vshield manager的一些笔记
开始装vshield manager 看了好多材料,发觉确实没有麻烦的安装方法,仅有最简单的安装 哈哈,就是下载ova文件然后通过vsphere client安装。
vshield manager 需要到vmware的官网注册后才能安装,在下载产品中找到VMware vCloud Networking and Security,仔细的找 一定能找到“下载试用”
然后首先还需要为下载的软件先注册一下,这样会得到一个许可码,保存好啊,不过丢了也没关系,再次来到这个界面还会看到许可码,下载ova文件后
使用 vSphere Client 登录到 vCenter Server。
2 选择文件 > 部署 OVF 模板。
3 浏览到 vShield Manager.ovf 文件的位置,并按照提示部署 OVF 文件。
4 部署 OVF 文件之后,启动 vShield Manager 虚拟机并打开控制台。
5 使用用户名 admin 和密码 default 登录到控制台。
6 在 manager 提示中,键入 enable。
7 在 Password 提示中,键入 default 以启用设置模式。
设置模式启用之后,提示字符串将更改为 manager#。
8 在 manager# 提示中,键入 setup,以开始设置过程。
9 输入 vShield Manager 虚拟机的 IP 地址、子网掩码和默认网关。
需要此信息将 vCenter Server 附加到 Cloud Director。
10 键入 exit 以注销。
11 关闭控制台并让虚拟机运行。
12 然后,用浏览器打开vShield Manager这台虚拟机,输入它的IP地址,例如:https://xx.xx.xx.xx,然后缺省用户名admin和缺省密码default:
13 下图所示就是这个vShield Manager的管理界面,这个界面在vShield Manager注册到vCenter之后将会直接在vCenter调出:
• 首先配置vShield Manager注册到vCenter Server;
• 在Settings and Reports > Configuration > Edit,输入相关的信息;
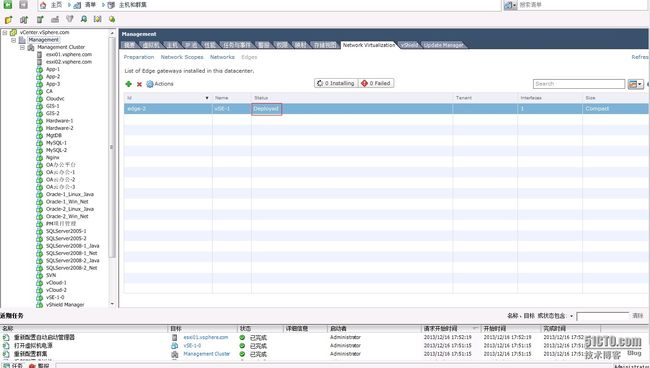
14 完成上述动作之后,在vSphere Client登录vCenter Server之后,即可看到vShield啦,如下图所示:
![]()
15 在License选项里,输入vCloud Networking and Security的LIcense,以便能够继续使用(别找猫猫要License):
