- discuz discuz_admincp.php 讲解,Discuz! 1.5-2.5 命令执行漏洞分析(CVE-2018-14729)
weixin_39740419
discuz讲解
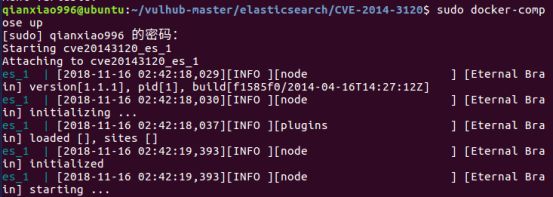
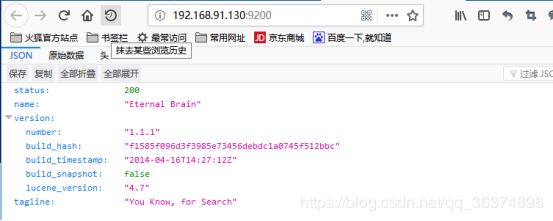
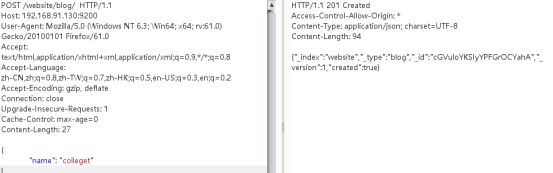
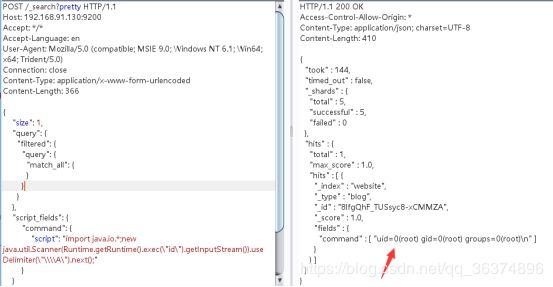
0x00漏洞简述漏洞信息8月27号有人在GitHub上公布了有关Discuz1.5-2.5版本中后台数据库备份功能存在的命令执行漏洞的细节。漏洞影响版本Discuz!1.5-2.50x01漏洞复现官方论坛下载相应版本就好。0x02漏洞分析需要注意的是这个漏洞其实是需要登录后台的,并且能有数据库备份权限,所以比较鸡肋。我这边是用Discuz!2.5完成漏洞复现的,并用此进行漏洞分析的。漏洞点在:so
- 【漏洞复现】2023HVV WPS Office 远程代码执行漏洞(RCE)
李火火安全阁
漏洞复现应用安全WPSOffice
文章目录前言声明一、漏洞描述二、影响范围三、漏洞复现服务端的功能客户端的功能四、修复建议前言2023HVV期间曝出的WPSOffice存在RCE漏洞,攻击者可通过该漏洞执行任意命令,获取服务器控制权限。声明请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
- aspcms webshell漏洞复现
青衫木牛马
aspaspcmsgetshell
1.【ip】/admin_aspcms/login.asp访问后台,admin123456登录2.点击【扩展功能】【幻灯片设置】点击【保存】开启代理进行抓包3.在抓取的数据包中修改slideTextStatus字段的值为以下代码并进行发包访问影响文件字段值1%25><%25密码是a影响文件/config/AspCms_Config.asp4.蚁剑连接
- Nginx越界读取缓存漏洞 CVE-2017-7529 漏洞复现
ADummy_
vulhub_Writeup网络安全渗透测试安全漏洞
Nginx越界读取缓存漏洞(CVE-2017-7529)byADummy0x00利用路线POC验证—>读取到缓存文件中位于“http返回包体”前的“文件头”、“http返回包头”等内容0x01漏洞介绍Nginx在反向代理站点的时候,通常会将一些文件进行缓存,特别是静态文件。缓存的部分存储在文件中,每个缓存文件包括“文件头”+“HTTP返回包头”+“HTTP返回包体”。如果二次请求命中了该缓存文件,
- 【漏洞复现】华三 H3C IMC 智能管理中心 /byod/index.xhtml RCE
凝聚力安全团队
漏洞复现xhtml前端htmlweb渗透web网络安全渗透测试
免责声明:本文内容旨在提供有关特定漏洞或安全漏洞的信息,以帮助用户更好地了解可能存在的风险。公布此类信息的目的在于促进网络安全意识和技术进步,并非出于任何恶意目的。阅读者应该明白,在利用本文提到的漏洞信息或进行相关测试时,可能会违反某些法律法规或服务协议。同时,未经授权地访问系统、网络或应用程序可能导致法律责任或其他严重后果。作者不对读者基于本文内容而产生的任何行为或后果承担责任。读者在使用本文所
- 「漏洞复现」契约锁电子签章平台 add 远程命令执行漏洞
鲨鱼辣椒丶D
漏洞复现web安全
0x01免责声明请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。工具来自网络,安全性自测,如有侵权请联系删除。本次测试仅供学习使用,如若非法他用,与平台和本文作者无关,需自行负责!!!0x02产品介绍契约锁电子签章平台是上海亘岩网络科技有限公司推出的一套数字签章解决方案。契约锁为中大型组织提供“数
- weblogic-SSRF漏洞复现(SSRF原理、利用与防御)
不想当脚本小子的脚本小子
中间件漏洞复现SSRF安全
一、SSRF概念服务端请求伪造(Server-SideRequestForgery),是一种由攻击者构造形成由服务端发起请求的一个安全漏洞。一般情况下,SSRF攻击的目标是从外网无法访问的内部系统。SSRF形成的原因大都是由于服务端提供了从其他服务器应用获取数据的功能,且没有对目标地址做过滤与限制。比如从指定URL地址获取网页文本内容,加载指定地址的图片、文档等等。首先,我们要对目标网站的架构了解
