利用openssl命令搭建私有CA管理证书
利用openssl命令搭建私有CA管理证书
- 一:PKI
- 二:SSL协议
- 三:自建CA颁发机构和自签名
- 3.1 搭建私有CA认证中心
- 3.2 申请证书
- 3.3 文件说明
- 四:吊销证书
一:PKI
CA中心——CA系统——数字证书
CA 中心管理并运营 CA 系统,CA 系统负责颁发数字证书。
专门负责颁发数字证书的系统称为 CA 系统,负责管理并运营 CA 系统的机构称为 CA 中心。所有与数字证书相关的各种概念和技术,统称为 PKI(Public Key Infrastructure)。
- 签证机构:CA(Certificate Authority)
- 注册机构:RA(Register Authority)
- 证书吊销列表:CRL(Certificate Revoke Lists)
- 证书存取库
X.509:定义了证书的结构和认证协议的标准。包括版本号、序列号、签名算法、颁发者、有效期限、主体名称、主体公钥、CRL分发点、扩展信息、发行者签名等
获取证书的两种方法:
- 使用证书授权机构
生成签名请求(csr)
将csr发送给CA
从CA处接收签名 - 自签名的证书
自已签发自己的公钥重点介绍一下自建CA颁发机构和自签名。
二:SSL协议
SSL (Secure Socket Layer)是Netscape所研发用保障Internet数据传输安全利用数据加密(Encryption)技术确保数据网络。传输程截取及窃听目前般通用规格40 bit安全标准美则已推128 bit更高安全标准限制境要3.0版本I.E.或Netscape浏览器即支持SSL。它已被广泛地用于Web浏览器与服务器之间的身份认证和加密数据传输.它位于TCP/IP协议与各种应用层协议之间,为数据通讯提供安全支持。
SSL (Secure Socket Layer) 协议提供的服务主要有:
1)认证用户和服务器,确保数据发送到正确的客户机和服务器;
2)加密数据以防止数据中途被窃取;
3)维护数据的完整性,确保数据在传输过程中不被改变。
SSL协议的工作流程:
服务器认证阶段:
1)客户端向服务器发送一个开始信息“Hello”以便开始一个新的会话连接;
2)服务器根据客户的信息确定是否需要生成新的主密钥,如需要则服务器在响应客户的“Hello”信息时将包含生成主密钥所需的信息;
3)客户根据收到的服务器响应信息,产生一个主密钥,并用服务器的公开密钥加密后传给服务器;
4)服务器恢复该主密钥,并返回给客户一个用主密钥认证的信息,以此让客户认证服务器。
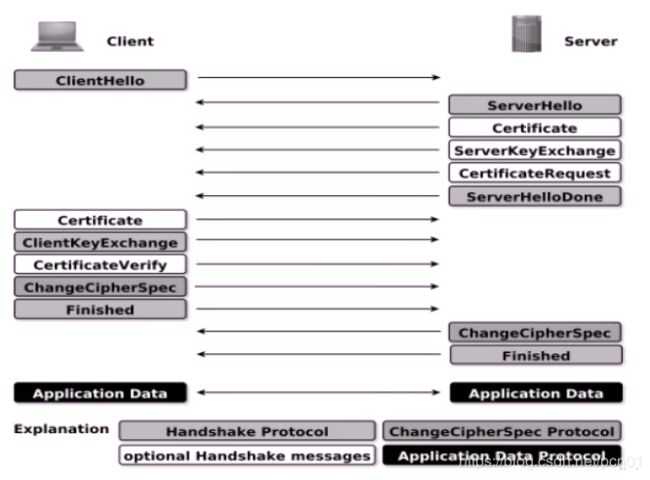
三:自建CA颁发机构和自签名
环境准备:
| IP地址 | Hostname | 操作系统 | 用途 |
|---|---|---|---|
| 172.17.2.245 | node245.ginvip.com | CentOS7.4 | CA认证中心 |
| 172.17.2.246 | node246.ginvip.com | CentOS7.4 | 请求签名证书 |
3.1 搭建私有CA认证中心
openssl的配置文件:/etc/pki/tls/openssl.cnf
####################################################################
[ ca ]
default_ca = CA_default # The default ca section(默认的CA配置,是CA_default,下面第一个小节就是)
####################################################################
[ CA_default ]
dir = /etc/pki/CA # Where everything is kept (dir变量)
certs = $dir/certs # Where the issued certs are kept(认证证书目录)
crl_dir = $dir/crl # Where the issued crl are kept(注销证书目录)
database = $dir/index.txt # database index file.(数据库索引文件)
new_certs_dir = $dir/newcerts # default place for new certs.(新证书的默认位置)
certificate = $dir/cacert.pem # The CA certificate(CA机构证书)
serial = $dir/serial # The current serial number(当前序号,默认为空,可以指定从01开始)
crlnumber = $dir/crlnumber # the current crl number(下一个吊销证书序号)
# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL(下一个吊销证书)
private_key = $dir/private/cakey.pem# The private key(CA机构的私钥)
RANDFILE = $dir/private/.rand # private random number file(随机数文件)
x509_extensions = usr_cert # The extentions to add to the cert
# Comment out the following two lines for the "traditional"
# (and highly broken) format.
name_opt = ca_default # Subject Name options(被颁发者,订阅者选项)
cert_opt = ca_default # Certificate field options(认证字段参数)
# Extension copying option: use with caution.
# copy_extensions = copy
# Extensions to add to a CRL. Note: Netscape communicator chokes on V2 CRLs
# so this is commented out by default to leave a V1 CRL.
# crlnumber must also be commented out to leave a V1 CRL.
# crl_extensions = crl_ext
default_days = 365 # how long to certify for (默认的有效期天数是365)
