5 rsyslog日志管理
rsyslog
Linux的日志记录了用户在系统上一切操作,看日志去分析系统的状态是运维人员必须掌握的基本功。
rsyslog日志服务器的优势:
1、日志统一,集中式管理2、日志实时传送到一个更加安全的远端服务器上,真正记录用户行为,使日志的2次更改可能性大大降低,从而能够对日志进行真实回放,便于问题追踪。
rsyslog的新功能:
rsyslog是一个加强版的syslog,具有各种各样的新功能,典型的有:1、多线程运行
2、支持多种传输协议
3、灵活的模板机制,可以得到多种输出格式
4、插件式结构,多种多样的输入、输出模块
5、可以把日志存放在Mysql ,PostgreSQL,Oracle等数据库中
配置文件
配置文件存放在 /etc/rsyslog.conf,由三部分组成:
MODULES:相关模块配置
GLOBAL DIRECTIVES:全局配置
RULES:日志记录相关的规则配置
[root@CentOS74 ~]# cat /etc/rsyslog.conf
# rsyslog configuration file
# For more information see /usr/share/doc/rsyslog-*/rsyslog_conf.html
# If you experience problems, see http://www.rsyslog.com/doc/troubleshoot.html
#### MODULES ####
# The imjournal module bellow is now used as a message source instead of imuxsock.
$ModLoad imuxsock # provides support for local system logging (e.g. via logger command)
$ModLoad imjournal # provides access to the systemd journal
#$ModLoad imklog # reads kernel messages (the same are read from journald)
#$ModLoad immark # provides --MARK-- message capability
# Provides UDP syslog reception
#$ModLoad imudp
#$UDPServerRun 514
# Provides TCP syslog reception
#$ModLoad imtcp
#$InputTCPServerRun 514
#### GLOBAL DIRECTIVES ####
# Where to place auxiliary files
$WorkDirectory /var/lib/rsyslog
# Use default timestamp format
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# File syncing capability is disabled by default. This feature is usually not required,
