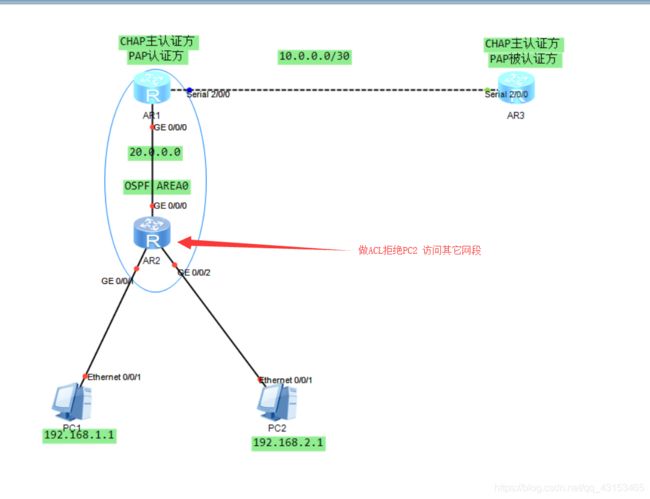
华为PPP pap和chap双向认证配置与抓包与基本ACL配置
PPP认证 加ACL综合实验
文章目录
- PPP认证 加ACL综合实验
- 实验背景
- 实验需求
- 1.配置 PAP和IPCP动态协商
- 2.可以在R1上看到自动获取到的IP地址
- 3.验证PAP和IPCP
- 4.抓包PAP分析
- 5.开始配置CHAP
- 6.验证双向认证通过
- 7.抓包CHAP验证
- 8.配置ospf实现全网通
- 9.查看R2的路由表
- 10.ping 10.0.0.1 测试
- 11.配置ACL
- 12.再次进行ping测试
- 13.总结
- PAP 报文
- **CHAP报文**
- **IPCP报文**
实验背景
实验需求
1.先在R2和R3上配ppp的CHAP和PAP认证,R2为PAP的认证方;CHAP的被认证方。R3为PAP的被认证方;CHAP的认证方。
2.R1的S2/0/0接口IP地址要通过IPCP动态协商获得。
3.抓包分析
4.先用ospf 实现全网通
6.在最合适的端口上用ACL2000拒绝PC2访问其它网段
1.配置 PAP和IPCP动态协商
R2
[R1]AAA
[R1-aaa]LOCAL-USER hst password cipher 123 //配置一个本地用户hst
[R1-aaa]LOCAL-USER HST service-type PPP //这个用户的服务类型为ppp
[R1-aaa]INT S 2/0/0
[R1-Serial2/0/0]link-protocol PPP //在华为S接口默认二层协议是PPP
[R1-Serial2/0/0]IP address ppp-negotiate // IP地址为PPP协议协商获得
[R1-Serial2/0/0]PPP authentication-mode PAP // 端口验证模式为PAP认证
R3
[R3]INT S2/0/0
[R3-Serial2/0/0]IP ADDRESS 10.0.0.2 30
[R3-Serial2/0/0]remote address 10.0.0.1 // 为远程 分配一个IP地址
[R3-Serial2/0/0]ppp pap local-user hst password cipher 123 //在接口上配置一个本地认证用户hst
2.可以在R1上看到自动获取到的IP地址
[R1]DIS IP INT brief
*down: administratively down
^down: standby
(l): loopback
(s): spoofing
The number of interface that is UP in Physical is 2
The number of interface that is DOWN in Physical is 3
The number of interface that is UP in Protocol is 2
The number of interface that is DOWN in Protocol is 3
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 unassigned down down
GigabitEthernet0/0/1 unassigned down down
NULL0 unassigned up up(s)
Serial2/0/0 10.0.0.1/32 up up //可以看到已经自动协商获得的ip
Serial2/0/1 unassigned down down
3.验证PAP和IPCP
R3
[R2-Serial2/0/0]shutdown //在配置发生更改后 一定要重起端口让配置生效
[R2-Serial2/0/0]un shutdown
[R3-Serial2/0/0]PING 10.0.0.1
PING 10.0.0.1: 56 data bytes, press CTRL_C to break
Reply from 10.0.0.1: bytes=56 Sequence=1 ttl=255 time=200 ms
Reply from 10.0.0.1: bytes=56 Sequence=2 ttl=255 time=30 ms
Reply from 10.0.0.1: bytes=56 Sequence=3 ttl=255 time=30 ms
Reply from 10.0.0.1: bytes=56 Sequence=4 ttl=255 time=20 ms
Reply from 10.0.0.1: bytes=56 Sequence=5 ttl=255 time=30 ms
--- 10.0.0.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/62/200 ms
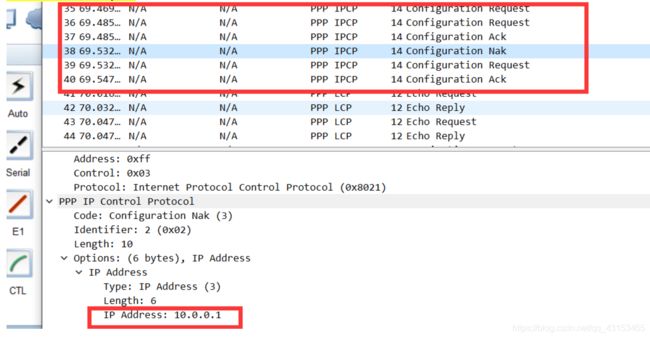
