文件上传绕过upload-labs-master通关 1-5
第一关:
上传2.php一句话木马
查看源码
此时,也是不可以抓包的。。。
怎么办?
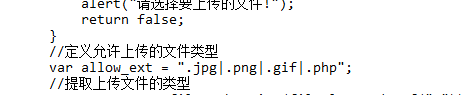
可以尝试在服务器向浏览器发回包时,在浏览器收到回包之前修改其允许上传的文件类型,此时页面的源代码中会允许上传.php文件(前端绕过)
打开Burp,开启拦截功能
刷新浏览器页面
Do intercept 用于显示和修改HTTP请求和响应,通过你的浏览器和Web服务器之间。在BurpProxy的选项中,可以配置拦截规则来确定请求是什么和响应被拦截。
允许上传的文件类型添加.php
查看网页源码,.php增加成功
上传2.php成功
菜刀连接成功
第二关
将一句话木马2.png上传,并开启抓包
修改后缀为.php
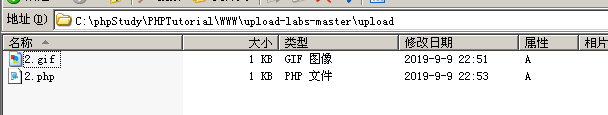
查看目标机upload下的文件,发现上传了.gif 和.php文件
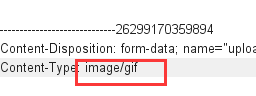
修改Type为任意一种接收的类型
第三关
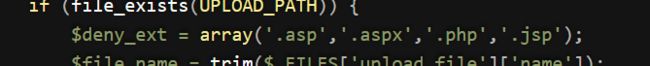
查看源码,拒绝上传以.asp .aspx .php .jsp为后缀的文件
尝试修改大小写 .pHp
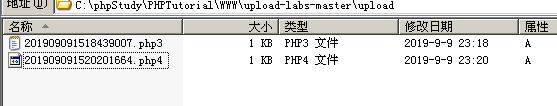
将文件后缀名改为php3或php4试试,发现上传成功
目标主机
第四关
查看源码,过分了噢,拒绝了第三关的办法。
![]()
$deny_ext = array(".php",".php5",".php4",".php3",".php2","php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2","pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf");
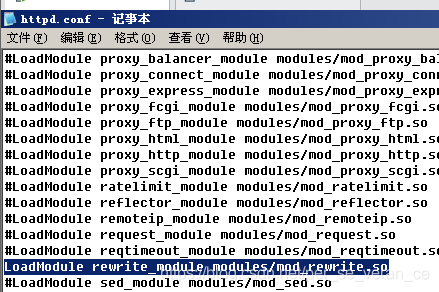
但是,没有过滤.htaccess 文件,可以在.htaccess文件里写入SetHandler application/x-httpd-php,使上传的文件以.php解析
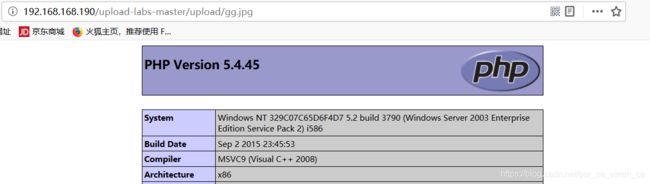
再上传gg.jpg,写入
访问gg.jpg
第五关
查看源码
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
这次,连.htaccess也过滤了,怎么办呢?
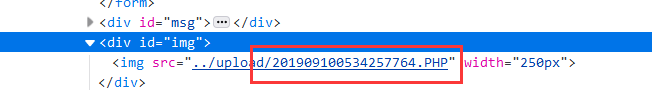
But,可以通过修改php的大小写绕过,文件名改为1.PHP
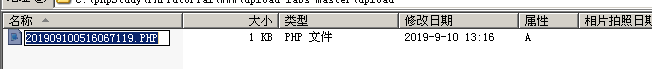
上传成功
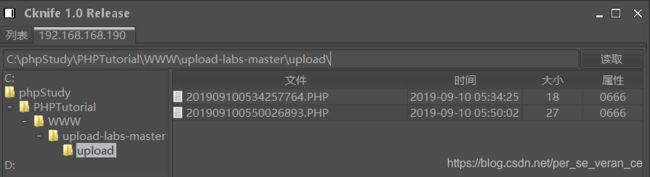
查看目标主机里的文件1.PHP文件,发现文件名被修改
可是,在实际情况下怎么知道文件名被修改为社么?
菜刀连接一句话木马也可以成功