Gartner 2018 年WAF魔力象限报告:云WAF持续增长,Bot管理与API安全拥有未来
来源 https://www.freebuf.com/articles/paper/184903.html
AngelaY 2018-09-19 *AngelaY 编译整理,转载请注明来自 FreeBuf.COM
8 月 29 日,Gartner 发布 2018 年度 Web 应用防火墙(WAF)魔力象限,这是 Gartner 自 2014 年之后连续第五年发布此类报告。报告中照例描述了全球 WAF 市场整体状况,并对主要 WAF 厂商进行了详细的优缺点分析。今年 Gartner 的评判标准有所提高,并对未来 WAF 市场的趋势做出了新的预测。
本份报告依旧为为企业安全团队提供了参考,可用于评估 WAF 如何在满足数据隐私需求的情况下,为企业提供易于使用和管理的安全服务。
近年来,企业纷纷采取云 WAF 服务来保护自己的业务安全,带动 WAF 市场的不断增长。2017 年的 Gartner WAF 魔力象限所得出的结论是云 WAF 将替代物理设备成为主流,这一结论在 2018 年 Gartner WAF 魔力象限报告中得到了验证。
战略规划展望
到 2020 年,独立的 WAF 硬件设备在新部署的 WAF 中所占的比例将不到 20%,明显低于目前的 35%。
到 2023 年,30% 以上面向公众的 Web应用将受到云 Web 应用和 API 保护(WAAP)服务的保护,与目前的 10% 相比将有巨大提升。分布式拒绝服务(DDoS)防御、bot 环节服务、API 保护和 WAF 等功能,可以为 Web 应用提供更好的安全保护。
WAF 市场现状
客户对于保护公共和内部 Web 应用的需求推动了 WAF 市场。 WAF 可保护 Web 应用和 API 远离自动化攻击(机器人程序)、注入攻击和应用层拒绝服务(DoS)等多种攻击。合格的 WAF 不仅提供基于特征的防护,还应支持主动安全模型(自动白名单)及/或异常检测。
WAF 通常部署在 Web 服务器的前端,旨在保护 Web 应用远离内部和外部的攻击、监控 Web 应用的访问,同时收集访问日志用于合规/审计和分析。WAF 通常以物理或虚拟设备的形式存在,现在已经逐渐通过云 WAF 服务的方式交付。WAF 最常以反向代理的方式进行嵌入式部署,因为以往反向代理是执行深入检测的唯一途径。目前,WAF 还可以采用其他部署模式。当前形势下,云 WAF 服务的兴起、有意设置反向代理来执行任务以及采用更新颖的需要解密嵌入式流量拦截(中间人攻击)的传输层安全(TLS)套件等都加大了反向代理的使用。
云WAF 服务将由云交付的 XX即服务部署与订阅模式结合起来。云WAF服务提供商可以提供托管服务;对于一些客户来说,它是使用 WAF的必备组件。一些供应商选择利用现有的 WAF 解决方案,将其重新包装成 SaaS。这使得供应商能够更快地向客户提供云 WAF 服务,而且可以利用现有功能,有别于功能特性相对有限的云原生 WAF 服务产品。这种方法的一个难点是简化管理和监控控制台,继承全面的 WAF 设备功能特性,以满足客户对易用性的期望,又不缩小安全范围。Gartner 将云 Web 应用和 API保 护(云 WAAP)服务定义为现有云 WAF 服务的演进。从长远来看,云 WAF 服务一开始就采用多租户模式、以云为中心,避免了花高昂的成本来维护遗留代码。它们还提供竞争优势,更快的发布周期,迅速实施创新的功能。一些企业使用由 WAF 设备构建的云 WAF 服务,这么做是为了获得统一的管理和报告控制台。
该魔力象限包括部署在 Web 应用程序外部而不直接集成到 Web 服务器上的 WAF:
专用的物理、虚拟或软件设备;
嵌入在应用交付控制器(ADC)中的WAF模块;
云 WAF 服务,包括嵌入在较大云平台中的 WAF 模块(比如内容交付网络,CDN),以及直接从基础设施即服务(IaaS)平台交付的云 WAF 服务;
IaaS平台上提供的虚拟设备,以及来自 IaaS 提供商的 WAF 解决方案。
API网关、bot 管理(包括恶意 bot 防范和善意 bot 白名单机制)以及 RASP 可以算是 WAF 服务的竞品,可能会与 WAF 服务争夺客户。这可以激励 WAF 厂商在合适的时机为 WAF 服务增添竞品的功能。例如,基于云的 WAF 服务可以将 Web 应用安全和 DDoS 防护及 CDN 结合在一起。WAF 能够与安全测试(AST)、Web 访问管理(WAM)或安全信息和事件管理(SIEM)等其他企业安全技术结相合,这一特点让 WAF 在市场上占据上风。WAF 与 ADC、CDN 或 DDoS 防护云服务等其他技术结合,既能带来优势也能带来挑战。然而,说到 Web 应用安全,市场评估更侧重于顾客的安全需求。因而,WAF 技术在以下几方面的表现就比较重要:
尽量提高已知和未知威胁的检测率和捕获率;
尽量减少虚假警报(误报),并灵活适应不断发展的 Web 应用;
可区别自动化流量和人类用户,并对这两类流量实施适当的控制;
借助易于使用和影响最小的优点,促进 WAF 得到更广泛的应用;
实现事件响应工作流程自动化,帮助 Web 应用安全分析员高效工作;
不光保护内部使用的 Web 应用和 API,还保护面向公众的 Web 应用和 API;
Gartner 充分利用通用特征规则集,认真分析了这些功能和创新技术,检测它们提升 Web 应用安全的功效。这些功能和技术的效果超出了网络防火墙、入侵检测系统(IPS)以及开源/免费 WAF(如 ModSecurity)等通过利用普通签名规则集所达到的安保效果。
Gartner加强了入围今年 Web 应用防火墙魔力象限的标准,体现企业在选择 WAF 提供商时不断变化的要求。经过更新的标准包括要求厂商在本埠之外的区域有最基本的收入,因此一些本地厂商被排除在外。
魔力象限
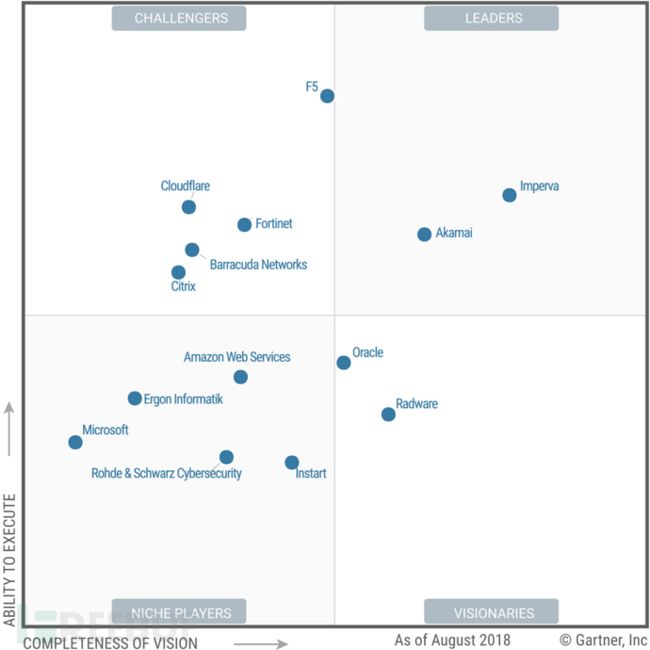
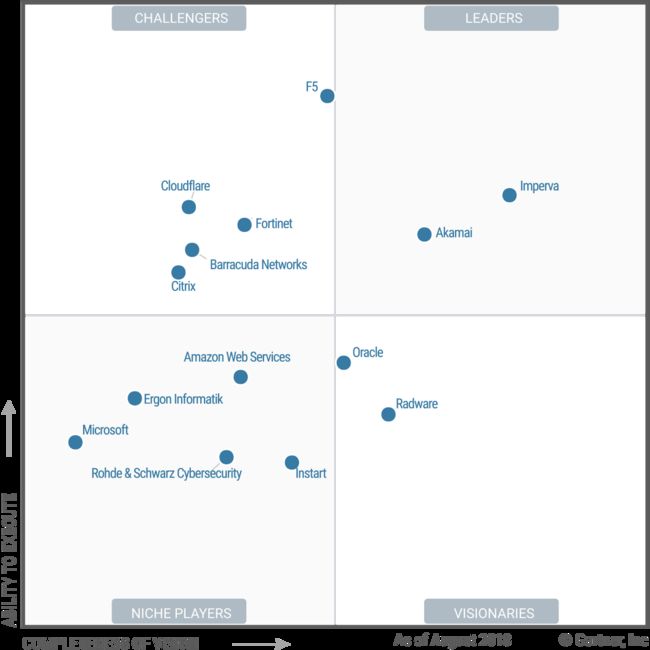
图1 WAF 魔力象限 2018
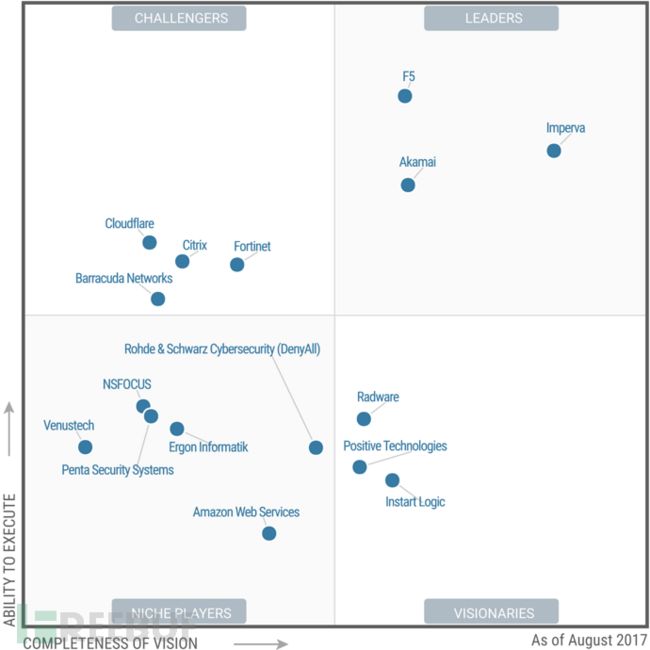
图2 WAF 魔力象限 2017
今年的 WAF 魔力象限如上图所示,其中:
处于 Leader 象限的厂商有: Akamai、Imperva;
处于 Challenger 象限的厂商有:F5、Fortinet、Cloudflare、Citrix、Barracuda Networks;
处于 Niche Players 象限的厂商有:Instart、Amazon Web Services、Rohde & Schwarz Cybersecurity、Ergon Informatik、Microsoft;
处于 Visionarie 象限的厂商的有:Oracle 和 Radwarea
厂商增减
2018 年,Gartner 更新了魔力象限准入标准,以便反应企业更真实更迫切的需求。其中一项要求就是厂商要在本埠之外也有客户群。Gartner 观察到越来越多的小型供应商在本地区与开展业务,更多的 CDN 和 ADC 供应商将 WAF 作为一项功能添加到产品或服务当中。为了反映全球 WAF 需求方的更严格要求,本次魔力象限包要求 WAF 供应商必须有超过 5% 的客户群位于其本国区域之外,这个标准值得注意。
由于标准有所变化,本年度的 WAF 魔力象限中的厂商也有所增减。
新增的厂商有:
Microsoft (Azure)
Oracle (收购了 Zenedge)
相较去年未上榜的厂商有:
NSFOCUS
Penta Security
Positive Technologies
Venustech
此外,F5 从 2017 年的 Leaders 象限跌到了 Challenger 的象限。
Gartner 关于 Leaders 象限的 Imperva 以及 Akamai 的简介与评估如下,相关厂商可以用于参考。
Imperva
Imperva 是一家应用程序、数据库和文件安全供应商,其产品组合包括数据库安全产品(SecureSphere Data Protection 和 Database Audit and CounterBreach),WAF 设备(SecureSphere WAF)和云 WAF 服务(Incapsula)。 Imperva 还提供托管安全服务和托管 SOC。
Gartner 认为 Imperva 的优势首先在于其营销策略。它不仅为具有内部部署和云托管应用程序组合的组织提供灵活的产品或服务搭配,还是少有的同时提供 WAF 设备和云 WAF 服务的供应商。同时,Imperva 还注重客户体验,在产品上搭载 ThreatRadar 的共享威胁情报,且不断更新改进。在地理战略上,Imperva 在大多数地区都提供产品和持续有效的支持,近期在亚太地区的表现尤为突出。
但值得注意的是,由于 Imperva 正在经历众多组织变革,因此其发布速度有所放缓,且市场响应能力需要加强。同时,客户对于其云 WAF 服务有更多的期待,如单点登录(SSO)以及更详细灵活的固定报告等。客户认为,当前 Imperva 的云 WAF 服务尚不能与其设备产品线涵盖的安全功能的深度和广度相匹配,且覆盖面不够广泛,部分产品定价较高。此外,高级功能对应的管理控制台依然复杂、跨站点和多域管理与报告有限等问题也是客户希望改进的问题。
Akamai
Akamai 是一家全球 CDN 提供商,有专门研究 Web 应用程序安全的团队。除了 WAF(Kona Site Defender)之外,Akamai 还提供其他安全服务,包括应用程序访问控制(企业应用程序访问)、托管 DDoS 清理服务(Prolexic)、API 网关(Akamai API网关)和 DNS 服务(快速 DNS)等 。 Akamai 还提供精简版和低成本的 Kona Site Defender 版本,也就是 Web 应用防护(WAP)。
