- 业务流逻辑如何搭建?为何橙武平台选用了 LogicFlow?
橙武科技
低代码低代码
前言在橙武低代码平台的架构设计中,“业务逻辑编排”并不是锦上添花的功能,而是决定平台扩展能力的根基之一。对内,它承担着流程驱动、条件分支、异步节点、子流程等任务;对外,它决定了平台能否真正支持多行业、多租户的复杂业务建模需求。我们评估过包括BPMN.js、ReactFlow、AntVG6、JointJS等多种图形与流程编排引擎,最终选择了滴滴开源的LogicFlow作为橙武平台的核心业务流程引擎。
- vue3使用AntV X6 (图可视化引擎)历程[二]
在路上`
Vuevue.jsjavascript
通过h函数动态展示自定义节点内容一、案例效果二、案例代码父组件.BloodTopology.vuerightContentimportRightDrawerfrom'@/common/components/topologyToolKit/RightDrawer.vue';importTopologyCompactfrom'@/common/components/topologyToolKit/To
- 【CTF】青少年CTF擂台挑战赛 2024 #Round 1 部分WriteUp_青少年ctf训练平台 追光者(1)
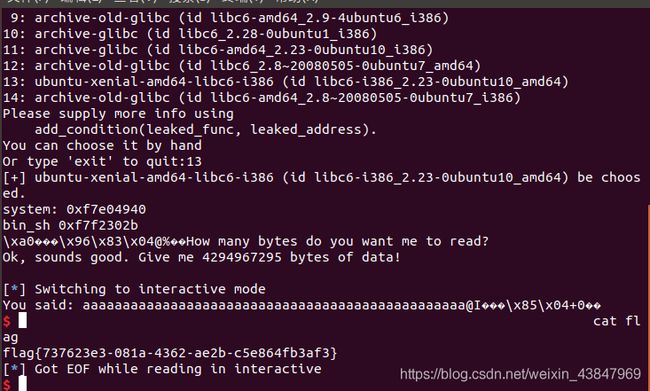
给大家的福利零基础入门对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。同时每个成长路线对应的板块都有配套的视频提供:因篇幅有限,仅展示部分资料网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。需要这份系统化资料的朋友,可以点击这里获取一个人可以走的很
- 如何打CTF竞赛?
jieyu1119
安全web安全网络
一、首先需要认识CTF竞赛1、什么是CTF竞赛?CTF(CaptureTheFlag)一般译作“夺旗赛”,在网络安全领域中指网络安全技术人员之间进行技术竞技的一种比赛形式。[11]通过各种攻击手法,获取服务器后寻找指定的字段,或者文件中某一个固定格式的字段,这个字段叫做Flag,其形式一般为Flag{xxxxxxxX},提交到裁判机就可以得分。2、竞赛模式解题模式(Jeopardy)在解题模式CT
- md5 collision(NUPT_CTF)
胖佳儿Clara
md5collision(NUPT_CTF)100http://120.24.86.145:9009/md5.php访问题目链接,得到提示inputa,而题目是md5collision,md5碰撞。根据==用法,0==字符串是成立的,从而可以绕过MD5检查。所以找一个md5是oe开头的值,get方式传参过去,PAYLOAD:120.24.86.145:9009/md5.php?a=s8789261
- rce漏洞测试
目录什么是RCE?漏洞介绍漏洞分类远程命令执行29关30关31关32~36关37关38关39关40关41关42关43关44关45关46~49关总结什么是RCE?漏洞介绍RCE漏洞,可以让攻击者直接向后台服务器远程注入操作系统命令或者代码,从而控制后台系统。RCE主要指远程代码执行和远程命令执行,CTFHub中将文件包含漏洞也看作RCE漏洞。漏洞分类远程命令执行远程代码执行文件包含漏洞实际上,RCE
- 重点句式114
俗世尘沙
今天的题目:Atthesametime,thepolicyaddressesnoneofthetrulythornyquestionsabouthomework.Ifthedistrictfindshomeworktobeunimportanttoitsstudents’academicachievement,itshouldmovetoreduceoreliminatetheassignment
- 【Oracle】Oracle 11g 中扩展表空间
瑞琪姐
