内网信息收集(Windows)--本机信息收集
文章目录
- 手动查询命令
- 本机网络配置信息
- 查询操作系统信息和软件信息
- 查询本机服务信息
- 查询进程信息
- 启动程序信息
- 查看计划任务
- 查询用户列表
- net session
- 端口信息
- 补丁信息
- 本机共享列表
- 路由表和ARP缓存表
- 防火墙
- 代理信息
- 远程端口
- 自动信息收集的一个脚本
- 权限收集
- 查看当前权限
- 获取域SID
- 查询指定用户信息
手动查询命令
本机网络配置信息
ipconfig /all查询网络配置信息
可查询代理信息,否处于域中
查询操作系统信息和软件信息
- systeminfo
通过systeminfo可以查询OS名称,版本,系统安装时间,启动时间,补丁,域信息等
- 查看系统体系结构 echo %PROCESSOR_ARCHITECTURE%
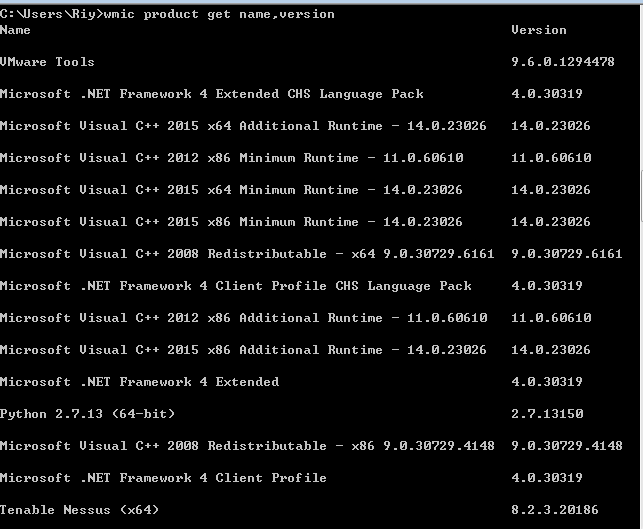
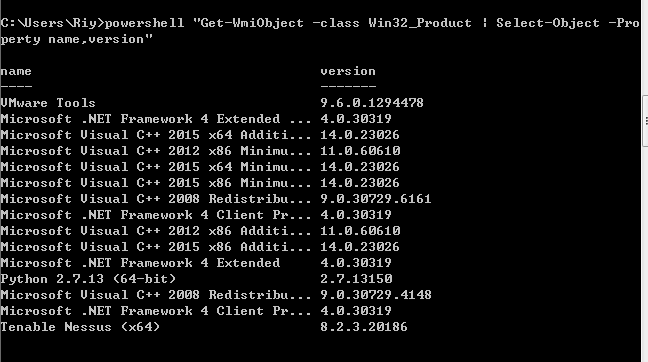
- 查看安装软件的版本,路径等
利用PowerShell命令,收集软件的版本信息: powershell “Get-WmiObject -class Win32_Product | Select-Object -Property name,version”
查询本机服务信息
wmic service list brief
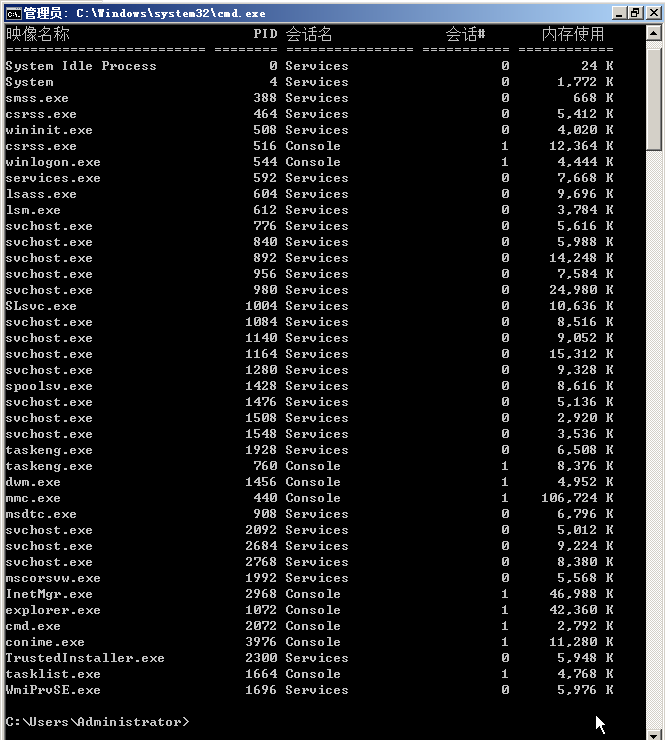
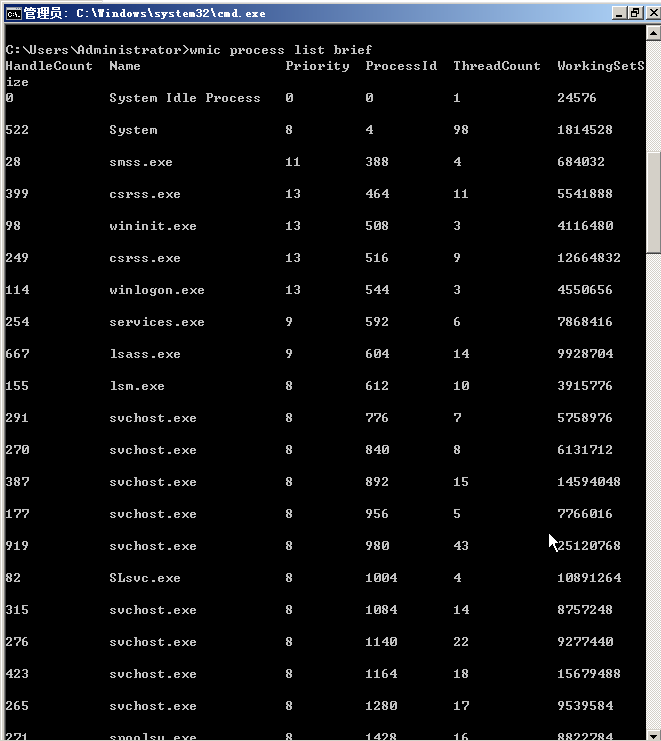
查询进程信息
tasklist
wmic process list brief
启动程序信息
wmic startup get command,caption
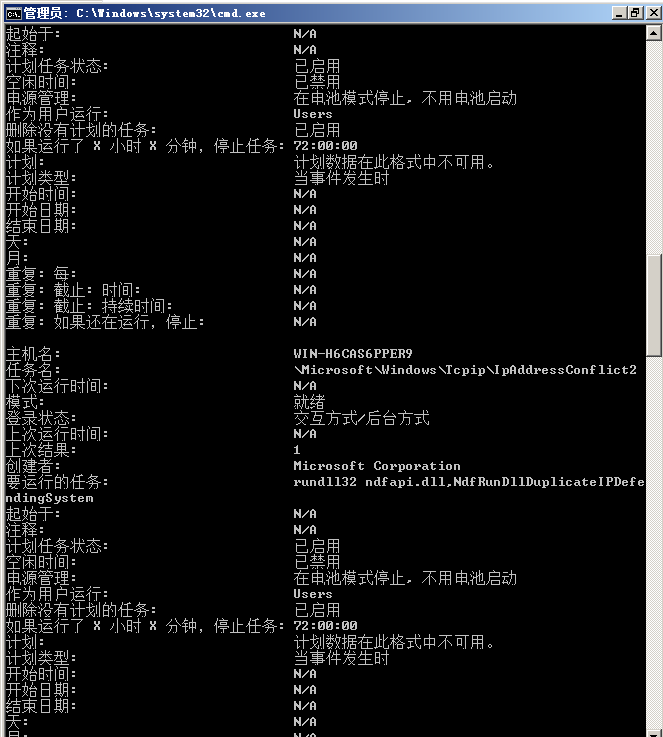
查看计划任务
schtasks /query /fo LIST /v