在我的百度云里有非常好用的key哦
----------------------------------------------------------------------------------------------------------------------------------------------------------
vshield edge 的配置
-
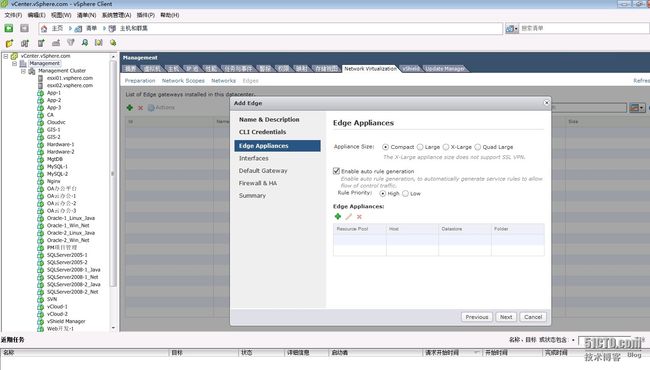
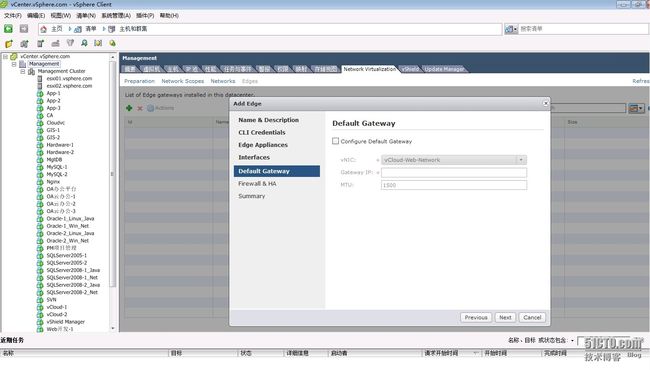
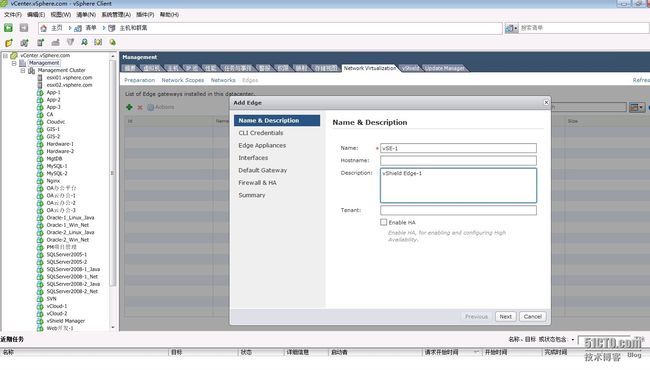
在网络虚拟化的选项框选择edge,打开 Add Edge 向导来安装和配置 vShield Edge 实例

vShield Edge 需要一个在单个租户中的所有vShield Edge 虚拟机中都唯一的描述名称。该名称会显示在vCenter 清单中。名字可以随便方便辨认出是edge即可,会在虚拟机的列中多出一个虚拟机。
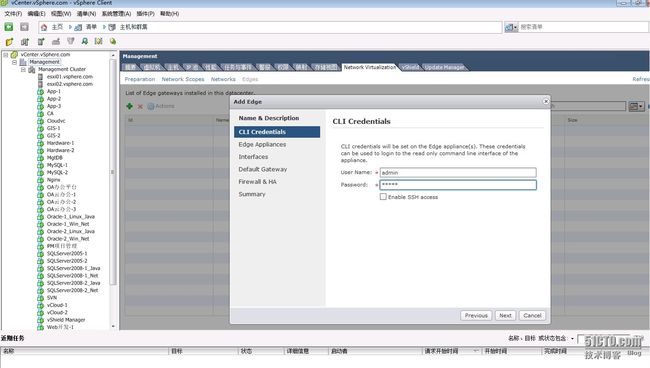
编辑用于登录命令行界面 (CLI) 的凭据,密码要求大写,小写,数字, 特俗字符都要有
您必须先添加设备,然后才可部署 vShield Edge。如果在安装 vShield Edge 时不添加设备,则 vShield Edge会保持脱机模式,直到您添加设备。
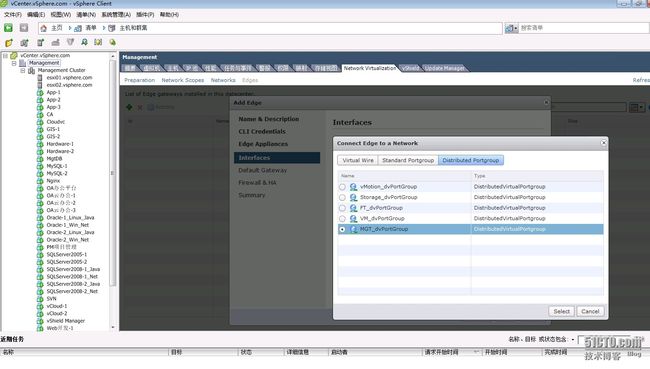
您可以将多达十个内部和上行链路接口添加到 vShield Edge 虚拟机
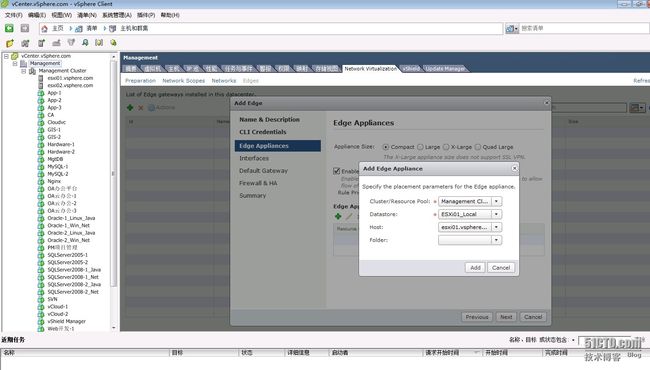
需要

添加上行链路接口,我的实验环境是
外部有个路由器外网ip为113.0.42.*,内网ip为172.17.201.254,其中172.17.201.*为虚拟化的管理段,此段包括vcenter等ip,ad的ip等,虚拟机的运行网段为10.23.0.0 255.255.252.0 现在我想用edge的来连接到10.23.0.0 255.255.252.0的网络段来连接这个段的虚拟机
现在建立edge的上行网络口,需要和外部路由器的内网口一个网段,(外网ip地址没有了啊 要不就不那么麻烦了 直接在这个上行对口设置外网ip 多easy啊 哈哈)
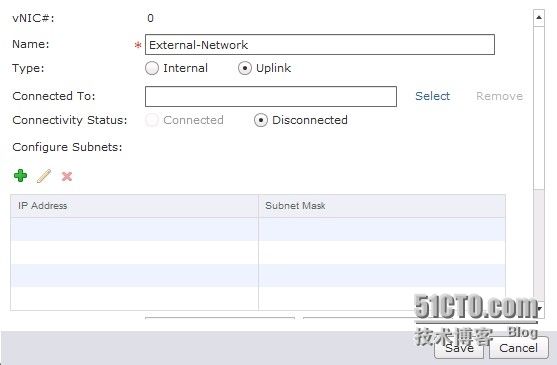
