3. PKI - 密钥、证书文件格式和编码的转换
3. PKI - 密钥、证书文件格式和编码的转换
- 1. 文件标准的转换
- ① generate rsa private key
- ② transform between pkcs#1 private key and pkcs#8 private key
- ③ transform between pkcs#1 private key and pkcs#8 private key encrypted
- ④ extract x.509 public key from pkcs#1 private key
- ⑤ extract pkcs#1 private key from pkcs#1 private key
- ⑥ transform between pkcs#1 public key and x.509 public key
- before ⑦ : generate certifcate sign request and self-signed certificate from pkcs#8 private key
- ⑦ extract x.509 public key from x.509 certificate
- ⑧ extract x.509 public key from x.509 certificate sign request (CSR)
- ⑨ store pkcs#8 private and x.509 certifcate as pkcs#12 certificate
- before ⑩ export x.509 certificate as pkcs#7 certificate chain
- ⑩ extract x.509 certificate from pkcs#7 certificate chain
- 2. 文件编码的转换
- 3. 文件内容查看
- 参考
1. 文件标准的转换
下图为各个标准之间的转换关系图。其编码均为PEM格式(PKCS#12除外)。

① generate rsa private key
openssl genrsa -out /export/pkcs1-private-key.pem -passout pass:mypass
该命令默认生成2048位的私钥,使用PEM编码格式,输出到文件/export/toman-private-key.pem,且设置私钥密码为mypass。
② transform between pkcs#1 private key and pkcs#8 private key
- transform from pkcs#1 private key to pkcs#8 private key
openssl pkcs8 -topk8 -in /export/pkcs1-private-key.pem -out /export/pkcs8-private-key.pem -nocrypt
该命令将pkcs#1标准的私钥文件转换为非加密的pkcs#8标准的私钥文件。
- transform from pkcs#1 private key to pkcs#8 private key
openssl rsa -in /export/pkcs8-private-key.pem -out /export/pkcs1-private-key-reserved.pem
该命令将pkcs#8标准的私钥文件转换为pkcs#1标准的私钥文件。pkcs1-private-key-reserved.pem 和 pkcs1-private-key.pem 文件的内容完全一致。
③ transform between pkcs#1 private key and pkcs#8 private key encrypted
- transform from pkcs#1 private key to pkcs#8 private key encrypted
openssl pkcs8 -topk8 -in /export/pkcs1-private-key.pem -out /export/pkcs8-private-key-encrypted.pem
该命令将pkcs#1标准的私钥文件转换为加密的pkcs#8标准的私钥文件。命令行操作时会提示输入密码,如设置密码mypass。
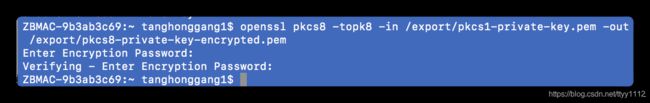
- transform from pkcs#1 private key to pkcs#8 private key
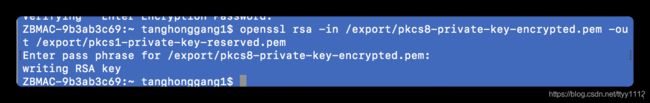
openssl rsa -in /export/pkcs8-private-key-encrypted.pem -out /export/pkcs1-private-key-reserved.pem
该命令将pkcs#8标准的加密私钥文件转换为pkcs#1标准的私钥文件。pkcs1-private-key-reserved.pem 和 pkcs1-private-key.pem 文件的内容完全一致。同样命令行操作时会提示输入密码,此时输入密码mypass。
④ extract x.509 public key from pkcs#1 private key
