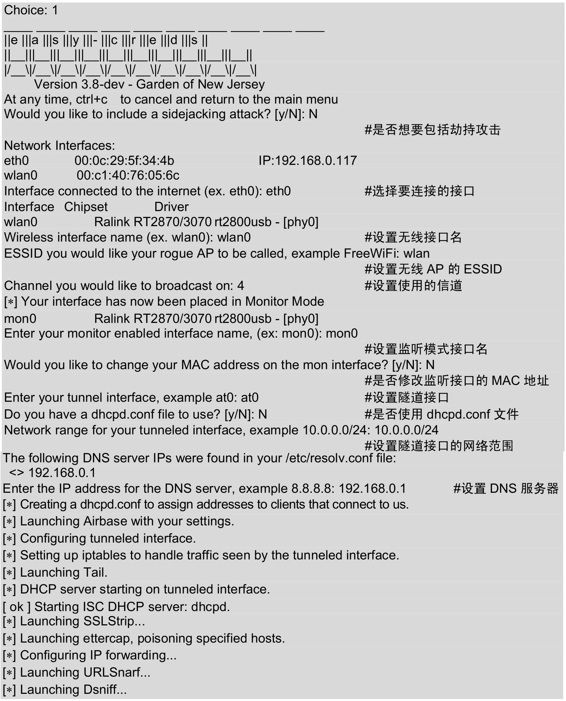
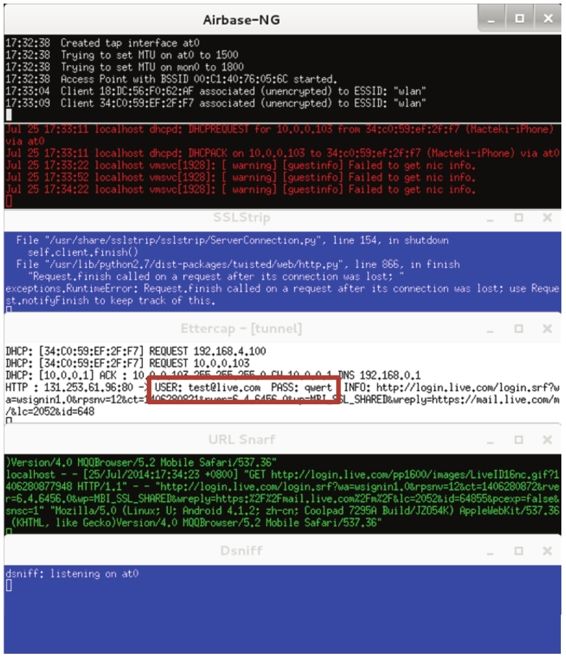
- 使用Python实现音频降噪
在音频处理领域,背景噪声是一个常见的问题。为了提高音频的质量,我们需要对音频进行降噪处理。本文将介绍如何使用Python实现音频降噪。依赖库安装在开始之前,我们需要安装以下依赖库:pydub:用于音频文件的读取和写入。numpy:用于数组和数值计算。noisereduce:用于音频降噪。matplotlib:用于绘制波形图。使用以下命令安装依赖库:pipinstallpydubnumpynoise
- Docker学习之Linux CentOS上安装Docker的完整图文教程
LinuxCentOS上安装Docker的完整图文教程来自Docker官方文档:支持的平台DockerEngine可通过DockerDesktop在各种Linux平台,macOS和Windows10上以静态二进制安装的形式使用。我买了个云服务器,现在想在上面装个Docker,服务器系统是CentOS,所以我选择了CentOS。来自Docker官方文档:要在CentOS上开始使用DockerEngi
- 关于使用FFmpeg进行视频拼接
关于使用FFmpeg进行视频拼接方案使用concatdemuxer使用concat协议更多支持其他方案使用concat滤镜失败其他工具MP4BoxMKVMergeMEncoder额外知识管道h264_mp4toannexb&aac_adtstoasc参考资料修改历史方案http://trac.ffmpeg.org/wiki/Concatenate使用concatdemuxerFFmpeg读取不同格
- linux基础学习方法指导(学习方法+基础命令用法)
景天科技苑
linux基础与进阶shell脚本编写实战linuxlinux基础命令linux学习方法
文章目录第1章计算机硬件的组成及其原理第2章Linux系统介绍与环境搭建准备第3章yum是linux的软件安装工具第4章远程连接管理Linux实践第5章Linux系统命令行入门基础第6章环境变量第7章linux不关机清理内存1、学习工具:笔记类app:notepad++云笔记有道云笔记印象笔记markdown博客头脑风暴思维导图:xmind2、学习模式:学习时间:不能中断,持续学习,视频学习与实际
- Linux 使用 docker 安装 File Browser 文件浏览器
liupeng_blog
dockerdockerlinux运维
文章目录个人知识库FileBrowser简介环境要求一.新建文件目录1.1.新建docker-compose.yml1.2.编写docker-compose.yml二.文件赋权限三、新建filebrowser.json四.启动容器4.1.启动并下载镜像4.2.停止并删除容器五.访问Filebrowser六.FileBrowser设置七.DockerHub官网更多知识平台个人知识库云网站:http:
- 系统遇到了关于locale设置的问题,而且文件名显示为乱码记录!