- fastbee物联网管理系统download接口任意文件下载漏洞
抠脚大汉在网络
漏洞复现漏洞
fastbee物联网管理系统download接口任意文件下载漏洞文章目录fastbee物联网管理系统download接口任意文件下载漏洞免责申明搜索语法漏洞描述漏洞复现修复建议免责申明本文章仅供学习与交流,请勿用于非法用途,均由使用者本人负责,文章作者不为此承担任何责任搜索语法fofaicon_hash="-307138793"&&title=="FastBee物联网系统"漏洞描述FastBee是
- 某云彩SRM2.0后台绕过漏洞
抠脚大汉在网络
漏洞复现漏洞
文章目录免责申明搜索语法漏洞描述漏洞复现修复建议免责申明本文章仅供学习与交流,请勿用于非法用途,均由使用者本人负责,文章作者不为此承担任何责任搜索语法fofaicon_hash="1665918155"漏洞描述某云采SRM2.0是一款先进的供应链管理系统,旨在优化企业的采购流程和供应商管理。该系统通过云端技术,提供实时的数据分析和智能决策支持,帮助企业提高采购效率和降低成本。该系统在autolog
- 【漏洞复现】蜂信物联 FastBee 开源物联网平台 download 任意文件读取漏洞
炫彩@之星
漏洞复现漏洞复现网络安全安全性测试安全
【漏洞复现】蜂信物联FastBee开源物联网平台download任意文件读取漏洞、01漏洞描述蜂信物联FastBee开源物联网平台download接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件),导致网站处于极度不安全状态。02漏洞环境FOFA语法:body=“FastBee物联网系统”||icon_hash=“-307138793”03漏
- CVE-2024-25852 Linksys RE7000无线扩展器 RCE漏洞
抠脚大汉在网络
漏洞复现漏洞漏洞
文章目录免责声明漏洞描述漏洞原理影响版本漏洞复现修复建议免责声明本文章仅供学习与交流,请勿用于非法用途,均由使用者本人负责,文章作者不为此承担任何责任漏洞描述RE7000是Linksys推出的一款具有无缝漫游功能的双频AC1900无线扩展器,重点是withseamlessroaming(无缝漫游)漏洞原理RE7000无线扩展器在访问/goform/AccessControl功能接口时在Access
- 用友U8 Cloud RepAddToTaskAction SQL注入漏洞复现
天官赐福万无禁忌
漏洞复现安全web安全
1产品简介用友U8Cloud是用友推出的新一代云ERP,主要聚焦成长型、创新型企业,提供企业级云ERP整体解决方案。2漏洞概述用友U8CloudRepAddToTaskAction接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。3影响范围
- 用友U8-CRM exportdictionary.php SQL注入
iSee857
漏洞复现安全
0x01漏洞描述:用友U8-CRM的/devtools/tools/exportdictionary.php接口处存在SQL注入漏洞。这可能导致泄露敏感数据、破坏数据库完整性,甚至获取对数据库的完全控制。0x02影响版本:V16.1,V16.0,V15.1,V15.0,V130x03搜索语句:Fofa:title="用友U8CRM"0x04漏洞复现:GET/devtools/tools/expor
- 用友U8 CRM exportdictionary.php SQL注入漏洞复现
0xSecl
漏洞复现安全web安全
0x01产品简介用友U8CRM客户关系管理系统是一款专业的企业级CRM软件,旨在帮助企业高效管理客户关系、提升销售业绩和提供优质的客户服务。0x02漏洞概述用友U8CRM客户关系管理系统exportdictionary.php文件存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。<
- 【系统安全】Windows内核权限提升漏洞(CVE-2024-30088)
李火火安全阁
漏洞复现系统安全系统安全windows
文章目录前言一、漏洞概述二、影响范围三、漏洞复现四、修复建议前言CVE-2024-30088是Windows内核提权漏洞,由越南安全研究员@BùiQuangHiếu详细分析。漏洞发生在AuthzBasepCopyoutInternalSecurityAttributes函数中,该函数在复制SecurityAttributesList时会使用用户提供的指针,在校验及复制期间存在时间差,导致存在TOC
