- NSSCTF_crypto_[HGAME 2022 week3]RSA attack 3
岁岁的O泡奶
python开发语言密码学cryptoNSSCTF维纳攻击
[HGAME2022week3]RSAattack3题目:太多了自己去看,提示:维纳攻击首先在做这题之前你得先懂得维纳攻击的原理https://www.cnblogs.com/wandervogel/p/16805992.htmlok啊看懂了维纳攻击的原理就来开始写脚本吧fromCrypto.Util.numberimportlong_to_bytesimportgmpy2#已知参数n=50741
- 新手必看——ctf六大题型介绍及六大题型解析&举例解题
沛哥网络安全
web安全学习安全udp网络协议
CTF(CaptureTheFlag)介绍与六大题型解析一、什么是CTF?CTF(CaptureTheFlag),意为“夺旗赛”,是一种信息安全竞赛形式,广泛应用于网络安全领域。CTF竞赛通过模拟现实中的网络安全攻防战,让参赛者以攻防对抗的形式,利用各种信息安全技术进行解决一系列安全问题,最终获得“旗帜(Flag)”来获得积分。CTF赛事一般分为两种形式:Jeopardy(解题模式):参赛者通过解
- 安卓无线调试连接不上
王的备忘录
A1_android开发基础android
今天发现的一个问题,如果要连接的是新手机,会无法连接上。提示connectfail。原因是第一次调试,先要在手机上进行授权。解决方法就是要先通过数据线连接手机,在手机端同意连接,之后再运用adb无线调试就可以连接了。
- HTML 元素和有效 DOCTYPES
智慧浩海
HTMLhtml前端
HTML元素-有效DOCTYPES下面的表格列出了所有的HTML5/HTML4.01/XHTML元素,以及它们会出现在什么文档类型(!DOCTYPE)中:HTML4.01/XHTML1.0TagHTML5TransitionalStrictFramesetXHTML1.1YesYesYesYesYesYesYesYesYesYesNoYesYesYesYesYesYesYesYesYesNoYes
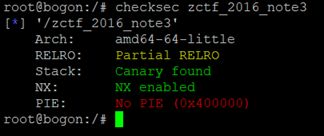
- Canary
Sean_summer
安全web安全
定义:Canary是一种用以防护栈溢出的保护机制。原理:是在一个函数的入口处,先从fs/gs寄存器中取出一个4字节(eax,四字节通常是32位的文件)或者8字节(rax,通常是64位的文件)的值存到栈上,当函数结束是会检查这个栈上的值是否和存进去的值相同。通常在pwn题写exp是用的字符a,这样存储进缓冲区,将会覆盖原始的canary的值当canary被覆盖后,也就是原应为canary的位置被字符
- CTF学习法则——寒假篇 新手赶快收藏吧!
网络安全技术分享
学习网络安全web安全php
CTF(CapturetheFlag)是网络安全领域中的一种比赛形式,涵盖了漏洞利用、逆向工程、加密解密、编码解码等多方面的技术,参与者通过解决难题(称为“Flag”)获得积分。对于想要在寒假期间提升CTF技能的同学们,以下是一些有效的学习法则,可以帮助你高效地进行学习和提升:1.合理规划学习时间寒假时间有限,建议制定合理的学习计划:每天固定时间学习:保持稳定的学习节奏,避免临时抱佛脚。分阶段学习
- 设计模式详解:提高代码复用性与可维护性的关键
誰能久伴不乏
设计模式
文章目录设计模式详解:提高代码复用性与可维护性的关键1.设计模式的分类2.创建型设计模式2.1单例模式(SingletonPattern)工作原理:代码示例:线程安全:2.2工厂方法模式(FactoryMethodPattern)工作原理:代码示例:适用场景:2.3抽象工厂模式(AbstractFactoryPattern)工作原理:代码示例:适用场景:2.4建造者模式(BuilderPatter
- [HelloCTF]PHPinclude-labs超详细WP-Level 2-data协议
Haicaji
WPphp网络安全web安全
源码分析重点关注这两行代码echoinclude("data://text/plain;base64,4pedKCrigbDilr/igbAqKeKXnEhlbGxvLUNURnd3");isset($_GET['wrappers'])?include("data://text/plain".$_GET['wrappers']):'';发现这里出现了data协议data://-数据流(RFC239
