ENSP-----防火墙NAT策略
一.NAT概述
NAT的分类
- NAT no-PAT:类似思科的动态转化,多对多,不转化端口,不能解约公网IP地址,实际应用场景使用较少,主要适用于需要上网的用户较少,而公网IP地址有足够多的场景
- NAPT(网络地址端口转换):类似于思科的PAT,NATP即转换报文的源地址,又转换源端口。转换后地址不能是外网接口IP地址,属于多对多或者多对一的转换,可以节省公网IP地址,使用场景较多
- Easy-IP(出接口地址):因其转换方式非常简单,所有也被称为Easy-IP、和NAPT一样,即转换源IP地址,又转换源端口。区别是出接口地址方式转换后的地址只能是NAT设备外网接口所配置的IP地址,属于多对一转换,可以节约IP地址
- NAT Server:静态一对一发布,主要用于内部服务器需要对internet提供服务时使用
- Smart NAT(智能转换):与源IP地址,源端口和协议类型有关的一种转换,将源IP地址和源端口转换为固定公网IP地址和端口,能解决一些特殊应用在普遍NAT中无法实现的问题
- 三元组NAT:与源地址、源端口和协议类型有关的一种转换,将源IP地址和源端口转换为固定公网IP地址和端口,能解决一些特殊应用在普遍NAT中无法实现的问题,主要应用外部访问局域网的一些P2P应用
黑洞路由的产生与分析
- 在特定的NAT转换时,可能会产生环路及无效ARP,关于其如何产生,大概就是,在有些NAT的转换方式中,是为了解决内网连接Internet,而映射出了一个公有IP,那么,若此时有人通过internet来访问这个映射出来的公有IP,就会产生这两种情况。解决这个问题的办法就是配置黑洞路由(将internet主动访问映射出来的地址流量指定到空接口null0)
- 黑洞路由的应用场景
| NAT类型 | 描述 | 是否配置黑洞路由 |
| NAT no-PAT | 当公网用户访问转换后地址时产生环路或者产生ARP报文 | 是 |
| NAT PAT | 当公网用户访问转换后地址时产生环路或者产生ARP报文 | 是 |
| Easy-ip(出口地址) | 转换后的地址就是外网接口的地址,公网用户访问该地址被防火墙接收(策略允许)或丢弃(策略不允许),不产生环路 | 否 |
| NAT Server (粗泛) | 当公网用户访问映射地址时直接转发给内部服务器 | 否
|
| NAT Server (精细) | 当公网用户访问映射地址时产生环路或者产生ARP报文 | 是 |
Server-map表
- 状态化防火墙中会有一张表叫做会话表,用来记录的是内网访问外网时的一个连接信息,当外网返回的数据匹配到会话表的记录时,直接放行相关返回流量
- 会话表与server-map表的区别
- 会话表记录的是连接信息,包括连接状态
- server-map表记录的不是当前的连接信息,而是通过分析当前连接的报文后得到的信息,该信息用来解决接下来的数据流通过防火墙的问题。可以将server-map表的作用理解为通过提前计划解决将来的问题,如FTP这种的多端口协议,在从一开始的三次握手,到最后完成数据传输,其过程中,可能端口会发生改变等问题,server-map正好可以解决这种问题
- 然而在NAT中也需要这个server-map表,就是在有数据流量通过NAT的方式穿越防火墙时,server-map表会记录其源地址和转换后地址的对应关系,从而使后续流量可以不用查看NAT策略,直接匹配到server-map表,从而实现高效的NAT转换。若用户通过互联网转换后的地址时,也可以匹配到server-map表,从而高效的将数据发到内网真实主机(必须保证安全策略允许通过)
- server-map表不用手动配置,是自动生成的,在NAT中,不是所有的表都可以生成server-map表,其中有:NAT no-PAT动态生成server-map表,也就是只有流量通过才会,自动生成server-map表,并且不是长期存在的。NAT Server静态生成server-map表,意味着表中的内容长期存在。NAPT以及出口地址方式,不会生成Server-map表
- 当防火墙上配置某些NAT后,在防火墙上会生成Server-map,默认生成两个Server-map条目,分别是正向条目和反向条目(Reverse)
