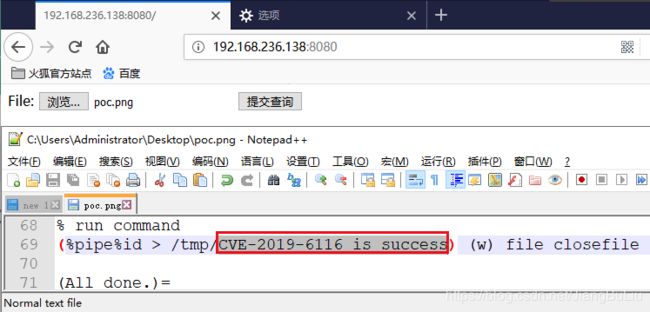
- 小林渗透入门:burpsuite+proxifier抓取小程序流量
ξ流ぁ星ぷ132
小程序web安全安全性测试网络安全安全
目录前提:代理:proxifier:步骤:bp证书安装bp设置代理端口:proxifier设置规则:proxifier应用规则:结果:前提:在介绍这两个工具具体实现方法之前,有个很重要的技术必须要大概了解才行---代理。代理:个人觉得代理,简而言之,就是在你和服务器中间的一个中间人,来转达信息。那为什么要代理呢,因为这里的burpsuite要抓包,burpsuite只有做为中间代理人才可以进行拦截
- .NET 一款基于BGInfo的红队内网渗透工具
dot.Net安全矩阵
网络.net安全.netcoreweb安全矩阵
01阅读须知此文所提供的信息只为网络安全人员对自己所负责的网站、服务器等(包括但不限于)进行检测或维护参考,未经授权请勿利用文章中的技术资料对任何计算机系统进行入侵操作。利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责。本文所提供的工具仅用于学习,禁止用于其他方面02基本介绍在内网渗透过程中,白名单绕过是红队常见的技术需求。Sharp4Bginfo.exe是一款基于微软签名工具
- 2025年渗透测试面试题总结-2025年HW(护网面试) 43(题目+回答)
独行soc
2025年护网面试职场和发展linux科技渗透测试安全护网
安全领域各种资源,学习文档,以及工具分享、前沿信息分享、POC、EXP分享。不定期分享各种好玩的项目及好用的工具,欢迎关注。目录2025年HW(护网面试)431.自我介绍与职业规划2.Webshell源码级检测方案3.2025年新型Web漏洞TOP54.渗透中的高价值攻击点5.智能Fuzz平台架构设计6.堆栈溢出攻防演进7.插桩技术实战应用8.二进制安全能力矩阵9.C语言内存管理精要10.Pyth
- 微算法科技的前沿探索:量子机器学习算法在视觉任务中的革新应用
MicroTech2025
量子计算算法
在信息技术飞速发展的今天,计算机视觉作为人工智能领域的重要分支,正逐步渗透到我们生活的方方面面。从自动驾驶到人脸识别,从医疗影像分析到安防监控,计算机视觉技术展现了巨大的应用潜力。然而,随着视觉任务复杂度的不断提升,传统机器学习算法在处理大规模、高维度数据时遇到了计算瓶颈。在此背景下,量子计算作为一种颠覆性的计算模式,以其独特的并行处理能力和指数级增长的计算空间,为解决这一难题提供了新的思路。微算
- 正义的算法迷宫—人工智能重构司法体系的技术悖论与文明试炼
一、法庭的数字化迁徙当美国威斯康星州法院采纳COMPAS算法评估被告再犯风险,当中国"智慧法院"系统年处理1.2亿件案件,司法体系正经历从石柱法典到代码裁判的范式革命。这场转型的核心驱动力是司法效率与公正的永恒张力:美国重罪案件平均审理周期达18个月,中国基层法官年人均结案357件(是德国同行的6倍),而算法能在0.3秒内完成百万份文书比对。人工智能渗透司法引发三重裂变:证据分析从经验推断转向数据
- 酒店新科技,飞睿智能毫米波雷达人体存在感应器,智能照明创新节能新风尚
飞睿科技
飞睿智能雷达人体存在感应器毫米波雷达人体传感器无线WiFi感应
