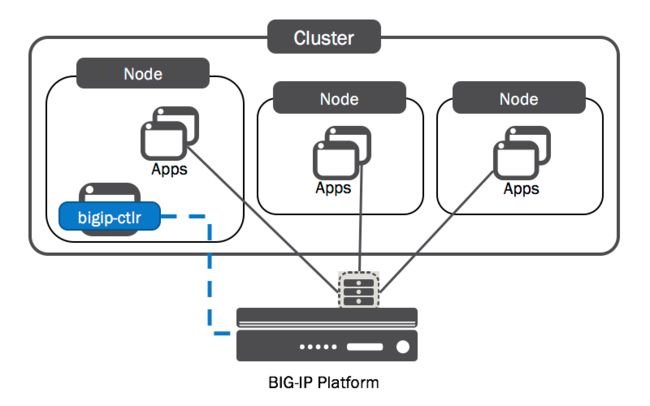
使用F5与Openshift集成目的
外部流量访问应用时,通过F5 BIG-IP硬件设备直接代理到集群中的Pod。
这样做的好处,很明显。
- 使用硬件负载均衡器替换掉软件负载均衡器,提高性能。
- F5有更灵活的配置,可以实现更复杂的流量控制
Openshift操作
Openshift通过BIG-IP Controller来控制BIG-IP设备。由于Openshift是基于Kubernetes的,所以它们使用同一个Controller(k8s-bigip-ctlr)。BIG-IP Controller为集群中的应用配置BIG-IP对象,提供南北流量的服务。
BIG-IP Controller有两种方式来使用F5 BIG-IP设备
- 为Openshift中的Service提供代理流量
- 为Openshift中的Route提供代理流量
为Openshift中的Service提供代理流量(不介绍具体部署操作)
这种方式,我们测试下来发现,需要为对外提供服务的Service绑定到F5的不同端口,同时外部访问应用时需要指定端口号。如:
app1.openshift.example.com:8000, app2.openshift.example.com:8001,app3.openshift.example.com:8002,其中端口号不能重复。
- 这种方式在真正使用时不能满足业务需求,除非在F5的前面再加一层代理,这又增加了架构的复杂性。
- 理想的状态是,所以的App应用的HTTP请求都访问F5的80端口,而HTTPS的请求访问F5的443端口,根据请求的域名路由到对应的Pool中(每个Pool是一个Service下的所有Pod的列表)。
- 很高兴告诉大家,第二种方式能够满足上面的需求
为Openshift中的Route提供代理流量
使用BIG-IP作为Openshift的Router,能实现以下功能:
- 为Services创建BIG-IP本地流量规则
- 提供HTTP/HTTPS路由
- 为Route资源添加BIG-IP健康检查
本文只介绍,如何使用F5提供HTTP/HTTPS路由。这也是最核心的部分。
部署环境版本:
2台F5:v13 192.168.200.82 192.168.200.83
Openshift集群: v3.9.1
创建新的HostSub
Openshift
# hostsubnet.yml
apiVersion: v1
kind: HostSubnet
metadata:
name: f5-bigip-node01
annotations:
pod.network.openshift.io/fixed-vnid-host: "0"
pod.network.openshift.io/assign-subnet: "true"
# provide a name for the node that will serve as BIG-IP's entry into the cluster
host: f5-bigip-node01
# The hostIP address will be the BIG-IP interface address routable to the
# OpenShift Origin nodes.
# This address is the BIG-IP VTEP in the SDN's VXLAN.
hostIP: 192.168.200.82
---
apiVersion: v1
kind: HostSubnet
metadata:
name: f5-bigip-node02
annotations:
pod.network.openshift.io/fixed-vnid-host: "0"
pod.network.openshift.io/assign-subnet: "true"
# provide a name for the node that will serve as BIG-IP's entry into the cluster
host: f5-bigip-node02
# The hostIP address will be the BIG-IP interface address routable to the
# OpenShift Origin nodes.
# This address is the BIG-IP VTEP in the SDN's VXLAN.
hostIP: 192.168.200.83
---
apiVersion: v1
kind: HostSubnet
metadata:
name: f5-bigip-float
annotations:
pod.network.openshift.io/fixed-vnid-host: "0"
pod.network.openshift.io/assign-subnet: "true"