大数据模块oracle数据库
在Oracle11g中扩展表空间是常见的数据库管理任务,通常有以下几种核心方法,操作步骤如下:一、扩展表空间常用方法方法1:调整现有数据文件大小(RESIZE)适用于磁盘空间充足,且当前数据文件未达上限的情况。--查询当前数据文件路径和大小SELECTfile_name,bytes/1024/1024AScurrent_size_mbFROMdba_data_filesWHEREtablespac
- 面试经验分享 | 成都某安全厂商渗透测试工程师
更多大厂面试题看我的主页或者专栏找我免费领取目录:所面试的公司:某安全厂商所在城市:成都面试职位:渗透测试工程师岗位面试过程:面试官的问题:1.平常在学校打CTF嘛,获奖情况讲下,以及你自己的贡献如何?2.内网渗透主要思路说一下吧?3.web打点过程中有没有遇到过waf?怎么绕过的4.现在给你一个站你会怎么做信息搜集?5.如何快速检测定位网站目录下的webshell呢?6.简单讲下反弹shell的
- C++ 设计模式:抽象工厂(Abstract Factory)
冀晓武
C++设计模式c++设计模式抽象工厂模式
链接:C++设计模式链接:C++设计模式-工厂方法链接:C++设计模式-原型模式链接:C++设计模式-建造者模式抽象工厂(AbstractFactory)是一种创建型设计模式,它提供一个接口,用于创建一系列相关或相互依赖的对象,而无需指定它们的具体类。抽象工厂模式通常用于创建一组相关的产品对象,例如不同类型的机器人和它们的配件。1.问题分析在某些情况下,我们需要创建一组相关或相互依赖的对象,但我们
- 23种设计模式
buyue__
设计模式
创建型模式1.单例模式(Singleton):确保有且只有一个对象被创建2.工厂方法模式(FactoryMethod):由子类决定要创建的具体类是哪一个3.抽象工厂模式(AbstractFactory):允许客户创建对象的家族,而无需指定他们的具体类4.原型模式(Prototype)5.建造者模式(Builder)结构型模式1.适配器模式(Adapter)2.装饰器模式(Decorator):包装
- 【Note】《深入理解Linux内核》Chapter 16 :深入理解 Linux 文件访问机制
CodeWithMe
读书笔记linuxlinux运维服务器
《深入理解Linux内核》Chapter16:深入理解Linux文件访问机制关键词:VFS、文件描述符、structfile、structinode、open、read、write、close、dentry、权限校验、file_operations、O_NOATIME、权限继承一、概览:Linux文件访问路径在Linux中,几乎一切资源都可以通过“文件”的形式访问。文件访问不仅涵盖传统的磁盘文件,
- BUUCTF在线评测-练习场-WebCTF习题[GYCTF2020]Blacklist1-flag获取、解析
解题思路打开靶场,跟之前有一题很像,应该是一个出题人,增强了靶场提示黑名单对于我来说太薄弱了,不是吗?上次题我记得用的是堆叠注入+预编译或者更改表名..这次估计把这两都过滤了没关系,我们还是常规思路起手,先判断闭合,输入1'1'error1064:YouhaveanerrorinyourSQLsyntax;checkthemanualthatcorrespondstoyourMariaDBserv
- CTFSHOW-WEB-36D杯
wyjcxyyy
前端android
给你shell这道题对我这个新手还是有难度的,花了不少时间。首先f12看源码,看到?view_source,点进去看源码location.href=\'./index.php\'');if(!isset($_GET['code'])){show_source(__FILE__);exit();}else{$code=$_GET['code'];if(!preg_match($secret_waf,
- DIDCTF-22蓝帽杯初赛
小丑001.