查询用户列表
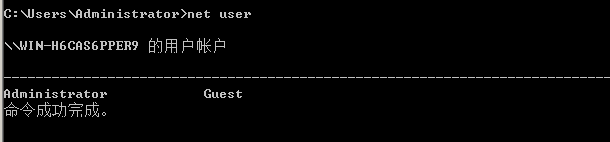
本机用户列表
net user
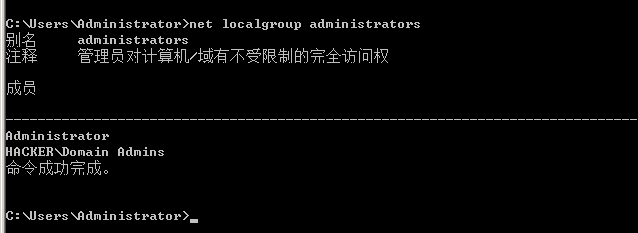
net localgroup administrators
query user 查看用户及登录状态
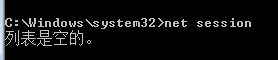
net session
查看本地计算机与所连接客户端之间的对话
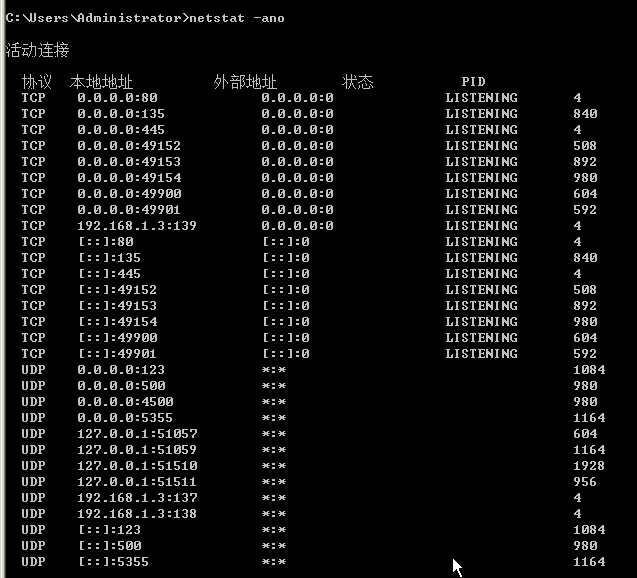
端口信息
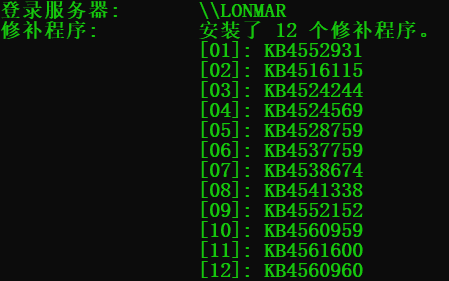
补丁信息
systeminfo
除了systeminfo,还有 wmic qfe get Caption,Description,HotFixID,InstalledOn
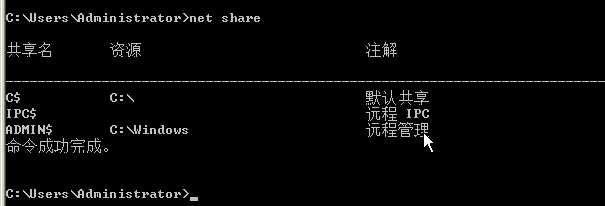
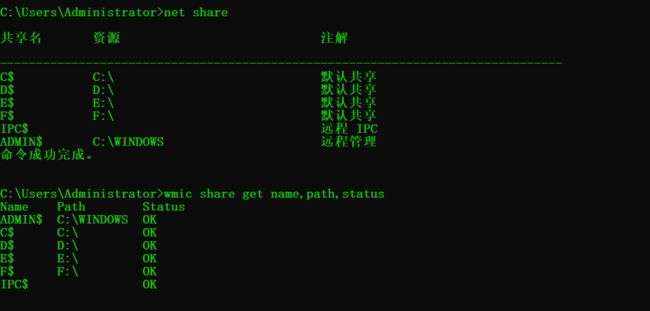
本机共享列表
net share
wmic share get name,path,status
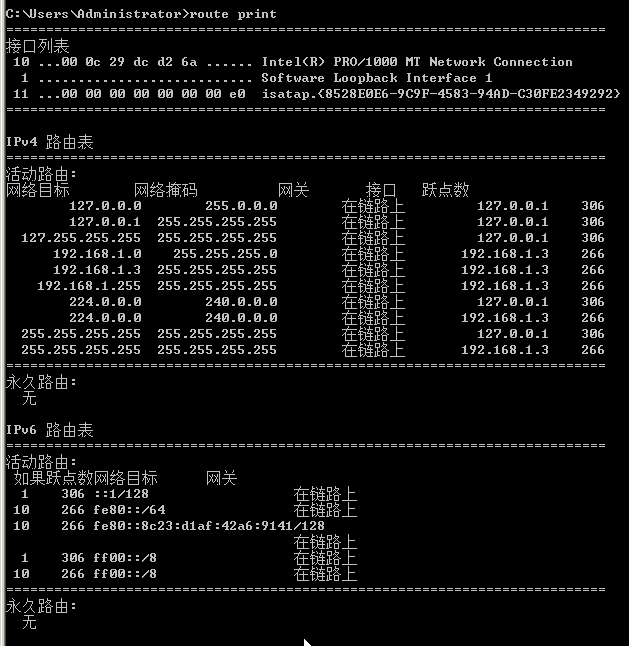
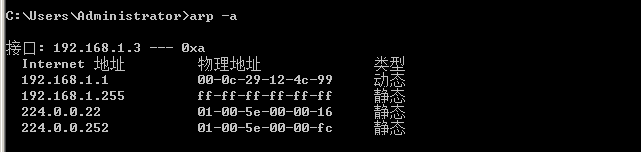
路由表和ARP缓存表
route print
arp -a
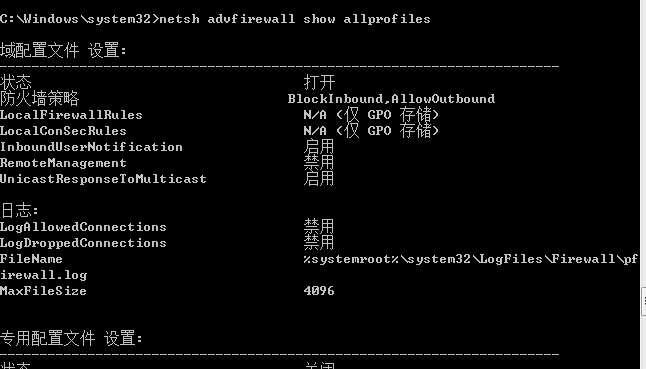
防火墙
- 关闭防火墙
Windows Server 2003及之前版本
命令:netsh firewall set opmode disable
Windows Server 2003之后版本
命令:netsh advfirewall set allprofiles state off
- 查看防火墙配置
命令: netsh advfirewall show allprofiles