# not useful and an extreme performance hit
#$ActionFileEnableSync on
# Include all config files in /etc/rsyslog.d/
$IncludeConfig /etc/rsyslog.d/*.conf #自定义的配置文件可以存放在/etc/rsyslog.d/,命名为*.conf
# Turn off message reception via local log socket;
# local messages are retrieved through imjournal now.
$OmitLocalLogging on
# File to store the position in the journal
$IMJournalStateFile imjournal.state
#### RULES ####
# Log all kernel messages to the console.
# Logging much else clutters up the screen.
#kern.* /dev/console
# Log anything (except mail) of level info or higher.
# Don't log private authentication messages!
*.info;mail.none;authpriv.none;cron.none /var/log/messages
#除了邮件、用户登录、计划任务的日志以外,所有info级别的事件都记录在/var/log/messages中
# The authpriv file has restricted access.
authpriv.* /var/log/secure #用户登录的所有事件都记录在/var/log/secure中
# Log all the mail messages in one place.
mail.* -/var/log/maillog
#^"-"代表异步写入,同步写入更加稳定
# Log cron stuff
cron.* /var/log/cron
# Everybody gets emergency messages
*.emerg :omusrmsg:*
# Save news errors of level crit and higher in a special file.
uucp,news.crit #可以使用 设施,[设施].级别 的格式定义 /var/log/spooler
# Save boot messages also to boot.log
local7.* /var/log/boot.log
# ### begin forwarding rule ###
# The statement between the begin ... end define a SINGLE forwarding
# rule. They belong together, do NOT split them. If you create multiple
# forwarding rules, duplicate the whole block!
# Remote Logging (we use TCP for reliable delivery)
#
# An on-disk queue is created for this action. If the remote host is
# down, messages are spooled to disk and sent when it is up again.
#$ActionQueueFileName fwdRule1 # unique name prefix for spool files
#$ActionQueueMaxDiskSpace 1g # 1gb space limit (use as much as possible)
#$ActionQueueSaveOnShutdown on # save messages to disk on shutdown
#$ActionQueueType LinkedList # run asynchronously
#$ActionResumeRetryCount -1 # infinite retries if host is down
# remote host is: name/ip:port, e.g. 192.168.0.1:514, port optional
#*.* @@remote-host:514
# ### end of the forwarding rule ###在各项中应用的配置文件中,也定义了各自日志的记录规则
[root@CentOS74 ~]# cat /etc/ssh/sshd_config | grep SyslogFacility #查看sshd的配置文件
#SyslogFacility AUTH
SyslogFacility AUTHPRIV #sshd定义了其日志记录在AUTHPRIV设施中
修改 sshd 的日志记录规则
[root@CentOS74 ~]# cat /etc/ssh/sshd_config | grep SyslogFacility
#SyslogFacility AUTH
SyslogFacility LOCAL0 #声明sshd的日志规则记录在local0设施中
在 /etc/rsyslog.d/ 中创建新的配置文件
[root@CentOS74 ~]# cat /etc/rsyslog.d/sshd.conf
local0.* /var/log/sshd.log语法:设施.级别;[设施.级别]... 目标
设施:
auth, authpriv, cron, daemon,ftp,kern, lpr, mail, news, security(auth), user, uucp, local0-local7, syslog
级别:
debug, info, notice, warn(warning), err(error), crit(critical), alert, emerg(panic),*
*: 所有级别
none:没有级别,即不记录
PRIORITY:指定级别(含)以上的所有级别
=PRIORITY:仅记录指定级别的日志信息
目标:
文件路径:通常在/var/log/,文件路径前的-表示异步写入
用户:将日志事件通知给指定的用户,* 表示登录的所有用户
日志服务器:@host,把日志送往至指定的远程服务器记录
管道: | COMMAND,转发给其它命令处理
重启服务,使用 shh 登陆后观察日志
[root@CentOS74 ~]# tail -f /var/log/sshd.log #sshd的日志记录文件修改为/var/log/sshd.log
Jun 26 10:27:49 CentOS74 sshd[11272]: Server listening on 0.0.0.0 port 22.
Jun 26 10:27:49 CentOS74 sshd[11272]: Server listening on :: port 22.
Jun 26 10:28:33 CentOS74 sshd[11288]: Accepted publickey for root from 192.168.30.75 port 53392 ssh2: RSA SHA256:YjkzBrLiMrUIiMJQKyWG+UYgFfMyN5UsjLrGgzmJ6tM利用UDP远程记录日志
rsyslog 服务的库文件存放在 /lib64/rsyslog/*.so