DIDCTF网络安全
手机取证_1题目描述现对一个苹果手机进行取证,请您对以下问题进行分析解答。627604C2-C586-48C1-AA16-FF33C3022159.PNG图片的分辨率是?(答案参考格式:1920×1080)注意:中间为乘号×,不是字母xflag:360×360手机取证_2题目描述姜总的快递单号是多少?(答案参考格式:abcABC123)flag:SF1142358694796网站取证_1题目描述据
- 一文讲清楚React Fiber
许先森森
Reactreact.jsjavascript前端ReactFiber
文章目录一文讲清楚ReactFiber1.基础概念1.1浏览器刷新率(帧)1.2JS执行栈1.3时间分片1.4链表2.ReactFiber是如何实现更新过程控制2.1任务拆分2.2挂起、恢复、终止2.2.1挂起2.2.2恢复2.2.3终止2.3任务具备优先级一文讲清楚ReactFiber1.基础概念1.1浏览器刷新率(帧)页面都是一帧一帧绘制出来的,浏览器大多是60Hz(60帧/s),每一帧耗时1
- 抽象工厂模式在React Hooks中的应用
抽象工厂模式的概念抽象工厂模式是所有形态的工厂模式中最为抽象和最具一般性的一种形态。当有多个抽象角色时会使用这种模式。它为创建一组相关或相互依赖的对象提供一个接口,而且无需指定它们的具体类。在抽象工厂模式中有几个重要角色:抽象工厂(AbstractFactory):它声明了一组用于创建一族产品的方法,每一个方法对应一种产品。例如,在一个图形绘制系统中,可能有一个抽象工厂接口ShapeFactory
- 已解决:React在Chrome F12 调试台断点调试中跳过node_modules内部黑盒
gzzeason
react.jschromejavascript浏览器控制台React源码
一、debugger代码如下当我在探究根节点和容器源码时候,将debugger代码添加在如下位置:importReactfrom'react';//用到JSXimportReactDOMfrom'react-dom/client';importAppfrom'./App';constparent_node=document.getElementById('root');//获取根节点debugge
- WinUI3入门16:Order自定义排序
初级代码游戏的专栏介绍与文章目录-CSDN博客我的github:codetoys,所有代码都将会位于ctfc库中。已经放入库中我会指出在库中的位置。这些代码大部分以Linux为目标但部分代码是纯C++的,可以在任何平台上使用。源码指引:github源码指引_初级代码游戏的博客-CSDN博客C#是我多年以来的业余爱好,新搞的东西能用C#的就用C#了。接上一篇继续研究排序问题。上一篇:WinUI3入门
- Ubuntu 20.04安装FlClash
墨玦子
ubuntulinux运维
1、下载好安装包使用sudodpkg-ixxx.deb安装好flclash2、终端输入FlClash,会遇到如下的问题,并附上解决方法(1)FlClash:errorwhileloadingsharedlibraries:libkeybinder-3.0.so.0:cannotopensharedobjectfile:Nosuchfileordirectory解决方法:sudoapt-getins
- BUUCTF在线评测-练习场-WebCTF习题[网鼎杯 2020 青龙组]AreUSerialz1-flag获取、解析
码农12138号
BUUCTF网络安全web安全CTF反序列化漏洞
解题思路打开靶场,贴有源码process();}publicfunctionprocess(){if($this->op=="1"){$this->write();}elseif($this->op=="2"){$res=$this->read();$this->output($res);}else{$this->output("BadHacker!");}}privatefunctionwrit
- Vite 常用配置详解
啃火龙果的兔子
开发DEMO前端
Vite是一个现代化的前端构建工具,相比Webpack具有更快的开发服务器启动和热更新速度。以下是Vite的常用配置项及其说明:1.基础配置(vite.config.js)import{defineConfig}from'vite'importvuefrom'@vitejs/plugin-vue'importreactfrom'@vitejs/plugin-react'exportdefaultd
- 利用systemd启动部署在服务器上的web应用
不是吧这都有重名
遇到的问题服务器前端运维
0.背景系统环境:Ubuntu22.04web应用情况:前后端分类,前端采用react,后端采用fastapi1.具体配置1.1前端配置开发态运行(启动命令是npmrundev),创建systemd服务文件sudonano/etc/systemd/system/frontend.service内容如下:[Unit]Description=ReactFrontendDevServerAfter=ne
- spring面试题【持续更新ing】
spring面试题一、什么是循环依赖(高频)?二、Spring如何解决循环依赖?三、Spring都有哪些重要的模块?四、什么是SpringIOC?五、SpringIOC有什么好处?六、Spring中的DI是什么?七、什么是SpringBean?八、Spring中的BeanFactory是什么?九、Spring中的FactoryBean是什么?十、Spring中的ObjectFactory是什么?十
- CTF-reverse逆向分析解题常用脚本汇总
晴友读钟
#逆向ctfreverse