- 福建科立讯通信 指挥调度管理平台 SQL注入漏洞复现(CVE-2024-2620、CVE-2024-2621)
OidBoy_G
漏洞复现安全web安全
0x01产品简介福建科立讯通信指挥调度管理平台是一个专门针对通信行业的管理平台。该产品旨在提供高效的指挥调度和管理解决方案,以帮助通信运营商或相关机构实现更好的运营效率和服务质量。该平台提供强大的指挥调度功能,可以实时监控和管理通信网络设备、维护人员和工作任务等。用户可以通过该平台发送指令、调度人员、分配任务,并即时获取现场反馈和报告。0x02漏洞概述福建科立讯通信指挥调度管理平台down_fil
- WordPress Plugin NotificationX插件 SQL注入漏洞复现(CVE-2024-1698)
OidBoy_G
漏洞复现sqlweb安全安全
0x01产品简介WordPress和WordPressplugin都是WordPress基金会的产品。WordPress是一套使用PHP语言开发的博客平台。该平台支持在PHP和MySQL的服务器上架设个人博客网站。0x02漏洞概述WordPresspluginNotificationX是一个应用插件。2.8.2版本及之前存在安全漏洞,该漏洞源于对用户提供的参数转义不充分以及对现有SQL查询缺乏充分
- 友点CMS GetSpecial SQL注入漏洞复现
OidBoy_G
漏洞复现安全web安全
0x01产品简介友点CMS是一款高效且灵活的网站管理系统,它为用户提供了简单易用的界面和丰富的功能。无论是企业还是个人,都能通过友点CMS快速搭建出专业且美观的网站。该系统支持多种内容类型和自定义模板,方便用户按需调整。同时,它具备强大的SEO功能,能提升网站在搜索引擎中的排名。友点CMS还支持多语言设置,适应国际化需求。总的来说,友点CMS是网站建设的理想选择,既高效又易用。0x02漏洞概述友点
- 友点CMS image_upload.php 文件上传漏洞复现
OidBoy_G
漏洞复现phpweb安全安全
0x01产品简介友点CMS是一款高效且灵活的网站管理系统,它为用户提供了简单易用的界面和丰富的功能。无论是企业还是个人,都能通过友点CMS快速搭建出专业且美观的网站。该系统支持多种内容类型和自定义模板,方便用户按需调整。同时,它具备强大的SEO功能,能提升网站在搜索引擎中的排名。友点CMS还支持多语言设置,适应国际化需求。总的来说,友点CMS是网站建设的理想选择,既高效又易用。0x02漏洞概述友点
- JeePlus快速开发平台 validateMobile SQL注入漏洞复现
OidBoy_G
漏洞复现sqlweb安全安全
0x01产品简介JeePlus(洁普斯)是一个软件快速开发平台,使用多种现代Web技术,包括SpringCloud/SpringBoot、MyBatisPlus、SpringSecurity、Redis、Vue3、ElementPlus等。该平台支持多种数据库,如MySQL、Oracle、sqlserver、postgresql等。JeePlus采用标准的SOA架构,依托优秀的前台富客户端框架(如
- F5漏洞复现[CVE-2020-5902]与[CVE_2021_22986]
Coder_preston
计算机安全pytorchgitbranch
引言 F5BIG-IP广泛应用于大型企业,数据中心、云计算平台中,可以实现应用加速、负载均衡、SLL过载、web应用防火墙等功能。这篇文章主要是复现F5的漏洞,包括其被远程代码执行的过程,以及探究以下我们可以在F5上远程执行代码之后可以做哪些事情。环境搭建 F5的环境搭建教程在网上可以查到很多,这里大概介绍以下流程与心得。首先搭建环境需要使用vmware软件运行F5的镜像来实现,需要下载并安装相关
- 【漏洞复现】F5 BIG-IP 远程代码执行漏洞(CVE-2023-46747)
webQD153
tcp/ip网络协议网络
F5BIG-IP远程代码执行漏洞(CVE-2023-46747)漏洞描述F5BIG-IP远程代码执行漏洞(CVE-2023-46747),未经授权的远程攻击者通过管理端口或自身IP地址访问BIG-IP系统,利用此漏洞可能绕过身份认证,导致在暴露流量管理用户界面(TMUI)的F5BIG-IP实例上执行任意代码。影响版本F5BIG-IP<=17.1.016.1.0<=F5BIG-IP<=16.1.41