亮亮哒
linuxcentos运维
1、安装中文语言包:首先,确保你的操作系统已经安装了中文语言包。你可以使用以下命令来安装:yuminstall-yglibc-common2、生成并启用zh_CN.UTF-8locale:执行以下命令生成并启用zh_CN.UTF-8locale:localedef-c-fUTF-8-izh_CNzh_CN.UTF-83、更新locale配置:确保/etc/locale.conf文件中包含以下内容:
- Ubuntu/Linux 配置 locale
iBlackAngel
Linuxlinuxubuntu数据库
文章目录Ubuntu/Linux配置locale1概述2locale2.1locale规则命令规则环境变量优先级2.2查看当前locale设置2.3查看当前系统所有可用的locale2.4安装中文locale语言环境/字符集2.5安装locales包2.6使用locale-gen命令生成语言支持2.7设置当前默认字符集3持久化3.1全局设置3.2用户级设置3.3使用update-locale进行配
- 京东2023年全年活动时间一览表,京东活动日购物节有哪些?
凌风导师
目前京东活动有京东生鲜到家活动,如果没在京东生鲜购买过商品的可以看一看,微信识别下图二维码进入会场京东是比较受欢迎的平台,今天就把2023年京东整年的活动优惠分享给大家,并奉上京东更省钱的方法,如何在京东领取神劵,一年省下不止是亿点点,文章最后分享京东内劵获取渠道使用教程;高省APP邀请码:高省-各大应用商城下载即可-购物领劵返利高,邀请码切记填777999,凌风高省邀请码777999,全网唯一教
- ansible awx自动化工具学习准备
七七powerful
ansible自动化学习
使用sealos快速搭建kubernetes集群!!!-CSDN博客使用Kuboard-Spray安装1套k8s集群Kuboard-Spray图形化工具安装kubernetes集群-CSDN博客使用KuboardSpray安装kubernetes_v1.23.1|Kuboard通过helm安装calico插件Kubernetes默认上网端口_小屁孩的技术博客_51CTO博客【K8s】Kuberne
- 京东内部优惠券软件叫什么?如何领取优惠券
高省_飞智666600
美团作为中国领先的本地生活服务平台,为广大用户提供包括美食、外卖、酒店住宿等多种服务。其中,美团住宿优惠券为广大旅行者和商务人士提供了实惠的住宿选择。本文将为您详细介绍美团住宿优惠券的购买、使用和领取方法。二、美团住宿优惠券怎么买?1.打开美团App,点击“酒店”或“住宿”频道;2.在搜索框输入目的地和入住时间,点击搜索;3.在搜索结果页面,您可以查看酒店的折扣信息和可用优惠券;4.点击选择您需要
- 使用 Ansible 批量部署 Zabbix
始知冰上有仙人
ansiblezabbix服务器
安装Ansible如果您还没有在控制节点上安装Ansible,请先根据您的操作系统版本安装Ansible。可在Ansible官方网站上找到相关文档。例如,在Ubuntu上安装Ansible,可以使用以下命令:$sudoaptupdate$sudoaptinstallansible创建Ansibleplaybook在创建playbook前,需要先在ansiblehosts文件中定义待配置主机信息,例
- 【bug】 jetson上opencv无法录制h264本地视频
lxmyzzs
bugopencv音视频
在JetsonOrinNX上无法使用opencv直接录制h264/h265视频流(h264格式的视频流才能在浏览器播放)解决:软件编码:需要源码编译opencv1.环境准备pipuninstallopencv-pythonsudoaptinstallbuild-essentialcmakegitpython3-devpython3-numpy\libavcodec-devlibavformat-d
- 【bug】global loadsave.cpp:241 cv::findDecoder imread_(‘xxx‘):: can‘t open/read file
lxmyzzs
bugpytorchopencv
问题OPENCV读取图片报错(win11)[WARN:
[email protected]]globalloadsave.cpp:241cv::findDecoderimread_('xxx.png'):can'topen/readfile:checkfilepath/integrity解决:在windows系统上如果直接使用路径加载图片会报上述错误,使用PIL加载也无济于事,问题在文件路径的格式。因此博主做了如下
- Ansible + Shell 服务器巡检脚本