Gartner 认为 Akamai 的优势在于不断开发和改进其 Web应用程序安全解决方案,并不断发展威胁研究和安全运营中心(SOC)团队。在云服务方面,Akamai 提供广泛的产品组合,适用于需求不同的用户。Akamai 在北美和欧洲都有广泛的业务网,能够对其处理的整个流程自动分析和分类,为客户提供托管服务等,这些都收获了较好的口碑。
同时,值得注意的是,Akamai 的 WAF 服务仅仅通过云的方式提供,这就无形中少了很多不使用或不方便使用云安全解决方案的客户。此外,Akamai 的 WAF 服务定价相对较高且捆绑很多选项。其政策管理系统体验较差,且没有有效方法测试更新的规则,在安全自动化以及主动安全模型方面也有所欠缺。
报告背景
Gartner 认为,客户企业及组织应当结合自身情况,综合考虑每个象限中厂商,基于功能和实际需求来选择产品和服务。事实上,WAF 市场中有很多规模较小的供应商,或者供应商的 WAF 业务只占到所有业务的很小一部分。如果客户需要选择 WAF 产品或服务,还需要考虑到自身的特殊需求,如部署方式、部署规模、合规、机密业务泄露风险、客户 Web 应用以及厂商的本地支持和市场熟悉程度等。
考虑部署 WAF 的安全管理专家应当首先考虑自身的部署限制,尤其要考虑以下几个方面:
是否能接受在 Web 应用中全面部署反向代理类嵌入式 WAF,因为这类 WAF 有屏蔽功能;
考虑不同 WAF 交付(针对专用应用、CDN、ADC以及云服务等)的优势和不足( 特定应用、CDN、ADC、云服务)
SSL 解密/重加密以及其他扩展需求
WAF 市场概览
据 Gartner 估计,2018 年 WAF 市场总值将达到 8 亿 5300 万美元,与 2017 年的 7 亿 6200 万美元相比增长了 11.9%。其中,美洲市场份额占总市场的 47.6% ,欧洲、中东、非洲三个地区总共占 31.2%,亚洲/太平洋地区占 21.2%,
随着越来越多的企业通过面向公众的应用程序(包括 API 驱动的移动或物联网应用程序)助力新的数字业务,Web 应用安全受到的重视日渐增加。根据 Verizon 的报告,网络应用程序是导致 2017 年数据泄露的头号攻击渠道。
Gartner 在与客户交流 WAF 使用情况时,发现有些客户会将 WAF 与网络防火墙上的应用程序控制功能(应用程序感知)相混淆。WAF 的主要优势和特点就在于防范企业开发的 Web 应用代码中“自己造成的”安全漏洞,同时防范现成的 Web 应用软件中的安全漏洞。如果不使用 WAF,那些主要用于防范已知 exploit 的其他技术将无法防范此类漏洞。此外,调查显示,针对这些企业 Web 应用的攻击大多数来自外部攻击者 。
Gartner 发现需要部署云 WAF 服务和需要部署 WAF 设备的客户之间存在不同的期望:
寻求云 WAF 服务的组织通常期望服务附带多个捆绑功能(特别是DDoS保护,bot 管理和 CDN 等),而这些功能都能通过易于部署且易于操作的软件包实现。此外,他们也愈发需要更深入的安全控制以及更优化的配置选项粒度。但是,对他们而言,部署 WAF 通常需要很多时间,这给他们带来不少压力;
寻找 WAF 设备(物理和虚拟)的组织更有可能已经安装了 WAF 设备。 他们对主动安全模型、高级安全功能以及 WAF 在事件响应工作流程中的集成提出了更高的期望。
WAF 市场趋势
Gartner 观察发现,WAF 市场有以下发展趋势:
来自 ADC 厂商的物理设备销量和 WAF 模块部署数量都在下降;同时,大部分厂商的销量都在经历下降,只有一些供应商在阅收入增加的推动下实现了缓慢的个位数增长;
云 WAF 服务继续稳步增长。目前,云 WAF 市场占整个 2017 年 WAF 市场的 35% 以上。最初就做云 WAF 解决方案的供应商相较于传统供应商具备更强的竞争力。在调查中,提供 WAF 服务的 IaaS 供应商依然处于初级阶段;
更多组织希望使用云 WAF“关注应用程序”;倾向于使用保守方法在本地和 IaaS 上使用相同 WAF 设备的组织也有增加的趋势。此外,多层战略已经纳入整体策略,从而激励人们实现更加统一的管理和报告。
云 WAF 服务更常用于面向公众的应用程序。云 WAF 设备的大规模部署过程很复杂,这仍然是云 WAF 的竞争劣势。 Web 应用程序策略可践行“混合方法”,使用与 WAF 设备最佳实践相同的 WAF 技术来保护内部部署和云托管资产。
此外,WAF 市场还面临相近技术的竞争,并且还更频繁地面临替代方法的挑战。包含传统 WAF 和 RASP 应用工具的解决方案、使用分析后端检测客户群攻击模式的方法、为各个传感器(例如Signal Sciences或tCell)提供更新等多种方式和方法,对于 WAF 而言都是挑战。
Bot 管理正在发展,API 安全性紧随其后
在过去几个月中,区分自动流量与人类客户的能力已成为 WAF 的一项更重要要求。 Bot 程序缓解和合理的僵尸处理已经成为通过审查的功能,WAF 供应商也正在调整产品,赋予产品更多功能。较大的企业针对专业供应商(如 Distil Networks、PerimeterX、Shape Security 和 Stealth Security 等)的 WAF 进行评估,以缓解僵尸攻击。传统的基于知名度检测和指纹控制的技术如今已经足够阻止低端和慢速高级僵尸,因此更多企业在其 RFP 中增加了行为分析的要求。 Gartner 预计 bot 管理(包括 bot 程序缓解和合理的僵尸处理)将成为不久的将来 WAF 评估所注重的核心功能。
API 安全性功能也将经历类似的发展,但目前对于这一功能的市场意识还不够高。此前,许多组织将 API 管理网关视为临时解决方案。Gartner 预测,到 2022 年,“API滥用将成为最常见的攻击媒介,导致企业 Web 应用程序出现数据泄露。”目前只有一些WAF 供应商提供基本的 API 安全功能,这一情况在未来会随着专业 API 安全厂商的出现而有所改善。
=====================================================================
Magic Quadrant for Web Application Firewalls
来源 https://www.gartner.com/doc/reprints?id=1-5ELTARA&ct=180904&st=sb
Published 29 August 2018 - ID G00340592 - 71 min read
Strategic Planning Assumptions
Market Definition/Description
-
Purpose-built physical, virtual or software appliances
-
WAF modules embedded in application delivery controllers (ADCs; see “Magic Quadrant for Application Delivery Controllers”)
-
Cloud WAF service, including WAF modules embedded in larger cloud platforms, such as content delivery networks (CDNs), and cloud WAF services delivered directly from infrastructure as a service (IaaS) platform providers
-
Virtual appliances available on IaaS platforms, as well as WAF solutions from IaaS providers
-
Maximizes the detection and catch rate for known and unknown threats
-
Minimizes false alerts (false positives) and adapts to continually evolving web applications
-
Differentiates automated traffic from human users, and applies appropriate controls for both categories of traffic
-
Ensures broader adoption through ease of use and minimal performance impact
-
Automates incident response workflow to assist web application security analysts
-
Protects public-facing, as well as internally used, web applications and APIs
Magic Quadrant
Vendor Strengths and Cautions
Akamai
Strengths
-
Product Strategy: Akamai demonstrates a sustained commitment to develop and improve its web application security solutions. The vendor also grows its threat research and security operations center (SOC) team at a good pace.