[root@CentOS74 ~]# ls /lib64/rsyslog/
imdiag.so imklog.so imptcp.so imuxsock.so lmnsd_ptcp.so lmtcpclt.so mmanon.so mmutf8fix.so omprog.so omtesting.so pmcisconames.so pmsnare.so
imfile.so immark.so imtcp.so lmnet.so lmregexp.so lmtcpsrv.so mmcount.so omjournal.so omruleset.so omuxsock.so pmlastmsg.so
imjournal.so impstats.so imudp.so lmnetstrms.so lmstrmsrv.so lmzlibw.so mmexternal.so ommail.so omstdout.so pmaixforwardedfrom.so pmrfc3164sd.so[root@CentOS74 ~]# cat /etc/rsyslog.d/sshd.conf
local0.* @192.168.30.75
[root@CentOS75 ~]# cat /etc/rsyslog.conf | grep local0
local0.* /var/log/local0.log[root@CentOS75 ~]# cat /etc/rsyslog.conf | grep -A 2 'Provides UDP'
# Provides UDP syslog reception
$ModLoad imudp #启用imudp模块
$UDPServerRun 514 #监听在udp514端口上 重启服务,使用 ssh 登陆后观察本地日志和远程日志
[root@CentOS74 ~]# tail -f /var/log/secure #本地日志,关于sshd的日志还在记录,但是是pam模块记录的日志
Jun 26 11:02:18 CentOS74 polkitd[557]: Unregistered Authentication Agent for unix-process:11383:489051 (system bus name :1.68, object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_US.UTF-8) (disconnected from bus)
Jun 26 11:06:30 CentOS74 sshd[11398]: pam_unix(sshd:session): session opened for user root by (uid=0)
Jun 26 11:07:34 CentOS74 sshd[11398]: pam_unix(sshd:session): session closed for user root
Jun 26 11:07:44 CentOS74 sshd[11421]: pam_unix(sshd:session): session opened for user root by (uid=0)
Jun 26 11:09:55 CentOS74 polkitd[557]: Registered Authentication Agent for unix-process:11485:534750 (system bus name :1.72 [/usr/bin/pkttyagent --notify-fd 5 --fallback], object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_US.UTF-8)
Jun 26 11:09:55 CentOS74 polkitd[557]: Unregistered Authentication Agent for unix-process:11485:534750 (system bus name :1.72, object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_US.UTF-8) (disconnected from bus)
Jun 26 11:10:54 CentOS74 sshd[11496]: pam_unix(sshd:session): session opened for user root by (uid=0)
Jun 26 11:13:20 CentOS74 sshd[11496]: pam_unix(sshd:session): session closed for user root
Jun 26 11:13:22 CentOS74 sshd[11421]: pam_unix(sshd:session): session closed for user root
Jun 26 11:18:01 CentOS74 sshd[11567]: pam_unix(sshd:session): session opened for user root by (uid=0)
[root@CentOS75 ~]# tail -f /var/log/local0.log #远程日志
Jun 26 11:18:01 CentOS74 sshd[11567]: Accepted publickey for root from 192.168.30.174 port 34204 ssh2: RSA SHA256:tfAEsr7jMYmGSWlqWGkzQSoAqlujC84eDkMnOfM5sgI
当然,也可以让日志在多个目标上记录
[root@CentOS74 ~]# cat /etc/rsyslog.d/sshd.conf
local0.* @192.168.30.75 #在远程主机上记录
local0.* /var/log/local0.log #在本机的指定文件中记录利用TCP远程记录日志
与UDP相同,在远程主机上启用 tcp 模块并开启端口
[root@CentOS75 ~]# cat /etc/rsyslog.conf | grep -A 2 'Provides TCP'
# Provides TCP syslog reception
$ModLoad imtcp
$InputTCPServerRun 514
[root@CentOS75 ~]# ss -tln | grep 514 #tcp的514端口已经打开
LISTEN 0 25 *:514 *:*
LISTEN 0 25 :::514 :::* 接下来在远程主机上定义对应的日志存放路径,并在本地主机上声明使用 tcp 协议传输
[root@CentOS74 ~]# cat /etc/rsyslog.d/sshd.conf
local0.* @@192.168.30.75 #两个@表示使用tcp协议传输
local0.* /var/log/local0.log重启服务,观察远程主机的日志记录情况
[root@CentOS75 ~]# tail -f /var/log/local0.log
Jun 26 11:40:28 CentOS74 sshd[11694]: Received disconnect from 192.168.30.174 port 34206:11: disconnected by user
Jun 26 11:40:28 CentOS74 sshd[11694]: Disconnected from 192.168.30.174 port 34206