- 命令执行漏洞超详细讲解
摆烂阳
网络安全服务器网络安全
博主昵称:摆烂阳博主主页跳转链接博主研究方向:web渗透测试、python编程博主寄语:希望本篇文章能给大家带来帮助,有不足的地方,希望友友们给予指导————————————————目录一、原理二、利用条件三、漏洞分类1、远程命令执行漏洞2、远程代码执行漏洞四、认识命令连接符1、window层面2、linux层面五、漏洞的产生原因六、漏洞的危害七、漏洞复现1、log4j命令执行2、向日葵命令执行
- [旧文系列] Struts2历史高危漏洞系列-part2:S2-007/S2-008/S2-009
xc8qanAFenlka@x1
struts安全web安全java
文章目录关于前言S2-007漏洞复现与分析可回显PoC漏洞修复S2-008漏洞复现与分析Vuln-1:RemotecommandexecutioninCookieInterceptorVuln-2:RemotecommandexecutioninDebuggingInterceptorVuln-2:可回显PoC漏洞修复S2-009漏洞复现与分析可回显PoC漏洞修复Reference关于系列是笔者将
- Struts2 S2-045漏洞复现
你能拿我咋的
渗透测试漏洞复现strutsjavaweb安全
1.漏洞概述OGNL是ObjectGraphicNavigationLanguage(对象图导航语言)的缩写,它是一个开源项目。Struts框架使用OGNL作为默认的表达式语言。struts2的rce本质都是一样的(除了S2-052以外),都是Struts2框架执行了恶意用户传进来的OGNL表达式,造成远程代码执行。可以造成“命令执行、服务器文件操作、打印回显、获取系统属性、危险代码执行”等,只不
- XMall 开源商城 SQL注入漏洞复现(CVE-2024-24112)
OidBoy_G
漏洞复现web安全安全sql
0x01产品简介XMall开源电商商城是开发者Exrick的一款基于SOA架构的分布式电商购物商城前后端分离前台商城:Vue全家桶后台管理:Dubbo/SSM/Elasticsearch/Redis/MySQL/ActiveMQ/Shiro/Zookeeper等。0x02漏洞概述XMall开源商城/item/list、/item/listSearch、/sys/log、/order/list、/m
- threehit漏洞复现以及防御
凌晨五点的星
网络安全安全web安全
说白了跟sql-liql靶场二次注入一样,也是一个转义函数而这次是,入库的时候不转义,出库的时候会转义导致这个漏洞出现开始测试:这是我注册完test刚登录的情况找注入点更新数据的update,很容易找到在age段这次我注册的时候用户还是test,但是年龄我对后面进行了省略可以看到我直接登录到管理员上了防御:可以进行强转这样无法闭合漏洞也就无法实现了
- 【漏洞复现】H3C 路由器多系列信息泄露漏洞
晚风不及你ღ
【漏洞复现】安全服务器web安全网络
Nx01产品简介H3C路由器是一款高性能的路由器产品,具有稳定的性能和丰富的功能。它采用了先进的路由技术和安全机制,可以满足不同用户的需求,广泛应用于企业、运营商和数据中心等领域。Nx02漏洞描述H3C路由器多系列存在信息泄露漏洞,攻击者可以利用该漏洞获取备份文件中的管理员账户及密码等敏感信息。Nx03产品主页hunter-query:app.name="H3CRouterManagement"N
- vulhub中Apache Log4j Server 反序列化命令执行漏洞复现(CVE-2017-5645)
余生有个小酒馆
vulhub漏洞复现apachelog4j
ApacheLog4j是一个用于Java的日志记录库,其支持启动远程日志服务器。ApacheLog4j2.8.2之前的2.x版本中存在安全漏洞。攻击者可利用该漏洞执行任意代码。1.我们使用ysoserial生成payload,然后直接发送给`your-ip:4712`端口即可。java-jarysoserial-master-v0.0.5-gb617b7b-16.jarCommonsCollect
- 【漏洞复现-通达OA】通达OA getcallist存在前台SQL注入漏洞
xiaokp7
漏洞复现sql数据库