-
Product Offering: the broad portfolio of Akamai’s cloud services, appeals to organizations looking for an easy way to deploy controls in front of a diverse set of applications. Many customers using Kona Site Defender are using other services, especially the CDN.
-
Geographic Strategy: Akamai is a global infrastructure provider with especially strong presence in North America, and good visibility in European shortlists too.
-
Managed Services: Akamai offers professional services to help harden the security configuration of Kona Site Defender. It also provides a managed SOC, which can monitor incidents.
-
Capabilities: Akamai applies automated analytics and triage on the entire traffic it processes for clients to tune their signatures and gather threat intelligence to create new protections. It has released a first version of API security features that customers find promising.
-
Customer Experience: Customers using Akamai managed security services and customers using the WAP product cite a lower-than-expected rate of false alerts.
Cautions
-
Market Segmentation: Akamai’s WAF is available as a cloud service only. For organizations that are simply not comfortable with cloud security solutions, or where prospective clients’ assessments determine that compliance and regulatory restrictions limit its use, Akamai does not appear on client shortlists.
-
Pricing and Contracting: Akamai Kona is an expensive product, especially when bundling multiple options, such as Bot Manager subscriptions. Clients continue to cite pricing as a barrier. Gartner analysts have observed an increase in complaints from prospects, and from existing clients. Organizations frequently consider using a second WAF brand, because it would be too expensive for them to deploy Akamai’s solution. The less-expensive WAP solution has not yet fixed this issue.
-
Customer Experience: The most-vocal complaints from clients target the poor policy management system, which is leaving clients frustrated by a dated policy and no useful way to test the updated rules. They also would like to see more improvements in the monitoring and reporting, as well as improved notification options.
-
Technical Architecture: Akamai has historically lagged behind some of its competitors in security automation. It has published a first version of an API to manage Kona’s security configuration, which is still in beta.
-
Capabilities: Akamai lacks a positive security model, with the exception of its API protection module. Customers using WAP cannot use Bot Manager.
Amazon Web Services
Strengths
-
Capabilities: With managed rulesets, AWS customers have access to more than a dozen sets of rules from established WAF or managed security service (MSS) vendors that are automatically updated. Because they can deploy multiple rulesets simultaneously, it is easy, even if it comes at a cost, to provide multiple layers of defense, or to test multiple providers.
-
Customer Experience: Existing AWS customers appreciate being able to quickly deploy and enable AWS WAF. Customers give good scores to the autoscaling and built-in integration with Cloudfront.
-
Capabilities: AWS WAF helps organizations in a DevOps mode of operation with the full-featured APIs and CloudFormation automation. AWS customers can provision a set of WAF rules for each stack, or provision a set of WAF rules, and automate the association of those rules with a new stack.
-
Roadmap Execution: AWS continues to regularly improve its WAF, releasing relevant features to close existing gaps, such as the recent firewall manager, at the time they are announced.
-
Sales Execution: AWS WAF is integrated in AWS Shield Advanced. For customers not using AWS Shield Advanced, AWS charges per use for AWS WAF are based on how many rules customers deploy and how many web requests are inspected.
Cautions
-
Marketing Strategy: AWS WAF’s reach is mainly limited to AWS workload protection, where it competes with cloud WAF services and virtual appliances. As more clients consider a multicloud strategy, AWS WAF is less likely to be on WAF shortlists.