lovely_nn
Linux系统运维服务器运维
脚本概述这是一个用于服务器日常巡检的Shell脚本,主要功能包括:检查多台主机的网络连通性监控CPU、内存和磁盘使用率生成详细的巡检报告通过企业微信发送告警通知核心技术点1.主机批量管理使用Ansible工具远程执行命令和脚本通过主机清单文件(ip_file)管理所有待巡检主机2.资源监控技术CPU监控:通过top命令获取CPU总使用率内存监控:调用自定义脚本mem.sh获取内存使用率磁盘监控:调
- 使用php实现导出pdf(mpdf扩展)
if时光重来
phpphppdf
安装扩展composerrequirempdf/mpdf使用true,'autoLangToFont'=>true,解决中文乱码问题$mpdf=new\Mpdf\Mpdf(['mode'=>'utf-8',//使用UTF-8编码'format'=>'A4-L',//设置纸张格式为A4横向'margin_left'=>15,//设置左边距为15mm'margin_right'=>15,//设置右边距
- Ansible命令
Neng_Miao
ansible
Ansible命令ansible常用命令/usr/bin/ansible#AnsibeAD-Hoc临时命令执行工具,常用于临时命令的执行/usr/bin/ansible-doc#Ansible模块功能查看工具/usr/bin/ansible-galaxy#下载/上传优秀代码或Roles模块的官网平台,基于网络的/usr/bin/ansible-playbook#Ansible定制自动化的任务集编排
- axios封装使用
Hui-1018
前端axios
axios配置配置拦截并使用promise封装get和post请求提示:注意部分伪代码,需要根据实际场景做一些修改importaxiosfrom'axios'constservice=axios.create({baseURL:process.env.BASE_API,//api的base_urltimeout:5000//请求超时时间})//请求拦截器service.interceptors.r
- 使用Ansible批量部署Zabbix Agent服务器
DpgrMl
服务器ansiblezabbix
Ansible是一种强大的自动化工具,可以帮助简化IT基础架构的部署和管理。在本文中,我们将使用Ansible来批量部署ZabbixAgent服务器。ZabbixAgent是一个用于监控和收集服务器指标的客户端程序,它允许Zabbix服务器通过Agent主动收集数据。以下是我们将要执行的步骤:安装Ansible:首先,我们需要在部署Ansible的主机上安装Ansible软件包。可以通过在终端中运
- R 和 Hadoop 大数据分析(一)
原文:annas-archive.org/md5/b7f3a14803c1b4d929732471e0b28932译者:飞龙协议:CCBY-NC-SA4.0前言企业每天获取的数据量呈指数增长。现在可以将这些海量信息存储在像Hadoop这样的低成本平台上。这些组织目前面临的难题是如何处理这些数据,以及如何从中提取关键见解。因此,R就成为了关键工具。R是一个非常强大的工具,它使得在数据上运行高级统计模
- VideoPrism模型论文速读:一种用于视频理解的基础视觉编码器
1.引言论文介绍了VideoPrism,这是一个通用视频编码器,能够在多种视频理解任务中实现最先进的性能。VideoPrism的目标是通过单一冻结模型处理不同的视频理解任务,包括分类、定位、检索、字幕生成和问答。VideoPrism在预训练过程中使用了大规模的视频-文本对数据和带有噪声平行文本的视频片段。预训练方法在掩码自动编码基础上进行了改进,通过全局-局部蒸馏语义视频嵌入和令牌洗牌方案,使Vi
- RedisJSON 的 JSON.STRAPPEND字符串追加的正确姿势
1·写在前面在数据模型中,“追加”是个高频需求:日志拼接、状态堆栈、消息跟踪……如果把这些信息存在RedisJSON文档里,与其整段读出再写回,不如直接用JSON.STRAPPEND就地完成。本文将带你从语法、返回值到性能陷阱,全方位掌握JSON.STRAPPEND的使用,并配套一段Go-Redis代码示例,随取随用。2·指令总览指令功能复杂度JSON.STRAPPENDkey[path]valu
- element-ui 轮播图的使用
b49779e26200
element-ui轮播图的使用```exportdefault{name:"Banner",data(){return{//图片地址数组img_list:["./banner1","./banner1","./banner1","./banner1"],//图片父容器高度bannerHeight:1000,//浏览器宽度screenWidth:0};},methods:{setSize:func