# provide a name for the node that will serve as BIG-IP's entry into the cluster
host: f5-bigip-float
# The hostIP address will be the BIG-IP interface address routable to the
# OpenShift Origin nodes.
# This address is the BIG-IP VTEP in the SDN's VXLAN.
hostIP: 192.168.200.84
oc create -f hostsubnet.yml
查看执行结果
[root@master01 ~]# oc get hostsubnet
NAME HOST HOST IP SUBNET EGRESS IPS
f5-bigip-float f5-bigip-float 192.168.200.84 10.128.6.0/23 []
f5-bigip-node01 f5-bigip-node01 192.168.200.82 10.129.6.0/23 []
f5-bigip-node02 f5-bigip-node02 192.168.200.83 10.130.4.0/23 []
master01.example.com master01.example.com 192.168.200.1 10.130.0.0/23 []
master02.example.com master02.example.com 192.168.200.2 10.128.0.0/23 []
master03.example.com master03.example.com 192.168.200.3 10.128.2.0/23 []
node01.example.com node01.example.com 192.168.200.21 10.129.0.0/23 []
node02.example.com node02.example.com 192.168.200.22 10.131.0.0/23 []
router01.example.com router01.example.com 192.168.200.11 10.129.2.0/23 []
router02.example.com router02.example.com 192.168.200.12 10.130.2.0/23 []
创建一个VXLAN profile
F5
在F5的TMOS终端,创建一个多点模式的vxlan
create /net tunnels vxlan openshift_vxlan flooding-type multipoint
创建一个VXLAN Tunnel
F5
Local Address使用vip: 192.168.200.84
Secondary Address使用F5的设备IP:node1 192.168.200.82, node2 192.168.200.83
在F5 Node1上的TMOS创建Tunnel
create /net tunnels tunnel key 0 profile openshift_vxlan local-address 192.168.200.84 secondary-address 192.168.200.82 traffic-group traffic-group-1
在F5 Node2上的TMOS创建Tunnel
create /net tunnels tunnel key 0 profile openshift_vxlan local-address 192.168.200.84 secondary-address 192.168.200.83 traffic-group traffic-group-1
在每个F5设备VXLAN中创建Self IP
F5
IP为设备对应在Openshift的HostSubnet下的一个IP(只要在对应的HostSubnet下就OK)
在F5 Node1中创建Self IP
create /net self 10.129.6.82/14 allow-service none vlan openshift_vxlan
在F5 Node2中创建Self IP
create /net self 10.130.4.83/14 allow-service none vlan openshift_vxlan
在当前主F5设备的VXLAN下创建Floating IP
F5
如:当前主F5设备为node1,那Floating IP为主设备所在的HostSubnet下。
create /net self 10.128.6.84/14 allow-service none traffic-group traffic-group-1 vlan openshift_vxlan
创建一个新的Partition
F5
create auth partition OpenShift
创建访问F5 BIG-IP的私钥
Openshift
oc create secret generic bigip-login --from-literal=username=admin --from-literal=password=admin -n kube-system
创建RBAC认证
Openshift
# cluster-role.yml
apiVersion: v1
kind: ServiceAccount
metadata:
name: bigip-ctlr
namespace: kube-system
---
# For use in OpenShift clusters
apiVersion: v1
kind: ClusterRole
metadata:
annotations:
authorization.openshift.io/system-only: "true"
name: system:bigip-ctlr
namespace: kube-system
rules:
- apiGroups: ["", "extensions"]
resources: ["nodes", "services", "endpoints", "namespaces", "ingresses", "routes" ]
verbs: ["get", "list", "watch"]
- apiGroups: ["", "extensions"]
resources: ["configmaps", "events", "ingresses/status"]
verbs: ["get", "list", "watch", "update", "create", "patch" ]
- apiGroups: ["", "extensions"]
resources: ["secrets"]
resourceNames: ["bigip-login"]
verbs: ["get", "list", "watch"]
---
apiVersion: v1
kind: ClusterRoleBinding
metadata:
name: bigip-ctlr-role
namespace: kube-system
userNames:
- system:serviceaccount:kube-system:bigip-ctlr
subjects:
- kind: ServiceAccount
name: bigip-ctlr
roleRef:
name: system:bigip-ctlr
oc create -f cluster-role.yml
部署BIG-IP Controller
Openshift
- 对应每台F5设备创建一个Deployment
- Deployment中的 --bigip-url 为设备的IP
- Deployment中的 --bigip-partition为之前F5下创建的Partition,Openshift
- Deployment中的 --route-vserver-addr 为F5对外提供服务的IP
#deployment.yml
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: f5-bigip-ctlr-01
spec:
replicas: 1
template:
metadata:
name: k8s-bigip-ctlr
labels:
app: k8s-bigip-ctlr
spec:
# Name of the Service Account bound to a Cluster Role with the required
# permissions
serviceAccountName: bigip-ctlr