在这个日新月异的时代,科技正以未有的速度改变着我们的生活。从智能手机到智能家居,每一个细微之处都渗透着科技的魅力。而今,这股科技浪潮已经席卷到了酒店行业,为传统的住宿体验带来了翻天覆地的变化。其中,引人注目的莫过于飞睿智能人体存在感应器的应用,它以其独特的毫米波雷达技术,实现了人来灯亮、人走灯灭的智能照明效果,不仅极大地提升了客户的住宿体验,更为酒店节能降耗开辟了一条全新的道路。你是否有过这样的经
- 混合云工具沦为隐蔽的远程代码执行与权限提升载体
FreeBuf-
flaskpython后端
通过WAC执行命令时分配的令牌权限|图片来源:IBM混合云管理工具的安全隐患IBMX-Force团队近日对微软AzureArc进行深入研究,发现这款旨在统一本地与云环境的混合云管理工具,可能成为代码执行、权限提升和隐蔽驻留的潜在攻击载体。这项研究始于IBM红队在一次渗透测试中,偶然发现PowerShell脚本中硬编码的Azure服务主体(ServicePrincipal)密钥,进而触发对Azure
- 2025年渗透测试面试题总结-字节跳动[实习]安全研究员(题目+回答)
独行soc
2025年渗透测试面试指南安全科技区块链linux职场和发展渗透测试网络安全
安全领域各种资源,学习文档,以及工具分享、前沿信息分享、POC、EXP分享。不定期分享各种好玩的项目及好用的工具,欢迎关注。目录字节跳动[实习]安全研究员1.你投的岗位是安全研究实习生,你了解我们这边主要是做什么的吗2.自我介绍3.现在有什么比较想做的方向吗?4.有没有审过开源框架、cms、中间件之类的?6.在A公司主要做什么的?7.入侵检测主要在做什么?遇到的问题?核心工作:典型问题:8.误报原
- 专题:2025数据资产AI价值化:安全、战略与应用报告|附400+份报告PDF、原数据表汇总下载
拓端研究室
人工智能大数据
原文链接:https://tecdat.cn/?p=42885在数字经济加速渗透的今天,数据作为核心生产要素的价值愈发凸显。上市公司作为经济高质量发展的微观主体,其数据价值化进程不仅关乎企业自身竞争力,更折射出中国产业数字化转型的深度与广度。本报告洞察基于《上海数据交易所:上市公司数据价值化研究报告(2025)》《绿盟科技:全球云上数据泄露风险分析报告(第五期)》《DigitalRealty:全球
- 2025年渗透测试面试题总结-2025年HW(护网面试) 40(题目+回答)
安全领域各种资源,学习文档,以及工具分享、前沿信息分享、POC、EXP分享。不定期分享各种好玩的项目及好用的工具,欢迎关注。目录2025年HW(护网面试)401.SQL注入读写文件/二次注入/防御2.XSS类型及防御3.CSRF与XSS区别4.文件上传绕过与防御5.服务器解析漏洞6.XXE与SSRF7.RCE与PHP函数区别8.Python迭代器与装饰器9.缓冲区溢出原理/防御10.内网渗透经验1
- 想转行网络安全,可以先看看过来人的建议
孤独的汤姆
web安全安全
在当前就业形势下,不少朋友面临转行的困境。网络安全作为一个热门领域,自然也吸引了许多人的目光。本文将就转行网络安全这一话题,提供一些切实可行的建议。网络安全行业概况网络安全涵盖了从基础的脚本编写到高级的漏洞研究等多个层面。该领域包括但不限于:渗透测试、漏洞评估、恶意软件分析、入侵检测、信息安全管理等。这些内容的复杂性不一,从基础的安全监控到复杂的安全架构设计都涉及其中。这就意味着,尽管有些领域可能