4.抓包PAP分析
可看到PAP认证的明文用户名和密码

可以IPCP 里交互确认的ip地址
5.开始配置CHAP
R3
[R3]aaa
[R3-aaa]local-user sss password cipher 123
[R3-aaa]local-user sss service-type ppp
[R3-aaa]INT S 2/0/0
[R3-Serial2/0/0]PPP authentication-mode CHAP
R1
[R1]int s 2/0/0
[R1-Serial2/0/0]ppp chap user sss
[R1-Serial2/0/0]ppp chap password cipher 123
6.验证双向认证通过
ping 10.0.0.1
PING 10.0.0.1: 56 data bytes, press CTRL_C to break
Reply from 10.0.0.1: bytes=56 Sequence=1 ttl=255 time=110 ms
Reply from 10.0.0.1: bytes=56 Sequence=2 ttl=255 time=20 ms
Reply from 10.0.0.1: bytes=56 Sequence=3 ttl=255 time=30 ms
Reply from 10.0.0.1: bytes=56 Sequence=4 ttl=255 time=20 ms
Reply from 10.0.0.1: bytes=56 Sequence=5 ttl=255 time=20 ms
--- 10.0.0.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/40/110 ms
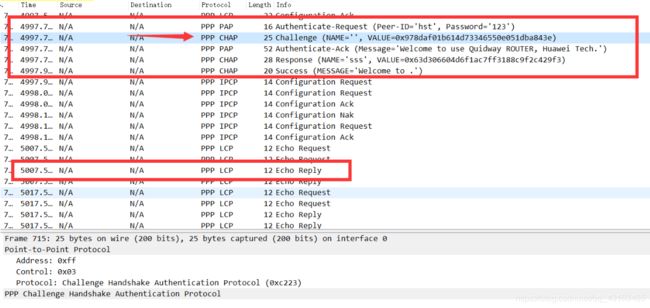
7.抓包CHAP验证
可以看到pap和chap的协议报文一开始的时候CHAP的Challenge 的name是空,需要被认证方回答的 ; 当用这个Echp-reply的报文 时说明已经完成了建立 是检测链路状态的报文
8.配置ospf实现全网通
R1
[R1]OSPF
[R1-ospf-1]AREA 0
[R1-ospf-1-area-0.0.0.0]network 20.0.0.0 0.0.0.255
[R1-ospf-1-area-0.0.0.0]network 10.0.0.0 0.0.0.3
R2
[R2]OSPF
[R2-ospf-1]AREA 0
[R2-ospf-1-area-0.0.0.0]network 192.168.0.0 0.0.255.255
[R2-ospf-1-area-0.0.0.0]network 20.0.0.0 0.0.0.255
9.查看R2的路由表
[R2-GigabitEthernet0/0/0]DIS IP ROUTING
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 14 Routes : 14
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.0.1/32 OSPF 10 49 D 20.0.0.1 GigabitEthernet
0/0/0
20.0.0.0/24 Direct 0 0 D 20.0.0.2 GigabitEthernet
0/0/0
20.0.0.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
20.0.0.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.1.0/24 Direct 0 0 D 192.168.1.254 GigabitEthernet
0/0/1
192.168.1.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
192.168.1.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
192.168.2.0/24 Direct 0 0 D 192.168.2.254 GigabitEthernet
0/0/2
192.168.2.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/2
192.168.2.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/2
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
10.ping 10.0.0.1 测试
PC1
Ping 10.0.0.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
From 10.0.0.1: bytes=32 seq=2 ttl=254 time=15 ms