- 前端怎么处理请求失败会弹出一个 toast,如何保证批量请求失败,只弹出一个
大莲芒
前端
在前端处理批量请求时,确保只弹出一个toast通知,可以通过以下步骤实现:使用状态管理首先,您可以使用状态管理工具(例如React的useState或Redux)来跟踪请求的状态。创建一个Toast组件如果还没有创建toast组件,可以简单实现一个。以下是一个基本的Reacttoast组件示例importReactfrom'react';import'./Toast.css';//添加样式cons
- ctfshow-stack36
dd-pwn
pwn
每天下午抖音(47253061271)直播pwn题,小白一只,欢迎各位师傅讨论可以发现全文只有一个ctfshow的自定义函数Gets函数,发现有溢出漏洞,可以利用该漏洞进行构建exp,发现有get_flag供我们使用,可以直接打开根目录的flag,因此只需要构造溢出,溢出返回地址覆盖成get_flag就行Exp:
- 新手必看——ctf六大题型介绍及六大题型解析&举例解题
沛哥网络安全
web安全学习安全udp网络协议
CTF(CaptureTheFlag)介绍与六大题型解析一、什么是CTF?CTF(CaptureTheFlag),意为“夺旗赛”,是一种信息安全竞赛形式,广泛应用于网络安全领域。CTF竞赛通过模拟现实中的网络安全攻防战,让参赛者以攻防对抗的形式,利用各种信息安全技术进行解决一系列安全问题,最终获得“旗帜(Flag)”来获得积分。CTF赛事一般分为两种形式:Jeopardy(解题模式):参赛者通过解
- 用于AI-CV项目标注的星标模型
深蓝海拓
pyside6系统学习机器视觉和人工智能学习pyside6学习笔记python开发语言pyqt
功能:生成星标图形项,并在目标点上将底图颜色反色显示,当定位和拖动后输出底图在标记点的像素值。输入和输出使用信号槽机制。代码:importmathimportsysfromPySide6.QtCoreimportQPointF,QObject,QRectF,SignalfromPySide6.QtGuiimportQBrush,QPixmap,QColor,QPenfromPySide6.QtWi
- 自我学习: Django-用户登录+中间件
yzybang
django中间件学习
以form来做,因为form没有写入能力,比较安全fromdjango.shortcutsimportrender,HttpResponse,redirectfromapp01importmodelsfromdjangoimportformsfromapp01.utils.encryptimportmd5#form需自己定义“字段”classLoginForm(forms.Form):name=f
- 深度探索 Java 代码审计:筑牢安全防线的关键之路
阿贾克斯的黎明
javajava安全开发语言
在当今高度数字化的时代,软件安全成为了至关重要的议题。对于众多使用Java语言进行开发的程序员而言,深入掌握Java代码审计技能,无疑是守护软件安全的核心手段。本文将围绕一本涵盖Java代码审计丰富知识的书籍目录,全面剖析Java代码审计的各个关键环节以及其在CTFAWD比赛中的重要应用。一、学习经验:开启Java代码审计的智慧之门Java代码审计之路并非坦途,需要有系统的学习方法和实践经验。书籍
- 【2025年春季】全国CTF夺旗赛-从零基础入门到竞赛,看这一篇就稳了!
白帽子凯哥
web安全学习安全CTF夺旗赛网络安全
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包目录一、CTF简介二、CTF竞赛模式三、CTF各大题型简介四、CTF学习路线4.1、初期1、html+css+js(2-3天)2、apache+php(4-5天)3、mysql(2-3天)4、python(2-3天)5、burpsuite(1-2天)4.2、中期1、SQL注入(7-8天)2、文件上传(7-8天)3、其他漏洞(14-15
- 抽象工厂模式
倒霉男孩
java设计模式抽象工厂模式