- 正向条目:携带端口信息,用来使internet用户访问内网中的服务器时直接通过server-map表来进行目标地址转换
- 反向条目:不携带端口信息,且目标地址是任意的,用来使服务器可以访问internet
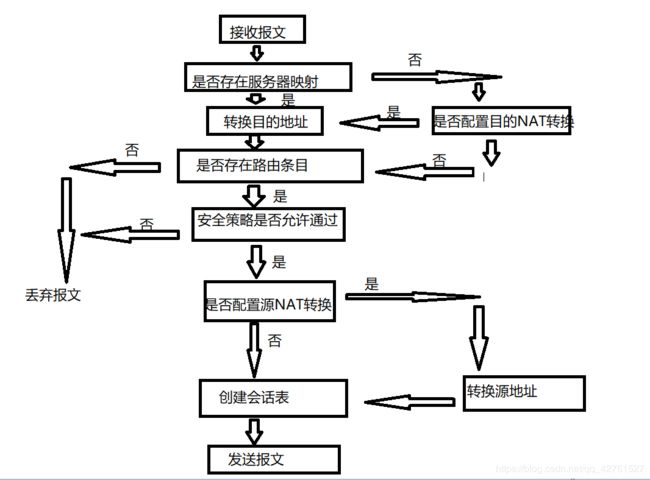
NAT对报文处理流程图
二.关于防火墙NAT的具体实例
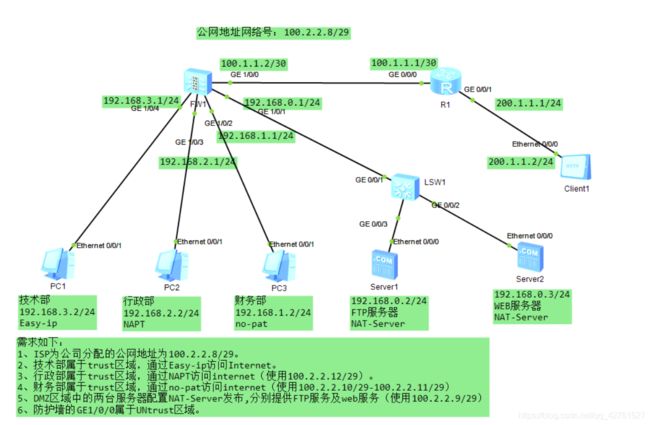
网络拓扑图
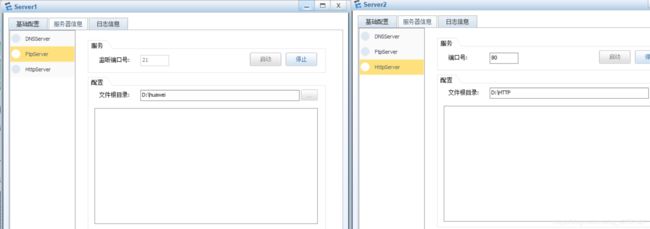
服务器的配置
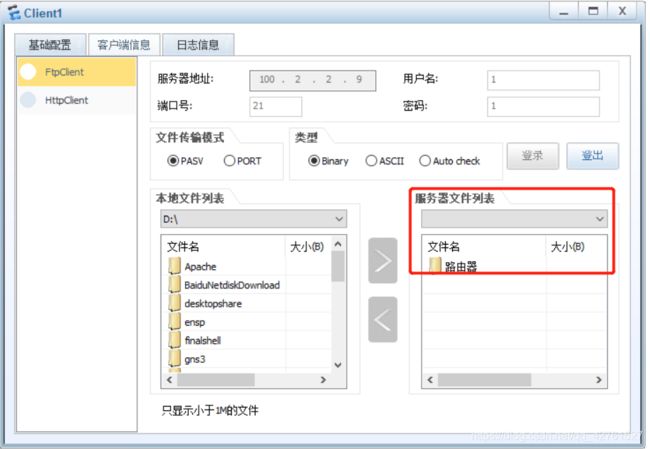
- 分别在FTP、WEB服务器中配置文件根目录,设置文件在该目录中,便于client登录查询
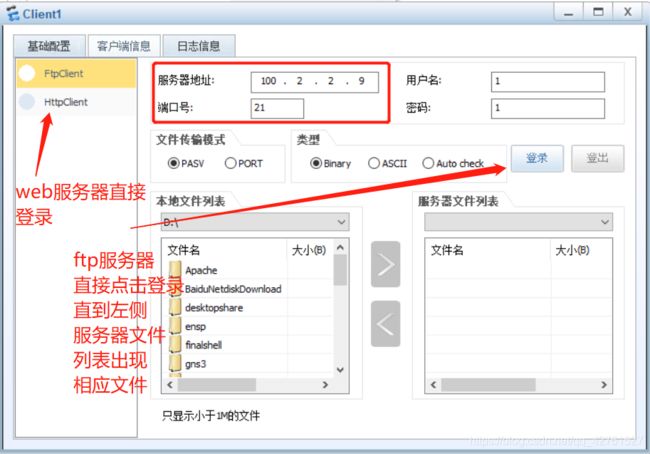
- 在Client配置服务器地址
FW1的详细配置
- 按照拓扑图配置接口地址
sys
[USG6000V1]in g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip add 100.1.1.2 30
[USG6000V1-GigabitEthernet1/0/0]in g1/0/4
[USG6000V1-GigabitEthernet1/0/4]ip add 192.168.3.1 24
[USG6000V1-GigabitEthernet1/0/4]in g1/0/3
[USG6000V1-GigabitEthernet1/0/3]ip add 192.168.2.1 24
[USG6000V1-GigabitEthernet1/0/3]in g1/0/2
[USG6000V1-GigabitEthernet1/0/2]ip add 192.168.1.1 24
[USG6000V1-GigabitEthernet0/0/0]in g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip add 192.168.0.1 24
[USG6000V1-GigabitEthernet1/0/1]quit - 按照需求将各个接口添加如各个信任区
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add in g1/0/4
[USG6000V1-zone-trust]add in g1/0/3
[USG6000V1-zone-trust]add in g1/0/2
[USG6000V1-zone-trust]quit
[USG6000V1]firewall zone dmz
[USG6000V1-zone-dmz]add in g1/0/1
[USG6000V1-zone-dmz]quit
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add in g1/0/0- 配置到Client的静态路由
[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 100.1.1.1- 配置技术部的防火墙NAT规则,easy-ip类型的NAT不会产生server-map
##配置安全策略:
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name easy ####定义安全策略名字
[USG6000V1-policy-security-rule-easy]source-zone trust ####源区域为trust
[USG6000V1-policy-security-rule-easy]destination-zone untrust ####目标区域为untrust
[USG6000V1-policy-security-rule-easy]action permit ####动作为允许
[USG6000V1-policy-security-rule-easy]quit
[USG6000V1-policy-security]quit
##配置NAT策略:
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name easypolicy ####定义NAT策略名字
[USG6000V1-policy-nat-rule-easypolicy]source-address 192.168.3.0 24 ####定义源地址
[USG6000V1-policy-nat-rule-easypolicy]source-zone trust ####定义源区域
[USG6000V1-policy-nat-rule-easypolicy]destination-zone untrust ####定义目标区域
[USG6000V1-policy-nat-rule-easypolicy]action source-nat easy-ip ####配置出接口方式
[USG6000V1-policy-nat-rule-easypolicy]quit
[USG6000V1-policy-nat]quit- 配置行政部的防火墙NAT规则,由于在上面已经配置了安全策略所以以下不需要再配置
###配置NAT地址组,地址组中的地址对应的是公网地址100.2.2.12/29。
[USG6000V1]nat address-group napt ####定义nat地址组名
[USG6000V1-address-group-napt]section 0 100.2.2.12 ####定义组中的地址
[USG6000V1-address-group-napt]mode pat ####配置为NAPT方式
[USG6000V1-address-group-napt]quit
###配置NAT策略
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name napt ####自定义nat策略的组名
[USG6000V1-policy-nat-rule-napt]source-address 192.168.2.0 24 ####定义需要转换的源地址
[USG6000V1-policy-nat-rule-napt]source-zone trust ####定义源区域
[USG6000V1-policy-nat-rule-napt]destination-zone untrust ####定义目标区域
[USG6000V1-policy-nat-rule-napt]action source-nat address-group napt ####关联地址组
###NAPT的NAT类型要配置黑洞路由,所以要针对转换后的全局地址100.2.2.12/32配置黑洞路由。
[USG6000V1] ip route-static 100.2.2.12 32 NULL 0 - 配置财务部的防火墙NAT规则
###配置NAT地址组,地址组中的地址对应的是公网地址100.2.2.10--100.2.2.11:
[USG6000V1]nat address-group natnopat ####定义nat地址组名
[USG6000V1-address-group-natnopat]section 0 100.2.2.10 100.2.2.11 ####定义组中的地址
[USG6000V1-address-group-natnopat]mode no-pat local ####配置为NAT No-PAT方式
[USG6000V1-address-group-natnopat]quit
###配置NAT策略:
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name nopat ####自定义nat策略的组名
[USG6000V1-policy-nat-rule-nopat]source-address 192.168.1.0 24 ####定义需要转换的源地址
[USG6000V1-policy-nat-rule-nopat]source-zone trust ####定义源区域
[USG6000V1-policy-nat-rule-nopat]destination-zone untrust ####定义目标区域
[USG6000V1-policy-nat-rule-nopat]action source-nat address-group natnopat ####关联地址组