注:本篇用于记录一些CTF-reverse中可能用上的脚本,脚本都来源于博主解出某道题后留下,如果遇上类似的题目,根据脚本中注释的提示更改对应的密文密钥或条件即可快速解题!持续更新!!点个收藏关注不迷路~常见解密系列这块是烂大街的各种加密,可以说这里任何一个加密都八成会出现在题目中的脚本只是模板,重点是学会找到密文密钥并套入进去,因此需要对脚本的原理(比如调用函数的方式和密文密钥的格式之类)稍微有
- Linux内核IPv4路由子系统深度剖析:FIB前端实现与设计原理
109702008
编程#C语言网络linux网络人工智能
深入理解Linux网络栈的核心组件:路由表管理、地址验证与事件处理机制引言在Linux网络栈中,IPv4转发信息库(FIB)是决定数据包传输路径的核心子系统。fib_frontend.c作为FIB的前端实现,承担着路由表管理、用户接口交互和网络事件响应等关键任务。本文将深入剖析这一关键文件的实现原理,揭示Linux路由机制的设计哲学。一、FIB前端整体架构/*核心数据结构*/structfib_t
- 前端手写题(二)
目录一、new二、call三、apply四、bind五、create一、newnew的核心作用:基于构造函数创建实例,绑定原型链,初始化对象属性。底层四步:创建空对象→绑定原型→执行构造函数→处理返回值functionobjectFactory(constructor,...args){ //严格校验构造函数 if(typeofconstructor!=='function'){ throwne
- springcloud feign调用get请求变成了post请求解决
只想要搞钱
springcloudjavaspring
1.feign调用get请求,feignService定义的get请求的参数是一个对象,如下图,调用另一个服务时,提示405,变成了post请求@GetMapping("/trainContact/queryContactForCurrentUser")Result>queryContactForCurrentUser(TrainContactPageDTOpageDTO);2.解决,对象前加一个
- Feign服务调用,Get、Post请求
目录GET请求POST请求GET请求Feign客户端@FeignClient("lik-dr-product")publicinterfaceProductFeign{/***从请求路径获取值,需要使用@PathVariable注解*/@GetMapping("/product/findById/{id}")ProductfindById(@PathVariable("id")Longid);/*
- 设计模式整理
分类模式名称简要说明创建型Singleton(单例)保证一个类只有一个实例,并提供全局访问点创建型FactoryMethod(工厂方法)定义创建对象的接口,由子类决定实例化哪一个类创建型AbstractFactory(抽象工厂)提供一组相关或相互依赖对象的接口创建型Builder(建造者)分步骤创建复杂对象,将构建与表示分离创建型Prototype(原型)通过复制已有实例创建新对象结构型Adapt
- 关于旗正规则引擎下载页面需要弹窗保存到本地目录的问题
何必如此
jsp超链接文件下载窗口
生成下载页面是需要选择“录入提交页面”,生成之后默认的下载页面<a>标签超链接为:<a href="<%=root_stimage%>stimage/image.jsp?filename=<%=strfile234%>&attachname=<%=java.net.URLEncoder.encode(file234filesourc
- 【Spark九十八】Standalone Cluster Mode下的资源调度源代码分析
bit1129
cluster
在分析源代码之前,首先对Standalone Cluster Mode的资源调度有一个基本的认识:
首先,运行一个Application需要Driver进程和一组Executor进程。在Standalone Cluster Mode下,Driver和Executor都是在Master的监护下给Worker发消息创建(Driver进程和Executor进程都需要分配内存和CPU,这就需要Maste
- linux上独立安装部署spark
daizj
linux安装spark1.4部署
下面讲一下linux上安装spark,以 Standalone Mode 安装
1)首先安装JDK
下载JDK:jdk-7u79-linux-x64.tar.gz ,版本是1.7以上都行,解压 tar -zxvf jdk-7u79-linux-x64.tar.gz
然后配置 ~/.bashrc&nb
- Java 字节码之解析一
周凡杨
java字节码javap
一: Java 字节代码的组织形式
类文件 {
OxCAFEBABE ,小版本号,大版本号,常量池大小,常量池数组,访问控制标记,当前类信息,父类信息,实现的接口个数,实现的接口信息数组,域个数,域信息数组,方法个数,方法信息数组,属性个数,属性信息数组
}
&nbs
- java各种小工具代码
g21121
java
1.数组转换成List
import java.util.Arrays;
Arrays.asList(Object[] obj); 2.判断一个String型是否有值
import org.springframework.util.StringUtils;
if (StringUtils.hasText(str)) 3.判断一个List是否有值
import org.spring
- 加快FineReport报表设计的几个心得体会
老A不折腾
finereport
一、从远程服务器大批量取数进行表样设计时,最好按“列顺序”取一个“空的SQL语句”,这样可提高设计速度。否则每次设计时模板均要从远程读取数据,速度相当慢!!