From 10.0.0.1: bytes=32 seq=3 ttl=254 time=16 ms
From 10.0.0.1: bytes=32 seq=4 ttl=254 time=31 ms
From 10.0.0.1: bytes=32 seq=5 ttl=254 time=16 ms
--- 10.0.0.1 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 0/19/31 ms
PC2
Ping 10.0.0.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
From 10.0.0.1: bytes=32 seq=2 ttl=254 time=16 ms
From 10.0.0.1: bytes=32 seq=3 ttl=254 time=15 ms
From 10.0.0.1: bytes=32 seq=4 ttl=254 time=31 ms
From 10.0.0.1: bytes=32 seq=5 ttl=254 time=16 ms
--- 10.0.0.1 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 0/19/31 ms
11.配置ACL
R2
[R2]ACL 2000 //定义一条ACL
[R2-acl-basic-2000]rule 5 deny source 192.168.2.1 0.0.0.0 //规则5 拒绝 源ip地址 192.168.2.1 的一个主机地址要尽可能精确
[R2-GigabitEthernet0/0/2]traffic-filter inbound acl 2000 // 在数据的入接口方向就拒绝比较好 免得浪费路由器资源
12.再次进行ping测试
PC1
PC>ping 10.0.0.1
Ping 10.0.0.1: 32 data bytes, Press Ctrl_C to break
From 10.0.0.1: bytes=32 seq=1 ttl=254 time=15 ms
From 10.0.0.1: bytes=32 seq=2 ttl=254 time=16 ms
From 10.0.0.1: bytes=32 seq=3 ttl=254 time=31 ms
From 10.0.0.1: bytes=32 seq=4 ttl=254 time=16 ms
From 10.0.0.1: bytes=32 seq=5 ttl=254 time=16 ms
--- 10.0.0.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 15/18/31 ms
PC2
PC>ping 10.0.0.1
Ping 10.0.0.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
Request timeout!
Request timeout!
Request timeout!
--- 10.0.0.1 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
13.总结
1. PAP是被认证方主动发出认证请求,CHAP是认证方主动发出认证请求
2. 配置上都是认证方在配置AAA库里配置用户密码;服务类型;在端口上开启认证模式 ,被认证方在端口上配置用户密码。
3. Echo-ply的报文出现时说明链路已经稳定 正在周期性维护状态。
4. 在数据的入接口方向就拒绝比较好 免得浪费路由器资源。
LCP 当链路断时会发送Terminate-Request;Terminate-Ack这两个报文
LCP 这两个报文Echo-Request Echo-reply 是检测链路状态
PAP 报文
Authenticate-Request(明文发送用户名和密码)
Authenticate-Ack/Authenticate-Nak(认证成功/认证失败)
CHAP报文
Challenge:为挑战包, 发一个空的用户名;ID;随机数
Response:接收到主认证方的challenge报文 知道了 ID和随机数。拿ID;随机数;密码。然后加上本地的密码 MD5加密 在哈希得出哈希值 发个对方一个明文的用户名 和得出来的哈希值
Sucess/Failure:成功或失败
IPCP报文
R1.Configure-Request(0.0.0.0) : 配置请求 我的IP地址是什么?
R2 Configure-Nak(10.1.1.1) :回复一个你的ip地址是10.1.1.1
R1.Configure-Request(10.1.1.1) :确认我的ip地址是10.1.1.1嘛 有没有冲突
R2. Configure-Ack : 没事你用吧 没有冲突
R1.Configure-Request(10.1.1.2) :看看我的地址冲突吗
R1. Configure-Ack: :没事你用吧 没有冲突