- 修改防火墙配置
Windows Server 2003及之前版本,允许指定程序全部连接
命令: netsh firewall add allowedprogram c:\nc.exe “allow nc” enable
Windows Server 2003之后版本,允许指定程序全部连接
命令: netsh advfirewall firewall add rule name=“pass nc” dir=in action=allow program=“C:\nc.exe”
允许指定程序退出
命令: netsh advfirewall firewall add rule name=“Allow nc” dir=out action=out program=“C:\nc.exe”
允许3389端口放行
命令:netsh advfirewall firewall add rule name=“Remote Desktop” protocol=TCP dir=in localport=3389 action=allow
- 自定义防火墙储存位置
命令: netsh advfirewall set currentprofile logging filename “C:\windows\temp\fw.log”
代理信息
reg query “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings”
远程端口
(1) 查看远程连接端口
REG query HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server\WinStations\RDP-Tcp /v PortNumber
0xd3d—3389
(2) 开启远程连接端口
在Windows Server 2003中开启3389端口
命令: wmic path win32_terminalservicesetting where (__CLASS !="") call setallowsconnections 1
在其它系统(server2012、win7)开启和关闭3389端口
开启命令: REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
关闭命令: REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 11111111 /f
自动信息收集的一个脚本
任何版本的Windows xp低权限无法执行wmic,Windows 7以上版本的低权限用户允许访问wmic并执行相关操作
for /f "delims=" %%A in ('dir /s /b %WINDIR%\system32\*htable.xsl') do set "var=%%A"
wmic process get CSName,Description,ExecutablePath,ProcessId /format:"%var%" >> out.html
wmic service get Caption,Name,PathName,ServiceType,Started,StartMode,StartName /format:"%var%" >> out.html
wmic USERACCOUNT list full /format:"%var%" >> out.html
wmic group list full /format:"%var%" >> out.html
wmic nicconfig where IPEnabled='true' get Caption,DefaultIPGateway,Description,DHCPEnabled,DHCPServer,IPAddress,IPSubnet,MACAddress /format:"%var%" >> out.html
wmic volume get Label,DeviceID,DriveLetter,FileSystem,Capacity,FreeSpace /format:"%var%" >> out.html