- 模型融合与人机协同:构建人机共生的智能未来
AI天才研究院
AgenticAI实战计算AI人工智能与大数据计算科学神经计算深度学习神经网络大数据人工智能大型语言模型AIAGILLMJavaPython架构设计AgentRPA
1.背景介绍在科技日新月异的今天,人工智能(AI)已经成为了我们生活中不可或缺的一部分。从智能手机,到自动驾驶汽车,再到医疗诊断,AI的应用已经渗透到了我们生活的方方面面。然而,尽管AI的发展已经取得了显著的成就,但是我们仍然面临着一个重大的挑战:如何让AI系统更好地理解和适应人类的需求,以实现人机共生的智能未来。为了解决这个问题,越来越多的研究者开始探索模型融合和人机协同的方法。2.核心概念与联
- [晕事]今天做了件晕事83: pen test
mzhan017
英语学习笔记晕事英语学习
这个缩写,就不能顾名思义了,而且pen是一个独立的单词,从读音上来说还容易和pain混淆,所以导致初接触者有些困扰。所以这个pentest的缩写,有些失败。全写是penetrationtest:渗透测试。https://en.wikipedia.org/wiki/Penetration_test修改建议是改成penetest,至少可以和pen在书写上区分,在读音是也可以区分,就读“排你test”。
- 分布式推客系统架构设计:从微服务到高性能计算的实践路径
wx_ywyy6798
推客系统推客小程序推客分销系统推客系统开发推客小程序开发推客分销系统开发分销系统
一、推客系统概述与市场背景分析推客系统(PromoterSystem)作为一种创新的社交化营销工具,近年来在电商、知识付费、本地生活服务等领域展现出强大的市场渗透力。该系统本质上是一种基于社交关系的分布式营销网络,通过激励用户主动分享商品或服务信息,实现裂变式传播效果。根据2023年数字营销行业白皮书显示,采用推客系统的企业平均获客成本比传统广告渠道降低47%,转化率提升3倍以上。在数字化转型浪潮
- Fortinet Security Fabric 解决方案:构建智能化、一体化的网络安全防御体系
江苏思维驱动智能研究院有限公司
安全fabricweb安全
一、方案背景与核心价值:应对数字化时代的安全挑战在云计算、物联网、远程办公等技术普及的背景下,企业网络边界逐渐模糊,攻击面呈指数级扩展。传统单点安全产品难以应对多维度威胁渗透,而FortinetSecurityFabric(安全架构)以“集成化、自动化、智能化”为核心,通过安全能力的协同联动与威胁情报共享,构建覆盖全网络环境的动态防御体系。其核心价值在于:打破安全孤岛:整合分散的安全组件,避免多产
- 基于python的api扫描器系统的设计与实现
博主介绍:✌在职Java研发工程师、专注于程序设计、源码分享、技术交流、专注于Java技术领域和毕业设计✌温馨提示:文末有CSDN平台官方提供的老师Wechat/QQ名片:)Java精品实战案例《700套》2025最新毕业设计选题推荐:最热的500个选题o( ̄▽ ̄)d介绍在当今数字化社会,网络安全问题日益突出,为了有效识别和防范网络威胁,开发一款全面的Web应用渗透测试系统至关重要。本研究基于Py
- AI 的出现,是否能替代 IT 从业者?