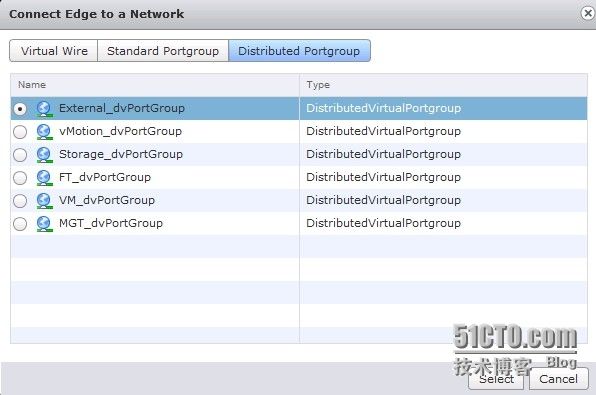
下面不是选择external 而是选择mgt即管理网络的ip段
ip地址设置为172.17.201.250
添加内部接口
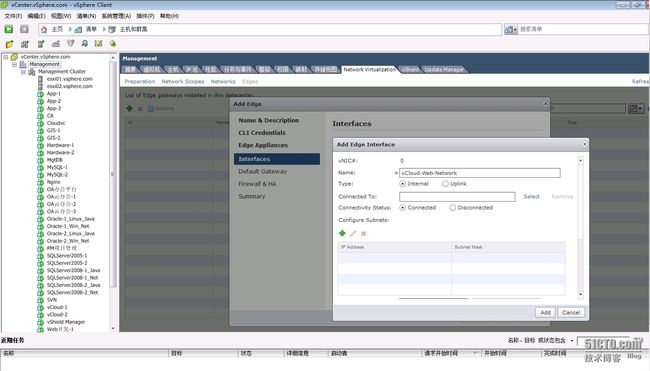
选择端口组为生产网络
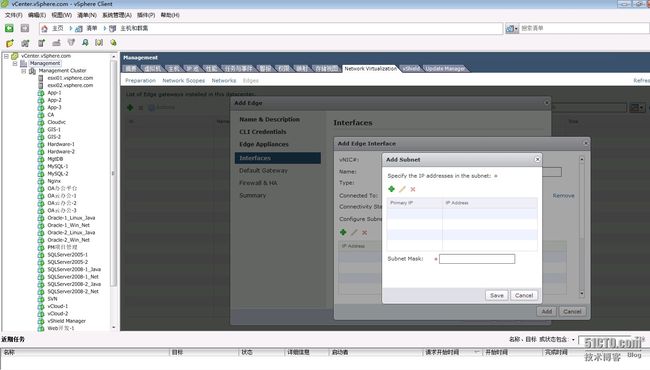
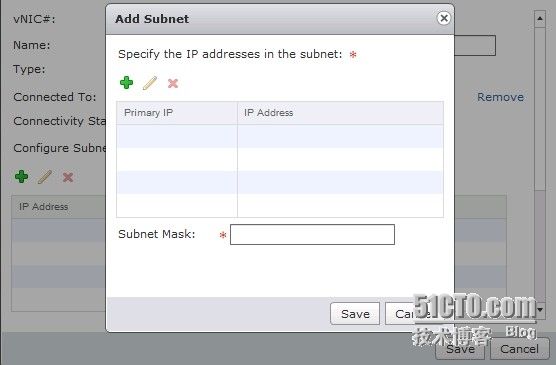
IP地址为10.23.0.223
为 vShield Edge 默认网关提供 IP 地址
网管为172.17.201.254为路由器的内网接口
默认防火墙策略会阻止所有入站流量,您可以对其进行更改
vShield Edge接口情况
选择选项卡
会出现ipsec 和ssl-的选项
下边我们仅对ssl-做描述
Then click on the SSL VPN-Plus menu item.
这里我们不能让其开启enable ,因为我们还没配置,开启会报错
From this dashboard you can see the operational state of the SSL VPN subsystem. Enable SSL VPN service in Edge Gateway when disabled.
Configuration Preparation
To configure the SSL VPN function we will need a number of different parameters and options to be prepared.
- Edge External IP Address: The outside IP address of the Edge Gateway.
- Edge External TCP Port: The default is 443, but this can be changed to any TCP port to suit business requirements.
- Encryption Cipher: The default is AES256-SHA, multiple ciphers preferential ordering can be used.
- SSL Digital Certificate: An SSL certificate can be specified or the default self signed certificate can be used.
- VPN IP Network: You add this as an IP Pool in SSL VPN configuration. The remote user is assigned a virtual IP address from this pool.
- VPN IP Network Gateway: The IP address that acts as an Edge Gateway virtual interface between the VPN IP Network and the corporate IP Networks.
- Corporate IP Networks: List of networks behind Edge Gateway that you want the remote user to be able to access.
- Authentication System: The SSL VPN function supports authenticating with RADIUS, Active Directory, LDAP, RSA-ACE or Local sources. Multiples sources can be selected.
Let’s configure the Edge SSL VPN function using the above parameters.
Server Settings
The first configuration item is the IP address and port number for SSL VPN traffic to the Edge Gateway. The IP address possibly is different from the default external address, if you have multiple overlay IP address networks on the external interface. The TCP port number by default is 443 (that is used by default for HTTPS/SSL traffic). It is feasible to use any TCP port number for communications and for a proof point I have configured this scenario to use TCP 8443.