wmic netuse list full /format:"%var%" >> out.html
wmic qfe get Caption,Description,HotFixID,InstalledOn /format:"%var%" >> out.html
wmic startup get Caption,Command,Location,User /format:"%var%" >> out.html
wmic PRODUCT get Description,InstallDate,InstallLocation,PackageCache,Vendor,Version /format:"%var%" >> out.html
wmic os get name,version,InstallDate,LastBootUpTime,LocalDateTime,Manufacturer,RegisteredUser,ServicePackMajorVersion,SystemDirectory /format:"%var%" >> out.html
wmic Timezone get DaylightName,Description,StandardName /format:"%var%" >> out.html
权限收集
查看当前权限
当内网中存在域时,本地普通用户只能查询本机相关信息,不能查询域内信息。本地管理员用户和域内用户可以查询域内信息。原理:域内所有查询都是通过域控制器实现的(基于LDAP协议),而这个查询需要权限认证,所以只有域内用户才有这个权限,当域用户执行命令时,会自动使用Kerberos协议进行认证,无须额外输入账号密码。
whoami
获取域SID
whoami /all
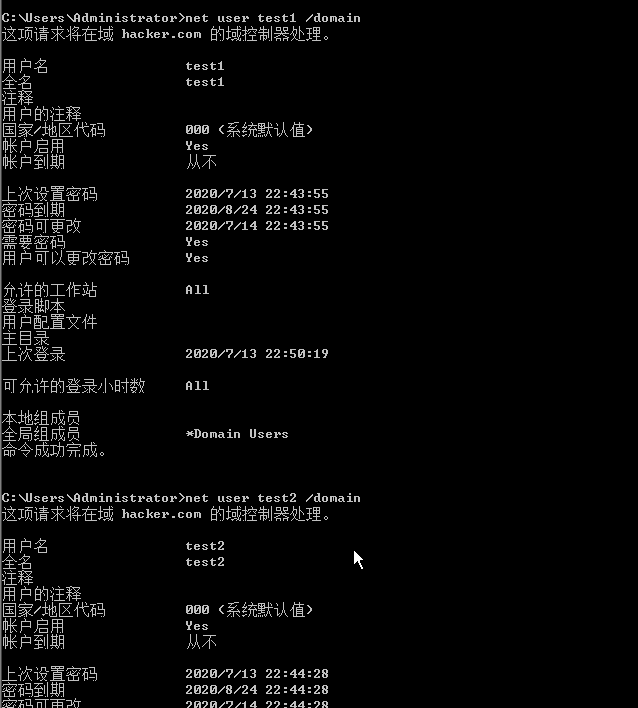
查询指定用户信息
net user username /domain