敲代码的苦13
人工智能
在科技浪潮奔涌向前的时代,AI正以惊人的速度渗透进各个领域,IT行业首当其冲。当AI编写代码的效率不断提升,当智能算法能够快速完成系统故障诊断,当自动化工具可以处理大量数据运维工作,IT从业者们不禁心生疑虑:AI真的会成为“职业终结者”,将自己从岗位上彻底替代吗?这场关于AI与IT从业者未来的讨论,充满了争议与悬念,也关乎着无数人的职业命运。一、AI在IT领域的应用现状编程开发中的AIAI在编程开
- AI“大航海”时代:企业人力资源的AI-HR实践与效能提升策略
在数字化浪潮的推动下,人工智能(AI)正以前所未有的速度渗透各行各业,人力资源管理(HR)领域也不例外。AI技术的引入与应用落地,不仅提升HR管理效率,更在深层次上带来人力资源运作模式的变革。什么是AI-HR所谓AI-HR,是指将人工智能技术应用于人力资源管理,并通过机器学习、自然语言处理、数据挖掘等技术,优化招聘、培训、绩效评估、员工关系等人力资源各个业务模块。近年来,随着AI技术的成熟和普及,
- 2025 年前端主流框架对比和竞争格局及趋势发展
2025年前端框架的竞争格局呈现出主流框架稳定演进、新兴技术快速渗透的特点,同时全栈整合、跨端效能、AI集成成为核心发展方向。以下是基于最新行业动态和技术实践的深度解析:一、主流框架竞争态势与核心能力1.React:企业级生态的持续统治力市场地位:全球使用率超40%,尤其在金融、社交等数据密集型场景占据主导。字节跳动、腾讯等大厂的复杂Web应用仍以React为首选。技术突破:并发模式(Concur
- 网络渗透2 指纹识别
郭莉914
网络安全web安全
一.指纹识别指纹由于其终身不变性、唯一性和方便性,几乎已成为生物特征识别的代名词。通常我们说的指纹就是人的手指末端正面皮肤上凹凸不平的纹线,纹线规律的排列形成不同的纹型。而本节所讲的指纹是指网站CMS指纹识别、计算机操作系统及Web容器的指纹识别等。在渗透测试中,对目标服务器进行指纹识别是相当有必要的,因为只有识别出相应的Web容器或者CMS,才能查找与其相关的漏洞,然后才能进行相应的渗透操作。C
- WEB渗透信息收集篇--网站架构和指纹识别
Pluto-2003
渗透测试网络安全渗透测试信息收集
往期文章WEB渗透信息收集篇--域名信息-CSDN博客WEB渗透信息收集篇--IP和端口信息-CSDN博客WEB渗透信息收集篇--其他信息-CSDN博客WEB渗透信息收集篇--人员信息-CSDN博客信息泄露电话、邮箱,姓名若是论坛ID=1的用户名一般为管理、或查看帖子信息、生成字典网页上客服的QQ(先判断是企业的还是个人,用处有时不太大,看怎么用,搞个鱼叉什么的)目录遍历dirsearch、御剑备
- 网络渗透中的指纹识别
jhf200306
web安全
主要内容:指纹是网站CMS指纹识别,计算机操作系统及web容器的指纹识别。1.CMS:(contentmanagementsystem)整站系统或文章系统作用:开发者只要给客服一个软件包,客服自己安装配置好,可以定期更新数据来维护网站,节省了大量的人力和物力。常见的CMS:Dedecms(织梦),Discuz,PHPWEBPHPWIND,PHPCMS,ECSHOP,WordPress(wp)等。(
- web渗透sql注入1之access
合作小小程序员小小店
计算机网络性能优化网络攻击模型网络安全安全性测试
web渗透sql注入1之access环境搭建:win2003+asp+access数据库特性:access数据库没有root,不能读写文件,不能执行命令,只能借助字典得到数据注入方式:联合注入偏移注入注入过程:1)判断当前表有多少列,Howmushcolumnsnumber?id=1orderby23?id=1orderby52)获取数据库Getdatabase?id=1unionselect1,
- web渗透之指纹识别2
合作小小程序员小小店
网络安全安全性测试安全威胁分析web安全网络协议