openssl rsa -in /export/pkcs1-private-key.pem -pubout -out /export/x509-public-key.pem
该命令从pkcs#1标准的私钥文件中导出x509标准的公钥文件。
⑤ extract pkcs#1 private key from pkcs#1 private key
openssl rsa -in /export/pkcs1-private-key.pem -RSAPublicKey_out -out /export/pkcs1-public-key.pem
该命令从pkcs#1标准的私钥文件中导出pkcs#1标准的公钥文件。
⑥ transform between pkcs#1 public key and x.509 public key
- transform from pkcs#1 public key to x.509 public key
openssl rsa -RSAPublicKey_in -in /export/pkcs1-public-key.pem -pubout -out /export/x509-public-key-from-pkcs1.pem
该命令将pkcs#1标准的公钥文件转换成x.509标准的公钥文件。文件x509-public-key-from-pkcs1.pem与x509-public-key.pem的内容一致。
- transform from x.509 public key to pkcs#1 public key
openssl rsa -pubin -in /export/x509-public-key.pem -RSAPublicKey_out -out /export/pkcs1-public-key-from-x509.pem
该命令将x.509标准的公钥文件转换成pkcs#1标准的公钥文件。文件pkcs1-public-key-from-x509.pem与pkcs1-public-key.pem的内容一致。
before ⑦ : generate certifcate sign request and self-signed certificate from pkcs#8 private key
- 根据pkcs#8私钥生成证书申请
openssl req -new -key /export/pkcs8-private-key.pem -out /export/x509-certificate-sign-request.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) []:CN
State or Province Name (full name) []:BJ
Locality Name (eg, city) []:BJ
Organization Name (eg, company) []:JD
Organizational Unit Name (eg, section) []:Y
Common Name (eg, fully qualified host name) []:edi.jd.com
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:mypass
- 根据pkcs#8私钥生成自签名证书
openssl x509 -req -days 365 -in /export/x509-certificate-sign-request.csr -signkey /export/pkcs8-private-key.pem -out /export/x509-certificate.crt
Signature ok
subject=/C=CN/ST=BJ/L=BJ/O=JD/OU=Y/CN=edi.jd.com/emailAddress=[email protected]
Getting Private key
- 改变签名算法
openssl默认采用SHA1withRSA签名算法进行签名,如果要使用SHA256withRSA算法进行签名,可以执行以下命令:
openssl x509 -req -sha256 -days 365 -in /export/x509-certificate-sign-request.csr -signkey /export/pkcs8-private-key.pem -out /export/x509-certificate-sha256.crt
⑦ extract x.509 public key from x.509 certificate
openssl x509 -in /export/x509-certificate.crt -inform pem -pubkey -noout > /export/x509-public-key-from-certificate.pem
该命令从证书文件中抽取x.509公钥文件。文件x509-public-key-from-certificate.pem与x509-public-key.pem的内容一致。
⑧ extract x.509 public key from x.509 certificate sign request (CSR)
openssl req -in /export/x509-certificate-sign-request.csr -pubkey -noout > /export/x509-public-key-from-csr.pem