- 磁盘分析软件(C盘爆满精确清理必备)---SpaceSniffer
潜心专研的小张同学
杂谈其他
1.第一步上图2.第二步分享软件链接:https://pan.baidu.com/s/1GhLmzNtG398ah_26lVV1aQ提取码:sfqf3.第三步简单使用教程3.1打开软件,选择要分析的盘(我这里选的C盘):3.2静待分析完成3.3根据分析的结果,删除对应文件目录的文件
- 我们可能不再需要UI工程师了~
强化学习曾小健
ui
我们可能不再需要UI工程师了~原创深度抑郁患者GIS小丸子2025年06月30日08:01中国香港我写这篇文章的时间是6月29日23:51分,刚刚和技术团队结束了本周的例会,例会上研发向我们展示了本周他基于原型直接使用Cursor生成的前端大屏页面,这个过程完全没有前端以及UI工程师的参与,只有一个程序员参考产品原型完成。如下是这张大屏页面对应的Axure原型图,当然还有PC版,但是PC管理后台虽
- jQuery的.toggle()事件
小乖nia
JQuery
$(selected).toggle()事件会自动获得当前对象的显示或者隐藏状态,并且使用触发事件进行切换。在元素的click事件中绑定两个或两个以上的函数toggle不像bind需要在后面添加"click"来绑定click触发事件,toggle本身就是click触发的(而且只能click触发)。jquery中toggle的2种用法一、在元素的click事件中绑定两个或两个以上的函数toggle不
- HTTPie: 开发者友好的http客户端工具
fire-flyer
http网络协议restful开发工具
一、HTTPie简介HTTPie是一个以开发者体验为核心的命令行HTTP客户端工具,目标是替代curl等传统工具,简洁优雅地发送HTTP请求并读取响应,尤其适用于调试、测试和日常开发中的RESTfulAPI操作。项目主页:HTTPie–APItestingclientthatflowswithyouGitHub:https://github.com/httpie/httpie二、核心特性功能类别H
- 从 Ollama 转向 vLLM:寻求高通量 LLM 服务的稳定性
知识大胖
NVIDIAGPU和大语言模型开发教程ai
简介在过去的一年里,我一直在大量使用GraphRAG(微软版本和我自己开发的版本),我总是惊讶于文档复杂性的微小增加会造成多大的预算浪费。当我使用gpt-4.1-miniOpenAI时——仅一套文档就花费了我200多美元(!!)。即使使用gpt-4.1-nano(目前最便宜的前沿模型),我的预算也是荒谬的。为几份(确实很大的)文件花费2.15亿个代币是荒谬的,而且需要几天的时间来处理,这太过分了。
- 【限时免费】 Claude Code WebUI v0.1.13版本发布:增强交互控制与权限管理
ClaudeCodeWebUIv0.1.13版本发布:增强交互控制与权限管理ClaudeCodeWebUI是一个基于ClaudeAI模型的代码辅助工具,提供了直观的Web界面让开发者能够更方便地与AI进行编程相关的交互。该项目通过简洁的用户界面,让开发者可以快速获取代码建议、调试帮助和编程知识。流式响应中断功能在v0.1.13版本中,项目团队引入了一个重要的新特性:流式响应中断功能。这项改进解决了
- claude-code-router:智能请求路由管理工具
claude-code-router:智能请求路由管理工具项目介绍在软件开发领域,高效管理请求并确保它们正确地被路由到对应的服务或模型是至关重要的。ClaudeCodeRouter就是这样一款工具,它专为ClaudeCode请求的路由管理而设计。通过这个工具,开发者可以自定义任何请求,将它们路由到不同的模型上,从而提高系统整体的工作效率和响应速度。项目技术分析ClaudeCodeRouter基于J
- 【云笔记搭建】Visual Code + Github仓库 + Git
GPNU_Log
githubgitvscode云端
0.前言文章目录0.前言1.需要的工具2.工具准备2.1VisualCode2.2Github仓库1.自行注册账号2.点击右上方新建仓库3.填写仓库信息4.获取仓库token2.3git的安装与使用3.笔记的使用及VisualCode插件的推荐3.1新建笔记文件夹3.2插件的推荐3.2.1.PicGo3.2.2markdownlint3.2.3MarkdownAllinone4.一些小技巧4.1改
- 怎么样才能成为专业的程序员?