-
Capabilities: AWS WAF lacks bot detection techniques, relying on reputation-based controls. Customers need to deploy AWS API Gateway to get dedicated API security features, because AWS does not parse JavaScript Object Notation (JSON) or XML. The vendor does not offer managed SOC for AWS WAF as part of its SiteShield managed services offering. Its DDoS Response Team (DRT) focuses on DDoS response only.
-
Product Strategy: Despite numerous corporate security initiatives, the WAF product remains mostly a siloed product. The vendor does not yet have a dedicated threat research team to add new protections to the WAF. AWS WAF does not leverage AWS AI capabilities, the use of machine learning for web app security is built-in only for DDoS protection.
-
Customer Experience: Customers would like to be able to whitelist a specific rule from the managed ruleset. Currently, they can only disable the entire ruleset, and have trouble identifying why a rule was triggered.
-
Customer Experience: Clients cite logging and reporting as a weakness. They cannot get detailed logging, aggregated events and mention occasional delays in getting the logs. Some clients also request integration with SIEM.
Barracuda Networks
Strengths
-
Offering Strategy: Barracuda remains one of the most visible WAFs on Microsoft Azure. Customers are then more likely to select Barracuda in multicloud strategy for unified management.
-
Pricing Strategy: Barracuda Cloud WAF as a Service includes DDoS protection at no additional charge.
-
Product Offering: With the release of the WAF appliance 1060, Barracuda now supports throughput as high as 10 Gbps.
-
Technical Support: Gartner clients across multiple regions give excellent scores to Barracuda’s customer support. Barracuda partners cite the vendor’s focus on customer satisfaction as the reason they choose to sell Barracuda WAF.
-
Capabilities: Barracuda’s offer of the free WAF add-on Vulnerability Remediation Service is attractive to Barracuda’s targeted small or midsize business (SMB) customers, which often lack the time, money and expertise to support an in-house application scanning program.
Cautions
-
Sales and Marketing Execution : Barracuda struggles to adapt to the multiplication of meaningful competitors. Its visibility in shortlists is shrinking, and the vendor has lost market share during the past 12 months.
-
Customer Experience: Many customers have complained about Barracuda’s WAF appliance user interface (UI). They cite a long learning curve, difficulties locating features buried in submenus and longer-than-necessary amounts of time spent updating the configuration.
-
Market Responsiveness: Barracuda has been late to the market in providing cloud WAF as a service. Prospects should scrutinize the vendor’s infrastructure and point-of-presence availability across regions, as well as investigate the vendor’s ability to meet enterprise-class SLAs for availability, because the solution remains a recent addition.
-
Capabilities: Despite recent improvements, Barracuda WAF lags behind the leaders in bot mitigation and advanced analytics for anomaly detection. Its predefined list of good bots is limited to a few search engines.
-
Capabilities: Barracuda WAF lacks access management features and support for Oauth.
-
Capabilities: Barracuda WAF lags behind the leaders in security monitoring. It lacks automated alert aggregation in the real-time log view, and users report that they would like to see more improvements.
Citrix
Strengths
-
Sales Execution: Citrix licenses its products and service through multichannel globally, which makes Citrix the No. 2 ranked ADC vendor (by revenue). This creates opportunities for selling a WAF module on top of its ADC appliances. Existing ADC and Citrix-based application customers like the tight integration of the AppFirewall module.
-
Capabilities: NetScaler’s ability to scale appeals to large organizations. NetScaler TLS’s decryption capabilities and integration with Thales and SafeNet hardware security modules (HSMs) are often key differentiators in prospect comparative testing.
-
Customer Experience: Customers score highly the support they receive from system integrators and service providers. They also praise improvements in API-driven manageability.
-
Customer Experience: Surveyed customers welcomed NetScaler management and analytics service (MAS), and give good scores to the Security Insight dashboards.
Cautions
-
Product Strategy: Citrix faces intense competition from many large and small vendors on its leading products. Acquisitions have been a significant part of its growth strategy. However, most of the recent acquisitions (CedexisInx, Norskale, Contrade and Unisdesk) have little to do with security and will take attention from innovating on the WAF technology.
-
Sales Execution: Citrix rarely competes in dedicated WAF deals, and its overall visibility has continued to decrease. The vendor mostly sells AppFirewall as an add-on to customers primarily interested in its ADC features, or in high-performance environments.
-
Technical Architecture: Most Citrix clients use NetScaler AppFirewall as a software option on top of an ADC physical appliance. Gartner rarely sees Citrix being deployed on IaaS, such as Amazon and Microsoft. Google Cloud is not supported.
-
Capabilities: AppFirewall does not include advanced bot mitigation and anomaly detection options.
-
Market Responsiveness: The pace of WAF features release on Netscaler has been slow for a few years now, except for TLS decryption-related capabilities. Although Citrix is only now catching up to its competitors in cloud WAF delivery, it has not gained visibility in shortlists against other cloud WAF vendors. Citrix cannot match competitors’ offerings, because it does not bundle CDN with its cloud WAF.
-
Customer Experience: Many customers would like better ways to handle false alerts (false positive rate). Citrix ability to block bots gets a low score. Clients would also like to see better documentation for the WAF advanced features.
Cloudflare
Strengths
-
Technical Architecture: Cloudflare is a provider with 15 Tbps capacity and 152 data centers worldwide. This infrastructure not only supports the high performance of the applications, it promotes a close-to-the-edge security protection capability.
-
Customer Experience: Customers typically score the ease of use and implementation of the WAF and DDoS solution highly. Customers also praise the vendor’s DDoS mitigation capabilities. Cloudflare has a large base of technically savvy individuals who use its solution for personal web applications, and then become internal sponsors when their organizations consider a cloud WAF.
-
Market Responsiveness: Cloudflare continually develops new capabilities related to better user experience in ease of use and implementation. Cloudflare has announced Spectrum, which is expanding DDoS protection beyond web servers to include other TCP-based services. The vendor also occasionally acquires technologies to more quickly serve new features, as they did when they acquired Neumob’s mobile SDK.
-
Capabilities: The recent addition of Cloudflare Workers enables customer to host web applications on Cloudflare’s infrastructure, which should appeal to smaller organizations. The vendor also provides an easy-to-reach, “I’m under attack” button. This automatically enables a set of protections, and is convenient for emergency reaction.
-
Capabilities: Cloudflare has recently released the ability to assign rules per uniform resource identifier (URI), improving its ability to provide more-granular control without damaging the security posture for the entire application. Its keyless SSL technology offers interesting support for customers that want to store their private keys on their preferred HSM solutions.
-
Geographic Strategy: Cloudflare is one of the few global providers with local points of presence in China.
Cautions
-
Market Segmentation: Cloudflare offers WAF as a cloud service only. For organizations with restrictions on cloud services, or in locations where the appetite for cloud services isn’t high (e.g., the Middle East and Asia regions), Cloudflare can’t address use cases that require on-premises physical or virtual appliances. The lack of WAF appliance might penalize them for the nascent hybrid web application deployment use cases (partly on-premises and partly cloud-hosted), where more-conservative organizations highly rank the ability to get unified management and reporting for the WAF solution.
-
Customer Experience: Many customers, especially the larger organizations, rated Cloudflare alert and reporting low. The vendor lacks an automated aggregation of alerts for faster incident triage. Some customers complain of occasional API instability, as well as a higher-than-expected frequency of local performance degradation.
-
Capabilities: Cloudflare’s management console presents restrictions on offering more-granular configuration capabilities, such as building custom-made rules. In addition, the management console’s role-based access shows its limits when users want to define the per-app role, or when auditing management actions.
-
Capabilities: Cloudflare still lags behind some of its competitors for bot management. It lacks an easy way to manage good bots. Despite a recent initiative to learn from the large amount of data the vendor processes, Captcha remains the most frequent technique Cloudflare uses to block bots. This hurts the user experience. The WAF also lacks an automated positive security model, which could prove useful, especially for high-risk pages or API-driven applications.
-
Product Strategy: Gartner observes thatCloudflare’s security roadmap appears to aim at good-enough security, with a focus on pervasive, commercial off-the-shelf (COTS) web applications (e.g., WordPress and Magento). Its web application security threat research team efforts are targeted at quick reaction in case of a new attack campaign. However, when it comes to using new protection techniques based on in-house threat research, the vendor is less proactive than its leading competitors.