二、找一个富文本编辑软件(如NOTEPAD+)编辑SQL语句,这样会很好地检查语法。有时候带参数较多检查语法复杂时,结合FineReport中生成的日志,再找一个第三方数据库访问软件(如PL/SQL)进行数据检索,可以很快定位语法错误。
- mysql linux启动与停止
墙头上一根草
如何启动/停止/重启MySQL一、启动方式1、使用 service 启动:service mysqld start2、使用 mysqld 脚本启动:/etc/inint.d/mysqld start3、使用 safe_mysqld 启动:safe_mysqld&二、停止1、使用 service 启动:service mysqld stop2、使用 mysqld 脚本启动:/etc/inin
- Spring中事务管理浅谈
aijuans
spring事务管理
Spring中事务管理浅谈
By Tony Jiang@2012-1-20 Spring中对事务的声明式管理
拿一个XML举例
[html]
view plain
copy
print
?
<?xml version="1.0" encoding="UTF-8"?>&nb
- php中隐形字符65279(utf-8的BOM头)问题
alxw4616
php中隐形字符65279(utf-8的BOM头)问题
今天遇到一个问题. php输出JSON 前端在解析时发生问题:parsererror.
调试:
1.仔细对比字符串发现字符串拼写正确.怀疑是 非打印字符的问题.
2.逐一将字符串还原为unicode编码. 发现在字符串头的位置出现了一个 65279的非打印字符.
- 调用对象是否需要传递对象(初学者一定要注意这个问题)
百合不是茶
对象的传递与调用技巧
类和对象的简单的复习,在做项目的过程中有时候不知道怎样来调用类创建的对象,简单的几个类可以看清楚,一般在项目中创建十几个类往往就不知道怎么来看
为了以后能够看清楚,现在来回顾一下类和对象的创建,对象的调用和传递(前面写过一篇)
类和对象的基础概念:
JAVA中万事万物都是类 类有字段(属性),方法,嵌套类和嵌套接
- JDK1.5 AtomicLong实例
bijian1013
javathreadjava多线程AtomicLong
JDK1.5 AtomicLong实例
类 AtomicLong
可以用原子方式更新的 long 值。有关原子变量属性的描述,请参阅 java.util.concurrent.atomic 包规范。AtomicLong 可用在应用程序中(如以原子方式增加的序列号),并且不能用于替换 Long。但是,此类确实扩展了 Number,允许那些处理基于数字类的工具和实用工具进行统一访问。
- 自定义的RPC的Java实现
bijian1013
javarpc
网上看到纯java实现的RPC,很不错。
RPC的全名Remote Process Call,即远程过程调用。使用RPC,可以像使用本地的程序一样使用远程服务器上的程序。下面是一个简单的RPC 调用实例,从中可以看到RPC如何
- 【RPC框架Hessian一】Hessian RPC Hello World
bit1129
Hello world
什么是Hessian
The Hessian binary web service protocol makes web services usable without requiring a large framework, and without learning yet another alphabet soup of protocols. Because it is a binary p
- 【Spark九十五】Spark Shell操作Spark SQL
bit1129
shell
在Spark Shell上,通过创建HiveContext可以直接进行Hive操作
1. 操作Hive中已存在的表
[hadoop@hadoop bin]$ ./spark-shell
Spark assembly has been built with Hive, including Datanucleus jars on classpath
Welcom
- F5 往header加入客户端的ip
ronin47
when HTTP_RESPONSE {if {[HTTP::is_redirect]}{ HTTP::header replace Location [string map {:port/ /} [HTTP::header value Location]]HTTP::header replace Lo
- java-61-在数组中,数字减去它右边(注意是右边)的数字得到一个数对之差. 求所有数对之差的最大值。例如在数组{2, 4, 1, 16, 7, 5,
bylijinnan
java
思路来自:
http://zhedahht.blog.163.com/blog/static/2541117420116135376632/
写了个java版的
public class GreatestLeftRightDiff {
/**
* Q61.在数组中,数字减去它右边(注意是右边)的数字得到一个数对之差。
* 求所有数对之差的最大值。例如在数组
- mongoDB 索引
开窍的石头
mongoDB索引
在这一节中我们讲讲在mongo中如何创建索引
得到当前查询的索引信息
db.user.find(_id:12).explain();
cursor: basicCoursor 指的是没有索引
&
- [硬件和系统]迎峰度夏
comsci
系统
从这几天的气温来看,今年夏天的高温天气可能会维持在一个比较长的时间内
所以,从现在开始准备渡过炎热的夏天。。。。
每间房屋要有一个落地电风扇,一个空调(空调的功率和房间的面积有密切的关系)
坐的,躺的地方要有凉垫,床上要有凉席
电脑的机箱
- 基于ThinkPHP开发的公司官网
cuiyadll