cocos2d-x小菜
编程PHP
如何要想成为一名专业的程序员?仅仅会写代码是不够的。从团队合作去解决问题到版本控制,你还得具备其他关键技能的工具包。当我们询问相关的专业开发人员,那些必备的关键技能都是什么的时候,下面是我们了解到的情况。
关于如何学习代码,各种声音很多,然后很多人就被误导为成为专业开发人员懂得一门编程语言就够了?!呵呵,就像其他工作一样,光会一个技能那是远远不够的。如果你想要成为
- java web开发 高并发处理
BreakingBad
javaWeb并发开发处理高
java处理高并发高负载类网站中数据库的设计方法(java教程,java处理大量数据,java高负载数据) 一:高并发高负载类网站关注点之数据库 没错,首先是数据库,这是大多数应用所面临的首个SPOF。尤其是Web2.0的应用,数据库的响应是首先要解决的。 一般来说MySQL是最常用的,可能最初是一个mysql主机,当数据增加到100万以上,那么,MySQL的效能急剧下降。常用的优化措施是M-S(
- mysql批量更新
ekian
mysql
mysql更新优化:
一版的更新的话都是采用update set的方式,但是如果需要批量更新的话,只能for循环的执行更新。或者采用executeBatch的方式,执行更新。无论哪种方式,性能都不见得多好。
三千多条的更新,需要3分多钟。
查询了批量更新的优化,有说replace into的方式,即:
replace into tableName(id,status) values
- 微软BI(3)
18289753290
微软BI SSIS
1)
Q:该列违反了完整性约束错误;已获得 OLE DB 记录。源:“Microsoft SQL Server Native Client 11.0” Hresult: 0x80004005 说明:“不能将值 NULL 插入列 'FZCHID',表 'JRB_EnterpriseCredit.dbo.QYFZCH';列不允许有 Null 值。INSERT 失败。”。
A:一般这类问题的存在是
- Java中的List
g21121
java
List是一个有序的 collection(也称为序列)。此接口的用户可以对列表中每个元素的插入位置进行精确地控制。用户可以根据元素的整数索引(在列表中的位置)访问元素,并搜索列表中的元素。