抽象工厂模式抽象工厂模式是一种创建型设计模式,旨在提供一个接口来创建一系列相关或依赖对象,而无需指定其具体类。同级别产品指同一类型产品,,同产品族是指一组相关的对象或产品,类似同一品牌。抽象工厂模式是工厂方法模式的升级版,工厂方法模式只生产一个等级的产品,而抽象工厂模式可生产多个等级的产品。抽象工厂模式结构:抽象工厂(AbstractFactory):声明创建不同产品的方法(如createButt
- 抽象工厂模式(附C++代码示例)
Warren++
设计模式抽象工厂模式c++开发语言设计模式
抽象工厂模式抽象工厂模式的含义核心思想及解释为什么要使用抽象工厂模式使用抽象工厂模式需要注意的点工程的应用场景示例代码及解释输出代码运行结果抽象工厂模式的含义抽象工厂模式(AbstractFactoryPattern)是一种创建型设计模式,它提供了一种方式,能够封装一组具有共同主题但各自独立的工厂,而无需指定具体类。抽象工厂模式允许客户端通过接口操作实例,而不需要依赖具体类。核心思想及解释抽象工厂
- 突破编程_C++_设计模式(抽象工厂模式)
breakthrough_01
突破编程_C++_设计模式c++设计模式抽象工厂模式
1抽象工厂的基本概念在C++中,抽象工厂(AbstractFactory)提供了一种方式来封装一系列相互关联或相互依赖的对象创建过程,而无需指定它们具体的类。抽象工厂模式允许客户端代码使用抽象接口来创建一系列相关的对象,而无需了解这些对象的具体实现。抽象工厂模式通常包含以下几个组成部分:(1)抽象工厂(AbstractFactory):这是一个接口或抽象类,它声明了创建一系列相关对象的方法。这些方
- 设计模式2之c++抽象工厂模式(示例代码)
小激动. Caim
设计模式设计模式c++抽象工厂模式
抽象工厂模式(AbstractFactoryPattern)是一种创建型设计模式,它提供了一种创建一系列相关或相互依赖对象的接口,而无需指定它们具体的类。在抽象工厂模式中,一个工厂类可以创建多个产品族,每个产品族包含多个产品。抽象工厂模式的角色:抽象工厂(AbstractFactory):定义了创建产品族的接口。具体工厂(ConcreteFactory):实现抽象工厂接口,创建具体产品。抽象产品(
- UE中:运行时(伪)无限细分网格
Dawn·张
android数码相机
先看效果:UE:运行时(伪)无限细分网格实际代码如下:InfiniteGrid.h#pragmaonce#include"CoreMinimal.h"#include"GameFramework/Actor.h"#include"InfiniteGrid.generated.h"USTRUCT()structFGridLayer{GENERATED_BODY()UPROPERTY(EditAnyw
- 《架构300讲》学习笔记(201-250)
newProxyInstance
笔记架构
前言内容来自B站IT老齐架构300讲内容。201小心selectforupdate,有效规避索引选择性锁表202设计模式之建造者模式的用途20320分钟上手ELK日志监控系统分类:【ELK】204设计模式之门面模式Facade205设计模式之适配器模式Adapter206经典设计!如何让RabbitMQ支持消息延迟投递207Docker容器基于NFS实现跨容器文件共享208数据向上追溯场景该如何优
- Pwn,我的栈溢出笔记就该这么写(上)
「已注销」
栈
一周的刨坟结束了,忙着搭建维护k8s,该整个小小的笔记了原理篇什么是栈溢出?栈溢出指的是程序向栈中某个变量中写入的字节数超过了这个变量本身所申请的字节数,因而导致与其相邻的栈中的变量的值被改变。栈溢出会导致什么结果?栈溢出漏洞轻则可以使程序崩溃,重则可以使攻击者控制程序执行流程。如何防范栈溢出?(1).金丝雀(canary)1、在所有函数调用发生时,向栈帧内压入一个额外的随机DWORD(数),这个
- ctfshow做题笔记—前置基础—pwn13~pwn19
Yilanchia
笔记学习
文章目录前言一、pwn13二、pwn14三、pwn15(编译汇编代码到可执行文件,即可拿到flag)四、pwn16(使用gcc将其编译为可执行文件)五、pwn17六、pwn18七、pwn19(关闭了输出流,一定是最安全的吗?)前言记录一下pwn13~pwn19,巩固一下学到的知识。一、pwn13知识点:如何使用GCCgccmain.c-oprogram·gcc是调用GCC编译器的命令。·-opro
- ctf-web:php反序列化逃逸 -- GHCTF Escape!