这里我们用8443口,默认为443口。加密选择256-SHA
The second configuration item is to choose which encryption algorithms to use. You can choose one or multiple to support, bear in mind the security risks involved with each algorithm. The choices are AES256-SHA, AES128-SHA, DES-CBC3-SHA and RC4-MD5.
The third item is your identity certificate. There are a variety of ways to utilise certificates within the Edge Gateway. You can choose to use the default self signed certificate that is generated for each individual Edge Gateway, or to use a previously imported externally generated digital certificate for an individual Edge or one that has been imported into the vShield Manager. See the section Working with Certificates on page 67 of the vShield Admin Guide http://www.vmware.com/pdf/vshield_51_admin.pdf
IP Pool
此处配置客户端拨号后获得的ip段,随便设置。
Next we need to create a pool of IP addresses that are distributed to the connecting VPN clients. This is a new virtual IP address subnet configured on the Edge Gateway. This address range must be different from all other networks configured on the Edge. The IP Pool also contains gateway, DNS server and DNS suffix details.
The Gateway address configured here can be any address, within the subnet range, that is not utilised by the IP Pool. This address is given to virtual interface within the Edge Gateway on creation of the IP Pool.
Multiple IP address pools can be created and used. At this point in time the Edge Gateway only supports 25 simultaneous client VPN tunnels in Compact version and 100 simultaneous client VPN tunnels in Large version. So keep this in mind when deciding how large to make the pool.
If multiple address pools are used with different gateway addresses for each pool. Each gateway address is assigned to the same interface within the Edge Gateway.
Private Networks
The private networks is a list of all reachable IP networks behind Edge Gateway that you wish to encrypt traffic for, or exclude from encrypting, from a VPN client. Each network you wish to tunnel traffic for will require a separate entry. You can use a route summarisation strategy to limit the number of entries.
For each private network you can specify whether you want to enable TCP optimization, this is a unique method of enhancing the performance of TCP packets within the VPN tunnel by removing the original TCP header and only shipping the data. This does not improve performance of UDP traffic.
私网段落设置的iP段应该10.23.0.0 255.255.252.0 这个段,因为我们要让客户端后来访问这一段的网络,network框填写的是10.23.0.0 不是一个ip地址啊
Type the port numbers that you want to open for the remote user to access the internal servers like 3389 for RDP, 20/21 for FTP, and 80 for http. If you want to give unrestricted access to the user, you can leave the Ports field blank.
Authentication
We need to configure an appropriate mechanism to authenticate users for VPN access. The Edge Gateway supports a number of industry standards for external authentication of users, as well a local username database. The choice of which authentication system to use is generally be decided by your corporate IT security policy. The choices for external authentication are RADIUS, LDAP, Active Directory and RSA-ACE. Each authentication option has its own individual configuration parameters.
认证:有好多种,如果我们radius服务器的话就选radius认证,这里我们选择local,即本地认证,设个选项会用到我们下边设置的users配置后的用户名和密码,
Multiple authentication systems can be configured and a hierarchical ordering system can be instituted to cycle automatically through the list.
Remember that there may be specific attributes that need to be configured on the authentication servers to allow user or group access.
Installation Package
In this section we can specify the behaviour of the VPN Client after installation. We also select what VPN client package we want to build for the OS’s we want to support.
installations package 即安装包,客户端的 client是通过访问https://172.17.201.250:8443 用户名和密码是在users中配置的
登陆有下载的client客户端就是在installations package中设置现在的。
我们在外部路由器上做了nat端口映射ip nat inside source static tcp 172.17.201.250 8443 113.0.42.* 8443 extendable
因为我们的edge的上行端口为私网iP地址172.17.201.250,不能再internet上访问,通过用外部路由器做端口映射我们在internet上访问https://113.0.42.*:8443就相当于访问https://172.17.201.250:8443 ,
我们在installation package做的客户端也是这个道理 我们如果做成iP地址172.17.201.250,在因特网上市不能识别出这个ip的,所以我们gateway栏中输入113.0.42.* 端口用8443 ,这样做出的客户端就是连接113.0.42.* 8443了,同样会映射到172.17.201.250上。ok了
Multiple client packages can be produced, each with different parameters. Each client package produced is directly accessible for download from the Edge Gateway VPN portal.