web渗透之指纹识别2框架识别在框架指纹识别中,我们可以使用response响应头,以及目标路由,目录,备份文件,图标,插件等方式来推断框架信息。cms识别在CMS指纹识别中,我们可以使用response响应头返回的信息中是否包含CMS的特有标识或其他独特的信息,文字,或者图标,插件等。在CMS的漏洞较多,我们可以通过它的指纹找到源码,或者历史漏洞查看并进行白盒测试等。cdn识别在cdn指纹识别中
- web渗透之其他信息收集篇
合作小小程序员小小店
网络安全安全性测试网络协议web安全安全威胁分析
web渗透之其他信息收集篇在前期渗透的时候,我们需要做很多信息收集资产获取。除了web网站,服务器指纹识别外,我们还可以通过以下的资产进行信息收集工作:APP在移动开发中常见的两种两种安装包apk,ios,以及老早以前塞班jar,Winphone等,老的一些开发我就不做过多的介绍,主要了解一下apk和ios怎么进行资产收集,常见的有两种方式第一种外部获取通过抓包工具获取apk,ios请求的数据如f
- web渗透之指纹识别1
合作小小程序员小小店
网络安全物联网网络安全网络攻击模型计算机网络
web渗透之指纹识别1前端技术:前端中我们需要掌握一些基础html,javascrip,jquery,bootstrap,前端框架vue.js,vue,angular,React等,在前端中可以利用的东西还是很多的,我们可使用xss配合csrf以及一些攻击漏洞进行弹框,获取cookie,劫持,绕过,跳转,跨域,重定向,重放,控制节点,挂暗链接,甚至隐藏我们的请求等。如果要说怎么在识别中使用,我们可
- Python 机器学习实战:Scikit-learn 算法宝典,从线性回归到支持向量机
清水白石008
pythonPython题库python机器学习算法
Python机器学习实战:Scikit-learn算法宝典,从线性回归到支持向量机引言各位Python工程师,大家好!欢迎来到激动人心的机器学习世界!在这个数据驱动的时代,机器学习已经渗透到我们生活的方方面面,从智能推荐系统到自动驾驶汽车,都离不开机器学习技术的支撑。作为一名Python开发者,掌握机器学习技能,无疑将为您的职业发展注入强大的动力,让您在人工智能浪潮中占据先机。Scikit-lea
- L国的战斗之伞兵
题目背景L国即将与I国发动战争!!题目描述为了在敌国渗透作战,指挥官决定:派出伞兵前往敌国!然而敌国的风十分强烈,能让伞兵在同一高度不停转悠,直到被刮到一个无风区……(可怜的小兵)输入输出格式输入格式:第一行:n、m两个正整数,表示敌国的大小。以下n行,每行m个字符,“u”表示风向北吹;“d”表示风向南吹;“l”表示风向西吹;“r”表示风向东吹;“o”表示无风。(上北下南,左西右东)输出格式:一个
- 2024年最全kali无线渗透之用wps加密模式可破解wpa模式的密码12_kali wps,网络安全开发究竟该如何学习
2401_84558314
程序员wpsweb安全学习
一、网安学习成长路线图网安所有方向的技术点做的整理,形成各个领域的知识点汇总,它的用处就在于,你可以按照上面的知识点去找对应的学习资源,保证自己学得较为全面。二、网安视频合集观看零基础学习视频,看视频学习是最快捷也是最有效果的方式,跟着视频中老师的思路,从基础到深入,还是很容易入门的。三、精品网安学习书籍当我学到一定基础,有自己的理解能力的时候,会去阅读一些前辈整理的书籍或者手写的笔记资料,这些笔
- 网络安全/Web安全/渗透测试入门/信息收集
&Sinnt&
网络安全web安全网络安全
网络安全/Web安全/渗透测试入门/信息收集本篇文章主要讲解如何进行信息收集,列举了在信息收集中常见的工具和手段。原文地址:sinblog一,whois查询WHOIS查询是一种查找域名注册信息的工具或服务。WHOIS是一个协议,允许用户查询某个域名或IP地址的域名、注册信息以及其他相关互联网的详细数据。WHOIS数据库由多个注册商提供和注册机构维护,公开提供域名注册人的信息。自己购买一个域名,配置
- log4j对象改变日志级别
3213213333332132
javalog4jlevellog4j对象名称日志级别
log4j对象改变日志级别可批量的改变所有级别,或是根据条件改变日志级别。
log4j配置文件:
log4j.rootLogger=ERROR,FILE,CONSOLE,EXECPTION
