基于Openresty进行配置https,配置https后能够对传输的文本进行加密传输(http请求转换为https请求)
一、配置https
1、默认openresty、openssl已经安装完成,我在/usr/local/openresty/nginx/conf/目录下创建一个cert文件夹用来存放证书和服务器私钥(可根据自己情况而定)。
[root@ZYL conf]# pwd
/usr/local/openresty/nginx/conf
[root@ZYL conf]# ls
cert fastcgi_params koi-win nginx.conf nginx.conf-99-9 scgi_params.default win-utf
fastcgi.conf fastcgi_params.default mime.types nginx.conf_198 nginx.conf.default uwsgi_params
fastcgi.conf.default koi-utf
2、进入cert目录下, 创建服务器私钥,命令会提醒输入一个密码
生成4096字节的服务器私钥:openssl genrsa -des3 -out server.key 4096
[root@ZYL cert]# openssl genrsa -des3 -out server.key 4096
Generating RSA private key, 4096 bit long modulus (2 primes)
.......................++++
..................................................................................++++
e is 65537 (0x010001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
3、创建签名请求的证书(CSR)
openssl req -new -key server.key -out server.csr
[root@ZYL cert]# openssl req -new -key server.key -out server.csr
Enter pass phrase for server.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:GUIZHOU
Locality Name (eg, city) []:Duyun
Organization Name (eg, company) [Internet Widgits Pty Ltd]:sy
Organizational Unit Name (eg, section) []:gt
Common Name (e.g. server FQDN or YOUR name) []:www.localhost.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:syf
邮箱地址可不用填,直接回车即可(我是没有填)。
4、在加载SSL支持的Nginx服务器上,使用上述私钥时除去必须的口令(注意,所谓除去,其实就是将必须的私钥密码写入到了私钥文件里面了,更新了原来的私钥文件)
[root@ZYL cert]# cp server.key server.key.org
[root@ZYL cert]# openssl rsa -in server.key.org -out server.key
Enter pass phrase for server.key.org:
writing RSA key
5、通过openssl的x509指令生成证书文件
[root@ZYL cert]# openssl x509 -req -days 3650 -in server.csr -signkey server.key -out server.crt
Signature ok
subject=C = CN, ST = GUIZHOU, L = Duyun, O = shineyue, OU = gt, CN = localhost
Getting Private key
6、配置nginx.conf文件
server {
listen 443 ssl;
server_name localhost;
#ssl on;
ssl_certificate /usr/local/openresty/nginx/conf/cert/server.crt;
ssl_certificate_key /usr/local/openresty/nginx/conf/cert/server.key;
ssl_session_cache shared:SSL:5m;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE;
ssl_prefer_server_ciphers on;
location / {
alias html/;
index index.html index.htm;
try_files $uri $uri/ /index.html;
client_max_body_size 100M;
}
......
}
7、重启nginx,访问https://192.168.60.128
可以看到红色https字样
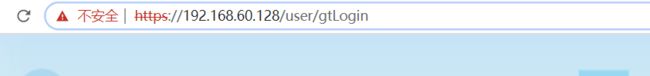
二、对https抓包查看是否进行了加密传输
对http进行抓包:
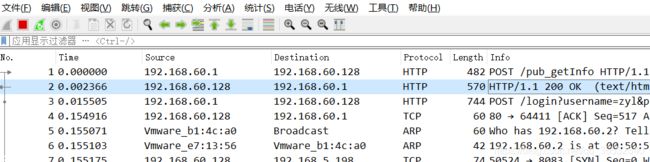
可以看到是HTTP传输,并没有加密。
对https进行抓包:
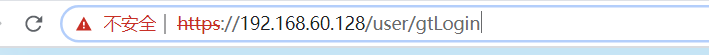
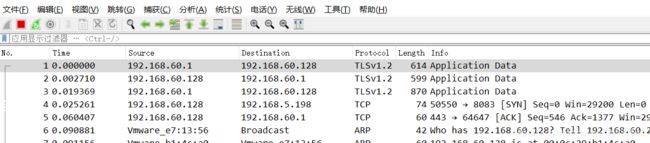
使用了https后传输的文本进行了加密。
三、http请求转换为https请求
把http的域名请求转成https
......
server {
listen 80;
#填写绑定证书的域名
server_name localhost;
#把http的域名请求转成https
rewrite ^(.*)$ https://$host$1 permanent;
}
server {
listen 443 ssl;
server_name localhost;
#ssl on;
ssl_certificate /usr/local/openresty/nginx/conf/cert/server.crt;
ssl_certificate_key /usr/local/openresty/nginx/conf/cert/server.key;
ssl_session_cache shared:SSL:5m;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE;
ssl_prefer_server_ciphers on;
location / {
alias html/;
index index.html index.htm;
try_files $uri $uri/ /index.html;
client_max_body_size 100M;
}
......
}
这样进行i访问时就会自动转为https。