该命令从证书签名申请中抽取x.509公钥文件。文件x509-public-key-from-csr.pem与x509-public-key.pem的内容一致。
⑨ store pkcs#8 private and x.509 certifcate as pkcs#12 certificate
openssl pkcs12 -export -out /export/pkcs12-certificate.p12 -inkey /export/pkcs8-private-key.pem -in /export/x509-certificate.crt
Enter Export Password:
Verifying - Enter Export Password:
该命令将pkcs#8标准的私钥文件和x.509标准的证书文件导出到pkcs#12标准的文件中。命令行提示输入密码:mypass。
before ⑩ export x.509 certificate as pkcs#7 certificate chain
openssl crl2pkcs7 -certfile /export/x509-certificate.crt -out /export/pkcs7-certificate-chain.p7b -nocrl
该命令将x.509证书文件导出为pkcs#7标准的证书链。
⑩ extract x.509 certificate from pkcs#7 certificate chain
openssl pkcs7 -in /export/pkcs7-certificate-chain.p7b -out /export/x509-certificate-from-pkcs7.crt -print_certs
该命令从pkcs#7标准的证书链中抽取x.509格式的证书文件,x509-certificate-from-pkcs7.crt文件中证书部分的内容与x509-certificate.crt文件一致。
2. 文件编码的转换
在文件标准转换时,所有文件采用的编码均为PEM编码,如果想实现PEM编码和DER编码之间的转换,需要明确指定需要转换的编码格式。以证书为例:
openssl x509 -in /export/x509-certificate.crt -inform pem -out /export/x509-certificate.der -outform der
该命令将pem格式的证书文件转换为der格式的证书文件。
3. 文件内容查看
- 查看DER格式x.509证书文件内容:
openssl x509 -in /export/x509-certificate.der -inform der -text -noout
Certificate:
Data:
Version: 1 (0x0)
Serial Number: 18206178146586227013 (0xfca9569058c07145)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=CN, ST=BJ, L=BJ, O=JD, OU=Y, CN=edi.jd.com/emailAddress=[email protected]
Validity
Not Before: Jul 13 02:51:10 2020 GMT
Not After : Jul 13 02:51:10 2021 GMT
Subject: C=CN, ST=BJ, L=BJ, O=JD, OU=Y, CN=edi.jd.com/emailAddress=[email protected]
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:e7:19:1b:6d:d9:93:91:d4:a3:0e:28:6e:89:29:
ca:cc:05:92:34:a0:9a:16:d9:23:c5:b0:c8:9a:f2:
5d:cf:6a:81:6b:8a:c0:c0:a7:bf:60:6e:c1:ae:10:
eb:58:6e:4a:3e:b5:ba:32:af:95:8a:84:c8:16:09:
a5:39:fc:92:cb:bb:4e:1e:9d:46:81:ff:0b:f6:fb:
54:03:3d:3d:19:0f:9e:d1:8f:96:5b:8a:95:86:f7:
7c:17:4d:e4:4b:b1:76:2f:48:8c:88:31:a2:b0:e7:
d1:c6:b4:1e:4e:b7:ea:8e:b8:80:11:57:fa:27:04:
8a:03:1b:74:16:8e:dd:c1:ab:2a:92:94:70:e9:d7:
e2:65:4f:b8:6b:5c:89:36:17:83:83:15:db:f8:13:
b1:b5:c0:ff:ba:ab:98:56:0d:5e:da:c2:64:87:ca:
0b:3a:76:9c:19:e3:0e:d5:3f:d3:1a:be:ec:09:65:
4b:38:3f:c3:75:63:a7:6a:be:2b:5c:69:b3:bc:bf:
dc:1f:d9:8e:c8:38:95:bf:82:ec:98:c4:5b:4d:a9:
7e:52:a5:bd:5f:92:8e:86:83:81:7c:cb:66:e7:23:
2d:9c:f5:c0:fd:f3:60:d7:29:7c:df:f4:47:cb:7f:
29:ab:83:c0:88:71:32:13:f2:45:31:3f:46:9a:0d:
ce:ff
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
63:5f:2f:47:2b:9b:a2:1e:50:ca:30:29:d1:de:76:c4:a5:e1:
39:6d:f1:59:5c:eb:64:32:14:6a:6f:1c:9d:dd:67:97:4f:15:
6b:1c:41:e3:aa:8a:de:21:01:e5:9e:0b:97:70:21:52:5e:42:
b3:29:ec:9e:1e:2d:64:a9:0d:80:eb:1e:43:ca:89:f5:9c:27:
44:e7:e0:4d:f1:95:9e:f0:fe:f7:ec:08:db:af:7e:63:82:1e:
4b:32:64:b6:7d:68:06:ad:04:2f:3e:69:89:b3:7e:5a:1c:de:
6e:8e:c2:16:0c:3c:b8:60:7f:d5:7e:07:33:9b:7e:29:87:05:
b0:78:2c:ac:94:fb:6e:43:57:bf:11:57:f8:e6:ce:60:a9:23:
d3:61:0e:33:60:c7:db:26:60:00:7c:bd:18:23:8f:9e:c7:58:
95:8e:9b:e9:e9:4f:99:b7:26:7e:04:d7:1a:9d:36:d0:15:7a:
10:93:52:6e:6e:3d:a6:df:ce:6c:e2:69:f2:0e:47:07:ed:65:
95:97:0c:8e:76:64:52:49:c0:56:d6:0a:e6:f6:a9:01:0e:5c:
78:a3:c6:0c:d1:59:42:b3:61:34:dd:a6:e4:88:dd:a1:32:fd:
6f:fa:22:f0:88:eb:56:f8:fd:4d:bf:6d:57:ff:ef:b1:bb:8f:
35:8b:9f:76
- 如果是PEM格式使用命令:
openssl x509 -in /export/x509-certificate.crt -text
- 查看pkcs#12标准文件内容:
openssl pkcs12 -in /export/pkcs12-certificate.p12
Enter Import Password:
MAC verified OK
Bag Attributes
localKeyID: 88 CA D0 F1 0F 22 ED A8 E4 46 5C 66 07 55 08 F5 A6 35 E1 B3
subject=/C=CN/ST=BJ/L=BJ/O=JD/OU=Y/CN=edi.jd.com/emailAddress=[email protected]
issuer=/C=CN/ST=BJ/L=BJ/O=JD/OU=Y/CN=edi.jd.com/emailAddress=[email protected]
-----BEGIN CERTIFICATE-----
MIIDXDCCAkQCCQD8qVaQWMBxRTANBgkqhkiG9w0BAQUFADBwMQswCQYDVQQGEwJD
TjELMAkGA1UECAwCQkoxCzAJBgNVBAcMAkJKMQswCQYDVQQKDAJKRDEKMAgGA1UE
CwwBWTETMBEGA1UEAwwKZWRpLmpkLmNvbTEZMBcGCSqGSIb3DQEJARYKZWRpQGpk
LmNvbTAeFw0yMDA3MTMwMjUxMTBaFw0yMTA3MTMwMjUxMTBaMHAxCzAJBgNVBAYT
AkNOMQswCQYDVQQIDAJCSjELMAkGA1UEBwwCQkoxCzAJBgNVBAoMAkpEMQowCAYD
VQQLDAFZMRMwEQYDVQQDDAplZGkuamQuY29tMRkwFwYJKoZIhvcNAQkBFgplZGlA
amQuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA5xkbbdmTkdSj
DihuiSnKzAWSNKCaFtkjxbDImvJdz2qBa4rAwKe/YG7BrhDrWG5KPrW6Mq+VioTI
FgmlOfySy7tOHp1Ggf8L9vtUAz09GQ+e0Y+WW4qVhvd8F03kS7F2L0iMiDGisOfR
xrQeTrfqjriAEVf6JwSKAxt0Fo7dwasqkpRw6dfiZU+4a1yJNheDgxXb+BOxtcD/
uquYVg1e2sJkh8oLOnacGeMO1T/TGr7sCWVLOD/DdWOnar4rXGmzvL/cH9mOyDiV
v4LsmMRbTal+UqW9X5KOhoOBfMtm5yMtnPXA/fNg1yl83/RHy38pq4PAiHEyE/JF
MT9Gmg3O/wIDAQABMA0GCSqGSIb3DQEBBQUAA4IBAQBjXy9HK5uiHlDKMCnR3nbE
peE5bfFZXOtkMhRqbxyd3WeXTxVrHEHjqoreIQHlnguXcCFSXkKzKeyeHi1kqQ2A