#log4j.appender.FILE=org.apache.log4j.RollingFileAppender
log4j.appender.FILE=org.apache.l
- elk+redis 搭建nginx日志分析平台
ronin47
elasticsearchkibanalogstash
elk+redis 搭建nginx日志分析平台
logstash,elasticsearch,kibana 怎么进行nginx的日志分析呢?首先,架构方面,nginx是有日志文件的,它的每个请求的状态等都有日志文件进行记录。其次,需要有个队 列,redis的l
- Yii2设置时区
dcj3sjt126com
PHPtimezoneyii2
时区这东西,在开发的时候,你说重要吧,也还好,毕竟没它也能正常运行,你说不重要吧,那就纠结了。特别是linux系统,都TMD差上几小时,你能不痛苦吗?win还好一点。有一些常规方法,是大家目前都在采用的1、php.ini中的设置,这个就不谈了,2、程序中公用文件里设置,date_default_timezone_set一下时区3、或者。。。自己写时间处理函数,在遇到时间的时候,用这个函数处理(比较
- js实现前台动态添加文本框,后台获取文本框内容
171815164
文本框
<%@ page language="java" import="java.util.*" pageEncoding="UTF-8"%>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://w
- 持续集成工具
g21121
持续集成
持续集成是什么?我们为什么需要持续集成?持续集成带来的好处是什么?什么样的项目需要持续集成?... 持续集成(Continuous integration ,简称CI),所谓集成可以理解为将互相依赖的工程或模块合并成一个能单独运行
- 数据结构哈希表(hash)总结
永夜-极光
数据结构
1.什么是hash
来源于百度百科:
Hash,一般翻译做“散列”,也有直接音译为“哈希”的,就是把任意长度的输入,通过散列算法,变换成固定长度的输出,该输出就是散列值。这种转换是一种压缩映射,也就是,散列值的空间通常远小于输入的空间,不同的输入可能会散列成相同的输出,所以不可能从散列值来唯一的确定输入值。简单的说就是一种将任意长度的消息压缩到某一固定长度的消息摘要的函数。
- 乱七八糟
程序员是怎么炼成的
eclipse中的jvm字节码查看插件地址:
http://andrei.gmxhome.de/eclipse/
安装该地址的outline 插件 后重启,打开window下的view下的bytecode视图
http://andrei.gmxhome.de/eclipse/
jvm博客:
http://yunshen0909.iteye.com/blog/2
- 职场人伤害了“上司” 怎样弥补
aijuans
职场
由于工作中的失误,或者平时不注意自己的言行“伤害”、“得罪”了自己的上司,怎么办呢?
在职业生涯中这种问题尽量不要发生。下面提供了一些解决问题的建议:
一、利用一些轻松的场合表示对他的尊重
即使是开明的上司也很注重自己的权威,都希望得到下属的尊重,所以当你与上司冲突后,最好让不愉快成为过去,你不妨在一些轻松的场合,比如会餐、联谊活动等,向上司问个好,敬下酒,表示你对对方的尊重,
- 深入浅出url编码
antonyup_2006
应用服务器浏览器servletweblogicIE
出处:http://blog.csdn.net/yzhz 杨争
http://blog.csdn.net/yzhz/archive/2007/07/03/1676796.aspx
一、问题:
编码问题是JAVA初学者在web开发过程中经常会遇到问题,网上也有大量相关的
- 建表后创建表的约束关系和增加表的字段
百合不是茶
标的约束关系增加表的字段
下面所有的操作都是在表建立后操作的,主要目的就是熟悉sql的约束,约束语句的万能公式
1,增加字段(student表中增加 姓名字段)