Jun 26 11:40:29 CentOS74 sshd[11764]: Accepted publickey for root from 192.168.30.174 port 34208 ssh2: RSA SHA256:tfAEsr7jMYmGSWlqWGkzQSoAqlujC84eDkMnOfM5sgI系统自带日志
/var/log/secure:系统安装日志,文本格式,应周期性分析
/var/log/btmp:当前系统上,用户的失败尝试登录相关的日志信息,二进制格式,lastb命令进行查看
/var/log/wtmp:当前系统上,用户正常登录系统的相关日志信息,二进制格式,last命令可以查看
/var/log/lastlog:每一个用户最近一次的登录信息,二进制格式,lastlog命令可以查看
/var/log/dmesg:系统引导过程中的日志信息,文本格式,专用命令dmesg查看
/var/log/messages :系统中大部分的信息
/var/log/anaconda : anaconda的日志
日志管理工具 journalctl
Systemd 统一管理所有 Unit 的启动日志。带来的好处就是,可以只用 journalctl 一个命令,查看所有日志(内核日志和应用日志)。日志的配置文件 /etc/systemd/journald.conf
语法:journalctl [选项] [参数]
常见用法:
-b [-#]:查看系统第前#次启动的日志
--since=时间:查看指定时间的日志
journalctl --since="2017-10-30 18:10:30"
journalctl --since "20 min ago"
journalctl --since yesterday
journalctl --since "2017-01-10" --until "2017-01-11 03:00"
journalctl --since 09:00 --until "1 hour ago"-f:实时滚动显示最新日志
journalctl /usr/lib/systemd/systemd #查看指定服务的日志_UID=用户编号:查看指定用户的日志
脚本路径:查看某个路径的脚本的日志
-u 服务:查看某个 Unit 的日志
--no-pager:不分页显示
-p 等级:查看指定优先级(及其以上级别)的日志
0: emerg
1: alert
2: crit
3: err
4: warning
5: notice
6: info
7: debug--disk-usage:显示日志占据的硬盘空间
--vacuum-size=容量:指定日志文件占据的最大空间
-vacuum-time=时间:指定日志文件保存多久
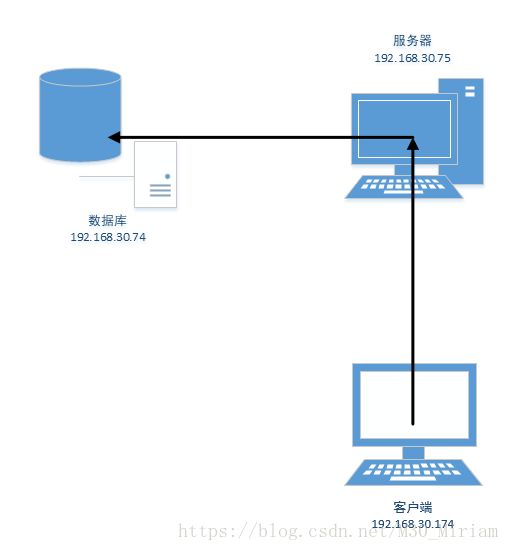
利用MySql存放日志
简单的规划如图
(1)在数据库机上准备 mariadb
[root@CentOS74 ~]# yum install mariadb-server
[root@CentOS74 ~]# systemctl start mariadb.service(2)在服务器上安装 ommysql 模块,模块在 rsyslog-mysql 软件包中
[root@CentOS75 ~]# yum install rsyslog-mysql.x86_64 [root@CentOS75 ~]# cat /etc/rsyslog.conf | grep ommysql
$ModLoad ommysql
local0.* :ommysql:192.168.30.74,Syslog,logadmin,dengniaiwo123
[root@CentOS75 ~]# scp /usr/share/doc/rsyslog-8.24.0/mysql-createDB.sql [email protected]:/root
mysql-createDB.sql 100% 1046 1.1MB/s 00:00 [root@CentOS74 ~]# mysql < mysql-createDB.sqlMariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| Syslog | #由mysql-createDB.sql生成的Syslog库
| mysql |
| performance_schema |
| test |
+--------------------+
5 rows in set (0.00 sec)
MariaDB [Syslog]> show tables;
+------------------------+
| Tables_in_Syslog | #Syslog库中的表
+------------------------+
| SystemEvents |
| SystemEventsProperties |
+------------------------+
2 rows in set (0.00 sec)
(4)在数据库中为 Syslog 库创建管理员
MariaDB [Syslog]> grant all on Syslog.* to logadmin@'192.168.30.%' identified by 'dengniaiwo123';
Query OK, 0 rows affected (0.00 sec)
(5)修改服务器上指定设施的日志规则
[root@CentOS75 ~]# cat /etc/rsyslog.conf | grep ommysql
$ModLoad ommysql #加载ommysql模块 #:模块:数据库IP,库名,管理员,密码
local0.* :ommysql:192.168.30.74,Syslog,logadmin,dengniaiwo123利用 logger 工具生成一条日志记录,并在数据库中查看
[root@CentOS75 ~]# logger -p local0.info "test log"
MariaDB [Syslog]> select * from SystemEvents \G;
*************************** 1. row ***************************
ID: 1
CustomerID: NULL
ReceivedAt: 2018-06-26 15:41:17
DeviceReportedTime: 2018-06-26 15:41:17
Facility: 16
Priority: 6
FromHost: CentOS75
Message: Server listening on 0.0.0.0 port 22.
NTSeverity: NULL
Importance: NULL
EventSource: NULL
EventUser: NULL
EventCategory: NULL
EventID: NULL
EventBinaryData: NULL
MaxAvailable: NULL
CurrUsage: NULL
MinUsage: NULL
MaxUsage: NULL
InfoUnitID: 1
SysLogTag: sshd[2395]:
EventLogType: NULL
GenericFileName: NULL
SystemID: NULL
*************************** 2. row ***************************
ID: 2
CustomerID: NULL
ReceivedAt: 2018-06-26 15:41:17
DeviceReportedTime: 2018-06-26 15:41:17
Facility: 16
Priority: 6
FromHost: CentOS75
Message: Server listening on :: port 22.