6x5Dyon1nCdE5+BN8ZWe8P737Ajbr35jgh5LMmS2fWgGrQQvPmmJs35aHN5ujsIW
DDy4YH/Vfgczm34phwWweCyslPtuQ1e/EVf45s5gqSPTYQ4zYMfbJmAAfL0YI4+e
x1iVjpvp6U+ZtyZ+BNcanTbQFXoQk1Jubj2m385s4mnyDkcH7WWVlwyOdmRSScBW
1grm9qkBDlx4o8YM0VlCs2E03abkiN2hMv1v+iLwiOtW+P1Nv21X/++xu481i592
-----END CERTIFICATE-----
Bag Attributes
localKeyID: 88 CA D0 F1 0F 22 ED A8 E4 46 5C 66 07 55 08 F5 A6 35 E1 B3
Key Attributes: <No Attributes>
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIFDjBABgkqhkiG9w0BBQ0wMzAbBgkqhkiG9w0BBQwwDgQIr3URCgaRGJwCAggA
MBQGCCqGSIb3DQMHBAijA5m/kFShHQSCBMgzIgdgOiQ0L3taHJf6QNieL66MFQ0B
tBaesdmNdAMfiCqfTrLRdvXvUODVKAENRCGetrPL+yEBiOSHwWsMfLI3Nu0BDq3N
ZLeXBEmh6mldpHBh9+MZ6lYI62/vWr2BparWHCOSvHAaALJgNucbxm+b6oqFns+w
ZkoekuPvsY3EPuh61tjGRtOc2q/Utn+67zVOaUOlr0KH+CpITD9TnUQs+kpexYNO
MDcv1KVP4DcON4zpmDNRjLmcriDGKlJpdgPrE/OdudhIkqnGgg2Jd1ceaZCpiYTa
XsjJExrY7XvoVNIstUMjdbY5QXxp+CoOa2E+uz8+wEe261blB8liKvITfGVR/sVk
dRh1/zxluwXhaWhZ3qTtqRduhVM3H3XZPmPGZAVzHsWqG4F6SGHtCe8mwYfFfCrk
72mKinUwyqXTnka0cbzIXZ7hIl3ps0TvaIFSnZ/osPXdwQ4Nq7cKLyhAdjl3Ykr1
hGXcqQLF9HPQDQoeQzVIYQQvz3BjhVF+BybfA1Cf782t+J+6IHd7jGUb0HXiaqa+
1O5DjWCRIURYZoshUQ2QYAj1zPo30D20Nm9TO+O9BZ1d7Pa2tYvHIHMbXXc4+JF8
lISnOV8hHOU3JXacwWa4H/Q/01TMeq0PcQjGki2ZXiXRNy7jz2Z2wac1eY2YjMwd
HtmI21SiTiAr3c8ok4lUGk5BaiKaiOzredyOD7ldpVHbPjx5CZY381pYQ1I3nqa8
58ibOqKYxR+GFu98pDDkCng65h5UZ8wXIevwcbKz+SaIaIxX9TuEcPIlhJDuO8Iw
b23nbbKZRcvuTzzNwGqyHA/kAhTzbEmBkZKc8iaQ0TJ+M+oG6ru8ju8TVy8/qnhr
N1BFp6fKjicwyobeSjHNTPtmO219+a5D2cS1YfRVKfRCRQNrS0djp1ElZEuzCHJs
4VHpvxKyffWNu+Inns/naLHUECcAdY5UI7tnMmPkJEd60EGBoCOuMSMeP7EF7R3j
JuyiuXs3pBOOfR+HVkF1zQKfCm9fZ9xXBIKsVixOiMVY15tNzzlnaMUNILLdRDkq
uS4rTlA3gPU5L3d5/TGyulG84IJ+tyH/v/MeKfI8wB+J9Biv3PejQsEknJURiVW/
5xy1BwRtpFhGel1Gd6T5BqqmT9ynEL5h904bwbPjUPpU7KDpSPc464kSQD1U52oU
8ofJ9+dmDG6Y2dONzASXxCumoJ3bI0r/XrL4pO9UJ3uCWbKnf5NJRS/VD8EViqUJ
9zYUOtXD0TZv+J8X+FHqSR86/tB6hlZ1EYOvX03M+M25cotGbZqMlCQQMj/Mxgm5
NGV8Ebr2WEJqgmJgxTvwoI8FfoQq+A+eUUN84I/t6EYWPA9Kw1Uj8BEYf1us28Mq
WtKmFPkikbtsv0/D2gEbNuN+l1db/iaYX0rHS/dfQgmVBPV4TBWhUpDvNbHTY7nt
GLn9xFobYorAxPv1BkzyX7eLOcyBd5qUJZnPQIprfDMDgSbpM4SE25zdLNFpEYA6
OE3TzuebvdeEF+2v9x/nBxamkakOaguctoD90K/wGXzkpchde9PU2nSEAGMv1Uzr
kTEyJ9EfmzFOwkKHm4bMHnTXyum0arjbNqJ80T1kUMi6AUWY1qwckEoyDGyZ4V6l
75A=
-----END ENCRYPTED PRIVATE KEY-----
参考
PKCS #1, PKCS #8, X.509
如何创建一个自签名的SSL证书(X509)
使用OpenSSL工具制作X.509证书的方法及其注意事项总结