与 set 不同,列表通常允许重复
- 读书笔记
永夜-极光
读书笔记
1. K是一家加工厂,需要采购原材料,有A,B,C,D 4家供应商,其中A给出的价格最低,性价比最高,那么假如你是这家企业的采购经理,你会如何决策?
传统决策: A:100%订单 B,C,D:0%
&nbs
- centos 安装 Codeblocks
随便小屋
codeblocks
1.安装gcc,需要c和c++两部分,默认安装下,CentOS不安装编译器的,在终端输入以下命令即可yum install gccyum install gcc-c++
2.安装gtk2-devel,因为默认已经安装了正式产品需要的支持库,但是没有安装开发所需要的文档.yum install gtk2*
3. 安装wxGTK
yum search w
- 23种设计模式的形象比喻
aijuans
设计模式
1、ABSTRACT FACTORY—追MM少不了请吃饭了,麦当劳的鸡翅和肯德基的鸡翅都是MM爱吃的东西,虽然口味有所不同,但不管你带MM去麦当劳或肯德基,只管向服务员说“来四个鸡翅”就行了。麦当劳和肯德基就是生产鸡翅的Factory 工厂模式:客户类和工厂类分开。消费者任何时候需要某种产品,只需向工厂请求即可。消费者无须修改就可以接纳新产品。缺点是当产品修改时,工厂类也要做相应的修改。如:
- 开发管理 CheckLists
aoyouzi
开发管理 CheckLists
开发管理 CheckLists(23) -使项目组度过完整的生命周期
开发管理 CheckLists(22) -组织项目资源
开发管理 CheckLists(21) -控制项目的范围开发管理 CheckLists(20) -项目利益相关者责任开发管理 CheckLists(19) -选择合适的团队成员开发管理 CheckLists(18) -敏捷开发 Scrum Master 工作开发管理 C
- js实现切换
百合不是茶
JavaScript栏目切换
js主要功能之一就是实现页面的特效,窗体的切换可以减少页面的大小,被门户网站大量应用思路:
1,先将要显示的设置为display:bisible 否则设为none
2,设置栏目的id ,js获取栏目的id,如果id为Null就设置为显示
3,判断js获取的id名字;再设置是否显示
代码实现:
html代码:
<di
- 周鸿祎在360新员工入职培训上的讲话
bijian1013
感悟项目管理人生职场
这篇文章也是最近偶尔看到的,考虑到原博客发布者可能将其删除等原因,也更方便个人查找,特将原文拷贝再发布的。“学东西是为自己的,不要整天以混的姿态来跟公司博弈,就算是混,我觉得你要是能在混的时间里,收获一些别的有利于人生发展的东西,也是不错的,看你怎么把握了”,看了之后,对这句话记忆犹新。 &
- 前端Web开发的页面效果
Bill_chen
htmlWebMicrosoft
1.IE6下png图片的透明显示:
<img src="图片地址" border="0" style="Filter.Alpha(Opacity)=数值(100),style=数值(3)"/>
或在<head></head>间加一段JS代码让透明png图片正常显示。
2.<li>标
- 【JVM五】老年代垃圾回收:并发标记清理GC(CMS GC)
bit1129
垃圾回收
CMS概述
并发标记清理垃圾回收(Concurrent Mark and Sweep GC)算法的主要目标是在GC过程中,减少暂停用户线程的次数以及在不得不暂停用户线程的请夸功能,尽可能短的暂停用户线程的时间。这对于交互式应用,比如web应用来说,是非常重要的。
CMS垃圾回收针对新生代和老年代采用不同的策略。相比同吞吐量垃圾回收,它要复杂的多。吞吐量垃圾回收在执
- Struts2技术总结
白糖_
struts2
必备jar文件
早在struts2.0.*的时候,struts2的必备jar包需要如下几个:
commons-logging-*.jar Apache旗下commons项目的log日志包
freemarker-*.jar
- Jquery easyui layout应用注意事项
bozch
jquery浏览器easyuilayout
在jquery easyui中提供了easyui-layout布局,他的布局比较局限,类似java中GUI的border布局。下面对其使用注意事项作简要介绍:
如果在现有的工程中前台界面均应用了jquery easyui,那么在布局的时候最好应用jquery eaysui的layout布局,否则在表单页面(编辑、查看、添加等等)在不同的浏览器会出
- java-拷贝特殊链表:有一个特殊的链表,其中每个节点不但有指向下一个节点的指针pNext,还有一个指向链表中任意节点的指针pRand,如何拷贝这个特殊链表?
bylijinnan
java
public class CopySpecialLinkedList {
/**
* 题目:有一个特殊的链表,其中每个节点不但有指向下一个节点的指针pNext,还有一个指向链表中任意节点的指针pRand,如何拷贝这个特殊链表?