containers:
- name: k8s-bigip-ctlr
# replace the version as needed
image: "f5networks/k8s-bigip-ctlr:1.5.1"
env:
- name: BIGIP_USERNAME
valueFrom:
secretKeyRef:
# Replace with the name of the Secret containing your login
# credentials
name: bigip-login
key: username
- name: BIGIP_PASSWORD
valueFrom:
secretKeyRef:
# Replace with the name of the Secret containing your login
# credentials
name: bigip-login
key: password
command: ["/app/bin/k8s-bigip-ctlr"]
args: [
# See the k8s-bigip-ctlr documentation for information about
# all config options
# http://clouddocs.f5.com/products/connectors/k8s-bigip-ctlr/latest
"--bigip-username=$(BIGIP_USERNAME)",
"--bigip-password=$(BIGIP_PASSWORD)",
"--bigip-url=192.168.200.82",
"--bigip-partition=OpenShift",
"--pool-member-type=cluster",
"--openshift-sdn-name=/Common/openshift_vxlan",
'--manage-routes=true',
'--route-vserver-addr=99.248.82.220'
]
imagePullSecrets:
# Secret containing the BIG-IP system login credentials
- name: bigip-login
---
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: f5-bigip-ctlr-02
spec:
replicas: 1
template:
metadata:
name: k8s-bigip-ctlr
labels:
app: k8s-bigip-ctlr
spec:
# Name of the Service Account bound to a Cluster Role with the required
# permissions
serviceAccountName: bigip-ctlr
containers:
- name: k8s-bigip-ctlr
# replace the version as needed
image: "f5networks/k8s-bigip-ctlr:1.5.1"
env:
- name: BIGIP_USERNAME
valueFrom:
secretKeyRef:
# Replace with the name of the Secret containing your login
# credentials
name: bigip-login
key: username
- name: BIGIP_PASSWORD
valueFrom:
secretKeyRef:
# Replace with the name of the Secret containing your login
# credentials
name: bigip-login
key: password
command: ["/app/bin/k8s-bigip-ctlr"]
args: [
# See the k8s-bigip-ctlr documentation for information about
# all config options
# http://clouddocs.f5.com/products/connectors/k8s-bigip-ctlr/latest
"--bigip-username=$(BIGIP_USERNAME)",
"--bigip-password=$(BIGIP_PASSWORD)",
"--bigip-url=192.168.200.83",
"--bigip-partition=OpenShift",
"--pool-member-type=cluster",
"--openshift-sdn-name=/Common/openshift_vxlan",
'--manage-routes=true',
'--route-vserver-addr=192.168.200.80'
]
imagePullSecrets:
- name: bigip-login
oc create -f deployment.yml
查看BIG-IP Controller的部署进度
[root@master01 ~]# oc get pod
NAME READY STATUS RESTARTS AGE
f5-bigip-ctlr-01-7f44695b97-lmwdh 1/1 Running 0 17h
f5-bigip-ctlr-02-54df674f58-j2x26 1/1 Running 0 17h
当BIG-IP Controller POD启动后,在F5上会自动创建两个virtual servers
- "ose-vserver" 为HTTP请求
- "https-ose-vserver" 为HTTPS请求
这两个virtual servers是Openshift下所有的Route共用的。
创建新的应用F5-Test,并创建HTTP Route
Openshift
- 使用自己镜像仓库中的镜像:harbor.example.com/public/nginx:1.14
- 该镜像的制作方法及说明参考:Openshfit上用ConfigMap来自定义Nginx配置
oc new-project f5-test
oc new-app harbor.example.com/public/nginx:1.14 --name=f5-test --allow-missing-images
oc expose dc/f5-test --port=8080
创建Route
apiVersion: route.openshift.io/v1
kind: Route
metadata:
labels:
name: f5-test
name: f5-test
annotations:
virtual-server.f5.com/balance: least-connections-node
spec:
host: f5-test.example.com
port:
targetPort: 8080
to:
kind: Service
name: f5-test
本地绑定hosts
192.168.200.80 f5-test.example.com
浏览器访问http://f5-test.example.com,即能看到应用页面。
创建HTTPS Route(仍然使用上面的应用)
Openshift
apiVersion: route.openshift.io/v1
kind: Route
metadata:
annotations:
virtual-server.f5.com/balance: least-connections-node
labels:
app: f5-test
name: f5-test-2
spec:
host: f5-tes-2t.example.com
tls:
insecureEdgeTerminationPolicy: Allow
termination: edge
to:
kind: Service
name: f5-test
本地绑定hosts
192.168.200.80 f5-test-2.example.com
浏览器访问https://f5-test.example.com,即能看到应用页面。
说明
- Openshit上创建Service后,F5会自动创建新的Pool,Pool里的资源即为Service下的Pod
- 请求到达F5后,F5根据请求的域名,找到对应的Pool,请求直接到达Pod。不会请求集群里的Route。
参考资料
- F5与Openshift中的Route集成
- F5与Openshift中的Service集成