TL-WR886N密码JS加密
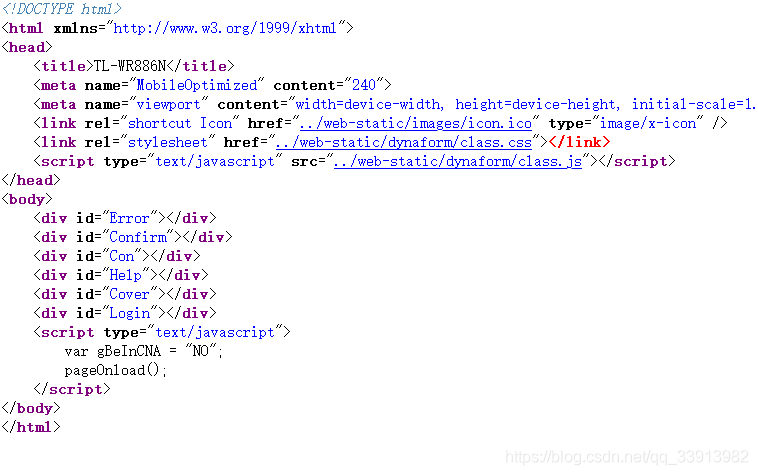
网页源码:
很明显又是JS解压缩了,跟进pageOnload后觉得有点麻烦,我就直接下XHR网址断点了,输入密码提交后直接就在jquery的代码里断下了
h.send(a.hasContent && a.data || null);
//a.data也就是实际发送的Body了
然后通过栈回溯先到Ajax函数
r.send(u, d)到 sendAjaxReq函数
$.ajax(a);再到Auth函数
auth: function (a, b, c) {
$.accountStatus.logoutHandle = !1;
(a == p || 0 == a.length) && b && b(EUNAUTH);
return $.sendAjaxReq('', {
method: 'do',
login: {
password: a
}
}, function (c) {
var d = c[ERR_CODE];
ENONE == d ? ($.session = decodeURIComponent(c.stok), $.setLgPwd(a), $.authRltObj.authStatus = !0) : ($.authRltObj.authStatus = !1, $.parseAuthRlt(c.data));
return b && b(d)
}, c || 'undefined' === typeof c, 'json')
}a也就是加密后的字符串
再回溯就到最后一段解码后的JS代码里了
function h() {
var a = id('lgPwd');
$.auth($.orgAuthPwd(a.value), function (b) {
b == ENONE ? (a.value = '', $.authRltObj.bHandLg = !0, unloadLogin()) : g(parseInt($.authRltObj.code))
})
}a.value也就是原始字符串,通过orgAuthPwd函数后传到auth函数
查找orgAuthPwd,和容易就找到
orgAuthPwd: function (a) {
return $.securityEncode('RDpbLfCPsJZ7fiv', a, 'yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciXTysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgMLwygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3sfQ1xtXcPcf1aT303wAQhv66qzW')
},很明显securityEncode就是加密函数,跟进后是如下代码
securityEncode: function (a, b, c) {
var e = '',
f,
g,
h,
k,
l = 187,
n = 187;
g = a.length;
h = b.length;
k = c.length;
f = g > h ? g : h;
for (var p = 0; p < f; p++) n = l = 187,
p >= g ? n = b.charCodeAt(p) : p >= h ? l = a.charCodeAt(p) : (l = a.charCodeAt(p), n = b.charCodeAt(p)),
e += c.charAt((l ^ n) % k);
return e
},python如下:
def securityEncode(encrypt,data,salt):
eecode = ''
saltLen = len(salt)
dataLen = len(data)
encryptLen = len(encrypt)
maxLenInSaltData = dataLen>sataLen?dataLen:sataLen
for index in 0,maxLenInSaltData:
n=l=187
index >= saltLen ? n = data.charCodeAt(index) : index >= dataLen ? l = encrypt.charCodeAt(index) : (l = encrypt.charCodeAt(index), n = data.charCodeAt(index)),
encode += salt.charAt((l ^ n) % saltLen );
return encode