Users
This section is where you can configure local users for authentication. By putting a user in this section, it automatically configures a local user authentication mechanism in the Authentication menu.
这里需要添加用户啊,即是网页登陆https://113.0.42.*:8443的用户名 也是客户端登陆的用户名
Web Resource
The Web Resource function is to provide a secure portal to access web content behind the Edge Firewall. When you open a web connection from the Internet on the port defined in the server settings (i.e. 8443 in our example), you are prompted with a sign-on page to the access portal. It is through this access portal that you first download the SSL-VPN client, but this page can also be used to access other resources defined below.
这个需要设置 开启后允许在web上下载客户端
Use the + button to add a URL that will be presented after login to the portal. This feature could be used to interact with selected corporate web resources. One note though is the HTTPMethod, depending on whether the remote user wants to read from or write to the web resource select either a GET or PUT method for each resource created.
In general you will leave the HTTPQuery section blank, unless you want to send a specific HTTP request to a web resource.
The final result is a login page that lists available resources like this.
其他的可以不设置了 谢谢
Client Configuration
The Client Configuration section is where we specify operating attributes for the SSL VPN client. The three options that can be configured are, Tunneling mode, Auto reconnect and Upgrade client notification.
Tunneling mode – Split tunnel versus Full Tunnel. A full tunnel sends all traffic to the SSL gateway including all Internet traffic. Split tunnel, only sends traffic to networks defined in the Private Networks configuration section. When you select full tunnel you can also choose to exclude locally attached subnets, i.e. home networks, this allows for a “tunnel everything” except my home network scenario, to allow access to things like home printers etc.
Auto reconnect – This changes the operating behaviour of the VPN client should the tunnel be disconnected during a session, i.e. mobile data/ DSL connection dropped, Edge transitioning through a HA scenario etc. Auto reconnect will continue to poll the Edge Gateway and automatically re-establish a connection for you.
Upgrade client notification – When a new version of the SSL VPN client is available, or the system policy for the VPN client configuration is changed, it will prompt you to upgrade the VPN client.
Login/Logoff Scripts
We provide a facility to execute login/logoff scripts that could be used to perform system administration or client usability functions at the time of connection, i.e. start email client, initiate a Horizon View session, or reconnect network drive mappings etc. once VPN is established.
General Settings
The General Settings let you configure a range of global values for the SSL VPN system.
Prevent multiple logon using same username: When enabled allows a remote user to login only once with a username.
Enable compression: Enable TCP based intelligent data compression and improve data transfer speed.
Enable logging: Maintain a log of the traffic passing through the SSL VPN gateway.
Force virtual keyboard: Allows remote users to enter web or client login information only via the virtual keyboard.
Randomize keys of virtual keyboard: Make the virtual keyboard keys random.
Enable forced timeout: Disconnect the remote user after the specified timeout period is over. Type the timeout period in minutes.
Session idle timeout: If there is no activity on the user session for the specified period, end the user session after that period is over.
User notification: Type a message to be displayed to the remote user after he logs in.
Enable public URL access: Allow remote user to access any site, which is not configured (and not listed on web portal) by administrator.
Portal Customization
You can configure the colors, logo and titles for the login portal to reflect your corporate presence.
For the logo you are best served with an image that is a multiple of 70 x 10 pixels i.e. 7 times wider than it is long. We will scale the image pixels to suit the portal, but incorrect initial ratio will result in distorted appearance.
Likewise, we can also change the appearance of the logo in the VPN client. The recommended image size is 390 x 75 pixels. We will scale the image to suit the space, but an incorrect ratio will result in image distortion. This is the last step of the SSL VPN configuration.You can now use the browser to connect to the Edge Gateway SSL VPN service using the IP address and port number configured in Server Settings e.g. https://10.1.1.2:8443. Once authenticated, you can access the web resources configured and download the SSL VPN client installation package.