A5rZ
php网络安全
step1寻找利用点随便注册一个进去,能写入文件isadmin){$tmp=file_get_contents("tmp/admin.html");echo$tmp;if($_POST['txt']){$content='';$content.=$_POST['txt'];file_put_contents($_POST['filename'],$content);}}else{$tmp=file
- Linux图形界面中客户端、服务器、窗口管理器之间的关系
谁不小心的
linux系统使用界面linux桌面环境x
作者:刘老师,华清远见嵌入式学院金牌讲师,ARMATC授权培训讲师。很多LINUX初学者在学习linux图形方面的知识时会遇到一些概念,如:X、X11、Xfree86、WM、KDE、GNOME、QT、QT/E、Qtopia、DirectFB、Framebuffer、显卡加速驱动等等。理解它们之间是什么关系,对我们学习来说是非常重要的。写这篇文章的目的,就是想让大家明晰这些概念及它们之间的关系。(部
- CTF中常用的小寄巧
脚底儿
网络网络安全ctf
ctf常用密码本/usr/share/wordlists最常用rockyou.txt需要gunzip解压一下全端口扫描nmap-sS-p1-65535-v192.168.187.1372、nmap扫描主机IP,发现目标主机IP为192.168.59.128nmap-sP-sV192.168.59.0/24主机发现:arp-scan-Ieth0-l^网卡打印可打印字符strings-el536.dm
- 新手必看——ctf六大题型介绍及六大题型解析&举例解题
沛哥网络安全
web安全学习安全udp网络协议
CTF(CaptureTheFlag)介绍与六大题型解析一、什么是CTF?CTF(CaptureTheFlag),意为“夺旗赛”,是一种信息安全竞赛形式,广泛应用于网络安全领域。CTF竞赛通过模拟现实中的网络安全攻防战,让参赛者以攻防对抗的形式,利用各种信息安全技术进行解决一系列安全问题,最终获得“旗帜(Flag)”来获得积分。CTF赛事一般分为两种形式:Jeopardy(解题模式):参赛者通过解
- 可重构智能表面仿真平台
brook1711
RIS
RIScomponentsThisisapythonprojectforRIS(reconfigurableintelligentsurface)simulations.relatedworksMyfirstpaperLinktomypaper/Pdftomypaper:[1]X.Guo,Y.ChenandY.Wang,“Learning-basedRobustandSecureTransmiss
- 第一篇:CTF入门指南:了解CTF的基本概念与比赛形式
菜腿承希
零基础小白入门CTFpythonjava网络安全前端
#零基础小白入门CTF解题到成为CTF大佬系列文章##引言CTF(CaptureTheFlag)是一种网络安全竞赛,参赛者需要通过解决各种安全相关的题目来获取“Flag”,从而得分。CTF题目通常涵盖密码学、逆向工程、漏洞利用、Web安全等多个领域。本系列文章将从零基础开始,逐步带你了解CTF的各个知识点,最终帮助你成为一名CTF大佬。##文章目录1.**CTF入门指南:了解CTF的基本概念与比赛
- 第二篇:CTF常见题型解析:密码学、逆向工程、漏洞利用、Web安全
菜腿承希
零基础小白入门CTFweb安全网络安全
#零基础小白入门CTF解题到成为CTF大佬系列文章##第二篇:CTF常见题型解析:密码学、逆向工程、漏洞利用、Web安全###引言在CTF比赛中,题目类型多种多样,涵盖了网络安全领域的多个方向。掌握这些题型的解题方法,是成为CTF大佬的关键。在本篇文章中,我们将详细解析CTF中常见的四大题型:密码学、逆向工程、漏洞利用和Web安全,帮助你快速入门并掌握解题技巧。---##2.1密码学(Crypto
- 基本数据类型和引用类型的初始值
3213213333332132
java基础
package com.array;
/**
* @Description 测试初始值
* @author FuJianyong
* 2015-1-22上午10:31:53
*/
public class ArrayTest {
ArrayTest at;
String str;
byte bt;
short s;
int i;
long
- 摘抄笔记--《编写高质量代码:改善Java程序的151个建议》
白糖_
高质量代码
记得3年前刚到公司,同桌同事见我无事可做就借我看《编写高质量代码:改善Java程序的151个建议》这本书,当时看了几页没上心就没研究了。到上个月在公司偶然看到,于是乎又找来看看,我的天,真是非常多的干货,对于我这种静不下心的人真是帮助莫大呀。
看完整本书,也记了不少笔记
- 【备忘】Django 常用命令及最佳实践
dongwei_6688
django
注意:本文基于 Django 1.8.2 版本
生成数据库迁移脚本(python 脚本)
python manage.py makemigrations polls
说明:polls 是你的应用名字,运行该命令时需要根据你的应用名字进行调整
查看该次迁移需要执行的 SQL 语句(只查看语句,并不应用到数据库上):
python manage.p
- 阶乘算法之一N! 末尾有多少个零
周凡杨
java算法阶乘面试效率
&n
- spring注入servlet
g21121
Spring注入
传统的配置方法是无法将bean或属性直接注入到servlet中的,配置代理servlet亦比较麻烦,这里其实有比较简单的方法,其实就是在servlet的init()方法中加入要注入的内容:
ServletContext application = getServletContext();
WebApplicationContext wac = WebApplicationContextUtil
- Jenkins 命令行操作说明文档
510888780
centos