alter table 增加字段的表名 add 增加的字段名 增加字段的数据类型
alter table student add name varchar2(10);
&nb
- Uploadify 3.2 参数属性、事件、方法函数详解
bijian1013
JavaScriptuploadify
一.属性
属性名称
默认值
说明
auto
true
设置为true当选择文件后就直接上传了,为false需要点击上传按钮才上传。
buttonClass
”
按钮样式
buttonCursor
‘hand’
鼠标指针悬停在按钮上的样子
buttonImage
null
浏览按钮的图片的路
- 精通Oracle10编程SQL(16)使用LOB对象
bijian1013
oracle数据库plsql
/*
*使用LOB对象
*/
--LOB(Large Object)是专门用于处理大对象的一种数据类型,其所存放的数据长度可以达到4G字节
--CLOB/NCLOB用于存储大批量字符数据,BLOB用于存储大批量二进制数据,而BFILE则存储着指向OS文件的指针
/*
*综合实例
*/
--建立表空间
--#指定区尺寸为128k,如不指定,区尺寸默认为64k
CR
- 【Resin一】Resin服务器部署web应用
bit1129
resin
工作中,在Resin服务器上部署web应用,通常有如下三种方式:
配置多个web-app
配置多个http id
为每个应用配置一个propeties、xml以及sh脚本文件
配置多个web-app
在resin.xml中,可以为一个host配置多个web-app
<cluster id="app&q
- red5简介及基础知识
白糖_
基础
简介
Red5的主要功能和Macromedia公司的FMS类似,提供基于Flash的流媒体服务的一款基于Java的开源流媒体服务器。它由Java语言编写,使用RTMP作为流媒体传输协议,这与FMS完全兼容。它具有流化FLV、MP3文件,实时录制客户端流为FLV文件,共享对象,实时视频播放、Remoting等功能。用Red5替换FMS后,客户端不用更改可正
- angular.fromJson
boyitech
AngularJSAngularJS 官方APIAngularJS API
angular.fromJson 描述: 把Json字符串转为对象 使用方法: angular.fromJson(json); 参数详解: Param Type Details json
string
JSON 字符串 返回值: 对象, 数组, 字符串 或者是一个数字 示例:
<!DOCTYPE HTML>
<h
- java-颠倒一个句子中的词的顺序。比如: I am a student颠倒后变成:student a am I
bylijinnan
java
public class ReverseWords {
/**
* 题目:颠倒一个句子中的词的顺序。比如: I am a student颠倒后变成:student a am I.词以空格分隔。
* 要求:
* 1.实现速度最快,移动最少
* 2.不能使用String的方法如split,indexOf等等。
* 解答:两次翻转。
*/
publ
- web实时通讯
Chen.H
Web浏览器socket脚本
关于web实时通讯,做一些监控软件。
由web服务器组件从消息服务器订阅实时数据,并建立消息服务器到所述web服务器之间的连接,web浏览器利用从所述web服务器下载到web页面的客户端代理与web服务器组件之间的socket连接,建立web浏览器与web服务器之间的持久连接;利用所述客户端代理与web浏览器页面之间的信息交互实现页面本地更新,建立一条从消息服务器到web浏览器页面之间的消息通路
- [基因与生物]远古生物的基因可以嫁接到现代生物基因组中吗?
comsci
生物
大家仅仅把我说的事情当作一个IT行业的笑话来听吧..没有其它更多的意思
如果我们把大自然看成是一位伟大的程序员,专门为地球上的生态系统编制基因代码,并创造出各种不同的生物来,那么6500万年前的程序员开发的代码,是否兼容现代派的程序员的代码和架构呢?