一、漏洞简介通达OA(OfficeAnywhere网络智能办公系统)是由北京通达信科科技有限公司自主研发的协同办公自动化软件,是与中国企业管理实践相结合形成的综合管理办公平台。通达OA为各行业不同规模的众多用户提供信息化管理能力,包括流程审批、行政办公、日常事务、数据统计分析、即时通讯、移动办公等,帮助广大用户降低沟通和管理成本,提升生产和决策效率。通达OAgetcallist存在前台SQL注入漏
- jdk tomcat 环境变量配置
Array_06
javajdktomcat
Win7 下如何配置java环境变量
1。准备jdk包,win7系统,tomcat安装包(均上网下载即可)
2。进行对jdk的安装,尽量为默认路径(但要记住啊!!以防以后配置用。。。)
3。分别配置高级环境变量。
电脑-->右击属性-->高级环境变量-->环境变量。
分别配置 :
path
&nbs
- Spring调SDK包报java.lang.NoSuchFieldError错误
bijian1013
javaspring
在工作中调另一个系统的SDK包,出现如下java.lang.NoSuchFieldError错误。
org.springframework.web.util.NestedServletException: Handler processing failed; nested exception is java.l
- LeetCode[位运算] - #136 数组中的单一数
Cwind
java题解位运算LeetCodeAlgorithm
原题链接:#136 Single Number
要求:
给定一个整型数组,其中除了一个元素之外,每个元素都出现两次。找出这个元素
注意:算法的时间复杂度应为O(n),最好不使用额外的内存空间
难度:中等
分析:
题目限定了线性的时间复杂度,同时不使用额外的空间,即要求只遍历数组一遍得出结果。由于异或运算 n XOR n = 0, n XOR 0 = n,故将数组中的每个元素进
- qq登陆界面开发
15700786134
qq
今天我们来开发一个qq登陆界面,首先写一个界面程序,一个界面首先是一个Frame对象,即是一个窗体。然后在这个窗体上放置其他组件。代码如下:
public class First { public void initul(){ jf=ne
- Linux的程序包管理器RPM
被触发
linux
在早期我们使用源代码的方式来安装软件时,都需要先把源程序代码编译成可执行的二进制安装程序,然后进行安装。这就意味着每次安装软件都需要经过预处理-->编译-->汇编-->链接-->生成安装文件--> 安装,这个复杂而艰辛的过程。为简化安装步骤,便于广大用户的安装部署程序,程序提供商就在特定的系统上面编译好相关程序的安装文件并进行打包,提供给大家下载,我们只需要根据自己的
- socket通信遇到EOFException
肆无忌惮_
EOFException
java.io.EOFException
at java.io.ObjectInputStream$PeekInputStream.readFully(ObjectInputStream.java:2281)
at java.io.ObjectInputStream$BlockDataInputStream.readShort(ObjectInputStream.java:
- 基于spring的web项目定时操作
知了ing
javaWeb
废话不多说,直接上代码,很简单 配置一下项目启动就行
1,web.xml
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns="h
- 树形结构的数据库表Schema设计
矮蛋蛋
schema
原文地址:
http://blog.csdn.net/MONKEY_D_MENG/article/details/6647488
程序设计过程中,我们常常用树形结构来表征某些数据的关联关系,如企业上下级部门、栏目结构、商品分类等等,通常而言,这些树状结构需要借助于数据库完成持久化。然而目前的各种基于关系的数据库,都是以二维表的形式记录存储数据信息,
- maven将jar包和源码一起打包到本地仓库
alleni123
maven
http://stackoverflow.com/questions/4031987/how-to-upload-sources-to-local-maven-repository
<project>
...