[USG6000V1-policy-nat-rule-nopat]quit
[USG6000V1-policy-nat]quit
###针对转换后的全局地址(NAT地址组中的地址)配置黑洞路由:
[USG6000V1]ip route-static 100.2.2.10 32 NULL 0
[USG6000V1]ip route-static 100.2.2.11 32 NULL 0- 配置DMZ区域中的两台服务器的防火墙NAT规则
###配置安全策略:
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name todmz
[USG6000V1-policy-security-rule-todmz]source-zone untrust
[USG6000V1-policy-security-rule-todmz]destination-zone dmz
[USG6000V1-policy-security-rule-todmz]destination-address 192.168.0.0 24
[USG6000V1-policy-security-rule-todmz]service ftp
[USG6000V1-policy-security-rule-todmz]service http
[USG6000V1-policy-security-rule-todmz]action permit
###配置NAT server:
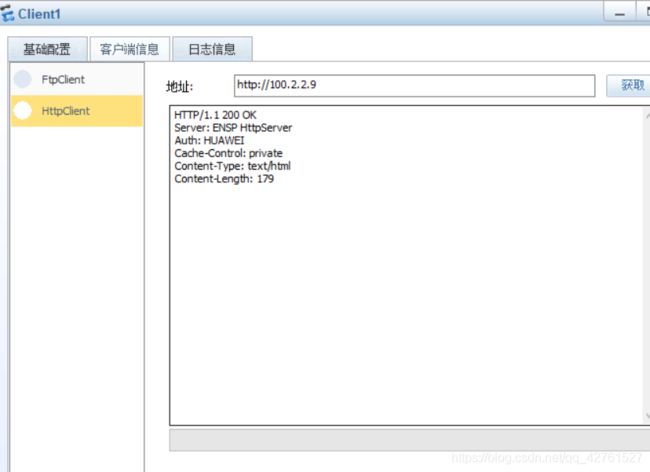
[USG6000V1]nat server ftp protocol tcp global 100.2.2.9 21 inside 192.168.0.2 21
[USG6000V1]nat server http protocol tcp global 100.2.2.9 80 inside 192.168.0.3 80
- 查看server-map表和会话表
[USG6000V1]dis firewall server-map
2020-02-12 09:31:47.960
Current Total Server-map : 4
Type: Nat Server, ANY -> 100.2.2.9:80[192.168.0.3:80], Zone:---, protocol:tc
p
Vpn: public -> public
Type: Nat Server, ANY -> 100.2.2.9:21[192.168.0.2:21], Zone:---, protocol:tc
p
Vpn: public -> public
Type: Nat Server Reverse, 192.168.0.2[100.2.2.9] -> ANY, Zone:---, protocol:
tcp
Vpn: public -> public, counter: 1
Type: Nat Server Reverse, 192.168.0.3[100.2.2.9] -> ANY, Zone:---, protocol:
tcp
Vpn: public -> public, counter: 1
[USG6000V1]dis firewall se tab
2020-02-12 09:49:58.400
Current Total Sessions : 3
ftp VPN: public --> public 200.1.1.2:2054 +-> 100.2.2.9:21[192.168.0.2:21]
ftp VPN: public --> public 200.1.1.2:2056 +-> 100.2.2.9:21[192.168.0.2:21]
ftp VPN: public --> public 200.1.1.2:2052 +-> 100.2.2.9:21[192.168.0.2:21]
[FW1]
注:由于老化时间,会导致会话表消失
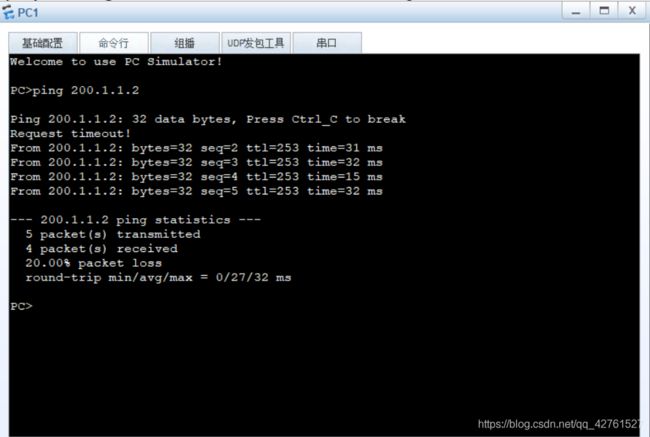
实验验证
- 在技术部处pingclient
- 在client处访问服务器