iptables 学习总结--匹配条件(四)
1.指定多个源地址(多个IP之间用,隔开)
iptables -t filter -A INPUT -s 192.168.1.111,192.168.1.110 -j ACCEPT查看结果
[root@localhost ~]# iptables -t filter -vnxL INPUT
Chain INPUT (policy ACCEPT 57 packets, 3972 bytes)
pkts bytes target prot opt in out source destination
6004 504336 ACCEPT all -- * * 192.168.1.39 0.0.0.0/0
0 0 ACCEPT all -- * * 192.168.1.39 0.0.0.0/0
0 0 ACCEPT all -- * * 192.168.1.111 0.0.0.0/0
0 0 ACCEPT all -- * * 192.168.1.110 0.0.0.0/0指定某个网段
iptables -t filter -F INPUT
iptables -t filter -I INPUT -s 10.39.0.0/16 -j DROP查看结果
[root@localhost ~]# iptables -t filter -vnxL INPUT
Chain INPUT (policy ACCEPT 37 packets, 2820 bytes)
pkts bytes target prot opt in out source destination
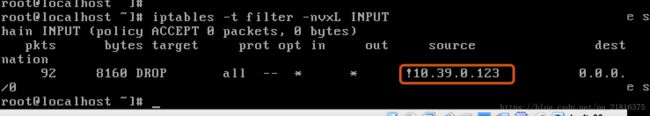
0 0 DROP all -- * * 10.39.0.0/16 0.0.0.0/0非(!)
iptables -t filter -F
iptables -t filter -A INPUT ! -s 10.39.0.123 -j DROP
匹配目标地址
丢掉从192.168.1.39 发往192.168.1.61的报文
iptables -t filter -F
iptables -t filter -A INPUT -s 192.168.1.39 -d 192.168.1.61 -j DROP[root@localhost ~]# iptables -t filter -nvL INPUT
Chain INPUT (policy ACCEPT 108 packets, 7632 bytes)
pkts bytes target prot opt in out source destination
67 5628 DROP all -- * * 192.168.1.39 192.168.1.61不指定源地址
[root@localhost ~]# iptables -t filter -R INPUT 1 -d 192.168.1.61 -j DROP匹配协议类型-p tcp(dup,icmp)
root@localhost ~]# iptables -t filter -I INPUT -s 192.168.1.39 -d 192.168.1.61 -p udp -j DROP
[root@localhost ~]# iptables -t filter -nxvL INPUT --line
Chain INPUT (policy ACCEPT 20 packets, 1560 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 DROP udp -- * * 192.168.1.39 192.168.1.61匹配网卡-i(-o) interface
iptables -t filter -A INPUT -i enp0s8 -s 192.168.1.34 -j ACCEPT[root@localhost ~]# iptables -t filter -A INPUT -i enp0s8 -s 192.168.1.34 -j ACCEPT
[root@localhost ~]# iptables -t filter -nxvL INPUT --line
Chain INPUT (policy ACCEPT 13 packets, 972 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 ACCEPT all -- enp0s8 * 192.168.1.34 0.0.0.0/0扩展匹配条件
匹配端口--dport port(--sport port) -m 表示模块
[root@localhost ~]# iptables -t filter -A INPUT -s 192.168.1.39 -p tcp -m tcp --dport 22 -d 192.168.1.61 -j REJECT
[root@localhost ~]# iptables -t filter -nvL INPUT
Chain INPUT (policy ACCEPT 87 packets, 6492 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT tcp -- * * 192.168.1.39 192.168.1.61 tcp dpt:22 reject-with icmp-port-unreachable结果
[root@fabric-cli ~]# ssh 192.168.1.61
ssh: connect to host 192.168.1.61 port 22: Connection refusedroot@localhost ~]# iptables -t filter -nvL INPUT
Chain INPUT (policy ACCEPT 7 packets, 488 bytes)
pkts bytes target prot opt in out source destination
1 60 REJECT tcp -- * * 192.168.1.39 192.168.1.61 tcp dpt:22 reject-with icmp-port-unreachable
0 0 ACCEPT tcp -- * * 192.168.1.39 192.168.1.61 tcp spt:22匹配连续的某个范围的端口
iptables -t filter -A INPUT -s 192.168.1.61 -d 192.168.1.39 -p tcp --dport 22:25 -j ACCEPT
[root@localhost ~]# iptables -t filter -nvL INPUT
Chain INPUT (policy ACCEPT 89 packets, 7158 bytes)
pkts bytes target prot opt in out source destination
2 120 REJECT tcp -- * * 192.168.1.39 192.168.1.61 tcp dpt:22 reject-with icmp-port-unreachable
0 0 ACCEPT tcp -- * * 192.168.1.39 192.168.1.61 tcp spt:22
0 0 ACCEPT tcp -- * * 192.168.1.61 192.168.1.39 tcp dpts:22:25匹配离散的多个端口(-m multiport --dports)
iptables -t filter -A INPUT -s 192.168.1.111 -p tcp -m multiport --dports 49,36,80 -j ACCEPT[root@localhost ~]# iptables -t filter -nvL INPUT
Chain INPUT (policy ACCEPT 9 packets, 636 bytes)
pkts bytes target prot opt in out source destination
2 120 REJECT tcp -- * * 192.168.1.39 192.168.1.61 tcp dpt:22 reject-with icmp-port-unreachable
0 0 ACCEPT tcp -- * * 192.168.1.39 192.168.1.61 tcp spt:22
0 0 ACCEPT tcp -- * * 192.168.1.61 192.168.1.39 tcp dpts:22:25
0 0 ACCEPT tcp -- * * 192.168.1.111 0.0.0.0/0 multiport dports 49,36,80iprange扩展模块(--src-range,--dst--range)
[root@localhost ~]# iptables -t filter -F INPUT
iptables -t filter -I INPUT -m iprange --src-range 192.168.1.1-192.168.1.34 -j ACCEPT
[root@localhost ~]# iptables -t filter -nvL INPUT
Chain INPUT (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