- oracle 外部表
daizj
oracle外部表external tables
oracle外部表是只允许只读访问,不能进行DML操作,不能创建索引,可以对外部表进行的查询,连接,排序,创建视图和创建同义词操作。
you can select, join, or sort external table data. You can also create views and synonyms for external tables. Ho
- aop相关的概念及配置
daysinsun
AOP
切面(Aspect):
通常在目标方法执行前后需要执行的方法(如事务、日志、权限),这些方法我们封装到一个类里面,这个类就叫切面。
连接点(joinpoint)
spring里面的连接点指需要切入的方法,通常这个joinpoint可以作为一个参数传入到切面的方法里面(非常有用的一个东西)。
通知(Advice)
通知就是切面里面方法的具体实现,分为前置、后置、最终、异常环
- 初一上学期难记忆单词背诵第二课
dcj3sjt126com
englishword
middle 中间的,中级的
well 喔,那么;好吧
phone 电话,电话机
policeman 警察
ask 问
take 拿到;带到
address 地址
glad 高兴的,乐意的
why 为什么
China 中国
family 家庭
grandmother (外)祖母
grandfather (外)祖父
wife 妻子
husband 丈夫
da
- Linux日志分析常用命令
dcj3sjt126com
linuxlog
1.查看文件内容
cat
-n 显示行号 2.分页显示
more
Enter 显示下一行
空格 显示下一页
F 显示下一屏
B 显示上一屏
less
/get 查询"get"字符串并高亮显示 3.显示文件尾
tail
-f 不退出持续显示
-n 显示文件最后n行 4.显示头文件
head
-n 显示文件开始n行 5.内容排序
sort
-n 按照
- JSONP 原理分析
fantasy2005
JavaScriptjsonpjsonp 跨域
转自 http://www.nowamagic.net/librarys/veda/detail/224
JavaScript是一种在Web开发中经常使用的前端动态脚本技术。在JavaScript中,有一个很重要的安全性限制,被称为“Same-Origin Policy”(同源策略)。这一策略对于JavaScript代码能够访问的页面内容做了很重要的限制,即JavaScript只能访问与包含它的
- 使用connect by进行级联查询
234390216
oracle查询父子Connect by级联
使用connect by进行级联查询
connect by可以用于级联查询,常用于对具有树状结构的记录查询某一节点的所有子孙节点或所有祖辈节点。
来看一个示例,现假设我们拥有一个菜单表t_menu,其中只有三个字段:
- 一个不错的能将HTML表格导出为excel,pdf等的jquery插件
jackyrong
jquery插件
发现一个老外写的不错的jquery插件,可以实现将HTML
表格导出为excel,pdf等格式,
地址在:
https://github.com/kayalshri/
下面看个例子,实现导出表格到excel,pdf
<html>
<head>
<title>Export html table to excel an
- UI设计中我们为什么需要设计动效
lampcy
UIUI设计
关于Unity3D中的Shader的知识
首先先解释下Unity3D的Shader,Unity里面的Shaders是使用一种叫ShaderLab的语言编写的,它同微软的FX文件或者NVIDIA的CgFX有些类似。传统意义上的vertex shader和pixel shader还是使用标准的Cg/HLSL 编程语言编写的。因此Unity文档里面的Shader,都是指用ShaderLab编写的代码,
- 如何禁止页面缓存
nannan408
htmljspcache
禁止页面使用缓存~
------------------------------------------------
jsp:页面no cache:
response.setHeader("Pragma","No-cache");
response.setHeader("Cache-Control","no-cach
- 以代码的方式管理quartz定时任务的暂停、重启、删除、添加等
Everyday都不同
定时任务管理spring-quartz
【前言】在项目的管理功能中,对定时任务的管理有时会很常见。因为我们不能指望只在配置文件中配置好定时任务就行了,因为如果要控制定时任务的 “暂停” 呢?暂停之后又要在某个时间点 “重启” 该定时任务呢?或者说直接 “删除” 该定时任务呢?要改变某定时任务的触发时间呢? “添加” 一个定时任务对于系统的使用者而言,是不太现实的,因为一个定时任务的处理逻辑他是不
- EXT实例
tntxia
ext
(1) 增加一个按钮
JSP:
<%@ page language="java" import="java.util.*" pageEncoding="UTF-8"%>
<%
String path = request.getContextPath();
Stri
- 数学学习在计算机研究领域的作用和重要性
xjnine
Math
最近一直有师弟师妹和朋友问我数学和研究的关系,研一要去学什么数学课。毕竟在清华,衡量一个研究生最重要的指标之一就是paper,而没有数学,是肯定上不了世界顶级的期刊和会议的,这在计算机学界尤其重要!你会发现,不论哪个领域有价值的东西,都一定离不开数学!在这样一个信息时代,当google已经让世界没有秘密的时候,一种卓越的数学思维,绝对可以成为你的核心竞争力. 无奈本人实在见地