Ergon Informatik
Strengths
-
Customer Experience: The vendor continues to get good feedback from faithful customers and resellers, who trust the company and praise its ability to be close to its clients. They almost always use the vendor’s IAM features and mention them as a differentiator.
-
Vertical Strategy: Ergon Informatik’s strongest presence is with banking and other financial institutions, where it can provide a large number of satisfied references.
-
Market Execution: Despite its smaller size, Ergon is a profitable company that enjoys growth at a rate that exceeds the WAF appliance market as a whole.
-
Customer Experience: Customers give good scores to Airlock WAF for its API security capabilities, and to the combination of access management features and content inspection on JSON and REST payloads.
-
Capabilities: The recent addition of geo-IP goes beyond blocking, and allows traffic to be redirected, based on the source’s region or country. Clients liked the real-time monitoring and logging upgrade, which provides the flexibility to build their own dashboards and advanced searches in log. Support for the CEF format improves the ability to integrate with SIEM vendors.
-
Capabilities: With the addition of automating whitelisting learning, Ergon Informatik now offers a comprehensive set of controls for positive security models, in addition to the already-available URL and cookie encryption features. It also provides predefined templates for known commercial applications, such as Microsoft Exchange.
Cautions
-
Product Strategy: Ergon is not a good choice for hybrid or cloud-native web applications. It does not offer cloud WAF or DDoS protection services, and has not shown any intention to pursue a cloud WAF service strategy. The vendor lacks centralized management for its WAF appliances, and its WAF virtual appliances are unavailable in the IaaS marketplace.
-
Market Segmentation: Ergon is not the best fit for smaller organizations. It offers only two hardware appliances (Medium and Large). Most customers mention that the deployment is not the easiest possible, and the management interface can be complex, especially for novice users.
-
Geographic Strategy: Ergon is predominantly visible in Swiss and German shortlists, with the exception of some rare appearances in Asian financial institution shortlists. The vendor has limited direct presence outside Western Europe. Prospects from other regions should first assess the ability of the vendor to provide support in their time zones and, if necessary, in local languages.
-
Capabilities: Airlock offers limited, role-based management with four predefined roles, and experimental command line interface (CLI)-based possibility to add custom roles. Its management API feature is not yet complete.
-
Capabilities: Airlock still lacks third-party or in-house threat intelligence feeds. Its generic rule set is updated only during firmware updates. This limits the ability of customers to benefit from ad hoc, emergency-released protections in case of a new attack campaign. The vendor also relies on integration with IBM Trusteer to provide bot mitigation.
-
Market Responsiveness: Ergon Informatik’s roadmap delivery contains a higher mix of continuous improvements of existing features.
F5
Strengths
-
Marketing Strategy: As its legacy ADC appliance market declines, F5 has identified security as one of the core markets for its new messaging. The vendor has publicly committed to reinforce its investment in security.
-
Technical Architecture: F5 supports AWS, Azure, Google Cloud, OpenStack and VMware Cloud. The support for multicloud with unified management appeals to the organizations building a hybrid architecture.
-
Capabilities: Clients continue to mention iRules as a reason to select, and to stick with ASM WAF. They also mention the depth and breadth of features available on the platform.
-
Customer Experience: Customers of the managed WAF services give good scores to their interactions with the professional services, and managed SOC teams. Surveyed customers like the multiple managed rulesets from F5, which can be deployed quickly on the top of AWS WAF.
-
Customer Experience: Several customers mention the user community and vendor support as strong assets.
Cautions
-
Product Strategy: With the existingSilverline product segmentation, F5 links its self-managed Silverline Express with the lower tier of the market, but positions it at a price point that’s much higher than its direct competitors. Gartner analysts see that as a missed opportunity for F5’s product strategy and its current portfolio gap. Larger enterprises are more likely to get in-house SOCs than midsize organizations, and most enterprises prefer self-service WAF options. F5 does not yet provide a fully-featured, and easy-to-manage self-service WAF.
-
Sales Execution: Gartner analysts observe limited adoption of Silverline products, and low visibility in cloud WAF shortlists.
-
Product Strategy: With Advanced WAF, F5 risks frustrating its core customer base, which has used WAF as a module of their ADC for years. They now fail to get the best security features, even when purchasing the “best” bundle, and need to get an additional security license upgrade.
-
Cloud WAF Service: Silverline’s infrastructure significantly lags behind its direct competitors. It lack a presence in South America, Middle East, Africa and China. It serves the entire Asia/Pacific (APAC) region from a single data center, hosted in Singapore.
-
Customer Experience: Many customers mention the need of the UI refresh, because it can be complex. They noted some improvement with the recently released hierarchy of policies.
-
Operations: F5 continues to experience big changes in its leadership, including a new lead for security business unit. Prospective clients should monitor early signs of strategic shift that could affect the investment on the appliance product line.
Fortinet
Strengths
-
Sales Execution: FortiWeb’s visibility in shortlists has improved, especially in Fortinet’s customer base.
-
Capabilities: Fortinet delivers strong threat intelligence, supported by the large team of its Fortiguard Labs, a shared resource for all Fortinet’s products. The vendor has strong ability to quickly deliver, and automatically deploy new targeted signatures, even before the attacks have gained enough scale to be visible globally. With FortiWeb 6.0, security analysts can search for attacks usingcommon vulnerabilities and exposures (CVE) IDs.
-
Marketing Strategy: Fortinet applies the same strategy to FortiWeb that drove FortiGate’s success. It offers a comprehensive portfolio of hardware appliances (eight models, ranging from 25 Mbps to 20 Gbps), and it wins on good price/performance ratio. The vendor also improves its WAF by leveraging global R&D efforts, to quickly mature its WAF solution, despite being a relatively recent entrant on the market. Recent release of FortiWeb Cloud now offers a solution to Fortinet’s large customer base of midmarket enterprises.
-
Capabilities: FortiWeb’s recent use of machine learning algorithms to complement ad hoc signatures and detect attacks from their behavior is promising. The syntax analysis pass on the request helps catch false alerts that could result from the new technique.
-
Capabilities: FortiWeb is a good choice to protect file-sharing services, because it offers comprehensive options and integration for malware detection. The WAF can inspect for malware, as well as integrate with Fortinet’s sandboxing solutions.
Cautions
-
Cloud WAF Service: Fortinet has been late releasing a first version of a cloud WAF service, which is still unproven, especially in its ability to avoid and mitigate false alerts. FortiWeb Cloud has more limited capabilities than its appliance counterpart, and it lacks available peer references.
-
Organization: The vendor has a modest increase of its WAF R&D department this year. Its investment in WAF remains less important than for other products in Fortinet’s portfolio, and is relatively small, compared with some of its direct competitors.
-
Market Segmentation: Fortinet is not yet visible in shortlists for web-scale organizations trying to protect their core business-critical applications, and for cloud-native web applications that heavily leverage continuous integration.
-
Customer Experience: Some customers would like Fortinet to go one step further and unify the centralized management for WAF and firewall. Today, you need two separate management platforms for FortiWeb and FortiGate. They also would like better documentation in the form of “how-to,” especially on recent features, and better change control.
-
Capabilities: FortiWeb lags behind leaders in bot mitigation. The vendor does not offer, nor does it integrate with DDoS protection service.
-
Capabilities: FortiWeb’s machine learning does not work in high-availability deployments. In the initial version, the UI exposes a lot of the internal mechanics behind the machine learning engine. Although it compares nicely with other vendors’ “black box” approaches, and this helps with the credibility of the engine, which can be intimidating and lengthen the learning curve.
Imperva
Strengths
-
Marketing Strategy: Imperva’s offers a flexible licensing for organizations with a mix of on-premises and cloud-hosted applications. It allows the vendor to target a wider range of use cases and organizations, and to better manage the transition from WAF appliance to cloud WAF service.
-
Sales Execution: Imperva is one of the only vendors providing both WAF appliances and cloud WAF service to achieve strong visibility in shortlists and large customer bases for both segments.
-
Customer Experience: Gartner clients using SecureSphere continue to praise customer support. They’ve noted some improvements in Incapsula’s bot mitigation.
-
Capabilities: Incapsula and SecureSphere benefit from the shared threat intelligence from ThreatRadar.
-
Capabilities: Imperva has recently released attack analytics to get unified and improved monitoring for SecureSphere and Incapsula. The vendor has also made available a first version of role-based administration for Incapsula.