<build>
<plugins>
<plugin>
<groupI
- java IO操作 与 File 获取文件或文件夹的大小,可读,等属性!!!
百合不是茶
类 File
File是指文件和目录路径名的抽象表示形式。
1,何为文件:
标准文件(txt doc mp3...)
目录文件(文件夹)
虚拟内存文件
2,File类中有可以创建文件的 createNewFile()方法,在创建新文件的时候需要try{} catch(){}因为可能会抛出异常;也有可以判断文件是否是一个标准文件的方法isFile();这些防抖都
- Spring注入有继承关系的类(2)
bijian1013
javaspring
被注入类的父类有相应的属性,Spring可以直接注入相应的属性,如下所例:1.AClass类
package com.bijian.spring.test4;
public class AClass {
private String a;
private String b;
public String getA() {
retu
- 30岁转型期你能否成为成功人士
bijian1013
成长励志
很多人由于年轻时走了弯路,到了30岁一事无成,这样的例子大有人在。但同样也有一些人,整个职业生涯都发展得很优秀,到了30岁已经成为职场的精英阶层。由于做猎头的原因,我们接触很多30岁左右的经理人,发现他们在职业发展道路上往往有很多致命的问题。在30岁之前,他们的职业生涯表现很优秀,但从30岁到40岁这一段,很多人
- 【Velocity四】Velocity与Java互操作
bit1129
velocity
Velocity出现的目的用于简化基于MVC的web应用开发,用于替代JSP标签技术,那么Velocity如何访问Java代码.本篇继续以Velocity三http://bit1129.iteye.com/blog/2106142中的例子为基础,
POJO
package com.tom.servlets;
public
- 【Hive十一】Hive数据倾斜优化
bit1129
hive
什么是Hive数据倾斜问题
操作:join,group by,count distinct
现象:任务进度长时间维持在99%(或100%),查看任务监控页面,发现只有少量(1个或几个)reduce子任务未完成;查看未完成的子任务,可以看到本地读写数据量积累非常大,通常超过10GB可以认定为发生数据倾斜。
原因:key分布不均匀
倾斜度衡量:平均记录数超过50w且
- 在nginx中集成lua脚本:添加自定义Http头,封IP等
ronin47
nginx lua csrf
Lua是一个可以嵌入到Nginx配置文件中的动态脚本语言,从而可以在Nginx请求处理的任何阶段执行各种Lua代码。刚开始我们只是用Lua 把请求路由到后端服务器,但是它对我们架构的作用超出了我们的预期。下面就讲讲我们所做的工作。 强制搜索引擎只索引mixlr.com
Google把子域名当作完全独立的网站,我们不希望爬虫抓取子域名的页面,降低我们的Page rank。
location /{
- java-3.求子数组的最大和
bylijinnan
java
package beautyOfCoding;
public class MaxSubArraySum {
/**
* 3.求子数组的最大和
题目描述:
输入一个整形数组,数组里有正数也有负数。
数组中连续的一个或多个整数组成一个子数组,每个子数组都有一个和。
求所有子数组的和的最大值。要求时间复杂度为O(n)。
例如输入的数组为1, -2, 3, 10, -4,
- Netty源码学习-FileRegion
bylijinnan
javanetty
今天看org.jboss.netty.example.http.file.HttpStaticFileServerHandler.java
可以直接往channel里面写入一个FileRegion对象,而不需要相应的encoder:
//pipeline(没有诸如“FileRegionEncoder”的handler):
public ChannelPipeline ge
- 使用ZeroClipboard解决跨浏览器复制到剪贴板的问题
cngolon
跨浏览器复制到粘贴板Zero Clipboard
Zero Clipboard的实现原理
Zero Clipboard 利用透明的Flash让其漂浮在复制按钮之上,这样其实点击的不是按钮而是 Flash ,这样将需要的内容传入Flash,再通过Flash的复制功能把传入的内容复制到剪贴板。
Zero Clipboard的安装方法
首先需要下载 Zero Clipboard的压缩包,解压后把文件夹中两个文件:ZeroClipboard.js
- 单例模式
cuishikuan
单例模式
第一种(懒汉,线程不安全):
public class Singleton { 2 private static Singleton instance; 3 pri
- spring+websocket的使用
dalan_123
一、spring配置文件