拷贝pNext指针非常容易,所以题目的难点是如何拷贝pRand指针。
假设原来链表为A1 -> A2 ->... -> An,新拷贝
- color
Chen.H
JavaScripthtmlcss
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd"> <HTML> <HEAD>&nbs
- [信息与战争]移动通讯与网络
comsci
网络
两个坚持:手机的电池必须可以取下来
光纤不能够入户,只能够到楼宇
建议大家找这本书看看:<&
- oracle flashback query(闪回查询)
daizj
oracleflashback queryflashback table
在Oracle 10g中,Flash back家族分为以下成员:
Flashback Database
Flashback Drop
Flashback Table
Flashback Query(分Flashback Query,Flashback Version Query,Flashback Transaction Query)
下面介绍一下Flashback Drop 和Flas
- zeus持久层DAO单元测试
deng520159
单元测试
zeus代码测试正紧张进行中,但由于工作比较忙,但速度比较慢.现在已经完成读写分离单元测试了,现在把几种情况单元测试的例子发出来,希望有人能进出意见,让它走下去.
本文是zeus的dao单元测试:
1.单元测试直接上代码
package com.dengliang.zeus.webdemo.test;
import org.junit.Test;
import o
- C语言学习三printf函数和scanf函数学习
dcj3sjt126com
cprintfscanflanguage
printf函数
/*
2013年3月10日20:42:32
地点:北京潘家园
功能:
目的:
测试%x %X %#x %#X的用法
*/
# include <stdio.h>
int main(void)
{
printf("哈哈!\n"); // \n表示换行
int i = 10;
printf
- 那你为什么小时候不好好读书?
dcj3sjt126com
life
dady, 我今天捡到了十块钱, 不过我还给那个人了
good girl! 那个人有没有和你讲thank you啊
没有啦....他拉我的耳朵我才把钱还给他的, 他哪里会和我讲thank you
爸爸, 如果地上有一张5块一张10块你拿哪一张呢....
当然是拿十块的咯...
爸爸你很笨的, 你不会两张都拿
爸爸为什么上个月那个人来跟你讨钱, 你告诉他没
- iptables开放端口
Fanyucai
linuxiptables端口
1,找到配置文件
vi /etc/sysconfig/iptables
2,添加端口开放,增加一行,开放18081端口
-A INPUT -m state --state NEW -m tcp -p tcp --dport 18081 -j ACCEPT
3,保存
ESC
:wq!
4,重启服务
service iptables
- Ehcache(05)——缓存的查询
234390216
排序ehcache统计query
缓存的查询
目录
1. 使Cache可查询
1.1 基于Xml配置
1.2 基于代码的配置
2 指定可搜索的属性
2.1 可查询属性类型
2.2 &
- 通过hashset找到数组中重复的元素
jackyrong
hashset
如何在hashset中快速找到重复的元素呢?方法很多,下面是其中一个办法:
int[] array = {1,1,2,3,4,5,6,7,8,8};
Set<Integer> set = new HashSet<Integer>();
for(int i = 0
- 使用ajax和window.history.pushState无刷新改变页面内容和地址栏URL
lanrikey
history
后退时关闭当前页面
<script type="text/javascript">
jQuery(document).ready(function ($) {
if (window.history && window.history.pushState) {
- 应用程序的通信成本
netkiller.github.com
虚拟机应用服务器陈景峰netkillerneo
应用程序的通信成本
什么是通信
一个程序中两个以上功能相互传递信号或数据叫做通信。
什么是成本
这是是指时间成本与空间成本。 时间就是传递数据所花费的时间。空间是指传递过程耗费容量大小。
都有哪些通信方式
全局变量
线程间通信
共享内存
共享文件
管道
Socket
硬件(串口,USB) 等等
全局变量
全局变量是成本最低通信方法,通过设置
- 一维数组与二维数组的声明与定义
恋洁e生
二维数组一维数组定义声明初始化
/** * */ package test20111005; /** * @author FlyingFire * @date:2011-11-18 上午04:33:36 * @author :代码整理 * @introduce :一维数组与二维数组的初始化 *summary: */ public c
- Spring Mybatis独立事务配置
toknowme
mybatis
在项目中有很多地方会使用到独立事务,下面以获取主键为例
(1)修改配置文件spring-mybatis.xml <!-- 开启事务支持 --> <tx:annotation-driven transaction-manager="transactionManager" /> &n
- 更新Anadroid SDK Tooks之后,Eclipse提示No update were found
xp9802
eclipse
使用Android SDK Manager 更新了Anadroid SDK Tooks 之后,
打开eclipse提示 This Android SDK requires Android Developer Toolkit version 23.0.0 or above, 点击Check for Updates
检测一会后提示 No update were found