假设Jenkins的URL为http://22.11.140.38:9080/jenkins/
基本的格式为
java
基本的格式为
java -jar jenkins-cli.jar [-s JENKINS_URL] command [options][args]
下面具体介绍各个命令的作用及基本使用方法
1. &nb
- UnicodeBlock检测中文用法
布衣凌宇
UnicodeBlock
/** * 判断输入的是汉字 */ public static boolean isChinese(char c) { Character.UnicodeBlock ub = Character.UnicodeBlock.of(c);
- java下实现调用oracle的存储过程和函数
aijuans
javaorale
1.创建表:STOCK_PRICES
2.插入测试数据:
3.建立一个返回游标:
PKG_PUB_UTILS
4.创建和存储过程:P_GET_PRICE
5.创建函数:
6.JAVA调用存储过程返回结果集
JDBCoracle10G_INVO
- Velocity Toolbox
antlove
模板toolboxvelocity
velocity.VelocityUtil
package velocity;
import org.apache.velocity.Template;
import org.apache.velocity.app.Velocity;
import org.apache.velocity.app.VelocityEngine;
import org.apache.velocity.c
- JAVA正则表达式匹配基础
百合不是茶
java正则表达式的匹配
正则表达式;提高程序的性能,简化代码,提高代码的可读性,简化对字符串的操作
正则表达式的用途;
字符串的匹配
字符串的分割
字符串的查找
字符串的替换
正则表达式的验证语法
[a] //[]表示这个字符只出现一次 ,[a] 表示a只出现一
- 是否使用EL表达式的配置
bijian1013
jspweb.xmlELEasyTemplate
今天在开发过程中发现一个细节问题,由于前端采用EasyTemplate模板方法实现数据展示,但老是不能正常显示出来。后来发现竟是EL将我的EasyTemplate的${...}解释执行了,导致我的模板不能正常展示后台数据。
网
- 精通Oracle10编程SQL(1-3)PLSQL基础
bijian1013
oracle数据库plsql
--只包含执行部分的PL/SQL块
--set serveroutput off
begin
dbms_output.put_line('Hello,everyone!');
end;
select * from emp;
--包含定义部分和执行部分的PL/SQL块
declare
v_ename varchar2(5);
begin
select
- 【Nginx三】Nginx作为反向代理服务器
bit1129
nginx
Nginx一个常用的功能是作为代理服务器。代理服务器通常完成如下的功能:
接受客户端请求
将请求转发给被代理的服务器
从被代理的服务器获得响应结果
把响应结果返回给客户端
实例
本文把Nginx配置成一个简单的代理服务器
对于静态的html和图片,直接从Nginx获取
对于动态的页面,例如JSP或者Servlet,Nginx则将请求转发给Res
- Plugin execution not covered by lifecycle configuration: org.apache.maven.plugin
blackproof
maven报错
转:http://stackoverflow.com/questions/6352208/how-to-solve-plugin-execution-not-covered-by-lifecycle-configuration-for-sprin
maven报错:
Plugin execution not covered by lifecycle configuration:
- 发布docker程序到marathon
ronin47
docker 发布应用
1 发布docker程序到marathon 1.1 搭建私有docker registry 1.1.1 安装docker regisry
docker pull docker-registry
docker run -t -p 5000:5000 docker-registry
下载docker镜像并发布到私有registry
docker pull consol/tomcat-8.0
- java-57-用两个栈实现队列&&用两个队列实现一个栈
bylijinnan
java
import java.util.ArrayList;
import java.util.List;
import java.util.Stack;
/*
* Q 57 用两个栈实现队列
*/
public class QueueImplementByTwoStacks {
private Stack<Integer> stack1;
pr
- Nginx配置性能优化
cfyme
nginx
转载地址:http://blog.csdn.net/xifeijian/article/details/20956605
大多数的Nginx安装指南告诉你如下基础知识——通过apt-get安装,修改这里或那里的几行配置,好了,你已经有了一个Web服务器了。而且,在大多数情况下,一个常规安装的nginx对你的网站来说已经能很好地工作了。然而,如果你真的想挤压出Nginx的性能,你必
- [JAVA图形图像]JAVA体系需要稳扎稳打,逐步推进图像图形处理技术
comsci
java
对图形图像进行精确处理,需要大量的数学工具,即使是从底层硬件模拟层开始设计,也离不开大量的数学工具包,因为我认为,JAVA语言体系在图形图像处理模块上面的研发工作,需要从开发一些基础的,类似实时数学函数构造器和解析器的软件包入手,而不是急于利用第三方代码工具来实现一个不严格的图形图像处理软件......