15 1080 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.1.1-192.168.1.34string 模块(-m string --algo bm(kmp) --string "CICD")
含有HEllO WORLD的报文就会拒绝
iptables -t filter -I INPUT -m string --algo bm --string "HEllO WORLD" -j REJECT
[root@localhost ~]# iptables -t filter -nvxL INPUT
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "HEllO WORLD" ALGO name bm TO 65535 reject-with icmp-port-unreachable
56 4411 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.1.1-192.168.1.34time 模块(-m time --timestart 09:00:00 --timestop 18:00:00)
[root@localhost ~]# iptables -t filter -I OUTPUT -p tcp --dport 80 -m time --timestart 09:00:00 --timestop 18:00:00 -j REJECT
[root@localhost ~]# iptables -t filter -nvxL INPUT
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match "HEllO WORLD" ALGO name bm TO 65535 reject-with icmp-port-unreachable
285 20569 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 source IP range 192.168.1.1-192.168.1.34
[root@localhost ~]# iptables -t filter -nvxL OUTPUT
Chain OUTPUT (policy ACCEPT 19 packets, 2600 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 TIME from 09:00:00 to 18:00:00 UTC reject-with icmp-port-unreachable[root@localhost ~]# iptables -t filter -I OUTPUT -p tcp --dport 80 -m time --weekdays 6,7 -j REJECT[root@localhost ~]# iptables -t filter -I OUTPUT -p tcp --dport 80 -m time --monthdays 6,7 -j REJECT[root@localhost ~]# iptables -t filter -I OUTPUT -p tcp --dport 80 -m time --datestart 2018-12-24 --datestop 2018-12-28 -j REJECTconnlimit模块--connlimit-above
[root@localhost ~]# iptables -t filter -I INPUT -p tcp --dport 80 -m connlimit --connlimit-above 2 -j REJECT
[root@localhost ~]# iptables -t filter -nvxL INPUT
Chain INPUT (policy ACCEPT 19 packets, 1376 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 #conn src/32 > 2 reject-with icmp-port-unreachableroot@localhost ~]# iptables -t filter -I INPUT -p tcp --dport 80 -m connlimit ! --connlimit-above 2 -j REJECT
[root@localhost ~]# iptables -t filter -nvxL INPUT
Chain INPUT (policy ACCEPT 7 packets, 488 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 #conn src/32 <= 2 reject-with icmp-port-unreachable
0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 #conn src/32 > 2 reject-with icmp-port-unreachable[root@localhost ~]# iptables -t filter -I INPUT -p tcp --dport 80 -m connlimit ! --connlimit-above 2 --connlimit-mask 27 -j REJECT[root@localhost ~]# iptables -t filter -nvxL INPUT
Chain INPUT (policy ACCEPT 14 packets, 1357 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 #conn src/27 <= 2 reject-with icmp-port-unreachable
0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 #conn src/32 <= 2 reject-with icmp-port-unreachable
0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 #conn src/32 > 2 reject-with icmp-port-unreachablelimit扩展模块(–limit-brust)
限制每秒流入的包的数量
[root@localhost ~]# iptables -t filter -I INPUT -p icmp -m limit --limit 10/minute -j ACCEPT
[root@localhost ~]# iptables -t filter -nvxL INPUT
Chain INPUT (policy ACCEPT 9 packets, 636 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/min burst 5tcp 扩展模块 –tcp-flags
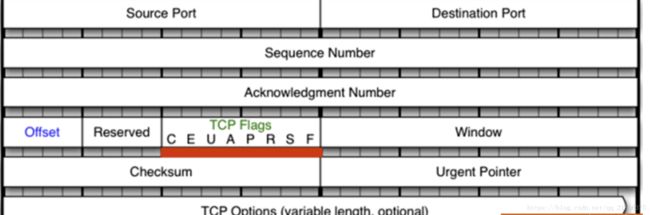
匹配tcp第一次握手的报文
[root@localhost ~]# iptables -t filter -I INPUT -p tcp -m tcp --dport 22 --tcp-flags SYN,ACK,FIN,RST,URG,PSH SYN -j REJECT
[root@localhost ~]# iptables -t filter -nvxL INPUT
Chain INPUT (policy ACCEPT 10 packets, 712 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 flags:0x3F/0x02 reject-with icmp-port-unreachable
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/min burst 5–tcp-flags SYN,ACK,FIN,RST,URG,PSH SYN 这个的意思是要匹配SYN,ACK,FIN,RST,URG,PSH这五个标志为,且SYN为1的报文
匹配tcp第二次握手的报文
[root@localhost ~]# iptables -t filter -I INPUT -p tcp -m tcp --dport 22 --tcp-flags SYN,ACK,FIN,RST,URG,PSH SYN,ACK -j REJECT上述可以简写成
用ALL来表示SYN,ACK,FIN,RST,URG,PSH
[root@localhost ~]# iptables -t filter -I INPUT -p tcp -m tcp --dport 22 --tcp-flags ALL SYN-j REJECT
[root@localhost ~]# iptables -t filter -I INPUT -p tcp -m tcp --dport 22 --tcp-flags ALL SYN,ACK -j REJECT匹配tcp新建请求链接的报文
iptables -t filter -I INPUT -p tcp -m tcp --dport 22 --syn -j REJECT参考
匹配条件
iprange