default_crl_days= 30 # how long before next CRL
default_md = sha256 # use SHA-256 by default
preserve = no # keep passed DN ordering
# A few difference way of specifying how similar the request should look
# For type CA, the listed attributes must be the same, and the optional
# and supplied fields are just that :-)
policy = policy_match # 是否匹配规则
# For the CA policy
[ policy_match ]
countryName = match # 国家名是否匹配,match为匹配
stateOrProvinceName = match # 州或省名是否需要匹配
organizationName = match # 组织名是否需要匹配
organizationalUnitName = optional # 组织的部门名字是否需要匹配
commonName = supplied # 注释
emailAddress = optional # 邮箱地址
# For the 'anything' policy
# At this point in time, you must list all acceptable 'object'
# types.
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
####################################################################
重点关注下面的几个参数:
dir = /etc/pki/CA # Where everything is kept (dir变量)
certs = $dir/certs # Where the issued certs are kept(认证证书目录)
database = $dir/index.txt # database index file.(数据库索引文件)
new_certs_dir = $dir/newcerts # default place for new certs.(新证书的默认位置)
certificate = $dir/cacert.pem # The CA certificate(CA机构证书)
serial = $dir/serial # The current serial number(当前序号,默认为空,可以指定从01开始)
private_key = $dir/private/cakey.pem # The private key(CA机构的私钥)
1:创建所需要的文件
touch /etc/pki/CA/index.txt # 生成证书索引数据库文件
echo 01 > /etc/pki/CA/serial # 指定第一个颁发证书的序列号,16进制数,比如可以从1a开始,一般从01开始。
2:生成私钥
[root@node245 ~]# (umask 066;openssl genrsa -out /etc/pki/CA/private/cakey.pem 4096)
Generating RSA private key, 4096 bit long modulus
.........................................++
..........++
e is 65537 (0x10001)
3:生成自签名证书
[root@node245 ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 7300 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:hunan
Locality Name (eg, city) [Default City]:changsha
Organization Name (eg, company) [Default Company Ltd]:ginvip
Organizational Unit Name (eg, section) []:m24
Common Name (eg, your name or your server's hostname) []:ca.ginvip.com # 会出现在证书的颁发者
Email Address []:admin@admin.com
参数解析:
-new: 生成新证书签署请求
-x509: 专用于CA生成自签证书
-key: 生成请求时用到的私钥文件
-days n:证书的有效期限
-out /PATH/TO/SOMECERTFILE: 证书的保存路径
查看生成的证书内容:
[root@node245 ~]# openssl x509 -in /etc/pki/CA/cacert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
88:42:ee:3c:55:7f:9e:ae
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=hunan, L=changsha, O=ginvip, OU=m24, CN=ca.ginvip.com/emailAddress=admin@admin.com
Validity
Not Before: Mar 22 12:53:33 2020 GMT
Not After : Mar 17 12:53:33 2040 GMT
Subject: C=CN, ST=hunan, L=changsha, O=ginvip, OU=m24, CN=ca.ginvip.com/emailAddress=admin@admin.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
...................................
