则将使用较大的随机数作为序列号。
· -days n—— 当使用-x509选项时,指定证书的有效期。默认为30天。
· -set_serial n—— 输出自签名证书时使用的序列号。如果前缀为0x,则可以将其指定为十进制值或十六进制值。
注意
· PEM格式使用头部和尾部:
—–BEGIN CERTIFICATE—–
—–END CERTIFICATE—–
它还将处理包含的文件:
—–BEGIN X509 CERTIFICATE—–
—–END X509 CERTIFICATE—–
可信任的证书有以下行:
—–BEGIN TRUSTED CERTIFICATE—–
—–END TRUSTED CERTIFICATE—–