-
Geographic Strategy: Imperva has strong WAF presence in most geographies, and offers effective support across most regions. Recent presence has been especially strong in the APAC region.
Cautions
-
Market Responsiveness: Imperva is experiencing a lot of organizational changes, which could be the source of a slower pace of release, especially for the SecureSphere product line.
-
Cloud WAF Service: Customers wish that Incapsula supported single sign-on (SSO) features, such as SAML 2.0. They also would like better and more-flexible canned reports.
-
Capabilities: Customers considering Incapsula to replace SecureSphere often notice the lack of feature parity. The cloud WAF service cannot yet match the depth and breadth of security function covered by the appliance product line.
-
Pricing: SeveralGartner clients cited higher-than-competitive prices for Imperva WAF SecureSphere, and to a lesser extent for Incapsula.
-
Cloud WAF Service: Incapsula’s infrastructure does not include any point of presence in China, and its infrastructure lags behind other cloud-native WAF services in South America and Africa.
-
Customer Experience (WAF Appliance): SecureSphere customers report that the management console remains complex when using the more advanced capabilities. Customers frequently mentioned that deployment often requires professional services to effectively implement the offerings at scale. They also would like to see closer integration between Attack Analytics and the WAF management consoles, and more-unified management capabilities between SecureSphere and Incapsula.
-
Customer Experience (Cloud WAF Service): Some customers complain about Incapsula’s limited cross-sites and multidomain management and reporting, especially when multiple applications share the same IP address. Surveyed customers and resellers indicated that they did not get the same quality of support for Incapsula, compared with what they are accustomed to with Securesphere. They cite too many canned and not necessarily helpful answers as a first response when contacting support.
Instart
Strengths
-
Organization: Instart is part of a new wave of web app security vendors developing easy-to-deploy, cloud-native solutions. The lack of technical debt from legacy solution allows the vendor to try new approaches, such as the Nanovisor, more easily.
-
Viability: Instart continues to grow quickly, demonstrating its ability to attract new customers. It is well-funded to further enhance its solutions in the future.
-
Vertical Strategy: Instart continues to be visible in shortlists for small and large e-commerce companies. Customers from these organizations report that they selected Instart for its ability to combine security features with the performance optimization and anti-advertisement blocking features for which they were primarily looking.
-
Customer Experience: New customers continue to be satisfied with the ease of deployment when collaborating with the vendor. They also mention high-quality vendor support.
-
Capabilities: Instart has released a bot mitigation feature, priced separately from the WAF. It is too early to judge the quality of the feature. However, customers from Instart’s top verticals, e-commerce and online media, are heavily targeted by bots, and welcomed the new feature.
-
Capabilities: Instart management provides a fully featured API, which facilitates its integration in dynamic application ecosystems. When adding a new feature, such as the custom rule creation, a related API is also available.
Cautions
-
Product Strategy: Instart positions its WAF as an add-on, and sells it mostly to its existing customer base for its other products, who don’t conduct in-depth evaluation of the security modules. The vendor has yet to demonstrate that it is interested in more than selling security as a commodity to its IT customer base.
-
Organization: Instart is a growing company, but has experienced organizational hiccups recently, with a change of CEO and internal reorganizations intended to overcome slower-than-investor-expected growth and market awareness. As the vendor prepares for its IPO, it might be distracted from innovating in the security space. Its WAF development team is one of the smallest among the vendors evaluated in this research.
-
Capabilities: Instart does not offer API security features. It does not parse JSON or XML payloads, does not offer authentication features, or integrate with identity providers to enable SSO, using SAML protocol.
-
Geographic Strategy: The vendor still has a low visibility in shortlists, especially outside the U.S. Prospective customers should first verify the availability of local skills, assess their need for support in their native language and ask for local peer references. The vendor has not yet deployed points of presence in China.
-
Capabilities: Instart does not provide a fully featured, self-service option. Although customers can now create their own rules, they still need the vendor for on boarding. The role-based access control (RBAC) feature is reputed to be quite limited. Configuration tuning quickly requires a request to Instart’s team. Many clients point out the poor documentation and scarcity of available technical resources.
-
Customer Experience: Customers would like to see more improvements in the reports, as well as more customizable dashboards. Because the WAF lacks integration with ticketing systems, AST and most SIEM technologies, organizations faces difficulty integrating it into their enterprise incident workflows.
Microsoft
Strengths
-
Sales Strategy: Azure WAF is bundled with the Application Gateway, making it easy for clients to enable it, while deploying the underlying application delivery infrastructure, and providing protection to their applications right away.
-
Capabilities: Azure WAF includes a fully featured REST API for managing the WAF configuration.
-
Capabilities: The vendor can parse JSON and XML payloads, and apply security rules to this content.
-
Geographic Strategy: Now that Azure WAF is available globally, it benefits from Microsoft’s global infrastructure of data centers, with multiple points of presence in all regions, except Africa and the Middle East.
Cautions
-
Organization: Microsoft is still building its WAF team, which is relatively small, when compared with the challengers and leaders in this research. Prospective buyers should get references to validate expected capabilities.
-
Product Strategy: At this point in time, Azure WAF consists mainly of a repackaged ModSecurity engine, using ModSecurity core rulesets (CRSs). Although many WAF offerings have started with similar approach, the vendor must continue to demonstrate its commitment to developing the WAF beyond basic.
-
Capabilities: As with any recent introduced product, customers should expect that Azure WAF lacks some of its competitor features. It lacks integrated CDN, bot management and user credential abuse detection. It cannot block based on geolocation or inspect malware.
-
Customer Experience: Rule propagation can take several minutes. WAF onboarding, based on deploying an Application Gateway virtual appliance, is more complicated than its cloud-native WAF’s competitors.
-
Customers Experience: Because of the limited number of deployments to protect applications in production, the feedback on Azure WAF is scarce. Early adopters mention initial scalability issues, because Microsoft’s WAF is built on VMs in the back end, and the lack the ease of autoscaling that other cloud-native WAFs offer.
-
Technical Architecture: Azure WAF is built on the top of Azure Application Gateway. It lacks autoscaling features, requiring the use of an Azure load balancer (Traffic Manager) to dynamically route the traffic between Azure WAF’s instances in multiple data centers.
Oracle
Strengths
-
Market Responsiveness: Surveyed customers liked the vendor’s responsiveness to feature requests, and the regular product improvements.
-
Market Execution: Through OEM agreement, the vendor has quickly acquired a sizable customer base.
-
Customer Experience: Although the solution is still recent, early feedback on the new bot manager features are promising. The vendor’s team in charge of managing the WAF also get good scores from surveyed customers and resellers.
-
Capabilities: Oracle WAF leverage statistical analysis to create a risk score for suspicious queries, and trigger alert, or blocking actions, based on this score. Feedback from customers indicates that this feature enables them to better tune the WAF configuration, and to focus on important events.
-
Capabilities: As Zenedge is now part of Oracle, it can get visibility on a big chunk of traffic, which could be useful to further improve the learning algorithms and, therefore, the quality of Oracle WAF’s detection.
-
Support: Contacted customers confirmed to Gartner analysts that the acquisition had no impact on the quality of their interactions with Zenedge team.
Cautions
-
Product Strategy: Zenedge, a relatively small startup, has been acquired by Oracle, which is a cloud provider and a large enterprise. In other network and application security acquisitions, Gartner analysts have observed that a cultural chasm, and potential conflicts in roadmap priorities could slow down feature delivery. Prospects, especially those protecting applications not hosted on Oracle cloud, should request commitment on the vendor’s roadmap delivery, in case required capabilities are missing at the time of purchase.
-
Technical Architecture: Oracle WAF infrastructure lacks points of presence in China, the Middle East and Africa. It has a limited number of points of presence in South America and Asia. Oracle infrastructure is global, so the vendor might quickly increase the number of available points of presence for Oracle WAF.
-
Capabilities: Although many features are available with a self-service portal, Oracle recommends to its customers to connect with Oracle Dyn managed services team to onboard new applications. Oracle WAF does not yet integrate with SIEM vendors. Logs can be exported in a comma-delimited flat file (.csv) format, or pulled through an API, but are not available in CEF or over syslog.