&nb
- MonkeyRunner的使用
dai_lm
androidMonkeyRunner
要使用MonkeyRunner,就要学习使用Python,哎
先抄一段官方doc里的代码
作用是启动一个程序(应该是启动程序默认的Activity),然后按MENU键,并截屏
# Imports the monkeyrunner modules used by this program
from com.android.monkeyrunner import MonkeyRun
- Hadoop-- 海量文件的分布式计算处理方案
datamachine
mapreducehadoop分布式计算
csdn的一个关于hadoop的分布式处理方案,存档。
原帖:http://blog.csdn.net/calvinxiu/article/details/1506112。
Hadoop 是Google MapReduce的一个Java实现。MapReduce是一种简化的分布式编程模式,让程序自动分布到一个由普通机器组成的超大集群上并发执行。就如同ja
- 以資料庫驗證登入
dcj3sjt126com
yii
以資料庫驗證登入
由於 Yii 內定的原始框架程式, 採用綁定在UserIdentity.php 的 demo 與 admin 帳號密碼: public function authenticate() { $users=array( &nbs
- github做webhooks:[2]php版本自动触发更新
dcj3sjt126com
githubgitwebhooks
上次已经说过了如何在github控制面板做查看url的返回信息了。这次就到了直接贴钩子代码的时候了。
工具/原料
git
github
方法/步骤
在github的setting里面的webhooks里把我们的url地址填进去。
钩子更新的代码如下: error_reportin
- Eos开发常用表达式
蕃薯耀
Eos开发Eos入门Eos开发常用表达式
Eos开发常用表达式
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
蕃薯耀 2014年8月18日 15:03:35 星期一
&
- SpringSecurity3.X--SpEL 表达式
hanqunfeng
SpringSecurity
使用 Spring 表达式语言配置访问控制,要实现这一功能的直接方式是在<http>配置元素上添加 use-expressions 属性:
<http auto-config="true" use-expressions="true">
这样就会在投票器中自动增加一个投票器:org.springframework
- Redis vs Memcache
IXHONG
redis
1. Redis中,并不是所有的数据都一直存储在内存中的,这是和Memcached相比一个最大的区别。
2. Redis不仅仅支持简单的k/v类型的数据,同时还提供list,set,hash等数据结构的存储。
3. Redis支持数据的备份,即master-slave模式的数据备份。
4. Redis支持数据的持久化,可以将内存中的数据保持在磁盘中,重启的时候可以再次加载进行使用。
Red
- Python - 装饰器使用过程中的误区解读
kvhur
JavaScriptjqueryhtml5css
大家都知道装饰器是一个很著名的设计模式,经常被用于AOP(面向切面编程)的场景,较为经典的有插入日志,性能测试,事务处理,Web权限校验, Cache等。
原文链接:http://www.gbtags.com/gb/share/5563.htm
Python语言本身提供了装饰器语法(@),典型的装饰器实现如下:
@function_wrapper
de
- 架构师之mybatis-----update 带case when 针对多种情况更新
nannan408
case when
1.前言.
如题.
2. 代码.
<update id="batchUpdate" parameterType="java.util.List">
<foreach collection="list" item="list" index=&
- Algorithm算法视频教程
栏目记者
Algorithm算法
课程:Algorithm算法视频教程
百度网盘下载地址: http://pan.baidu.com/s/1qWFjjQW 密码: 2mji
程序写的好不好,还得看算法屌不屌!Algorithm算法博大精深。
一、课程内容:
课时1、算法的基本概念 + Sequential search
课时2、Binary search
课时3、Hash table
课时4、Algor
- C语言算法之冒泡排序
qiufeihu
c算法
任意输入10个数字由小到大进行排序。
代码:
#include <stdio.h>
int main()
{
int i,j,t,a[11]; /*定义变量及数组为基本类型*/
for(i = 1;i < 11;i++){
scanf("%d",&a[i]); /*从键盘中输入10个数*/
}
for
- JSP异常处理
wyzuomumu
Webjsp
1.在可能发生异常的网页中通过指令将HTTP请求转发给另一个专门处理异常的网页中:
<%@ page errorPage="errors.jsp"%>
2.在处理异常的网页中做如下声明:
errors.jsp:
<%@ page isErrorPage="true"%>,这样设置完后就可以在网页中直接访问exc