防火墙双机热备命令行配置
文章目录
- 实验要求
- 实验内容
- 步骤一
- 步骤二
- 步骤三
- 步骤四
- 步骤五
- 步骤六
实验要求
- 部署防火墙双机热备,避免防火墙出现单点故障而导致的网络瘫痪
- 进行故障模拟,在双机热备的部署完成之后,关闭主设备,查看业务连通性是否收到影响
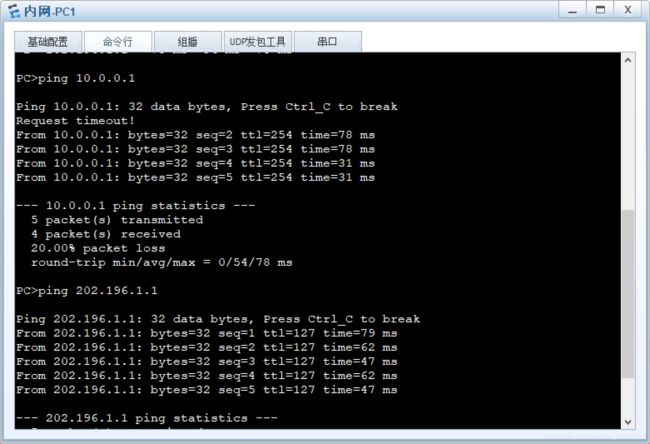
连通性要求:
- 内网用户可以访问外网、服务器
- 外网用户可以访问服务器
实验内容
步骤一
搭建拓扑,规划网段。配置终端和防火墙各个接口IP地址。
FW1:
[USG6000V1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip ad 192.168.1.253 24
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip ad 202.196.1.253 24
[USG6000V1-GigabitEthernet1/0/1]int g1/0/2
[USG6000V1-GigabitEthernet1/0/2]ip ad 10.0.0.253 24
[USG6000V1-GigabitEthernet1/0/2]int g1/0/3
[USG6000V1-GigabitEthernet1/0/3]ip ad 10.0.12.1 24
FW2:
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip ad 192.168.1.252 24
[USG6000V1-GigabitEthernet1/0/1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip ad 10.0.0.252 24
[USG6000V1-GigabitEthernet1/0/0]int g1/0/3
[USG6000V1-GigabitEthernet1/0/3]ip ad 10.0.12.2 24
[USG6000V1-GigabitEthernet1/0/3]int g1/0/2
[USG6000V1-GigabitEthernet1/0/2]ip ad 202.196.1.252 2
步骤二
根据拓扑,将接口划入对应的安全区域。
注意:两个防火墙之间的心跳接口要必须放进信任区域
FW1:
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add interface g1/0/0
[USG6000V1-zone-trust]ad interface g1/0/3
[USG6000V1-zone-trust]q
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]ad in g1/0/1
[USG6000V1-zone-untrust]q
USG6000V1]firewall zone dmz
[USG6000V1-zone-dmz]ad in g1/0/2
FW2:
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]ad in g1/0/3
[USG6000V1-zone-trust]ad in g1/0/1
[USG6000V1-zone-trust]q
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]ad in g1/0/2
[USG6000V1]firewall zone dmz
[USG6000V1-zone-dmz]ad in g1/0/0
步骤三
配置VRRP备份组
主设备:FW1
[USG6000V1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 192.168.1.254 active
[USG6000V1-GigabitEthernet1/0/0]int g1/0/2
[USG6000V1-GigabitEthernet1/0/2]vrrp vrid 2 virtual-ip 10.0.0.254 active
[USG6000V1-GigabitEthernet1/0/2]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]vrrp vrid 3 virtual-ip 202.196.1.254 active
备份设备:FW2
[USG6000V1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]vrrp vrid 2 virtual-ip 10.0.0.254 standby
[USG6000V1-GigabitEthernet1/0/0]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 192.168.1.254 standby
[USG6000V1-GigabitEthernet1/0/1]int g1/0/2
[USG6000V1-GigabitEthernet1/0/2]vrrp vrid 3 virtual-ip 202.196.1.254 standby
我们可以通过display vrrp interface G1/0/3来查看VRRP备份组中的接口状态信息
步骤四
开启HRP协议并配置心跳接口和会话备份功能
FW1:
[USG6000V1]hrp enable //开启HRP功能,开启后提示符出现HRP_M(Master)
HRP_M[USG6000V1]hrp interface g1/0/3 remote 10.0.12.2 //指定心跳口: hrp interface [心跳口] remote [邻居心跳口IP地址]
HRP_M[USG6000V1]hrp mirror session enable //启动会话快速备份
FW2:
[USG6000V1]hrp enable ////开启HRP功能,开启后提示符出现HRP_S(standby)
HRP_S[USG6000V1]hrp interface g1/0/3 remote 10.0.12.1
HRP_S[USG6000V1]hrp mirror session enable
我们可以通过dis hrp state查看HRP状态
步骤五
配置安全策列,是内网用户可以访问服务器和外网用户;外网用户只能访问服务器
注意:只需要配置Master即可,Backup设备不用配置,配置命令会自动从主设备备份到备份设备。
FW1:
HRP_M[USG6000V1]security-policy (+B) //(+B)的意思为配置同时备份到备份设备。
HRP_M[USG6000V1-policy-security]rule name t2ud (+B)
HRP_M[USG6000V1-policy-security-rule-t2ud]source-zone trust (+B)
HRP_M[USG6000V1-policy-security-rule-t2ud]destination-zone untrust dmz (+B)
HRP_M[USG6000V1-policy-security-rule-t2ud]action permit (+B)
HRP_M[USG6000V1-policy-security-rule-t2ud]q
HRP_M[USG6000V1-policy-security]rule name u2d (+B)
HRP_M[USG6000V1-policy-security-rule-u2d]source-zone untrust (+B)
HRP_M[USG6000V1-policy-security-rule-u2d]destination-zone dmz (+B)
HRP_M[USG6000V1-policy-security-rule-u2d]action permit (+B)
验证