----------------------------------------------------------------------------------------------------
配置负载平衡器服务
添加vCloud Web服务器池
打开添加池向导,启动添加负载平衡器池的过程
![]()
为负载平衡器池提供描述性名称和可选描述
![]()
您可以选择和配置该池支持的服务,
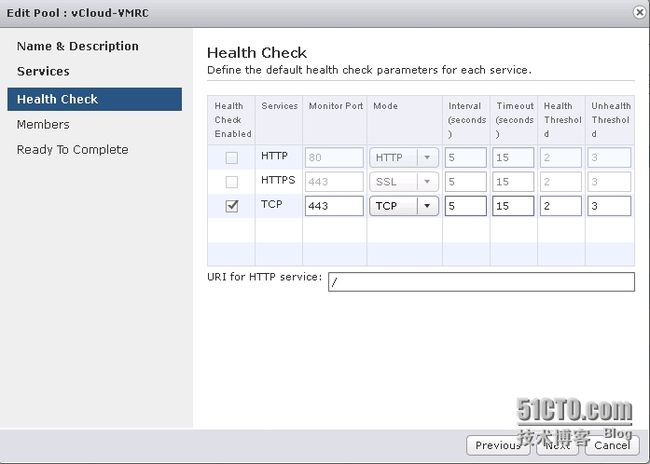
健康状况检查将检查服务器池中的所有服务器是否都处于活动状态并正在应答查询
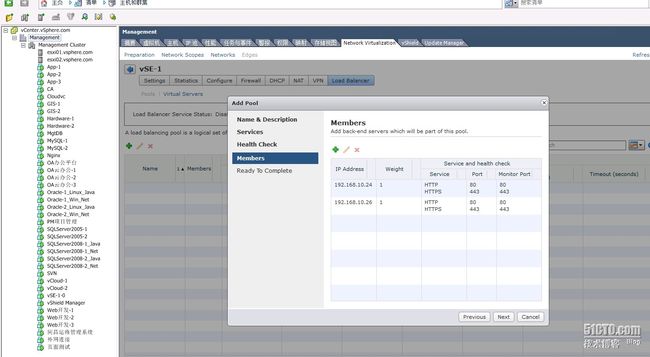
向池中添加后端服务器
![]()
![]()
在添加服务器池之前,请检查您输入的设置
![]()
![]()
添加VMRC服务器池
![]()
![]()
vCloud Director Web和远程控制台代理服务器池完成配置
![]()
添加虚拟服务器
键入虚拟服务器的名称。
(可选)键入虚拟服务器的描述。
键入 vShield Edge 接口的 IP 地址。
选择要与虚拟服务器相关联的池。
此时将显示选定的池所支持的服务。
在服务中,对每个将受到支持的服务单击启用。
根据需要,更改“端口”、“保持方法”、“Cookie 名称”和“Cookie 模式”的默认值。
单击已启用以启用虚拟服务器。
添加vCloud Web虚拟服务器
![]()
添加VMRC虚拟服务器
vCloud Director门户和远程控制台代理的虚拟服务器配置完成
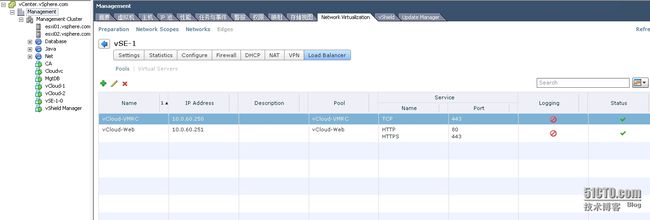
负载均衡启用后的状态
![]()
vShield Edge 防火墙默认规则
![]()
添加相对应的规则
进行测试
vCloud Director服务器组使用vShieldEdge负载均衡配置完毕!
完成上述动作之后,在
vSphere Client
登录
vCenter Server
之后,即可看到
vShield
啦,如下图所示