-
Customer Experience: Customers would like to see improvements in Oracle WAF’s reporting. The event view, which is different from the active-learning view, where the risk score appears, does not aggregate individual alerts into attack or attack campaign, resulting in a large number of alerts.
-
Product: Some early clients highlighted that Zenedge WAF, prior to the acquisition, was still a work in progress, lacking some expected features. Oracle Dyn has a smaller team for WAF-related threat research, compared with many of its leading competitors.
Radware
Strengths
-
Capabilities: Radware’s Emergency Response Team (ERT) leverages in-house threat research and provides 24/7 managed SOC, in addition to ad hoc support, when Radware’s customers are under attack.
-
Product Strategy: At the heart of the AppWall WAF technology is Radware’s automatic policy learning. Radware’s engine tracks changes and updates to the application and updates the policy, also leveraging integration with AST solutions to implement virtual patches in case of new vulnerabilities. This also works for APIs.
-
Customer Experience: Radware customers praise the combination of high-efficacy DDoS protection and WAF. Users of the AppWall appliances are satisfied with the level of effort required to tune the positive security model.
-
Market Execution: Many customers of Radware’s WAF were initially DDoS protection customers, or purchase the WAF and DDoS protection offers all together. Radware’s good reputation in the DDoS protection space reflects positively on its WAF prospects.
-
Cloud WAF Service: Radware customers, relying on the vendor to manage the WAF, express satisfaction with the vendor’s professional service and incident response (ERT) teams.
-
Vertical Strategy: Radware has good visibility in media and retail organizations, two vertical segments combining large-scale web applications, budget constraints and relatively small security teams.
-
Marketing Strategy: The vendor regularly publishes threat reports as a tool to raise awareness about issues. However, this also incidentally demonstrates the efficacy of its approach.
Cautions
-
Customer Experience: Although comments on support are generally positive, customers in the APAC regions are less satisfied with the timeliness of the response from Radware’s support for issues that require more than a canned answer.
-
Cloud WAF Service: Managed WAF is not the preferred option for many customers; however, it is the main option for Radware cloud WAF service. Radware cloud WAF service clients express interest in further improvements of the self-service management capabilities.
-
Customer Experience: Radware’s customers cite a need to improve the AppWall UI. It scores low on surveys, and the most frequently cited issue is its lack of intuitiveness, when searching for a configuration option. Customers also comment on the lack of out-of-box reports related to compliance. These reports are available on APSolute Vision reporter, Radware’s dedicated reporting solution.
-
Capabilities: Some prospects encountered challenges successfully implementing Radware’s positive security approach.
-
Market Execution: Radware is not as visible in U.S. shortlists as many of its competitors. Organizations evaluating AppWall should focus on their evaluation of the vendor’s capabilities, relative to their requirements, rather than on the overly aggressive communications from the vendor and its channel partners, who frequently exaggerate capabilities relative to leading competitors.
-
Customer Experience: Radware customers continue to be dissatisfied with the training and documentation on AppWall, mentioning that it lengthens the learning curve when trying to deploy the technology, implement new features or understand whether there’s a configuration issue.
Rohde & Schwarz Cybersecurity
Strengths
-
Customer Experience: Rohde & Schwarz customers like the graphical workflow, backed up by a more traditional view. Former DenyAll rWeb users noted that the addition of a web security engine in the new WAF product improved their results.
-
Product Strategy: Following the acquisition, the DenyAll team maintained an open security culture, participating in events where they let penetration testers try to hack or pass through the WAF. R&S WAF is also one of the only products evaluated in this research with an official bug bounty program.
-
Capabilities: DenyAll WAF includes multiple analysis engines and leverages user session risk scoring to ensure accurate detection and low false-positive rates.
-
Capabilities: Building on previous enhancements to its reporting solution, Rohde & Schwarz has improved its investigative capabilities by enabling attack replay and dedicated investigation dashboards.
-
Capabilities: R&S Cloud Protector offers predefined configurations only using the management console, like most cloud WAF services built on the foundation of a WAF appliance. However, customers can fully manage the WAF, using the API.
-
Customer Experience: Customers continue to give positive feedback about presale and postsale local support.
Cautions
-
Market Responsiveness: The number of new features released on R&S WAF and R&S Cloud Protector has been severely limited for a few years now. Smaller vendors evaluated for this research have achieved significantly more during the same period, especially when it comes to the development of a cloud WAF service.
-
Marketing and Sales Execution: Even though the acquisition gave DenyAll access to Rohde & Schwarz’s sales force, the vendor is losing market share.
-
Capabilities: The acquisition by Rohde & Schwarz did not lead to significant investment in the DenyAll small threat research team. DenyAll WAF does not automatically deploy ad hoc signatures, following an attack, relying on the generic engine, and leaving customers to guess from the detailed log information whether the alert triggered is related to recent attack campaigns.
-
Capabilities: Rohde & Schwarz does not offer unified centralized management for its WAF appliance and R&S Cloud Protector. The vendor offers limited bot mitigation, compared with many of the vendors evaluated in this research.
-
Geographic Strategy: R&S WAF is not visible in shortlist outside its original home market, France, and Germany. Prospective customers outside of these countries should verify the availability of peer references.
-
Customer Experience: Many customers have complaints about the Java-based UI, and would like to see faster transition to the web-based management promised for years. They also note that bot mitigation could be better.
Vendors Added and Dropped
Added
-
Microsoft (Azure)
-
Oracle (acquired Zenedge)
Dropped
-
NSFOCUS, Penta Security, Positive Technologies and Venustech were dropped, due to updated and more-demanding inclusion criteria.
Inclusion and Exclusion Criteria
-
Their offerings can protect applications running on different types of web servers.
-
Their WAF technology is known to be approved by qualified security assessors as a solution for PCI DSS Requirement 6.6, which covers Open Web Application Security Project (OWASP) Top 10 threats, in addition to others.
-
They provide physical, virtual or software appliances, or cloud WAF service.
-
Their WAFs were generally available as of 1 January 2017.
-
Their WAFs demonstrate global presence, and features/scale relevant to enterprise-class organizations:
-
$12 million in WAF revenue during 2017; able to demonstrate that at least 200 enterprise customers use its WAF products under support as of 31 December 2017.
-
And, the vendor must have sold at least 40 net-new customers in 2017.
-
Or, $7 million in WAF revenue during 2017, and two years of compound annual revenue growth of at least 30%growth.
-
-
The vendor must provide at least three WAF customer references for WAF appliances, or three customer references for cloud WAF service, or both, if the vendor offers both solutions.
-
The vendor must demonstrate minimum signs of global presence:
-
Gartner received strong evidence than more than 5% of its customer base is outside its home region. Vendors appearing in Gartner client inquiries, competitive visibility, client references and the vendor’s local brand visibility are considered.
-
The vendor can provide at least two references outside its home region.
-
-
The provider offers 24/7 support, including phone support (in some cases, this is an add-on, rather than being included in the base service).
-
Gartner has determined that they are significant players in the market, due to market presence, competitive visibility or technology innovation.
-
Gartner analysts assess that the vendor’s WAF technology provides more than a repackaged ModSecurity engine and signatures.
-
The vendor must provide evidence to support meeting the above inclusion requirements.
-
The vendor primarily has a network firewall or IPS with a non-enterprise-class WAF.
-
The vendor is primarily a managed security service provider (MSSP), and WAF sales mostly come as part of broader MSSP contract.
-
The vendor is not actively providing WAF products to enterprise customers, or has minimal continued investments in the enterprise WAF market.
-
The vendor has minimal or negligible apparent market share among Gartner clients, or is not actively shipping products.
-
The vendor is not the original manufacturer of the firewall product. This includes hardware OEMs, resellers that repackage products that would qualify from their original manufacturers, and carriers and internet service providers (ISPs) that provide managed services. We assess the breadth of OEM partners as part of the WAF evaluation, and do not rate platform providers separately.
-
The vendor has a host-based WAF, WAM, RASP or API gateway (these are considered distinct markets).