3.2 申请证书
上面的CA认证中心在node245.ginvip.com主机上操作
在需要使用证书的主机上生成证书请求(node246.ginvip.com主机)
1:生成私钥
[root@node246 ~]# (umask 066; openssl genrsa -out /root/tools/service.key 4096)
2:生成证书请求文件
注意:默认国家,省,公司名称三项必须和CA一致
[root@node246 ~]# openssl req -new -key /root/tools/service.key -out /root/tools/service.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN # 必须与上面申请CA证书时填写的要一致
State or Province Name (full name) []:hunan # 必须与上面申请CA证书时填写的要一致
Locality Name (eg, city) [Default City]:changsha
Organization Name (eg, company) [Default Company Ltd]:ginvip # 必须与上面申请CA证书时填写的要一致
Organizational Unit Name (eg, section) []:IT
Common Name (eg, your name or your server's hostname) []:*.ginvip.com # 指定域名,必须唯一
# 下面的选项可留空,直接回车即可
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
3:将证书请求文件传输给CA
[root@node246 ~]# scp tools/service.csr [email protected]:/etc/pki/CA/csr/
4:CA签署证书,并将证书颁发给请求者
[root@node245 CA]# openssl ca -in /etc/pki/CA/csr/service.csr -out /etc/pki/CA/certs/service.crt -days 100
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Mar 22 13:29:18 2020 GMT
Not After : Jun 30 13:29:18 2020 GMT
Subject:
countryName = CN
stateOrProvinceName = hunan
organizationName = ginvip
organizationalUnitName = IT
commonName = *.ginvip.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
89:94:EF:12:25:AA:9C:5B:5E:E4:FC:B3:99:90:7D:60:44:34:D9:AA
X509v3 Authority Key Identifier:
keyid:16:23:4C:19:42:5F:92:9D:88:FA:94:B1:6C:E8:82:8B:22:7B:B0:BF
Certificate is to be certified until Jun 30 13:29:18 2020 GMT (100 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
把 /etc/pki/CA/certs/service.crt 证书回传给申请者,申请者可以使用此证书。
3.3 文件说明
服务器:
1:cakey.pem:私钥
2:cacert.pem:自签名证书------根据私钥(cakey.pem)生成自签名证书(cacert.pem)
客户端:
key:自己的私钥
csr:客户端根据自己私钥生成的申请证书文件
crt:服务器颁发给客户端的证书
四:吊销证书
[root@node245 CA]# cat index.txt
V 200630132918Z 01 unknown /C=CN/ST=hunan/O=ginvip/OU=IT/CN=*.ginvip.com
# V表示证书有效;R表示证书被吊销
[root@node245 CA]# openssl ca -revoke newcerts/01.pem
吊销证书的编号:
注意:第一次更新证书吊销列表前,才需要执行
[root@node245 CA]# openssl ca -gencrl -out cal.pem //更新证书吊销列表