<?xml version="1.0" encoding="UTF-8"?><beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.or
- 细节问题:ZEROFILL的用法范围。
dcj3sjt126com
mysql
1、zerofill把月份中的一位数字比如1,2,3等加前导0
mysql> CREATE TABLE t1 (year YEAR(4), month INT(2) UNSIGNED ZEROFILL, -> day
- Android开发10——Activity的跳转与传值
dcj3sjt126com
Android开发
Activity跳转与传值,主要是通过Intent类,Intent的作用是激活组件和附带数据。
一、Activity跳转
方法一Intent intent = new Intent(A.this, B.class); startActivity(intent)
方法二Intent intent = new Intent();intent.setCla
- jdbc 得到表结构、主键
eksliang
jdbc 得到表结构、主键
转自博客:http://blog.csdn.net/ocean1010/article/details/7266042
假设有个con DatabaseMetaData dbmd = con.getMetaData(); rs = dbmd.getColumns(con.getCatalog(), schema, tableName, null); rs.getSt
- Android 应用程序开关GPS
gqdy365
android
要在应用程序中操作GPS开关需要权限:
<uses-permission android:name="android.permission.WRITE_SECURE_SETTINGS" />
但在配置文件中添加此权限之后会报错,无法再eclipse里面正常编译,怎么办?
1、方法一:将项目放到Android源码中编译;
2、方法二:网上有人说cl
- Windows上调试MapReduce
zhiquanliu
mapreduce
1.下载hadoop2x-eclipse-plugin https://github.com/winghc/hadoop2x-eclipse-plugin.git 把 hadoop2.6.0-eclipse-plugin.jar 放到eclipse plugin 目录中。 2.下载 hadoop2.6_x64_.zip http://dl.iteye.com/topics/download/d2b
- 如何看待一些知名博客推广软文的行为?
justjavac
博客
本文来自我在知乎上的一个回答:http://www.zhihu.com/question/23431810/answer/24588621
互联网上的两种典型心态:
当初求种像条狗,如今撸完嫌人丑
当初搜贴像条犬,如今读完嫌人软
你为啥感觉不舒服呢?
难道非得要作者把自己的劳动成果免费给你用,你才舒服?
就如同 Google 关闭了 Gooled Reader,那是
- sql优化总结
macroli
sql
为了是自己对sql优化有更好的原则性,在这里做一下总结,个人原则如有不对请多多指教。谢谢!
要知道一个简单的sql语句执行效率,就要有查看方式,一遍更好的进行优化。
一、简单的统计语句执行时间
declare @d datetime ---定义一个datetime的变量set @d=getdate() ---获取查询语句开始前的时间select user_id
- Linux Oracle中常遇到的一些问题及命令总结
超声波
oraclelinux
1.linux更改主机名
(1)#hostname oracledb 临时修改主机名
(2) vi /etc/sysconfig/network 修改hostname
(3) vi /etc/hosts 修改IP对应的主机名
2.linux重启oracle实例及监听的各种方法
(注意操作的顺序应该是先监听,后数据库实例)
&nbs
- hive函数大全及使用示例
superlxw1234
hadoophive函数
具体说明及示例参 见附件文档。
文档目录:
目录
一、关系运算: 4
1. 等值比较: = 4
2. 不等值比较: <> 4
3. 小于比较: < 4
4. 小于等于比较: <= 4
5. 大于比较: > 5
6. 大于等于比较: >= 5
7. 空值判断: IS NULL 5
- Spring 4.2新特性-使用@Order调整配置类加载顺序
wiselyman
spring 4
4.1 @Order
Spring 4.2 利用@Order控制配置类的加载顺序
4.2 演示
两个演示bean
package com.wisely.spring4_2.order;
public class Demo1Service {
}
package com.wisely.spring4_2.order;
public class