k8s 测试七 Ingress
Ingress
官网:
https://kubernetes.github.io/ingress-nginx/deploy/
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/mandatory.yamlkubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/provider/baremetal/service-nodeport.yaml测试:
deployment
apiVersion: apps/v1
kind: Deployment
metadata:
name: myapp-deploy
spec:
replicas: 3
selector:
matchLabels:
app: mynginx
release: nginxapp
template:
metadata:
labels:
app: mynginx
release: nginxapp
env: test
spec:
containers:
- name: nginx
image: nginx
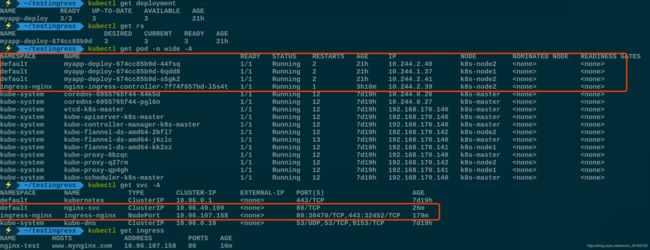
创建了三个 nginx pod 标签为:
- app:mynginx
- release:nginxapp
svc
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
selector:
app: mynginx
ports:
- port: 80
targetPort: 80
protocol: TCP创建了一个Service 代理pod标签为的pod
- app:mynginx
Ingress :
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: nginx-test
spec:
rules:
- host: www.mynginx.com
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80创建了一个ingress 代理 那么为 nginx-svc 的 svc
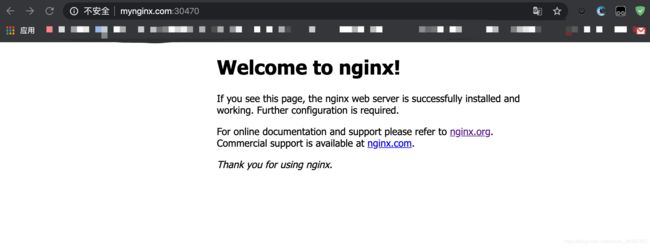
修改本地hosts:
sudo vim /etc/hosts
添加解析:
192.168.170.142 www.mynginx.com
任意节点皆可用但是这里推荐修改为ingress pod所在的节点我这里是node2,这里就将其当作有nginx功能的NodePort使用即可
浏览器访问:
修改为https:
创建证书,以及cert存储方式
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=nginx-svc/O=nginx-svc"
kubectl create secret tls tls-secret --key tls.key --cert tls.crt
ingres yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: nginx-test
spec:
tls:
- hosts:
- www.mynginx.com
secretName: tls-secret
rules:
- host: www.mynginx.com
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
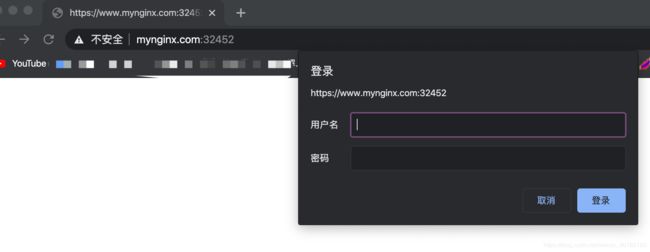
BasicAuth
yum -y install httpd
htpasswd -c auth foo
kubectl create secret generic basic-auth --from-file=auth
yaml:
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: nginx-test
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - foo'
spec:
tls:
- hosts:
- www.mynginx.com
secretName: tls-secret
rules:
- host: www.mynginx.com
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80Nginx 进行重写
nginx.ingress.kubernetes.io/rewrite-target 必须重定向流量的目标URI
nginx.ingress.kubernetes.io/ssl-redirect 指示位置部分是否仅可访问SSL(当Ingress包含证书时默认为True)
nginx.ingress.kubernetes.io/force-ssl-redirect 即使Ingress未启用TLS,也强制重定向到HTTPS
nginx.ingress.kubernetes.io/app-root 定义Controller必须重定向的应用程序根,如果它在'/'上下文中
nginx.ingress.kubernetes.io/use-regex 指示Ingress上定义的路径是否使用正则表达式
前面的例子我们继续使用
yaml:
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: nginx-test1
annotations:
nginx.ingress.kubernetes.io/rewrite-target: https://www.mynginx.com:32452
spec:
tls:
- hosts:
- www1.mynginx.com
secretName: tls-secret
rules:
- host: www1.mynginx.com我们这里继续使用https并且该ingress没有指定其他svc,而是直接跳转到了www.mynginx.com
本地hosts添加:
192.168.170.142 www1.mynginx.com
Ingress实现iphash轮询:
创建资源deployment:
kind: Deployment
apiVersion: apps/v1
metadata:
name: nginx-deployment
spec:
replicas: 3
selector:
matchLabels:
run: nginx-deployment
template:
metadata:
creationTimestamp: null
labels:
run: nginx-deployment
spec:
containers:
- name: nginx-deployment
image: 'wangyanglinux/myapp:v1'
ports:
- containerPort: 80
protocol: TCP
restartPolicy: Always创建资源svc:
kind: Service
apiVersion: v1
metadata:
name: demo-client
spec:
ports:
- name: http
protocol: TCP
port: 80
targetPort: 80
selector:
run: nginx-deployment
type: ClusterIP
sessionAffinity: ClientIP
sessionAffinityConfig:
clientIP:
timeoutSeconds: 10800创建资源svc2:
kind: Service
apiVersion: v1
metadata:
name: demo-client2
spec:
ports:
- name: http
protocol: TCP
port: 80
targetPort: 80
selector:
run: nginx-deployment
type: ClusterIP可以看到svc1和svc2的区别在于
sessionAffinity: ClientIP //
sessionAffinityConfig:
clientIP:
timeoutSeconds: 10800
开启了session保持。下面的timeoutSeconds指的是session保持的时间,这个时间默认是10800秒,也就是三个小时。
当不设置session保持时,service向后台pod转发规则是轮询。当设置了session保持之后,k8s会根据访问的ip来把请求转发给他以前访问过的pod,这样session就保持住了。
之后创建ingress:
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: cxa-mynginxe
spec:
rules:
- host: testmynginx.wellnessshop.cn
http:
paths:
- path: /
backend:
serviceName: demo-client
servicePort: 80但是这里我们发现它的访问规则还是轮训所以这里也要修改ingress配置:
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: cxa-mynginxe
annotations:
nginx.ingress.kubernetes.io/affinity: "cookie"
nginx.ingress.kubernetes.io/session-cookie-name: "route"
ginx.ingress.kubernetes.io/session-cookie-hash: "sha1"
spec:
rules:
- host: testmynginx.wellnessshop.cn
http:
paths:
- path: /
backend:
serviceName: demo-client
servicePort: 80到这里我们就可以做到访问相同pod的目的了