Evaluation Criteria
Ability to Execute
-
Product or Service: This includes the core WAF technology offered by the technology provider that competes in and serves the defined market. This also includes current product or service capabilities, quality, feature sets, and skills, whether offered natively or through OEM agreements/partnerships, as defined in the Market Definition/Description section. Strong execution means that a vendor has demonstrated to Gartner that its products or services are successfully and continually deployed in enterprises. Execution is not primarily about company size or market share, although these factors can considerably affect a company’s Ability to Execute. Some key features, such as the ability to support complex deployments (including on-premises and cloud options) with real-time transaction demands, are weighted heavily. Product evaluation also considers adjacent security functions. These include DDoS protection services, bot management (e.g., bad-bot mitigation and good-bot whitelisting), fraud detection, API security and threat intelligence feeds, which might be bundled or integrated with WAFs. Integration with other markets, such as CASBs and AST, is evaluated as well, but more lightly.
-
Overall Viability: This includes an assessment of the organization’s overall financial health, and the financial and practical success of the business unit. It also involves the likelihood that individual business units will continue to invest in WAF, offer WAF products and advance the state of the art in the organization’s portfolio of products.
-
Sales Execution/Pricing: This is the technology provider’s capabilities in all presales activities and the structure that supports them. It includes deal management, pricing and negotiation; presales support; and the overall effectiveness of the sales channel. It also includes deal size, as well as the use of the product or service in large enterprises with critical public web applications, such as banking applications or e-commerce. Low pricing will not guarantee high execution or client interest. Buyers want good results more than they want bargains. Buyers balance WAF security requirements and pricing, and don’t consider best pricing only.
-
Market Responsiveness/Record: This is the ability to respond, change direction, be flexible and achieve competitive success as opportunities develop, competitors act, and security trends and customer needs evolve. A vendor’s responsiveness to new or updated web application frameworks and standards, as well as its ability to adapt to market dynamics, changes (such as the relative importance of PCI compliance). This criterion also considers the provider’s history of releases, but gives higher weight to its responsiveness during the most recent product life cycle.
-
Marketing Execution: This is the clarity, quality, creativity and efficacy of programs designed to deliver the organization’s message. It is aimed at influencing the market, promoting the brand and business, increasing product awareness, and establishing positive identification with the product/brand and organization among buyers. This mind share can be driven by a combination of publicity, promotional activities, thought leadership, word of mouth and sales activities.
-
Customer Experience: This assesses the relationships, products and services/programs that enable clients to be successful with the products that are evaluated. Specifically, this includes the ways customers receive technical support or account support. This can also include ancillary tools, customer support programs (and the quality thereof), availability of user groups, service-level agreements (SLAs) and so on.
-
Operations: This is the organization’s ability to meet its goals and commitments. Factors include the quality of the organizational structure, including skills, experiences, programs, systems and other vehicles that enable the organization to operate effectively and efficiently on an ongoing basis.
Table 1: Ability to Execute Evaluation Criteria
|
Evaluation Criteria
|
Weighting
|
|---|---|
|
Product or Service
|
High
|
|
Overall Viability
|
Medium
|
|
Sales Execution/Pricing
|
Medium
|
|
Market Responsiveness/Record
|
High
|
|
Marketing Execution
|
Medium
|
|
Customer Experience
|
High
|
|
Operations
|
Medium
|
Completeness of Vision
-
Market Understanding: This is the technology provider’s ability to understand buyers’ wants and needs, and translate them into products and services. Vendors that show the highest degree of vision listen to and understand buyers’ wants and needs, and can shape or enhance them with their added vision. They also determine when emerging use cases will greatly influence how the technology has to work. Vendors showing a better understanding of how the changes in web applications that affect security will receive higher scores. Trends include cloud, IaaS, agile methodologies, web services and microservices, continuous integration, and the growing importance of APIs.
-
Marketing Strategy: This is a clear, differentiated set of messages that is consistently communicated throughout the organization and externalized through the website, advertising, customer programs and positioning statements.
-
Sales Strategy: This strategy for selling products uses the appropriate network of direct and indirect sales, marketing, service and communication affiliates to extend the scope and depth of market reach, skills, expertise, technologies, services and the customer base. The ability to attract new customers in need of web application security only has a strong influence on this criterion.
-
Offering (Product) Strategy: This is the technology provider’s approach to product development and delivery that emphasizes differentiation, functionality, methodology and feature sets, as they map to current and future requirements. As attacks change and become more targeted and complex, we highly weight vendors that move their WAFs beyond rule-based web protections that are limited to known attacks. For example:
-
Enabling a positive security model with automatic and efficient policy learning
-
Leveraging machine learning to improve the quality of the detection engines
-
Using a weighted scoring mechanism based on a combination of techniques
-
Providing updated security engines to handle new protocols and standards (such as JSON, HTML5, HTTP/2, IPv6 and WebSockets), and remaining efficient against changes in how older web technologies (e.g., Java, JavaScript and Adobe Flash) are used
-
Providing dedicated protection techniques on emerging web application use cases, such as mobile and IoT applications
-
Bot mitigation not limited to reputation-based controls
-
API security
-
User behavioral analysis
-
Countering evasion techniques actively
-
-
This criterion includes the evaluation of the depth of features, especially features that ease the management of the solution, and integration with other solutions, including DDoS protection services and emerging technologies, such as CASB.
-
Business Model: This is the soundness and logic of a technology provider’s underlying business proposition.
-
Vertical/Industry Strategy: This is the technology provider’s strategy to direct resources, skills and offerings to meet the specific needs of individual market segments, including vertical markets. Vendors focusing on a single vertical get lower scores; vendors with differentiated vertical strategies and the ability to reproduce success across several verticals receive higher scores.
-
Innovation: This refers to the direct, related, complementary and synergistic layouts of resources, expertise or capital for investment, consolidation, defensive or preemptive purposes. It includes product innovation and quality differentiators, such as:
-
New methods for detecting web attacks and avoiding false positives
-
A management interface, monitoring and reporting that contribute to easy web application setup and maintenance, better visibility, and faster incident response
-
Automated delivery of detection and protection
-
Ability to integrate with DevOps process and tooling
-
Integration with companion security technologies, which improves overall security
-
-
Geographic Strategy: This is the technology provider’s strategy to direct resources, skills and offerings to meet the specific needs of geographies outside the “home” or native geography. This can be directly or through partners, channels and subsidiaries, as appropriate for the geographies and markets.
Table 2: Completeness of Vision Evaluation Criteria
|
Evaluation Criteria
|
Weighting
|
|---|---|
|
Market Understanding
|
High
|
|
Marketing Strategy
|
Medium
|
|
Sales Strategy
|
Low
|
|
Offering (Product) Strategy
|
High
|
|
Business Model
|
Medium
|
|
Vertical/Industry Strategy
|
Low
|
|
Innovation
|
High
|
|
Geographic Strategy
|
Medium
|
Quadrant Descriptions
Leaders
Challengers
Visionaries
Niche Players
Context
-
Their tolerance for a full, in-line reverse proxy with blocking capabilities in front of the web applications
-
The benefits and constraints of the different WAF delivery options:
-
Dedicated appliances
-
CDNs
-
ADCs
-
Cloud services
-
-
SSL decryption/re-encryption and other scalability requirements
Market Overview
-
Organizations looking for cloud WAF services generally expect multiple, bundled features — notably DDoS protection, bot management and CDN — in an easy-to-deploy and easy-to-operate package. They increasingly request more depth for security controls, and better granularity for configuration options, but are often under time pressures to deploy the WAF.
-
Organizations looking for WAF appliances (physical and virtual), are more likely to have a WAF appliance already in place. They put higher expectations on positive security model, advanced security features and integration of the WAF in the incident response workflow.
WAF Market Trends
-
Gartner estimates that the number of deployments for physical appliance sales and WAF modules on ADC appliances is declining, with most vendors experimenting a decline in volume, and many vendors seeing a slow, single-digit growth driven by increased subscription revenue.
-
Cloud WAF service continues to grow steadily. Gartner estimates that it now represents more than 35% of the WAF market revenue in 2017 and most Gartner client inquiries about WAF. Cloud-native solutions increasingly compete with the more-mature vendors. IaaS providers’ visibility is nascent.
-
More organizations want to “follow the app,” using a cloud WAF. However, Gartner analysts have seen an increase, from a small base of inquiries with organizations leaning toward the conservative approach to use the same WAF appliance on-premises and on IaaS. Also, multicloud strategies have started to be visible in strategic roadmaps, creating an incentive to have more unified management and reporting.
Bot Management Is on the Rise, API Security Is Next
Evidence
Evaluation Criteria Definitions
Ability to Execute
Completeness of Vision
======================== End