NTSeverity: NULL
Importance: NULL
EventSource: NULL
EventUser: NULL
EventCategory: NULL
EventID: NULL
EventBinaryData: NULL
MaxAvailable: NULL
CurrUsage: NULL
MinUsage: NULL
MaxUsage: NULL
InfoUnitID: 1
SysLogTag: sshd[2395]:
EventLogType: NULL
GenericFileName: NULL
SystemID: NULL
*************************** 3. row ***************************
ID: 3
CustomerID: NULL
ReceivedAt: 2018-06-26 15:41:25
DeviceReportedTime: 2018-06-26 15:41:25
Facility: 16
Priority: 6
FromHost: CentOS75
Message: Accepted publickey for root from 192.168.30.174 port 46452 ssh2: RSA SHA256:tfAEsr7jMYmGSWlqWGkzQSoAqlujC84eDkMnOfM5sgI
NTSeverity: NULL
Importance: NULL
EventSource: NULL
EventUser: NULL
EventCategory: NULL
EventID: NULL
EventBinaryData: NULL
MaxAvailable: NULL
CurrUsage: NULL
MinUsage: NULL
MaxUsage: NULL
InfoUnitID: 1
SysLogTag: sshd[2397]:
EventLogType: NULL
GenericFileName: NULL
SystemID: NULL
*************************** 4. row ***************************
ID: 4
CustomerID: NULL
ReceivedAt: 2018-06-26 15:44:07
DeviceReportedTime: 2018-06-26 15:44:07
Facility: 16
Priority: 6
FromHost: CentOS75
Message: test log
NTSeverity: NULL
Importance: NULL
EventSource: NULL
EventUser: NULL
EventCategory: NULL
EventID: NULL
EventBinaryData: NULL
MaxAvailable: NULL
CurrUsage: NULL
MinUsage: NULL
MaxUsage: NULL
InfoUnitID: 1
SysLogTag: root:
EventLogType: NULL
GenericFileName: NULL
SystemID: NULL
4 rows in set (0.00 sec)Logrotate 日志滚动
logrotate 程序是一个日志文件管理工具。用来把旧的日志文件删除,并创建新的日志文件,称为日志转储或滚动。可以根据日志文件的大小,也可以根据其天数来转储,这个过程一般通过 cron 程序来执行。
查看 /etc/logrotate.conf 配置文件
[root@CentOS74 ~]# cat /etc/logrotate.conf
# see "man logrotate" for details
# rotate log files weekly #单位时间
weekly
# keep 4 weeks worth of backlogs #滚动间隔
rotate 4
# create new (empty) log files after rotating old ones #滚动策略
create
# use date as a suffix of the rotated file #旧日志的命名格式
dateext
# uncomment this if you want your log files compressed #是否打包
#compress
# RPM packages drop log rotation information into this directory #应用各自的日志滚动策略
include /etc/logrotate.d
# no packages own wtmp and btmp -- we'll rotate them here
/var/log/wtmp {
monthly
create 0664 root utmp
minsize 1M
rotate 1
}
/var/log/btmp {
missingok
monthly
create 0600 root utmp
rotate 1
}
# system-specific logs may be also be configured here.
查看 /etc/logrotate.d 中的应用日志滚动策略
[root@CentOS74 ~]# cat /etc/logrotate.d/yum
/var/log/yum.log {
missingok
notifempty
size 30k
yearly
create 0600 root root
}常见参数:
compress 通过gzip 压缩转储以后的日志nocompress 不需要压缩时,用这个参数
copytruncate 用于还在打开中的日志文件,把当前日志备份并截断
nocopytruncate 备份日志文件但是不截断
create mode owner group 转储文件,使用指定的文件模式创建新的日志文件
nocreate 不建立新的日志文件
delaycompress 和 compress 一起使用时,转储的日志文件到下一次转储时才压缩
nodelaycompress 覆盖 delaycompress 选项,转储并压缩
errors address 专储时的错误信息发送到指定的Email 地址
ifempty 即使是空文件也转储,是缺省选项。
notifempty 如果是空文件的话,不转储
mail address 把转储的日志文件发送到指定的E-mail 地址
nomail 转储时不发送日志文件
olddir directory 转储后的日志文件放入指定的目录,必须和当前日志文件在同一个文件系统
noolddir 转储后的日志文件和当前日志文件放在同一个目录下
prerotate/endscript 在转储以前需要执行的命令可以放入这个对,这两个关键字必须单独成行
postrotate/endscript 在转储以后需要执行的命令可以放入这个对,这两个关键字必须单独成行
daily 指定转储周期为每天
weekly 指定转储周期为每周
monthly 指定转储周期为每月
size 大小 指定日志超过多大时,就执行日志转储
rotate count 指定日志文件删除之前转储的次数,0 指没有备份,5 指保留5 个备份
Missingok 如果日志不存在,提示错误
Nomissingok如果日志不存在,继续下一次日志,不提示错误