行业系统
后端基于ThinkPHP,前端基于jQuery和BootstrapCo.MZ 企业系统
轻量级企业网站管理系统
运行环境:PHP5.3+, MySQL5.0
系统预览
系统下载:http://www.tecmz.com
预览地址:http://co.tecmz.com
各种设备自适应
响应式的网站设计能够对用户产生友好度,并且对于
- Transaction and redelivery in JMS (JMS的事务和失败消息重发机制)
darrenzhu
jms事务承认MQacknowledge
JMS Message Delivery Reliability and Acknowledgement Patterns
http://wso2.com/library/articles/2013/01/jms-message-delivery-reliability-acknowledgement-patterns/
Transaction and redelivery in
- Centos添加硬盘完全教程
dcj3sjt126com
linuxcentoshardware
Linux的硬盘识别:
sda 表示第1块SCSI硬盘
hda 表示第1块IDE硬盘
scd0 表示第1个USB光驱
一般使用“fdisk -l”命
- yii2 restful web服务路由
dcj3sjt126com
PHPyii2
路由
随着资源和控制器类准备,您可以使用URL如 http://localhost/index.php?r=user/create访问资源,类似于你可以用正常的Web应用程序做法。
在实践中,你通常要用美观的URL并采取有优势的HTTP动词。 例如,请求POST /users意味着访问user/create动作。 这可以很容易地通过配置urlManager应用程序组件来完成 如下所示
- MongoDB查询(4)——游标和分页[八]
eksliang
mongodbMongoDB游标MongoDB深分页
转载请出自出处:http://eksliang.iteye.com/blog/2177567 一、游标
数据库使用游标返回find的执行结果。客户端对游标的实现通常能够对最终结果进行有效控制,从shell中定义一个游标非常简单,就是将查询结果分配给一个变量(用var声明的变量就是局部变量),便创建了一个游标,如下所示:
> var
- Activity的四种启动模式和onNewIntent()
gundumw100
android
Android中Activity启动模式详解
在Android中每个界面都是一个Activity,切换界面操作其实是多个不同Activity之间的实例化操作。在Android中Activity的启动模式决定了Activity的启动运行方式。
Android总Activity的启动模式分为四种:
Activity启动模式设置:
<acti
- 攻城狮送女友的CSS3生日蛋糕
ini
htmlWebhtml5csscss3
在线预览:http://keleyi.com/keleyi/phtml/html5/29.htm
代码如下:
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title>攻城狮送女友的CSS3生日蛋糕-柯乐义<
- 读源码学Servlet(1)GenericServlet 源码分析
jzinfo
tomcatWebservlet网络应用网络协议
Servlet API的核心就是javax.servlet.Servlet接口,所有的Servlet 类(抽象的或者自己写的)都必须实现这个接口。在Servlet接口中定义了5个方法,其中有3个方法是由Servlet 容器在Servlet的生命周期的不同阶段来调用的特定方法。
先看javax.servlet.servlet接口源码:
package
- JAVA进阶:VO(DTO)与PO(DAO)之间的转换
snoopy7713
javaVOHibernatepo
PO即 Persistence Object VO即 Value Object
VO和PO的主要区别在于: VO是独立的Java Object。 PO是由Hibernate纳入其实体容器(Entity Map)的对象,它代表了与数据库中某条记录对应的Hibernate实体,PO的变化在事务提交时将反应到实际数据库中。
实际上,这个VO被用作Data Transfer
- mongodb group by date 聚合查询日期 统计每天数据(信息量)
qiaolevip
每天进步一点点学习永无止境mongodb纵观千象
/* 1 */
{
"_id" : ObjectId("557ac1e2153c43c320393d9d"),
"msgType" : "text",
"sendTime" : ISODate("2015-06-12T11:26:26.000Z")
- java之18天 常用的类(一)
Luob.
MathDateSystemRuntimeRundom
System类
import java.util.Properties;
/**
* System:
* out:标准输出,默认是控制台
* in:标准输入,默认是键盘
*
* 描述系统的一些信息
* 获取系统的属性信息:Properties getProperties();
*
*
*
*/
public class Sy
- maven
wuai
maven
1、安装maven:解压缩、添加M2_HOME、添加环境变量path
2、创建maven_home文件夹,创建项目mvn_ch01,在其下面建立src、pom.xml,在src下面简历main、test、main下面建立java文件夹
3、编写类,在java文件夹下面依照类的包逐层创建文件夹,将此类放入最后一级文件夹
4、进入mvn_ch01
4.1、mvn compile ,执行后会在